Early in May 2024, S2 Grupo’s intelligence unit, Lab52, detected a new phishing campaign in which attackers impersonated the Colombian Attorney General’s Office. The attack aims to infect victims’ systems with the generic malware artefact AsyncRAT. To do so, it deploys a series of malicious files, including the legitimate file of the free IObit anti-malware solution used to execute the rest of the artefacts and initiate the infection using the DLL side-loading technique.
Although the beacon, the objectives, and the artefacts used by the attackers match with those known to be used by APT-C-36, the kill-chain does not correspond with the one used by the actor in their latest campaigns. Therefore, this could mean a modification of their Tactics, Technics, and Procedures.
This time, the threat actor employs a ZIP file containing four relevant documents: an IObit antivirus legitimate file, a malicious BPLfile, which is a type of DLL for AutoCAD, a malicious M4A file which is an Apple audio file, and a malicious VCF text format file. The attackers use the HijackLoader malware to execute the malicious artefacts.
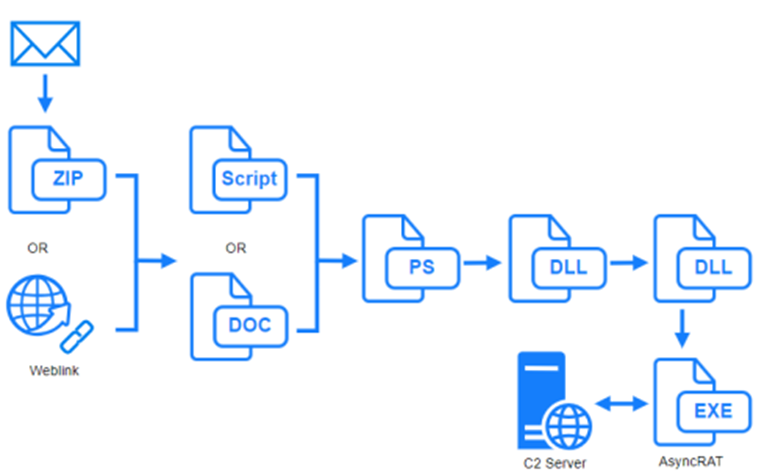
The following figure represents the infection chain employed by the APT-C-36 threat actor in recent years, as explained in this Lab52 publication.
The figure below shows two decoys used by the attackers. On the left, is the decoy used in the new campaign discovered by Lab52. On the right, is an APT-C-36 campaign from July 2022.

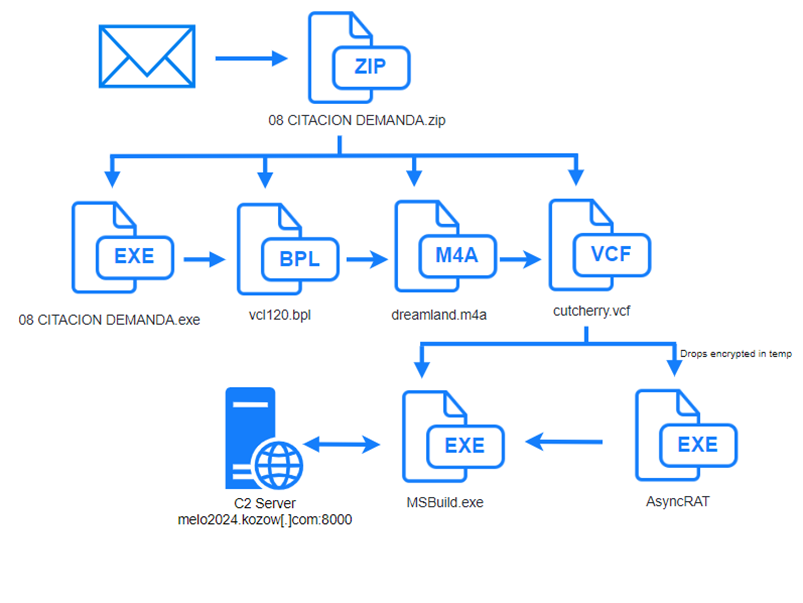
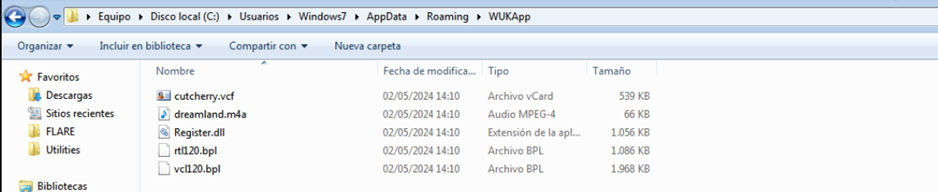
The infection starts with the file “08 CITACION DEMANDA.zip” which contains the files: a legitimate executable signed as IObit RttHlp “08 CITACION DEMANDA.exe”, “Register.dll”, “vcl120.bpl”, “dreamland.m4a” and “cutcherry.vcf” and on execution, all files, except for the executable are copied to C:UsersXXXXAppDataRoamingWUKApp.
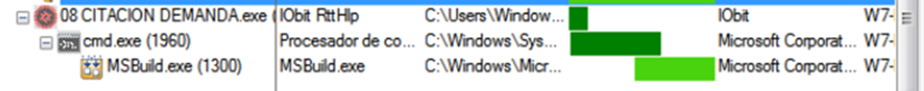
In the same way as other HijackLoader infections, the first-stage executable “08 CITACION DEMANDA.exe” loads the malicious DLL “vcl120.bpl” through DLL Side Loading. Then, the DLL creates a cmd.exe process that starts a suspended MSBuild process.
The loader manages the process explained above through the files contained in the zip. It will deobfuscate and use “dreamland.m4a” in order to inject a shellcode into memory. It will then perform the same process with “cutcherry.vcf”. Finally, the loader injects into the previously created “MSBuild.exe” the AsyncRAT contained in “cutcherry.vcf” via Process Hollowing. The communications with the C2 were detected through this process.
During the execution process, we managed to detect the use of the mutex AsyncMutex_6SI8OkPnk and the creation of other processes, such as a PowerShell:
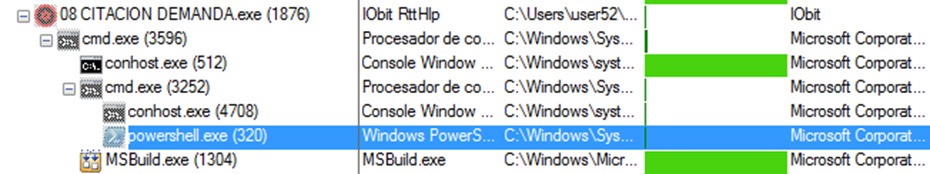
In order to obtain persistence, the attackers followed through with two different mechanisms that load the executable file uncopied before to the secondary folder. In the first place, via the creation of a link file on the user’s home folder “chromeHttp_zx_test”.

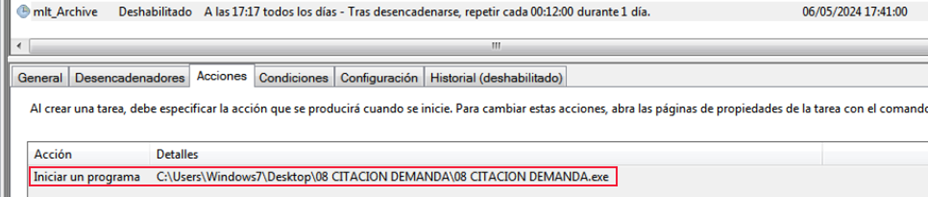
Furthermore, the attackers also created a scheduled task called “mlt_Archive”:
This article analyses a new campaign detected in Colombia. In this campaign, we found several similarities with previous decoys and malware used by APT-C-36. Therefore, we might find ourselves before a new kill-chain used by this group.
As a side note, campaigns using RATs, such as AsyncRAT, are commonly found in attacks against Colombian entities as we analysed in our previous blog.
| 08 CITACION DEMANDA.zip | ab731fe108986f53117e09272f12701a77e013d8 |
| 08 CITACION DEMANDA.exe | 22afcdc180400c4d2b9e5a6db2b8a26bff54dd38 |
| cutcherry.vcf | 931c51eed1716a0dddeb005899efd16a79a22782 |
| dreamland.m4a | a31edd70cb923893c736b633806e294a66ffbd41 |
| Register.dll | 8fb5da182dea64c842953bf72fc573a74adaa155 |
| rtl120.bpl | e6ccaf016fc45edcdadeb40da64c207ddb33859f |
| vcl120.bpl | 1e387320704c8b94c41df2409e79c67a030018c4 |
Source: https://lab52.io/blog/dll-side-loading-through-iobit-against-colombia/