Imagine you are a homeowner who wants to protect your valuable assets against theft. Vulnerability management is like installing a security system in your home. If someone tries to break in, it will help alert you to an unexpected open door or broken window. However, it cannot eliminate risk entirely.
Exposure management, on the other hand, takes security to the next level. It is like hiring a security firm with deep intelligence on ongoing crime to patrol your neighborhood and monitor for anomalous activity. It provides a proactive layer of security and helps improve your ability to detect and respond to threats.
Similarly, in the cyber realm, exposure management takes a more holistic approach to security, considering not only vulnerabilities but also the likelihood of an attack and the potential impact of a breach. It also includes steps to reduce risk, like implementing security controls and educating employees about security best practices.
For more, listen to the recent The Defender’s Advantage Podcast, Frontline Stories: Exposure Management Beyond Vulnerabilities.
A New, Proactive Approach to Exposure Management
Mandiant, now part of Google Cloud, aims to help every organization be more proactive in managing risk from cyber threats. To support this mission, Mandiant now offers Mandiant Proactive Exposure Management. The solution provides a suite of products and services to enable organizations to reliably and continuously reduce the most critical and attackable exposures—before adversaries act on them.
Vulnerability management is a singular process focused on identifying and mitigating vulnerabilities. Exposure management is a program consisting of tools, services, and processes that allow organizations to assess all enterprise assets, digital risks and security posture to continuously evaluate response prioritization and risk mitigation strategies.
Exposures are more than vulnerabilities. Exposures are cloud misconfigurations, human errors like clicking on a phishing email—anything that exposes the company to risk.
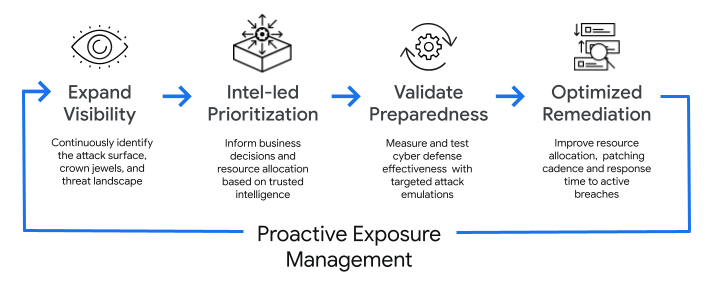
A proactive approach to exposure management is a four-step strategy that helps organizations:
- Know what’s exposed
- Know who’s targeting them
- Know if they are prepared to handle an attack
- Know if they’re being attacked right now
Assess the Property — Know What’s Exposed
You can’t protect what you don’t know exists. Therefore, the first step is to gain visibility into all assets belonging to the organization. This includes identifying the crown jewels of the organization–the assets that hold the greatest value to the business–and determining which assets are exploitable. The capabilities required include:
- Continuous asset discovery, classification and criticality assessment
- Vulnerability, misconfiguration and exposure enumeration

The outcome of expanding visibility of the attack surface and exposures can be accomplished with technologies, like external attack surface management (EASM), cyber asset attack surface management (CAASM), cloud security posture management (CSPM), or with consistent red team or penetration testing.
The Neighborhood Crime Watch — Know Who’s Targeting the Organization
Next, you need to understand the adversaries targeting your organization and how they are orchestrating attacks. Mandiant recently published the Global Perspectives on Threat Intelligence report, in which 79% of respondents reported that they make decisions without adversary insight.
To effectively prioritize and make intelligence-led decisions for prioritization and resource allocation, organizations need to be able to answer:
- Who are the threat actors targeting my organization or my industry peers?
- What are the top five to ten tactics, techniques and procedures (TTPs) that my security controls and team need to be able to defend against?
- Are we informing the detection and response functions with threat intelligence?
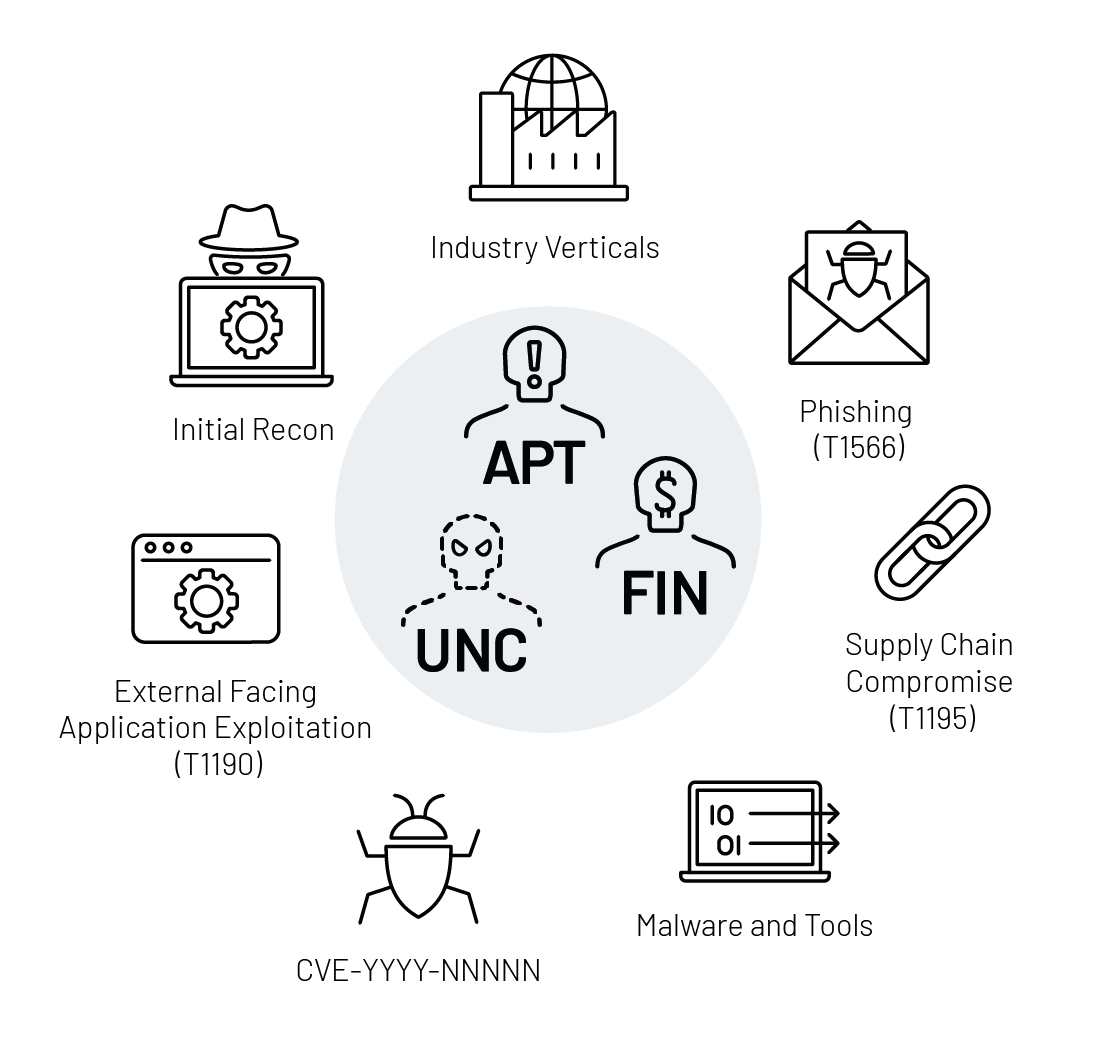
With the proper tools, security teams can be alerted and see how threat actors are planning their attack in the initial reconnaissance stage of the attack lifecycle. This insight enables organizations to develop a risk-based approach to exposure mitigation that considers the likelihood of and impact of different attacks.
Test the Alarm System — Know They are Prepared to Handle an Attack
A routine check of a home alarm system gives peace of mind and holds the alarm company accountable to maintain a reliable system. Security controls are no different.
After identifying the scope of the attack surface and areas of the threat landscape to focus on, organizations need to continuously test and validate the effectiveness of the security controls and their operations. Testing should involve both automated and manual attack emulation, using real-world TTPs that adversaries use in the wild.
Real-Time Intruder Alarms — Know if They’re Being Attacked Right Now
With the current state of home security systems, most homeowners would receive near real-time alarms to intrusion events or if the neighbor’s kid accidentally hit a baseball through the window.
Security teams require near real-time alerts to ongoing malicious activity and the means to be incident response readiness. The capability can be achieved by mapping indicators of compromise to security events to identify an ongoing attack or by working with trusted experts to make the organization threat ready.
Conclusion
Organizations can take a proactive approach to cybersecurity that combines a broader, continuous look at the expanding attack surface with a process for prioritizing remediation activities based on both the potential business impact and the likelihood of a security incident.
Mandiant partners with organizations as they build and mature their exposure management strategy.
Learn more about Mandiant Proactive Exposure Management and talk to a Mandiant expert about adopting a more proactive approach.
Source: https://www.mandiant.com/resources/blog/proactive-approach-exposure-management
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português