
EXECUTIVE SUMMARY
At CYFIRMA, our mission is to empower you with the latest insights into the dynamic landscape of cybersecurity threats, addressing risks that impact both organizations and individuals. This report details a sophisticated cyber threat involving a malicious Word file with an embedded macro that, upon opening, prompts victims to enable macros. Once activated, the macro initiates a series of actions, including the creation and deployment of VB scripts, BAT scripts, and the extraction of conhost.zip onto the victim’s machine. This process culminates in the installation of final payload Nim backdoor. The primary objective of this backdoor is to establish a connection with the adversaries’ command and control (C2) server, facilitating unauthorized access. The malicious document, along with the Nim backdoor as its final payload, is attributed to the Sidewinder group (also known as Rattlesnake, BabyElephant, APT Q4, APT Q39, Hardcore Nationalist, HN2, RAZOR Tiger, and GroupA21). Based on available information, the Sidewinder group is believed to originate from South Asia. The group activities can be traced back to 2012. The group typically focuses its attacks on governmental and military entities in various South Asian nations.
INTRODUCTION
This report delves into a recent campaign involving a malicious Word document equipped with an embedded macro, unravelling a sophisticated cyber threat orchestrated by the Sidewinder group possibly to target Nepalese government officials. The threat begins with a potentially spear-phished email delivering a malicious Word document. After download and upon opening the document, the embedded macro executes, manipulating victims into enabling macros. This triggers a complex sequence of events, involving the creation and execution of various scripts and the establishment of persistence mechanisms. The analysis uncovers a multi-stage attack designed to hide activities, establish persistence, and execute malicious payloads.
Through the careful analysis of the embedded macro, this report exposes the intricacies of the attack chain, shedding light on the creation and deployment of VB scripts, BAT scripts, and the extraction of a concealed payload, conhost.exe, exhibiting similarities with the Nim backdoor. Conhost.exe, the primary payload, serves as a gateway for unauthorized access, connecting to the adversary’s Command and Control (C2) server. As part of the Sidewinder group’s broader strategy, the campaign involves the deployment of a reverse shell, adding a layer of complexity to their malicious operations.
Throughout this report, we provide an in-depth exploration of the attack’s technical aspects, shedding light on the functionalities of each component of the malware. Our objective is to equip cybersecurity professionals, organizations, and individuals with a comprehensive understanding of the threat landscape, enabling them to enhance their defenses and proactively mitigate the risks posed by sophisticated threat actors like the Sidewinder group.
KEY POINTS
- Analysis of a highly sophisticated cyber threat involving a malicious Word document with an embedded macro possibly targeting Nepalese government officials.
- The threat, including the Nim backdoor payload, is linked to the Sidewinder group, suggesting a South Asian origin and a history of malicious activities dating back to 2012.
- Detailed breakdown of the attack chain initiated by a malicious Word document, emphasizing victim manipulation to enable macros. The sequence includes the deployment of VB scripts, BAT scripts, and the extraction of final payload.
- The final payload, Nim backdoor (conhost.exe), serves as a gateway for unauthorized access, can connect to the adversaries’ Command and Control (C2) server.
- The malware’s functionality highlights its obstruction of dynamic analysis by detecting and exiting upon identification of analysis tools, showcasing a proactive defense mechanism employed by threat actors.
- These key findings present a nuanced perspective on the cyber threat, from its origin and tactics to the potential impact on cybersecurity defenses.
ETLM ATTRIBUTION
The threat landscape presented by the sophisticated Sidewinder APT group highlights a highly skilled and persistent adversary that, in this instance, has orchestrated a targeted campaign against the Nepalese Government. While their focus extends beyond Nepal, encompassing various South Asian government entities, the recent attack showcased a particularly intricate strategy. Researchers have recently identified similar attacks targeting Bhutan.
The group’s modus operandi involves the deployment of decoy malicious documents, adeptly camouflaged as communications from the Nepalese Prime Minister’s Office. This deceptive tactic underscores the advanced nature of the threat, employing a spectrum of techniques, including email spear-phishing and the exploitation of malicious macros within documents. The urgency of this situation necessitates swift attention and coordinated action from relevant stakeholders.
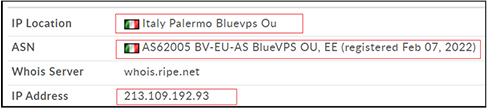
As per the OSINT investigation, all the URLs hardcoded in main payload conhost.exe (Nim Backdoor) resolved to IP address “213[.]109[.]192[.]93”.
- http[:]//mail[.]mofa[.]govnp[.]org/mail/AFA/
- http[:]//nitc[.]govnp[.]org/mail/AFA/
- http[:]//dns[.]govnp[.]org/mail/AFA/
- http[:]//mx1[.]Nepal[.]govnp[.]org/mail/AFA/

IP hosting a C2 server in Italy on BlueVPS having ASN no. AS62005.
The server is Apache and Metasploit running on port 3790 for remote connection open.


Believed to originate from South Asia, the suspected Sidewinder APT group has a historical footprint targeting diverse sectors such as Government, Military, Education, Healthcare, ISP, and Telecommunication across Asia. Known by various aliases like Rattlesnake, Hardcore Nationalist, HN2, APT Q4, RAZOR Tiger, APT Q39, BabyElephant, and GroupA21, their persistent and evolving tactics pose a substantial risk to regional cybersecurity. The comprehensive analysis provided in this report aims to enhance awareness and preparedness against the multifaceted and dynamic nature of cyber threats orchestrated by the Sidewinder APT group.
ANALYSIS:
Basic Details:
MD5: E5859B366B93B05414E1E95D65CE7414
SHA256: 7459a6106d3562d72c7a4fee62d106064a3ed5b48e16474da2b448aeacc2a333
File Type: Office Open XML Document (Microsoft Word Document)
The potentially spear-phished email delivers a malicious document. Upon opening this document, the embedded malicious macro is triggered and executed. The manipulation of the victim occurs as the document prompts them to enable editing as shown below:

The deceptive content found in the sample appears to be associated with the Nepalese government, potentially indicating a focus on Nepalese government officials as the target.

Upon investigation, it was determined that the document contains an embedded macro. Subsequently, the macro was extracted for further analysis. The macro appears to be a part of a multi-stage attack, designed to establish persistence, hide its activities, and execute malicious payloads.

The Document_Open subroutine is executed when the document is opened. When the victiim opens the document, it automatically calls four functions (sch_task, hide_cons, read_shell, vb_chain) responsible for different aspects of the malicious behavior.

sch_task function performs several actions; it sets up environment variables and paths, creates a VBScript file (OCu3HBg7gyI9aUaB.vbs) in the Startup folder (C:UsersUserNameAppDataRoamingMicrosoftWindowsStart MenuProgramsStartup) for persistence.

Firstly, the function leverages the GetObject method to create a WScript.Shell object, a common technique in malware for executing commands. It dynamically retrieves system environment variables such as AppData, LocalAppData, and Temp to construct file paths. Subsequently, a VBScript file (OCu3HBg7gyI9aUaB.vbs) is generated within the user’s startup directory, fostering persistence and ensuring execution upon subsequent system reboots. The script introduces deliberate delays, exemplified by WScript.Sleep 300000, a tactic employed to evade immediate detection and analysis.

Following is the code snippet for “OCu3HBg7gyI9aUaB.vbs” file, which was created by “sch_task” function:

The script introduces sleep delays, likely to avoid immediate detection. It checks internet connectivity by pinging Google. Depending on the result, it either sets an object to Nothing and runs the batch file (81Ghf8kIPIuu3cM.bat) or directly runs the batch file after another sleep delay.
The subsequent execution of an encoded batch file (8lGghf8kIPIuu3cM.bat) further exemplifies the obfuscation techniques employed to conceal the true intent of the script. Following is the code snippet for “8lGghf8kIPIuu3cM.bat” file.

The batch script (8lGghf8kIPIuu3cM.bat) performs several actions, including extracting and executing VBScript files, creating scheduled tasks, and self-deleting files. The batch script is orchestrating the execution of VBScript files (unzFile.vbs, skriven.vbs) and other batch files (2L7uuZQboJBhTERK.bat, 2BYretPBD4iSQKYS.bat, d.bat, e.bat). It sets up a scheduled task (ConsoleHostManager) that runs conhost.exe every minute. After completing its tasks, it attempts to clean up by deleting the created files.
Read_shell function reads bytes from a UserForm text box, splits them, and writes them to a binary file (conhost.zip) in the user’s local application data folder (C:UsersUserNameAppDataLocalMicrosoft).

It is designed to take binary data from a user interface component (UserForm1) and write it to a binary file named “conhost.zip” in the Microsoft folder within the local application data directory.

hide_cons function creates a VBScript file (skriven.vbs) in the local application data folder (C:UsersdilpreetAppDataLocal). The hide_cons function appears to be creating a VBScript file (skriven.vbs), that, when executed, hides the console window (cmd.exe).

Following is the code snippet for “skriven.vbs” file:

The code is configured to hide the window of the executed program, and the script does not wait for the command to complete before continuing. The purpose of this mechanism may be to run a command discreetly without displaying the command prompt or any associated window. The specific command that gets executed is determined by the value passed as a command-line argument (WScript.Arguments(0)). The script takes the command as an argument and runs it using the Windows Script Host Shell object, while hiding the window of the executed program.
Another function from the macro, the vb_chain is responsible for orchestrating a series of actions, including creating and executing multiple scripts and scheduling tasks. The purpose of this function within the context of a malicious document is to establish a chain of events that likely includes downloading, extracting, executing files, and scheduling tasks on the infected system.
The function initializes objects and variables, including the Windows Script Host Shell object (objShell), the FileSystemObject (objFSO), and various file paths. It creates several files (unzFile.vbs, 2L7uuZQboJBhTERK.bat, etc.) with specific content written to each. The created batch files (2L7uuZQboJBhTERK.bat, 2BYretPBD4iSQKYS.bat, etc.) are executed using wscript.exe. It schedules a new task using schtasks to execute conhost.exe (extracted from cohost.zip file) after a minute.

unzFile.vbs VBScript file is responsible for extracting the contents of conhost.zip to a specified folder. The purpose is to unzip the contents of conhost.zip and make them accessible for further actions.
2L7uuZQboJBhTERK.bat batch file executes unzFile.vbs using wscript.exe, and then it executes skriven.vbs with 2BYretPBD4iSQKYS.bat as an argument. The purpose is to initiate the unzipping process and subsequently execute another script (skriven.vbs).
2BYretPBD4iSQKYS.bat batch file executes unz.vbs and then executes skriven.vbs with d.bat as an argument. D.bat batch file creates a scheduled task (ConsoleHostManager) to execute conhost.exe after a minute. Afterward, it executes skriven.vbs with e.bat as an argument. E.bat batch file is for cleanup purposes. It deletes unnecessary files (unzFile.vbs, 2L7uuZQboJBhTERK.bat, 2BYretPBD4iSQKYS.bat, d.bat, and e.bat itself). The final line executes the main VBScript (skriven.vbs) with an argument, initiating the execution chain.
Macro code exhibits advanced evasion techniques, leveraging VBScript, batch files, and scheduled tasks to achieve its objectives. The use of obfuscation and multi-stage execution makes it challenging to analyze and detect. The overall intent seems to be to establish persistence, hide malicious activities, and execute potentially harmful payloads on the victim’s system.
When victim opens the malicious Word file, victims are urged to enable macros, triggering the creation and deployment of VB scripts, BAT scripts, and the extraction of conhost.zip. This results in the installation of conhost.exe, mirroring Nim backdoor characteristics. Conhost.exe aims to connect to the adversaries’ C2 server for unauthorized access.
Following are the details related to “conhost.exe” file which is Nim Backdoor providing unauthorized access to the threat actors.
MD5: 777fcc34fef4a16b2276e420c5fb3a73
SHA256: 696f57d0987b2edefcadecd0eca524cca3be9ce64a54994be13eab7bc71b1a83
The sample file is 64-Bit PE executable having compiled time Sept-23, which is quite recent and indicates that campaign is running since September, as other file samples also are detected in the same period.

As per the OSINT investigation, the sample mentioned as reverseshell used to provide access to threat actors. Malicious actors frequently utilize a reverse shell as a strategy to illicitly obtain control over a compromised system. The reverse shell facilitates a connection from the victim’s machine to an external server under the attacker’s control. This establishes a backdoor entry, granting the malicious actor the ability to execute commands, transfer files, and potentially carry out additional attacks without direct engagement with the compromised system.

This trojan.khalesi family consists of malicious software that obstructs dynamic analysis. This software checks the environment for dynamic analysis tools and exits if they are found and same behaviour we noticed in the sample. The malicious binary detects various monitoring, malware analysis, network monitoring, debuggers and other analysis tools which include processhacker.exe, procmon.exe, pestudio.exe, procmon64.exe, x32dbg.exe, x64dbg.exe, CFF Explorer.exe, procexp64.exe, procexp.exe, pslist.exe, tcpview.exe, tcpvcon.exe, dbgview.exe, RAMMap.exe, RAMMap64.exe, vmmap.exe, ollydbg.exe, agent.py, autoruns.exe, autorunsc.exe, filemon.exe, regmon.exe, idaq.exe, idaq64.exe, ImmunityDebugger.exe, Wireshark.exe, dumpcap.exe, HookExplorer.exe, ImportREC.exe, PETools.exe, LordPE.exe, SysInspector.exe, proc_analyzer.exe, sysAnalyzer.exe, sniff_hit.exe, windbg.exe, joeboxcontrol.exe, joeboxserver.exe, ResourceHacker.exe, Fiddler.exe, httpdebugger.exe as shown below.

The following is the process tree corresponding to binary. The command “C:Windowssystem32cmd.exe /c tasklist.exe” indicates that the Windows Command Prompt (cmd.exe) is being used to execute the tasklist.exe command periodically. The /c switch in cmd.exe is used to carry out the command specified and then terminate. Here, the Command Prompt is invoked to run the tasklist.exe command, which lists all running processes on the system. The overall purpose of this command could be to retrieve information about the currently running processes on the system and use for system monitoring or information gathering process.

The binary has several hardcoded URLs, possibly alternative C&C server URLs. Following are the URLs:
- http[:]//mail[.]mofa[.]govnp[.]org/mail/AFA/
- http[:]//nitc[.]govnp[.]org/mail/AFA/
- http[:]//dns[.]govnp[.]org/mail/AFA/
- http[:]//mx1[.]Nepal[.]govnp[.]org/mail/AFA/

CONCLUSION
The detailed analysis of the sophisticated cyber threat orchestrated by the Sidewinder group underscores the evolving nature of cyber threats. The multi-stage attack chain, initiated through a malicious Word document, reveals a strategic blend of advanced evasion techniques and victim manipulation. The attribution to the Sidewinder group, with a history dating back to 2012, emphasizes the persistent and evolving nature of this threat actor.
The deployment of the Nim backdoor, serves as a stark reminder of the threat landscape’s complexity. This final payload acts as an unauthorized access gateway, connecting to the adversaries’ Command and Control (C2) server. This report sheds light on the threat actor’s proactive defense measures, with the malware detecting and exiting upon identifying various analysis tools. This demonstrates a calculated effort to thwart dynamic analysis and maintain the threat’s efficacy.
This comprehensive analysis aims to equip cybersecurity professionals, organizations, and individuals with the insights needed to enhance their defenses against evolving and sophisticated cyber threats. The dynamic landscape of cyber threats necessitates a proactive and informed approach to cybersecurity, and this report contributes valuable intelligence to that end.
LIST OF IOCS
| Sr No. | Indicator | Type | Remarks |
| 1 | E5859B366B93B05414E1E95D65CE7414 | MD5 File Hash | Malicious Macro Document |
| 2 | 4319a76108da6dbcc46a8e50dce25bace3dfe518 | SHA1 File Hash | Malicious Macro Document |
| 3 | 7459a6106d3562d72c7a4fee62d106064a3ed5b48e16474da2b448aeacc2a333 | SHA256 Hash | Malicious Macro Document |
| 4 | 777fcc34fef4a16b2276e420c5fb3a73 | MD5 File Hash | Conhost.exe |
| 5 | 5d2e2336bb8f268606c9c8961bed03270150cf65 | SHA1 File Hash | Conhost.exe |
| 6 | 696f57d0987b2edefcadecd0eca524cca3be9ce64a54994be13eab7bc71b1a83 | SHA256 Hash | Conhost.exe |
| 7 | http://mail.mofa.govnp.org/mail/AFA/ | URL | Hardcoded URLs |
| 8 | http://nitc.govnp.org/mail/AFA/ | URL | Hardcoded URLs |
| 9 | http://dns.govnp.org/mail/AFA/ | URL | Hardcoded URLs |
| 10 | http://mx1.nepal.govnp.org/mail/AFA/ | URL | Hardcoded URLs |
MITRE ATT&CK TTPs
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| T1566.001: Spear phishing Attachment | ||
| 2 | Execution (TA0002) | T1204: User Execution |
| T1204.002: Malicious File | ||
| 3 | Persistence (TA0003) | T1547: Boot or Logon Auto start Execution |
| T1547.001: Registry Run Keys/ Startup Folder | ||
| 4 | Defense Evasion (TA0005) | T1140: Deobfuscate/Decode Files or Information |
| 5 | Discovery (TA0007) | T1057: Process Discovery |
| T1082: System Information Discovery | ||
| 6 | Exfiltration (TA0010) | T1041 – Exfiltration Over Command-and-Control Channel |
| 7 | Lateral Movement (TA0008) | T1021: Remote Services |
Yara Rules
(Source: Surface Web (OSINT))
rule Office_Document_with_VBA_Project
{
meta:
description = “This signature detects an office document with an embedded VBA project. While this is fairly common it is sometimes used for malicious intent.”
Source: Surface Web (OSINT)
samples = “7459a6106d3562d72c7a4fee62d106064a3ed5b48e16474da2b448aeacc2a333”
strings:
$magic1 = /^xD0xCFx11xE0xA1xB1x1AxE1x00x00x00/
$magic2 = /^x50x4Bx03x04x14x00x06x00/
$vba_project1 = “VBA_PROJECT” wide nocase
$vba_project2 = “word/vbaProject.binPK”
condition:
(($magic1 at 0) or ($magic2 at 0)) and any of ($vba_project*)
}
rule sandboxdetect_misc : sandboxdetect
{
meta:
source: Surface Web (OSINT)
description = “Sandbox detection tricks”
strings:
$sbxie1 = “sbiedll” nocase ascii wide
// CWSandbox
$prodid1 = “55274-640-2673064-23950” ascii wide
$prodid2 = “76487-644-3177037-23510” ascii wide
$prodid3 = “76487-337-8429955-22614” ascii wide
$proc1 = “joeboxserver” ascii wide
$proc2 = “joeboxcontrol” ascii wide
condition:
any of them
}
rule INDICATOR_SUSPICIOUS_References_SecTools {
meta:
source: Surface Web (OSINT)
description = “Detects executables referencing many IR and analysis tools”
strings:
$s1 = “procexp.exe” nocase ascii wide
$s2 = “perfmon.exe” nocase ascii wide
$s3 = “autoruns.exe” nocase ascii wide
$s4 = “autorunsc.exe” nocase ascii wide
$s5 = “ProcessHacker.exe” nocase ascii wide
$s6 = “procmon.exe” nocase ascii wide
$s7 = “sysmon.exe” nocase ascii wide
$s8 = “procdump.exe” nocase ascii wide
$s9 = “apispy.exe” nocase ascii wide
$s10 = “dumpcap.exe” nocase ascii wide
$s11 = “emul.exe” nocase ascii wide
$s12 = “fortitracer.exe” nocase ascii wide
$s13 = “hookanaapp.exe” nocase ascii wide
$s14 = “hookexplorer.exe” nocase ascii wide
$s15 = “idag.exe” nocase ascii wide
$s16 = “idaq.exe” nocase ascii wide
$s17 = “importrec.exe” nocase ascii wide
$s18 = “imul.exe” nocase ascii wide
$s19 = “joeboxcontrol.exe” nocase ascii wide
$s20 = “joeboxserver.exe” nocase ascii wide
$s21 = “multi_pot.exe” nocase ascii wide
$s22 = “ollydbg.exe” nocase ascii wide
$s23 = “peid.exe” nocase ascii wide
$s24 = “petools.exe” nocase ascii wide
$s25 = “proc_analyzer.exe” nocase ascii wide
$s26 = “regmon.exe” nocase ascii wide
$s27 = “scktool.exe” nocase ascii wide
$s28 = “sniff_hit.exe” nocase ascii wide
$s29 = “sysanalyzer.exe” nocase ascii wide
$s30 = “CaptureProcessMonitor.sys” nocase ascii wide
$s31 = “CaptureRegistryMonitor.sys” nocase ascii wide
$s32 = “CaptureFileMonitor.sys” nocase ascii wide
$s33 = “Control.exe” nocase ascii wide
$s34 = “rshell.exe” nocase ascii wide
$s35 = “smc.exe” nocase ascii wide
condition:
uint16(0) == 0x5a4d and 4 of them
}
Sigma Rules
(Source: Surface Web (OSINT))
title: Winword Drops Script In Startup
source: Surface Web (OSINT)
description: Winword.exe drops script file in startup location
threatname:
behaviorgroup: 1
classification: 7
logsource:
service: sysmon
product: windows
detection:
selection:
EventID: 11
Image: ‘*Microsoft OfficeOffice*WINWORD.EXE*’
TargetFilename:
– ‘*AppDataRoamingMicrosoft*STARTUP*.vbs*’
– ‘*AppDataRoamingMicrosoft*STARTUP*.js*’
– ‘*AppDataRoamingMicrosoft*STARTUP*.bat*’
– ‘*AppDataRoamingMicrosoft*STARTUP*.url*’
– ‘*AppDataRoamingMicrosoft*STARTUP*.cmd*’
– ‘*AppDataRoamingMicrosoft*STARTUP*.hta*’
– ‘*AppDataRoamingMicrosoft*STARTUP*.ps1*’
condition: selection
level: critical
title: Drops script at startup location
source: Surface Web (OSINT)
description: Drops script at startup location
threatname:
behaviorgroup: 1
classification: 7
logsource:
service: sysmon
product: windows
detection:
selection:
EventID: 11
TargetFilename:
– ‘*AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup*.vbs*’
– ‘*AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup*.js*’
– ‘*AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup*.jse*’
– ‘*AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup*.bat*’
– ‘*AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup*.url*’
– ‘*AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup*.cmd*’
– ‘*AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup*.hta*’
– ‘*AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup*.ps1*’
– ‘*AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup*.wsf*’
condition: selection
level: critical
title: WScript or CScript Dropper
source: Surface Web (OSINT)
description: Detects wscript/cscript executions of scripts located in user directories
tags:
– attack.execution
– attack.t1059.005
– attack.t1059.007
logsource:
category: process_creation
product: windows
detection:
selection1:
Image|endswith:
– ‘wscript.exe’
– ‘cscript.exe’
CommandLine|contains:
– ‘C:Users’
– ‘C:ProgramData’
selection2:
CommandLine|contains:
– ‘.jse’
– ‘.vbe’
– ‘.js’
– ‘.vba’
– ‘.vbs’
falsepositive:
ParentImage|contains: ‘winzip’
condition: selection1 and selection2 and not falsepositive
fields:
– CommandLine
– ParentCommandLine
falsepositives:
– Winzip
– Other self-extractors
level: high
title: WMI Module Loaded By Non Uncommon Process
source: Surface Web (OSINT)
description: Detects a WMI modules being loaded by an uncommon process
references:
tags:
– attack.execution
– attack.t1047
logsource:
category: image_load
product: windows
detection:
selection:
ImageLoaded|endswith:
– ‘fastprox.dll’
– ‘wbemcomn.dll’
– ‘wbemprox.dll’
– ‘wbemsvc.dll’
– ‘WmiApRpl.dll’
– ‘wmiclnt.dll’
– ‘WMINet_Utils.dll’
– ‘wmiprov.dll’
– ‘wmiutils.dll’
filter_main_generic:
Image|contains:
– ‘:Windowsexplorer.exe’
– ‘:WindowsSysmon.exe’
– ‘:WindowsSysmon64.exe’
– ‘:WindowsSystem32’
– ‘:WindowsSysWOW64’
– ‘MicrosoftTeamscurrentTeams.exe’
– ‘MicrosoftTeamsUpdate.exe’
filter_optional_other:
Image|endswith:
– ‘WindowsAzureGuestAgent.exe’
– ‘WaAppAgent.exe’
filter_optional_thor:
Image|endswith:
– ‘thor.exe’
– ‘thor64.exe’
filter_optional_defender:
Image|endswith: ‘MsMpEng.exe’
filter_optional_dotnet:
Image|contains:
– ‘:WindowsMicrosoft.NETFramework’
– ‘:WindowsMicrosoft.NETFramework64’
Image|endswith: ‘ngentask.exe’
filter_optional_programfiles:
Image|contains:
– ‘:Program Files’
– ‘:Program Files (x86)’
condition: selection and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
– Unknown
level: low
RECOMMENDATIONS
- Deploy robust endpoint security solutions equipped with advanced threat detection and prevention mechanisms to identify and thwart malicious activities effectively.
- Employ reputable antivirus and anti-malware software capable of detecting and removing malicious payloads promptly.
- Regularly update operating systems, applications, and security software to address known vulnerabilities that threat actors often exploit.
- Segregate your network into segments to limit lateral movement within it. This containment strategy helps prevent malware from accessing critical assets and spreading further.
- Educate employees about the dangers of phishing threats, emphasizing the risks associated with opening attachments or clicking on links in unsolicited emails.
- Train employees to recognize social engineering tactics employed by threat actors, enabling them to avoid falling victim to deceptive tricks that lead to executing malicious files.
- Configure firewalls to block outbound communication with known malicious IP addresses and domains linked to RAT command and control servers.
- Deploy behavior-based monitoring to detect unusual activity patterns, including suspicious processes attempting unauthorized network connections.
- Establish application whitelisting policies to permit only approved applications to run on endpoints, preventing the execution of unauthorized or malicious executables.
- Keep a close watch on network traffic for any anomalous patterns, such as large data transfers to unfamiliar or suspicious IP addresses.
- Create a comprehensive incident response plan outlining the necessary steps in case of a malware infection. This should include isolating affected systems and notifying relevant stakeholders promptly.
- Stay updated on the latest threat intelligence reports and indicators of compromise related to malware to proactively identify potential threats.
- Maintain regular backups of critical data and systems to minimize the impact of ransomware attacks or data loss due to malware infections.
- Adhere to the principle of least privilege (PoLP) by restricting user permissions to only those required for their specific roles. This approach limits the impact of malware that relies on elevated privileges.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence and Rules provided.