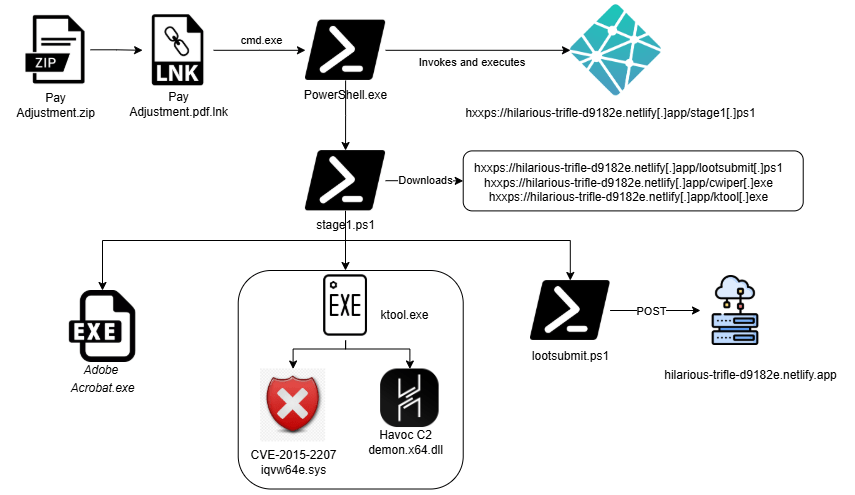
This article details a sophisticated ransomware operation that uses a deceptive ZIP file containing an LNK shortcut to deploy a multi-stage PowerShell-based infection. The attack exploits a vulnerable driver (CVE-2015-2291) to escalate privileges and introduces a customized ransomware known as “DOGE BIG BALLS Ransomware.” The manipulative tactics of the attackers include psychological elements and targeted location tracking for enhancing the attack’s precision. Affected: Ransomware victims, Organizations, Cybersecurity sectors
Keypoints :
- The attack employs a ZIP file with an LNK shortcut for stealthy execution.
- Exploits the CVE-2015-2291 vulnerability for privilege escalation.
- Ransomware is branded as “DOGE BIG BALLS Ransomware” for psychological manipulation.
- Uses router MAC addresses for precise location tracking via the Wigle.net API.
- Extensive system profiling is conducted prior to encryption.
- Incorporates a Havoc C2 beacon for ongoing control post-infection.
- Prominent use of PowerShell scripts for the attack’s execution.
- Utilizes provocative and misleading content to confuse victims.
- Includes ransom demands with personal information to further intimidate victims.
- The presence of various anti-analysis techniques to evade detection.
MITRE Techniques :
- Initial Access (TA0001): Phishing (T1566) – Malicious ZIP archive delivered through phishing with embedded LNK file.
- Execution (TA0002): Command and Scripting Interpreter: PowerShell (T1059.001) – PowerShell is used to download and execute malicious payloads via stage1.ps1.
- Persistence (TA0003): Boot or Logon Autostart Execution: Startup Folder (T1547.001) – Ransomware placed in the startup folder for persistence.
- Privilege Escalation (TA0004): Token Impersonation/Theft (T1134.001) – SYSTEM token is stolen using a vulnerable driver for privilege escalation.
- Privilege Escalation (TA0004): Abuse Elevation Control Mechanism: Exploitation for Privilege Escalation (T1068) – Uses a vulnerable signed driver (iqvw64e.sys) to gain kernel-level access.
- Defense Evasion (TA0005): Obfuscated Files or Information (T1027) – stage1.ps1 executes payloads in memory to avoid detection.
- Defense Evasion (TA0005): Signed Binary Proxy Execution: Signed Driver (T1218.005) – Loads a signed but vulnerable driver to evade detection.
- Discovery (TA0007): System Information Discovery (T1082) – Collects hardware and system information.
- Discovery (TA0007): System Network Configuration Discovery (T1016) – Gathers network configuration including MAC and IP info.
- Discovery (TA0007): System Location Discovery (T1614) – Uses BSSID and Wigle API for precise geolocation tracking.
- Collection (TA0009): Data from Local System (T1005) – Exfiltrates collected system and network data.
- Command and Control (TA0011): Ingress Tool Transfer (T1105) – Downloads malicious binaries and components for the attack.
- Impact (TA0040): Data Encrypted for Impact (T1486) – Encrypts files with a specific extension and drops ransom notes.
- Impact (TA0040): Inhibit System Recovery (T1490) – Deletes system restore points to prevent file recovery.
Indicator of Compromise :
- [SHA-256] 5402c5dc6656697b22a20e90f6ab7a2cd216ce7c70126ed0e855682035c299be
- [URL] hxxps://hilarious-trifle-d9182e.netlify.app/Pay%20Adjustment.zip
- [SHA-256] d802bdaad6713549b5098d3545e07794900869c01a68024a1282fea74d40c4a3
- [URL] hxxps://hilarious-trifle-d9182e.netlify.app/stage1.ps1
- [SHA-256] 3d2cbef9be0c48c61a18f0e1dc78501ddabfd7a7663b21c4fcc9c39d48708e91
Full Story: https://cyble.com/blog/doge-big-balls-ransomware-edward-coristine/
Views: 46

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português