09/04/2024
A sophisticated malicious campaign is currently underway, aimed at compromising Android devices in Italy through the SpyNote malware. This is disguised as the “INPS Mobile” application, available for download on a specifically created domain yesterday, with the aim of deceiving victims.
The phishing page, reported by D3lab to CERT-AGID, is carefully designed with logos and content that reproduce the official ones of the Institute. Furthermore, it offers a meticulously elaborated guide on the home page for downloading and installing the fake “INPS Mobile” application.
App Installation
The victim who follows the false instructions and presses the “Download” button receives an APK file on their device. Once installed, this file requires an update and prompts for certain permissions. Finally, the application shows the real INPS website page.

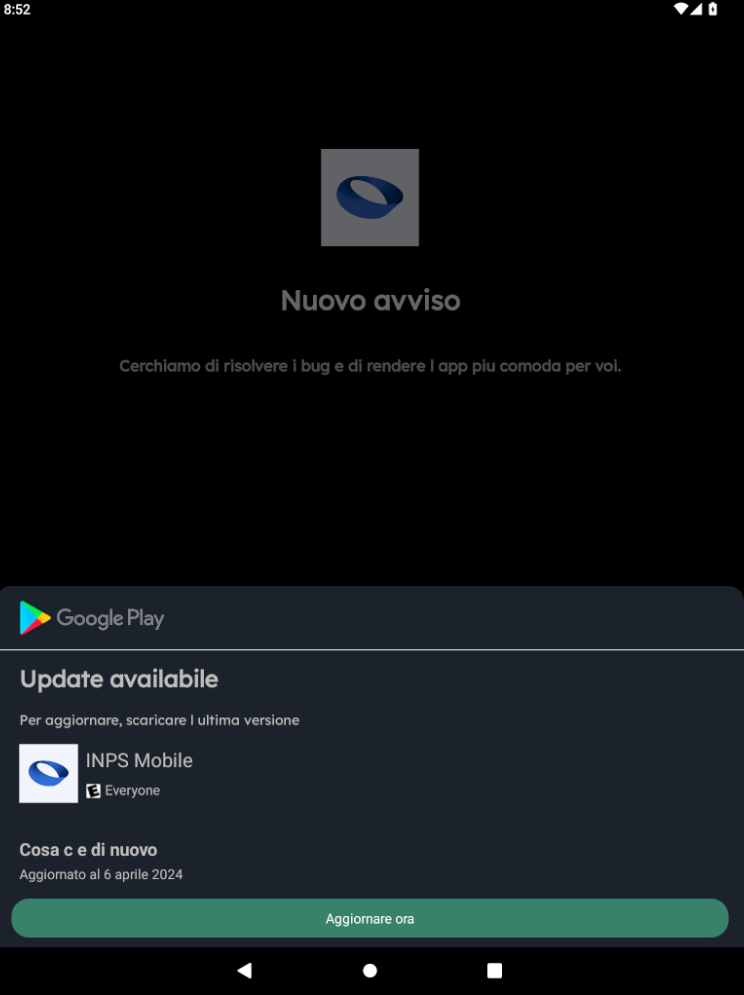
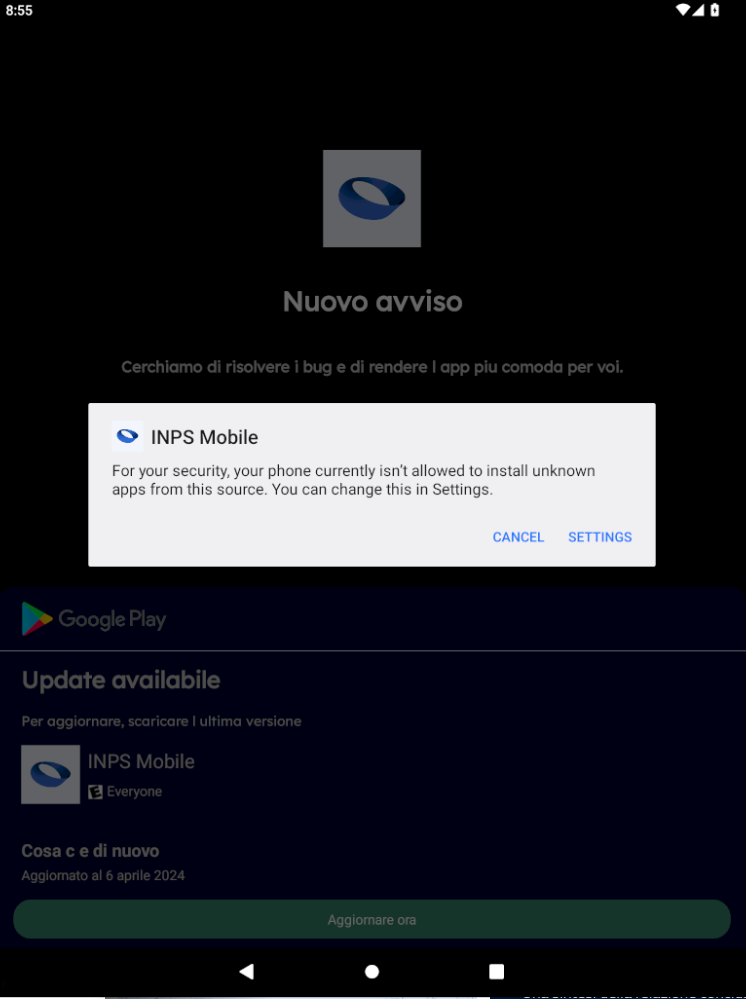
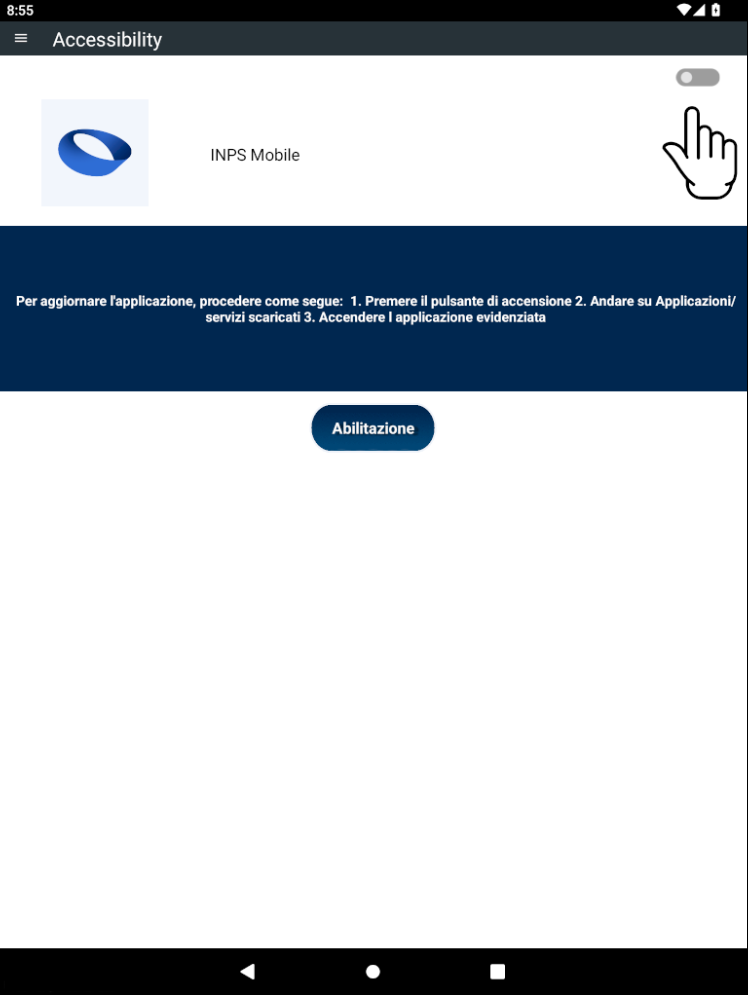
What happens on the device?
The application incorporates a sequence of strings, decipherable through a series of nested functions, necessary to obtain the keys of the AES algorithm used to encrypt the instructions. The following Java code is illustrated for decrypting the strings:
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
public class MyClass {
public static String m103(String str, String str2) {
byte[] bArr;
byte[] bArr2;
int length = str.length();
if (length % 2 == 1) {
length++;
bArr = new byte[(length / 2)];
str = "0" + str;
} else {
bArr = new byte[(length / 2)];
}
int i = 0;
for (int i2 = 0; i2 < length; i2 += 2) {
bArr[i] = (byte) ((byte) Integer.parseInt(str.substring(i2, i2 + 2), 16));
i++;
}
try {
SecretKeySpec secretKeySpec = new SecretKeySpec(str2.getBytes(), "AES");
Cipher instance = Cipher.getInstance("AES");
instance.init(2, secretKeySpec);
bArr2 = instance.doFinal(bArr);
} catch (Exception e) {
e.printStackTrace();
bArr2 = null;
}
return new String(bArr2);
}public static String m0(String str, String str2) {
byte[] bArr;
byte[] bArr2;
int length = str.length();
if (length % 2 == 1) {
length++;
bArr = new byte[(length / 2)];
String m254 = MyClass.m103("12202599d2de5887e30d8b7ebde8ec45", "67c48674e8b8c7f5");
str = m254 + str;
} else {
bArr = new byte[(length / 2)];
}
int i = 0;
for (int i2 = 0; i2 < length; i2 += 2) {
bArr[i] = (byte) ((byte) Integer.parseInt(str.substring(i2, i2 + 2), 16));
i++;
}
try {
// m264 = m303
String m264 = MyClass.m103("0bcc2afe4d25a75b7b7f228ab7a2d6b3", "67c48674e8b8c7f5");
String m303 = MyClass.m103("0bcc2afe4d25a75b7b7f228ab7a2d6b3", "67c48674e8b8c7f5");
SecretKeySpec secretKeySpec = new SecretKeySpec(str2.getBytes(), m303);
Cipher instance = Cipher.getInstance(m264);
instance.init(2, secretKeySpec);
bArr2 = instance.doFinal(bArr);
} catch (Exception e) {
e.printStackTrace();
bArr2 = null;
}
return new String(bArr2);
}
public static void main(String args[]) {String m142 = MyClass.m103("61ba9f85d95954b587cce057a4be58d5eae702a96d475e3103c1e23c8c95e72b6658928e145ea1a7499164cce5c1fc4c2ba845e669a73a01b0d41a1be7fde78f211df4d284f17a693118108a825acacc", "9080bea66a356436");
String m416 = MyClass.m103("9a184fa0d30ce94a06261e280c5108b350c1b3e6bb00550de77cb3cd4e7b9000", "0ec47edd8db3a02b");
String m45 = MyClass.m0(m142, m416);
System.out.println(m45);
}
}
This APK serves as a cover to hide the real malware. Once installed on the
Source: Original Post
Views: 0