Ransomware attacks continue to be a significant threat worldwide, with victims facing average ransom demands of .5 million in 2024. A report has identified 10 of the most active ransomware families and detailed a total of 120 indicators of compromise (IoCs) associated with these variants, including domains and IP addresses. The investigation revealed numerous malicious entities and connections to ongoing threats. Affected: ransomware victims, cybersecurity sector
Keypoints :
- Ransomware continues to plague users and organizations globally, with hefty ransom demands.
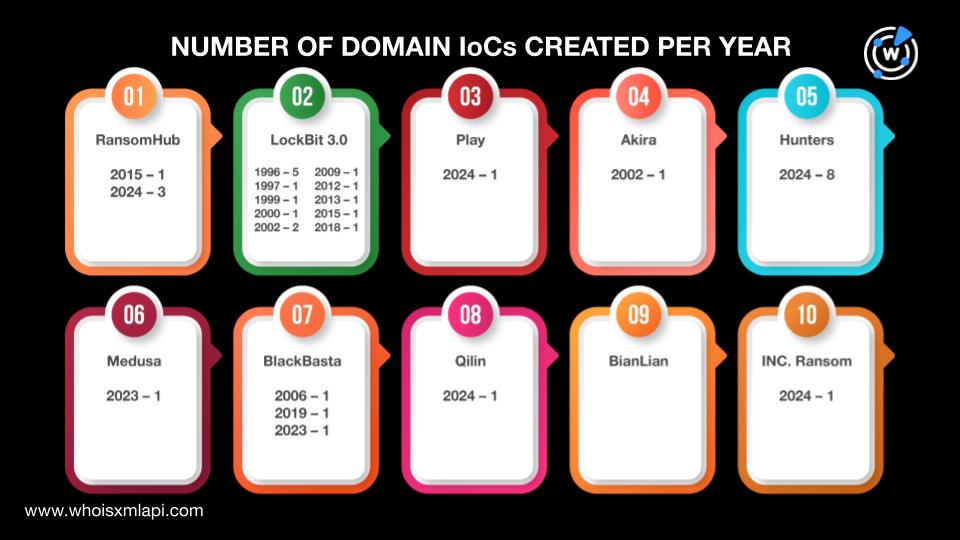
- A report identified 10 active ransomware families for 2024, revealing significant IoCs.
- A total of 120 IoCs were identified, including 48 domains and 72 IP addresses.
- Further analysis expanded the IoC list, uncovering additional email-connected domains and IP addresses linked to malicious activities.
- Existing connections to historical records provided insights into the origins and registrations of the identified IoCs.
MITRE Techniques :
- TA0001 – Initial Access: The malware uses phishing emails to gain access to victim systems.
- TA0011 – Command and Control: Compromised systems connect to malicious command-and-control servers for further instructions.
- TA0009 – Command Line Interface: Ransomware often utilizes command line interfaces to execute tasks.
- TA0040 – Impact: The ransomware encrypts files on the victim’s system, demanding payment for decryption.
Indicator of Compromise :
- [Domain] malicious-domain[.]com
- [Domain] capsonic[.]com
- [IP Address] 104[.]86[.]182[.]8
- [IP Address] 209[.]197[.]3[.]8
- [Email Address] aaeieiiiofffpn[.]su
Full Story: https://circleid.com/posts/dns-deep-diving-into-2025s-up-and-coming-ransomware-families