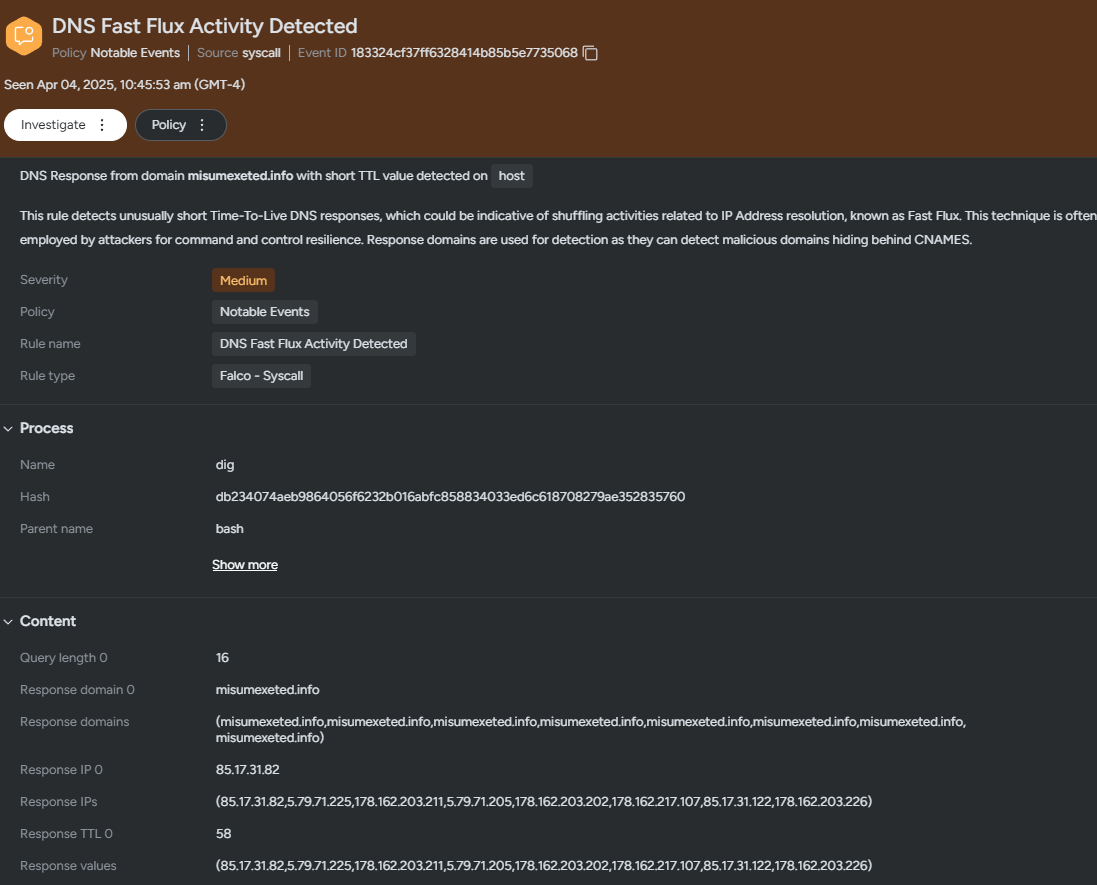
The article discusses Fast Flux, a technique used by attackers to obfuscate their infrastructure by rapidly changing the IP addresses associated with a domain name. It explains the implications of this attack method, outlines how Sysdig Secure detects it, and emphasizes the need for a layered defense strategy using tools like Sysdig. Affected: DNS, Cybersecurity, Malware, Cloud Security
Keypoints :
- Fast Flux is a technique that shuffles IP addresses of domain names to hide attacker infrastructure.
- This technique sets a short Time To Live (TTL) value for DNS records, commonly at 5 minutes or less.
- Attackers use Fast Flux to evade IP blocklists and maintain the availability of their Command and Control (C2) infrastructure.
- Sysdig Secure can detect Fast Flux activities through advanced DNS inspection techniques.
- Detection is triggered when domains have low TTLs and resolve to multiple IP addresses.
- Sysdig Secure has offered detection capabilities for Fast Flux since October 2024.
- Indicators of Compromise (IoCs) from VirusTotal can be used to assist in detecting Fast Flux domains.
- A layered defense strategy is essential for preventing Fast Flux attacks.
- Utilizing Protective DNS services can enhance overall DNS security.
MITRE Techniques :
- T1071 – Application Layer Protocol: Attackers use this technique for communication with the Fast Flux servers.
- T1071.001 – Application Layer Protocol: Web Protocols: Specifically utilized through DNS protocols for the rapid IP address changes.
- T1075 – Pass the Hash: Used indirectly when shifting IPs to maintain connections with compromised systems.
Indicator of Compromise :
- [Domain] a_ttl:300 (malware category)
- [Domain] from VirusTotal indicating suspected Fast Flux activity
- [URL] http://malicious.com/path
- [URL] https://example.com
- [IP Address] 192.168.1.1
Full Story: https://sysdig.com/blog/detecting-fast-flux-with-sysdig-secure-and-virustotal/