By Nati Tal (Guardio Labs) — BadEx II
TL;DR
The “Dormant Colors” is yet another vast campaign of malicious extensions with millions of active installations worldwide, this time with a color-related theme and full of deception all through the chain. It starts with the trickery malvertising campaign, continues with a crafty novel way to side-load the real malicious code without anyone noticing (until now!), and finally with stealing not only your searches and browsing data, but also affiliation to 10,000 targeted sites — a capability that is easily leveraged for targeted spear phishing, account takeover and credential extraction — all using this powerful network of millions of infected computers worldwide!
We will share our findings and shine a light on those already not-so-dormant extensions, how we discovered their crafty way to avoid detection, and yet again — how they find new ways to steal our data and monetize on our backs!
More in this series:
BadEx Part I: The Dynamic Search Hijackers
The Dormant Colors Extensions Catalogue
By mid-October 2022 there were at least 30 variants of this extension part of a campaign for both Chrome and Edge, available freely in the relevant stores:
This campaign has been around for a while and some variants of those extensions were flagged already as potentially harmful in the past — yet this campaign continues in full throttle, with many variants currently available on both Edge and Chrome stores, leading to millions of currently active installations worldwide!
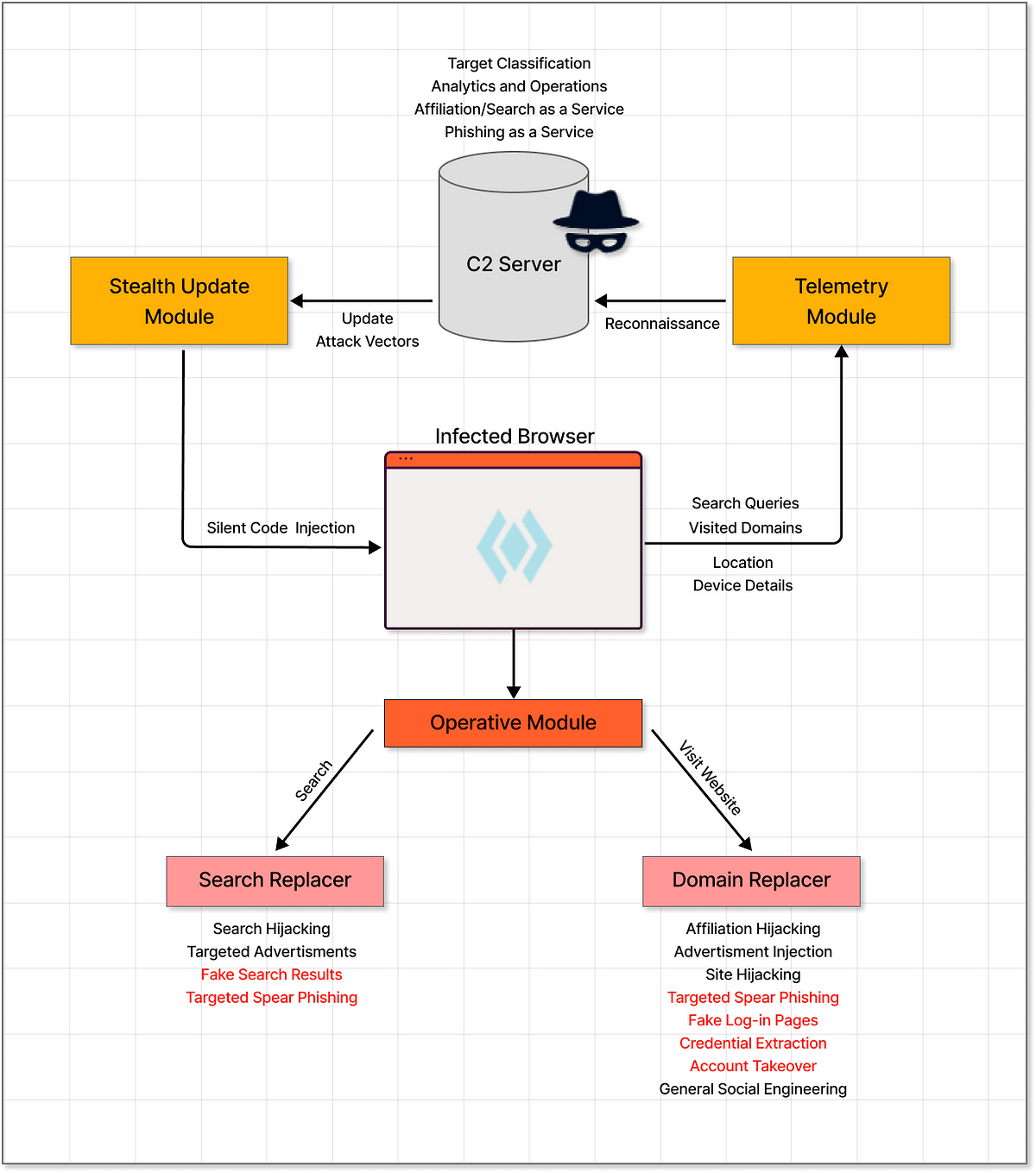
Powerful Command & Control Infrastructure Abusing Your Browser
To cut it short, this bad extension is much more than another search hijacker — it includes stealth modules for code updating and telemetry collection, as well as a backbone of servers harvesting data from millions of users, classifying potential targets, and being able to target specific users with many kinds of social engineering attack vectors that can quickly steal credentials and put people and even big organizations out of business!
In the following diagram, we can witness the vast command and control infrastructure and capabilities of this bad extension campaign.
The above shows how this campaign can both target innocent internet users and make affiliation fees, while can also be leveraged to target organizations — all with the same capabilities and infrastructure already deployed to millions of devices worldwide! After all, you only need one employee to do one mistake while trying to log in to his/her corporate email from an infected personal computer — being presented with a deceptive corporate login page instead.
The Dormant State
So how do they do that? And if indeed they practice those malicious activities — how come they weren’t banned already for violating the extension store policies? Here lies the simple yet powerful trickery that managed to fool even the big names and policy enforcers!
In its initial state, the extension is harmless. Looking through the code will reveal tons of color and style-related functions with names likecssbgcolors() and setlightmodes(). Here are some examples of functions that do nothing bad (at least for now):
rgbcu is one of many color-themed “library” functions all around the code. In some cases, you also see many nested functions that do nothing and are never called — but can calculate some RGB color conversions or even PDF-related stuff. Anyhow, we will get back to those and other code snippets later on.
Initial Propagation With Classic Deception
Let’s start with the first stage of infection — Malvertising. Like in many other malicious campaigns, advertisements are one of the most abused distribution methods. In our case, it also includes some lies and manipulations just to get you to click on the install button as seen in this example video:
No. You don’t need to install an extension to continue. But it won’t let you see that movie you wanted to stream or download that e-book— unless you click OK and surrender your will.
“Backdoor Code Injection Weaponizer Flow”
So you clicked OK and installed the extension that supposedly does nothing bad. Well, here comes the exciting bit. Note how once you install the extension a new tab is automatically created (after auto-closing the Edge store popup windows in that case) redirecting you to a blank “thank you” page that again redirects you to yet another advertisement. Well, you will probably just dismiss that tab and continue on your way — but something else just happened behind the scenes.
Along this redirect chain, you stumble upon a PHP resource returning an HTTP 200 with content instead of the HTTP 302 redirection. This means the next redirect was forced by code in the page itself and something else is also happening there. The flow instyleflex (extensions id: adpffjpbhgiofmjffgcnohaielbeekfk) extension variant looks like this:
The getcolor1.php returns a nasty and LONG page with tons of scripts full of string arrays and some obfuscated code. It’s almost 200kb, so we can’t show it all here (see IOCs for detailed samples) — but some snippets are mandatory:
It starts with a full blank HTML page that does nothing (and this is what the user actually sees) but then includes the malicious scripts. The first one dynamically creates elements on the page while trying desperately to obfuscate the javascript API calls. Both of those HTML elements (colorstylecsse and colorrgbstylesre) include content (InnerText) that for the first is a ‘#’ separated list of strings and regexes and the last is a comma-separated list of 10k+ domains (!!!). To finish it up, it also assigns a new URL to the location object so you are redirected to the advertisement (https://nkingwithea[.]com/?tid=956865&subid=typage) that finalizes this flow as it is was just another advertisement popup.
The scripts continue with the advertising tracker looking for cookies and other tracking info you might already have from other variants of this campaign. There is also an interesting image element generation, used for tracking installations of the extension by requesting a specific resource with relevant query strings from their C&C server at superofferss[.]com . A nice twist for hiding this bit as well.
Side Loading Code From Generated Style Elements
Back to the interesting huge lists of domains and parameters, let’s look at the companion malicious code on the extension itself. After all, no one sees those elements and their content — yet there must be a reason for all of this.
Looks like it was always under our noses in the content.js file, the one that includes some code bits that are injected into EVERY site’s DOM you visit once the extension is installed:
The first part is doing what styleflex promised — waits for commands to change the alignment and padding of the page. Yet we should focus on the second part — the load listener.
This does a double document.getElementByID call and sends the InnerText of those elements as a message to the background worker of the extension. Those messages are entitled color and stylergb … how original. Now note the element names it looks for — yep, our old friends colorstylecsse and colorrgbstylesre.
To make a long story short, the color message is handled in some very simple functions in the background.js worker. Those will grab the content of the color message, store it on local extension storage for persistency, split the string using the commas or the sharp symbols accordingly, and save it on a dedicated global array variable (rgb[] and boxm[]).
Here is an example of the above flow handling the element colorstylecsse placing its values in rgb[]:
Note the functionrgbpag() that creates some regex globals (masqueraded as style variables) out of some injected content.
From Dormant to Fully Awake and Kicking
Combining the above, and also adding the huge list of domains, we get the following list of newly generated global variable values, used heavily in the extension background worker, finally revealed:
// Array of URL handling and hijacking features params
rgb[0] - "yahoo.com"
rgb[1] - "p"
rgb[2] - "q"
rgb[3] - "https://005gs.com/bingchr?q="
rgb[4] - "^http(s)?://(www|search?).(google|yahoo|bing|ecosia)?.[a-z]{2,4}/search"
rgb[5] - "^http(s)?://(www|search?).yahoo.com/yhs/search"
rgb[6] - "duckduckgo.com/?q="
rgb[7] - "ask.com/web?"
rgb[8] - "/%20/g"
rgb[9] - "+"
rgb[10] - "www."
rgb[11] - "&first"
rgb[12] - "bing.com"
rgb[13] - "7fk8qechol"
rgb[14] - "popup"
rgb[15] - "https://smashaff.com/redirect?&url="
rgb[16] - "www"
rgb[17] - "amazon.com"
rgb[18] - "colort"// 10,000+ domains used for affiliation and general hijacking
mbox = ['alibaba.com', '1ink.com', '365games.co.uk', ..... ]// Regex for default search URL detection
styledefault = RegExp('^http(s)?://(www|search?).(google|yahoo|bing|ecosia)?.[a-z]{2,4}/search')// Regex for Yahoo's Hosted Search Service Query URL detection
styley = RegExp('^http(s)?://(www|search?).yahoo.com/yhs/search')// Regex for DuckDuckGo query URL detection
styled = RegExp('duckduckgo.com/?q=')// Regex for ASK.com query URL detection
stylea = RegExp('ask.com/web?')
For completeness — here are the same example functions we mentioned earlier — this time with rgb[] and style* replaced with their actual “weaponized” values:
And this is how it looks like once you try to search for anything:
This extension is dormant no more!
“Show Me the (Affiliation) Money!”
We now have a “weaponized” extension, but what for? Yet again, the same story of search hijacking — but this time with a twist!
Remember that huge list of domains? It’s not only search hijacking in our case, as here we have another malicious service created by those bad actors — An Affiliation Hijacker.
The concept is simple — the extensions continuously snoop around for any site you visit. Once you visit a site part of their “shopping list”, it will wait for a second and then redirect you to this special service URL:
https://smashaff[.]com/redirect?&url={www.hijackedsite.com}The above acts like any other cloud service — gets the domain you wanna hijack and selects what to do with it according to its service configuration. You can see this magic happening in the colorcheck function in the extension worker:
Most of the configuration of what to do with those sites is managed by the bad actors on their servers smassaff[.]com allowing them to do practically whatever they want — and indeed they practice different scamming for different sites:
- AliExpress — Redirects you to the affiliation service page of AliExpress (
https://s[.]click[.]aliexpress[.]com/e/_AZEgcp) that in turn get’s you back to the main store page as if you were directed by the affiliate (gifting some affiliation fees to the bad actors here). - Amazon — Specifically, redirects you to a blog post about some electric bike brand (
https://electricwheelss[.]com/2022/08/04/top-5-ancheer-electric-bikes-of-2021-reviews-pros-cons/) that is followed with an affiliated redirect to that bike brand shopping page on amazon. - Adult sites — in this case, there is a totally different approach. Any relevant domain of this category in the list is directly forwarded to
smashaff[.]com/adultwhich in turn directs you to an advertisement in this category using another fishy ad service atsmashofferss[.]com/r.php?key=oc88a3. Finally, you go to the site of the bad actors’ choice!
As an example, we can witness here the affiliation hijacking kicking in for this shopping site at 365games.co.uk. Notice the address bar being filled with affiliation sources data that wasn’t there before.:
It is possible to quickly reconfigure the operation using the stealth update module we’ve seen above, and also right on the server side, to add other even more malicious flows — starting from presenting phishing fake log-in pages instead of account login pages for domains like Facebook, Twitter, and even bank accounts and organization cloud account portals:
Summary
This campaign is still up and running, shifting domains, generating new extensions, and re-inventing more color and style-changing functions you can for sure manage without. Adding to that, the code injection technique analyzed here is a vast infrastructure for mitigation and evasion and allows leveraging the campaign to even more malicious activities in the future. At the end of the day, it’s not only affiliation fees being collected on your back, this is your privacy as well as your internet experience being compromised here, in ways that can target organizations by harvesting credentials and hijacking accounts and financial data. No extension that makes a fine-looking website look dark and ugly is worth it…
More from the BadEx Project:
BadEx Part I: The Dynamic Search Hijackers
About Guardio
Guardio develops tools and products to combat modern web and cloud-based threats and uses a combination of ML and proprietary algorithms to detect and prevent online threats.
Guardio’s flagship product is an AI-based browser extension that keeps millions of users and businesses safe online and is available for Chrome & Edge.
Key features include antiphishing protection, identity monitoring, notification blocking, and malicious extension removal.
Visit us at guard.io
References and IOCs
Summing up this campaign with the following IOCs, extracted from extensions code, injected code, and analysis of malvertising campaigns and malicious services hosted by the bad actors themselves:
Domains:
------------------------
isloov[.]com
changecolorss[.]com
simpledark-tab[.]com
toodipex-sucticago[.]icu
productivitytab[.]co
smashofferss[.]com
superofferss[.]com
smashsearches[.]com
smashaff[.]com
005gs[.]com
lkbx[.]me
websearches[.]club
xcfss[.]xyz
pelsx[.]xyz
xcfss3[.]xyz
eisx2[.]xyz
lso2[.]xyz
eisx[.]xyz
vnhs[.]xyz
dgopx[.]xyz
yt5ds[.]xyz
eisx3[.]xyz
666xs[.]xyz
sikxsx[.]xyz
bvii[.]xyz
sokjs[.]xyz
cs5s[.]xyz
rssok[.]xyz
188xs[.]xyz
udjx[.]xyz
zcgxd[.]xyz
lso1[.]xyz
eisx4[.]xyz
xcfss2[.]xyz
xcfss3[.]xyz
eisx2[.]xyz
lso2[.]xyz
eisx[.]xyz
vnhs[.]xyz
dgopx[.]xyz
yt5ds[.]xyz
eisx3[.]xyz
666xs[.]xyz
sikxsx[.]xyz
bvii[.]xyz
sokjs[.]xyz
cs5s[.]xyz
rssok[.]xyz
188xs[.]xyz
udjx[.]xyz
zcgxd[.]xyz
lso1[.]xyz
eisx4[.]xyz
xcfss2[.]xyzExtensions ID's
------------------------
edbgoocdeaamfeeeocpfkpfjmjnmhcla
egfchmabkmedeeempggjnolmijhfdagi
opkokhpmbgjdfjbggnmdnoekjknnaghh
hmaclblocpanindmnimojolnaclhfole
ehbjgclhokkohpolmaipdehahneepele
imkhfhibmmkbheampboljhbmjlhjdlmk
elemmnlneeddpnhlgkfhipecchjebcgk
mpdelknfnohhapohdlgfekdfkamkolok
ddbdapfmebdgkjkjgddapklpghceojmb
fjekbjmijhhpcdclgmejeadnpiepncbc
pbpddckmkaicajigbchfomigmmkkdoke
ekldkpcedenimoinejnfdpfaffpinhki
jlpahiloaaihfkckaaihjecoggkoeaca
adpffjpbhgiofmjffgcnohaielbeekfk
dbikcelahekbgkiljdppbimlhinomclc
kcfdboeljlefeagnjaheanpmhddpdced
fceoddkknbldnpigkpdgpldjbkgammgm
jjopiefdgbhpkohefjckmllpfjidbegj
gejnljpgdanbokhpfbkcfdhppbadhaik
dolkekeohjbdpclenociegcnolpipafo
offhdmdommnophkdkgciggcghoioimdo
amjpdgpgkinjeonoelcinmjdopohhgci
fjjcldfecppdliaaljdgjbjdcmkemidl
ajpffhafeldpnckpoemahieecnphaldi
mbfbhfipcpijkpehhkdceahlliegfchg
maembbfdjjclmehfclijpljfnpeoafgc
hbidbmehgcplinfedbdpegpinfphhjdj
mmnmjaaahajpohkgfdicddpoedkdidkp
bmhaidbpfbdgfgjbgphbmmbdejabldpp
gdemnenfidchpoijhfgfjmjljohbaajc
bppigngppakjooidhckpoboboboaghdj
fhpcjlokhfjadfcnhdhphhdlcafmpook
kanegamnjhfjdblagekgnffmjcfiphao
dpffejkpogfomgjgigpeccndfonkpiad
gkghknppcanelmfgeffbmfjpoklnnmbk
For your reference, we also share these gist links of one of the extensions code including reversing notes and comments — so you will be able to witness the full extent of this operation firsthand:
- background.js
- content.js
- getcolor1.php