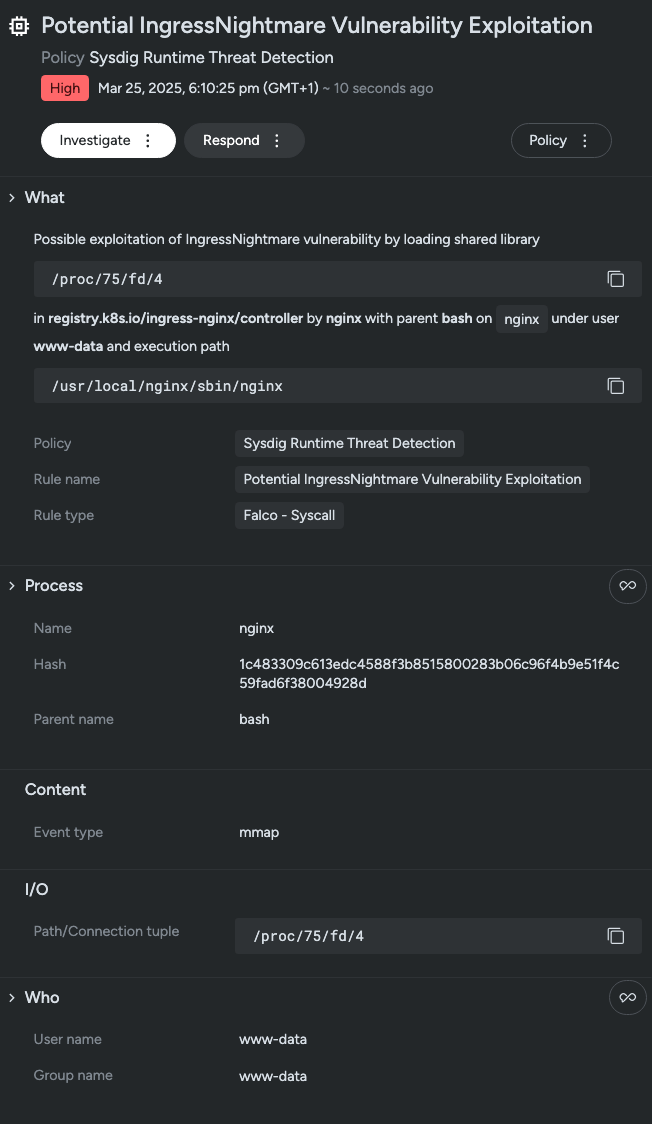
A set of critical vulnerabilities, including CVE-2025-1974, affecting the Ingress NGINX Controller in Kubernetes was disclosed, posing severe threats such as remote code execution. Organizations are encouraged to mitigate these risks by promptly upgrading to the latest versions of the NGINX Controller and securing admission webhook endpoints. Affected: Ingress NGINX Controller, Kubernetes, Cloud Services (Amazon EKS, Google GKE)
Keypoints :
- Five vulnerabilities were announced for the Ingress NGINX Controller for Kubernetes.
- CVE-2025-1974 (CVSS 9.8) is critical, allowing unauthenticated remote command execution.
- Other vulnerabilities include configuration injection and path traversal issues.
- Access to the NGINX Ingress Controller can be exploited if publicly exposed.
- An attacker can gain cluster-wide access through the exploitation of these vulnerabilities.
- Mitigation includes upgrading to versions v1.11.5 and v1.12.1 or later.
- Detection rules are available for users of Sysdig Secure and Falco.
MITRE Techniques :
- Remote Code Execution (T1203) – Exploitation of vulnerability CVE-2025-1974 allows attackers to run arbitrary commands.
- Command and Control (T1071) – Use of crafted ingress objects to manipulate the NGINX admission controller.
- Credential Dumping (T1003) – Potential to extract secrets from the Kubernetes cluster.
- Privilege Escalation (T1068) – Exploiting elevated permissions in the cluster via compromised ingress controller.
Indicator of Compromise :
- [Domain] ingress-nginx-controller.example.com
- [Hash] 3fd9e1a5e3a9a7fe5e4e8d942e2a76f1 (hypothetical shared library example)
- [IP Address] 192.168.1.100
- [URL] http://malicious[. ]com/exploit_payload
- [Email Address] attacker@example[. ]com
Full Story: https://sysdig.com/blog/detecting-and-mitigating-ingressnightmare-cve-2025-1974/