On February 22, 2025, the Critical Infrastructure and Security Agency (CISA) issued a #StopRansomware: ALPHV Blackcat ransomware alert. This alert builds upon earlier Federal Bureau of Investigation (FBI) work and contributions from other agencies and OSINT sources in 2022, 2023, and early 2024. This alert released new Indicators of Compromise (IoC), including several command and control (C&C) server domains essential to the Kill Chain1 currently used by the Blackcat threat actors.
| We share how Infoblox Threat Intel SUSPICIOUS domain feeds can proactively identify likely MALICIOUS Blackcat ransomware C2 domains before this information is available in commercial or public OSINT sources. By blocking access to these MALICIOUS C2 domains you can break the Blackcat Kill Chain early and decisively. |
Many threat actors utilize a rolling tide of malicious domains to support their Kill Chain activity, from early infection to ongoing malicious activity relying on C&C servers. Once one of their malicious domains is discovered, the threat actors switch rapidly to one of the newer domains. Most of these threat actors, likely including the Blackcat threat actors, create, sometimes age, and rotate these domains into their operations. Once identified in OSINT, or perhaps based upon some algorithm the threat actors are using, these domains are rotated out and replaced.
That period of time is the critical window of danger during which organizations are most vulnerable. Within hours to days of these domains appearing in OSINT, most well-staffed and managed security operations centers (SOC) have blocked them, if only manually. Smaller organizations may remain vulnerable for months if this data is not utilized. The point is that the damage by these threat actors is done between the time the domains are created and the time they finally end up identified as visible in OSINT or as delivered in threat feeds.
Blackcat Ransomware – Anatomy of the Attack
Blackcat is yet another highly dangerous ransomware family. The CISA alert puts Blackcat front and center. You may know that the U.S. State Department issued a $15 million reward for the ALPHV/Blackcat threat actors, who have caused untold economic damage. Blackcat ransomware appears linked to Russian threat actors and likely involves other members from varying countries and backgrounds.
| According to the FBI, the Blackcat ransomware group has compromised thousands of businesses and organizations worldwide and extorted over $300 million in funds. |
The Blackcat business model generally works as a ransomware-as-a-service (RaaS). The Blackcat threat actors build the code for other affiliates to utilize and deploy. This enables new infrastructure to be widely used to realize the greatest illicit gain on the initial investment. This gives all parties involved leverage.
To make matters worse the Blackcat threat actors routinely use TRIPLE EXTORTION. Triple extortion is as bad as it sounds. Triple extortion means they (1) demand extortion payments to decrypt the data, (2) threaten to leak the data, and (3) threaten additional DoS attacks. Finally, as always, the FBI has documented many instances of ransom being paid by victims who still could not decrypt their data with the key provided by the threat actors.
The Blackcat Kill Chain can be complex. The Blackcat threat actors leverage previously compromised user credentials to access the victim system. Once the malware establishes access to C&C servers, it can compromise the Active Directory user and administrator accounts.
The malware uses the Windows Task Scheduler to configure malicious Group Policy Objects (GPO) to deploy ransomware. The Blackcat threat actors leverage PowerShell Scripts and Cobalt Strike and disable security features within the victims’ network.
| The key is identifying the Blackcat threat early and immediately breaking the Kill Chain. Once the Blackcat Kill Chain has begun to unfold, it is generally too late to stop the exfiltration of an organization’s confidential and proprietary data and the extortion fee payments demanded by the threat actors to regain data access. |
Analysis and Methodology
Our DNS Early Detection Program identifies and analyzes potentially harmful domains and cross-references our findings with public Open Source Intelligence (OSINT) such as government alerts, commercial threat intelligence feeds, and the many blogs and public threat exchanges frequented by many cyber defenders.
The CISA publication reference in this article released two key C&C domains on February 27, 2024. Detailed links are provided at the end of this article. Additional domains were published on/about February 20, 2024.
Infoblox extracted malicious domains identified within these OSINT sources. The Infoblox team then analyzed the identified malicious domains to determine whether they had been identified earlier by our suspicious domain feeds.
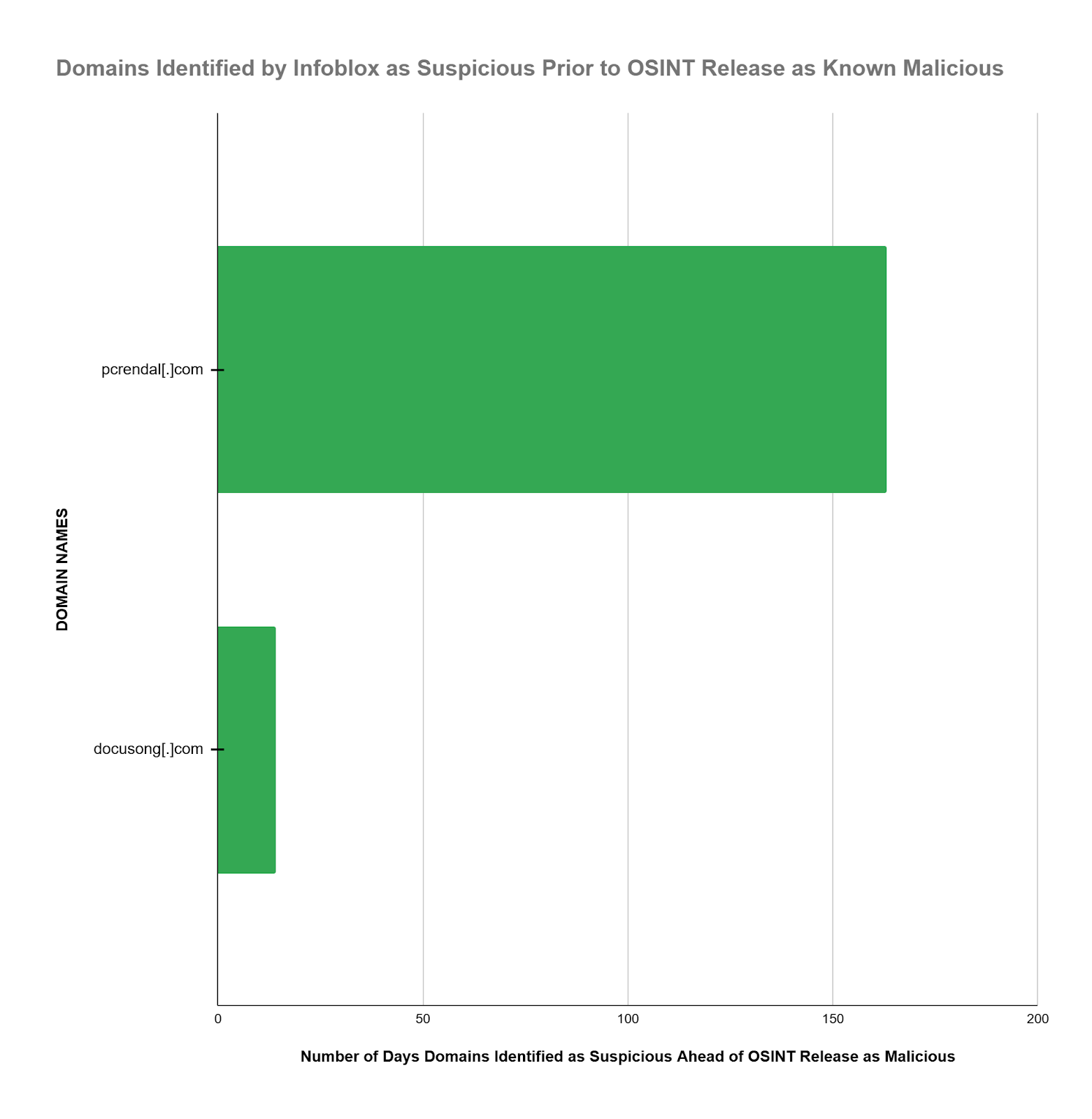
| Infoblox identified both key Blackcat C&C domains as SUSPICIOUS days to months ahead of availability in OSINT as MALICIOUS. In one case, for pcrendal[.]com, we declared and blocked the C&C domain as suspicious 163 days before OSINT availability as known malicious. |
The Blackcat threat has been active long before the release of the OSINT data. Given the long-term activity of the Blackcat threat actors, we believe it is highly likely that the threat actors were already ramping up activity shortly after our suspicious designations and long before visibility to the public at large via OSINT availability.
The conclusions of our analysis illustrate the potential benefits of SUSPICIOUS domain feeds in identifying both key C&C domains which CISA identified in their February 27 alert:
- Pcrendal[.]com was identified as SUSPICIOUS and BLOCKED 163 days before OSINT availability as one of the key MALICIOUS C&C domains
- Docusong[.]com was identified as SUSPICIOUS and BLOCKED 14 days before OSINT availability as one of the key MALICIOUS C&C domains
- Our DNS early detection program identifies suspicious domains weeks to months, as in this case, ahead of OSINT identification as MALICIOUS
- There is often an extended period of time from availability via OSINT to utilization by your cybersecurity ecosystem and defense-in-depth strategy. Infoblox designation of suspicious domains can link to automation to block them immediately.
OSINT publication dates may sometimes be unclear or lack precision. The dates of published articles by reputable 3rd parties may not always accurately reflect the OSINT availability of each domain. The critical point is that even if you have the OSINT data, it must propagate through the threat feeds you use and your cybersecurity ecosystem to support actionable policies. All of that is automated with Infoblox DNS Detection and Response (DNSDR) and our suspicious domain data.
| Infoblox’s DNS Early Detection Program uses proprietary techniques to identify potentially malicious domains quickly. Infoblox flags these domains as suspicious so your defenders can automatically block them. |
Comparison to WHOIS Data
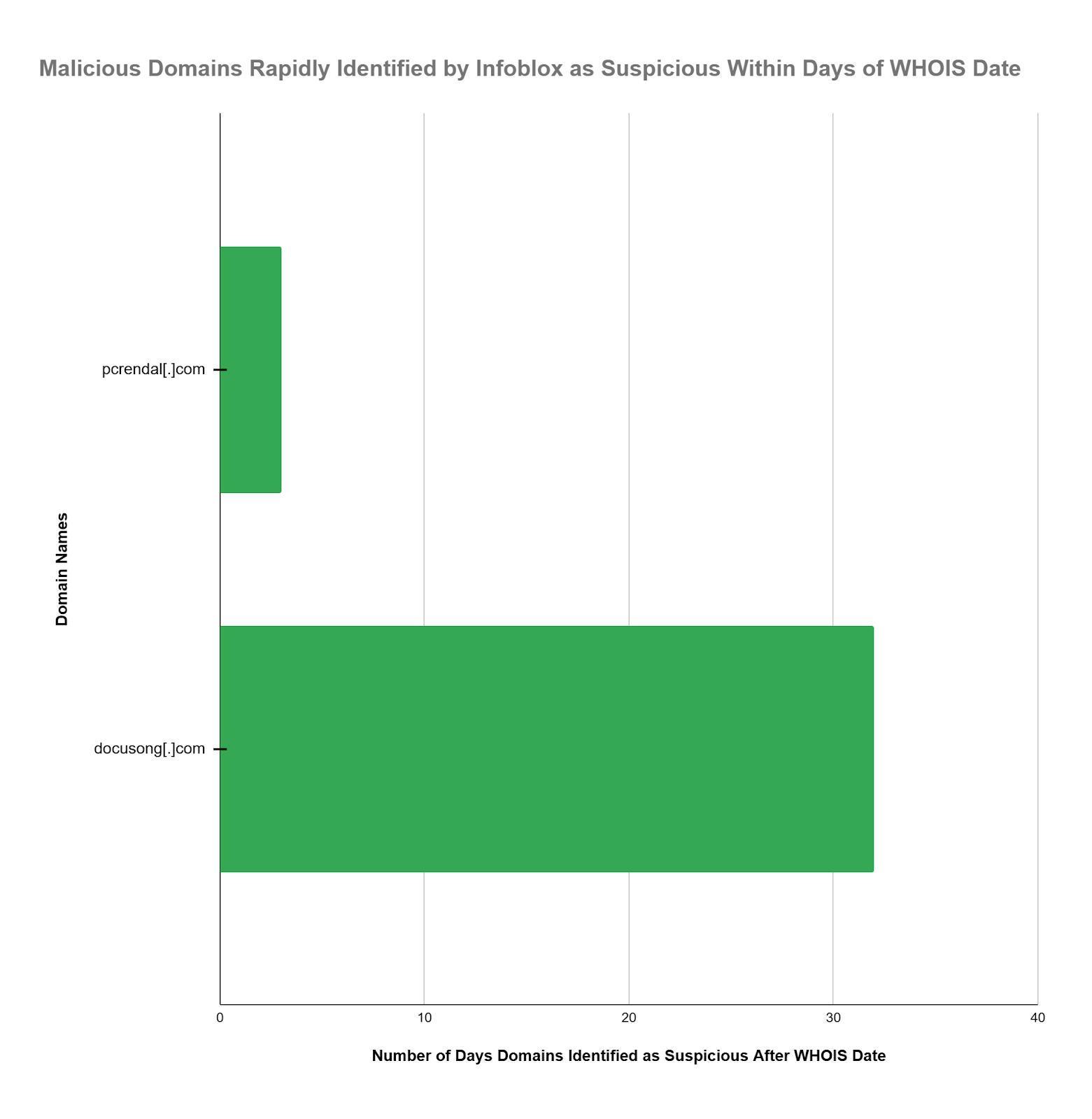
OSINT data release dates are approximate. Determining when a specific IoC was released into OSINT can be difficult. WHOIS records are much more precise and present hard data on when a malicious domain was first available. A comparison with WHOIS data tells you how well your threat intelligence systems work. To provide context on the performance of our suspicious threat intel feeds, we extracted WHOIS dates and found that pcrendal[.]com was blocked as suspicious within 3 days after the WHOIS domain registration date. The WHOIS dates are relatively precise and provide another perspective on the high value and relative performance of suspicious DNS threat intel feed content.
Similarly, Docusong[.]com was blocked as suspicious 32 days after the WHOIS domain registration date.
| Infoblox regularly identifies suspicious domains within 2 to 3 days of WHOIS registration. This enables our customers to stop the execution of the intended Cyber Kill Chain by automatically blocking access to these dangerous domains. |
The threat actors behind most campaigns have learned to continually create and change the domains they use to camouflage their malicious activities. Any key domains used in perpetuating the Blackcat campaigns may be shut down at any time and replaced with new infrastructure. This is almost always part of the threat actor’s planning.
Suspicious Domains Can Bring High Value to Your Threat Intel Program
Infoblox DNS Early Detection using our suspicious feeds can help your SOC to identify and block potentially dangerous threats such as Blackcat ransomware faster. Infoblox Threat Intel proprietary technology can detect suspicious domains faster than the industry’s current methods. It can help protect your organization from a disastrous data breach.
| Infoblox Threat Intel SUSPICIOUS domain data is HIGH VALUE, can be used with relatively LOW EFFORT, and can SHRINK THE TIME TO VALUE, and INCREASE THE RETURN ON INVESTMENT for your threat intelligence program. |
Suspicious domain feeds provide a significant advantage in developing and using DNS threat intelligence information. With Infoblox’s suspicious domain data, security operations teams can get the timely information they need to prevent and counter new threats before they do any damage.
MITRE ATT&CK Enterprise Techniques – Blackcat Ransomware
| Technique Title | ID | Use |
| RECONNAISSANCE | ||
| Phishing for Information | T1598 | Blackcat ransomware affiliates pose as company IT and/or helpdesk staff using phone calls or SMS messages to obtain credentials from employees to access the target network. |
| RESOURCE DEVELOPMENT | ||
| Compromise Accounts | T1586 | Blackcat ransomware affiliates use compromised accounts to gain access to victims’ networks. |
| CREDENTIAL ACCESS | ||
| Obtain Credentials from Passwords Stores | T1555 | Blackcat ransomware affiliates obtain (steal!) passwords from local networks, deleted servers, and domain controllers. |
| Steal or Force Kerberos Tickets | T1558 | Blackcat ransomware affiliates use Kerberos token generation for domain access. |
| Adversary (Man)-in-the-Middle | T1557 | Blackcat ransomware affiliates use the open-source framework Evilginx2 to obtain MFA credentials, login credentials, and session cookies for targeted networks. |
MITRE ATT&CK data sourced from:
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-353a
For Additional Information
The Infoblox Threat Intel Group provides fast access to accurate, contextual threat alerts and reports from our real-time research teams. Suspicious Domains feeds were introduced as an Infoblox proprietary product on November 10, 2022, and, since then, have successfully provided many thousands of customers with the advanced information to block domains that ultimately become malicious long before most other threat intelligence sources identify them as malicious. Infoblox allows your team to leverage the high value of suspicious domain threat intelligence while ensuring a unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
To learn more about suspicious domains and DNS early detection: https://www.infoblox.com/cyber-threat-intelligence/
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
To learn more about Advanced DNS Protection:
https://www.infoblox.com/products/advanced-dns-protection/
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF
OSINT sources on Blackcat Ransomeware included, but were not limited to:
Footnotes
- https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html Cyber Kill Chain is a registered trademark of Lockheed Martin.