Emerging as a new group in the cybercrime landscape, this Russian-speaking group, WereWolves Ransomware, has gained notoriety recently for its rapid emergence last year. We are going to explore their modus operandi, and their growing list of victims, which stands at 23.
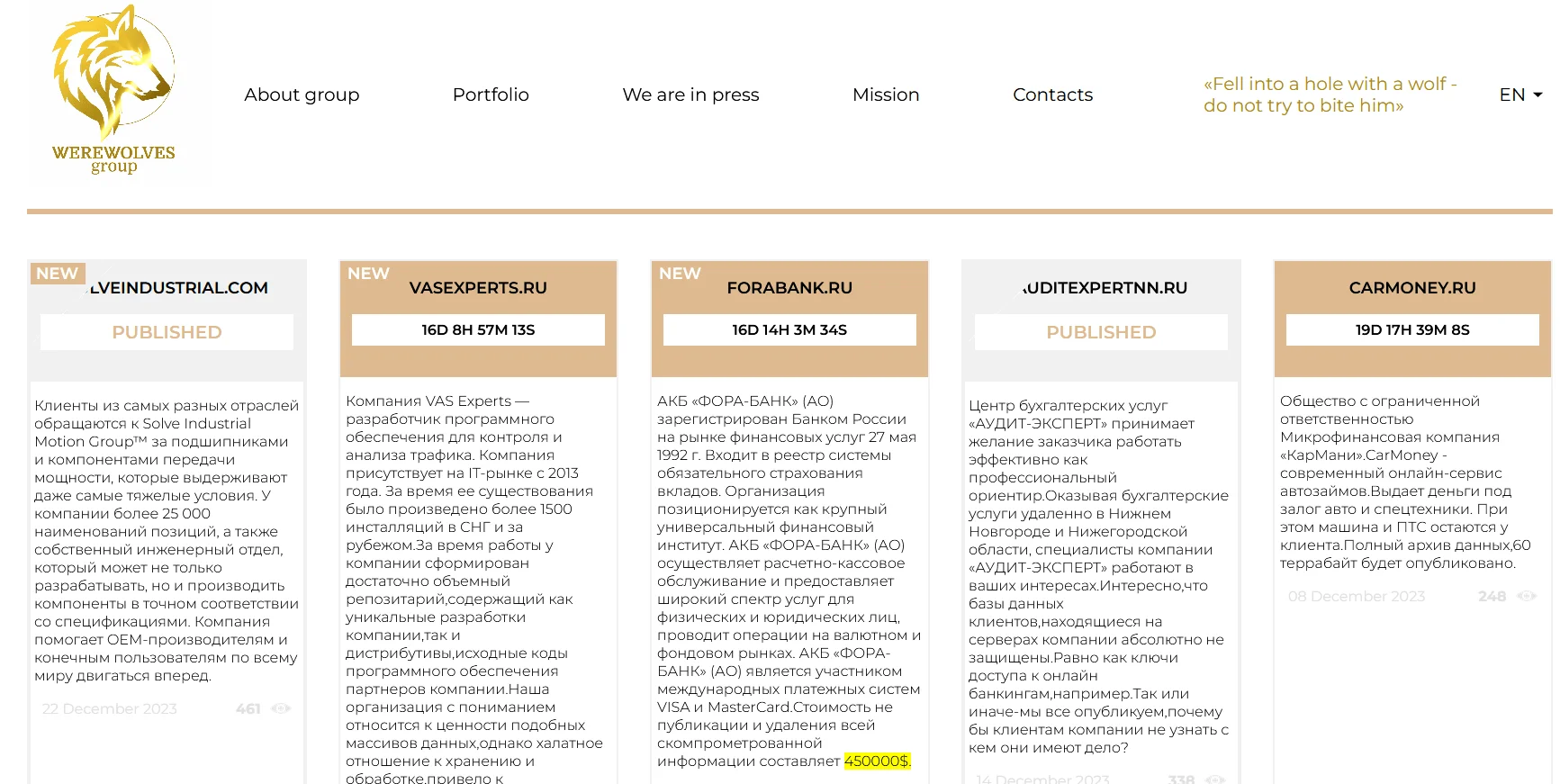
WereWolves’ leak website’s main page
Who is WereWolves Ransomware?
The WereWolves group emerged in May 2023, primarily Russian-speaking, representing a new breed in the cybercrime world. Their communication and operational style reflect their cultural and social origins, offering insights into their methodologies. However, there are still some question marks about the group. The fact that one of their websites has a German name and they list the same victims as LockBit raises a few unanswered questions for now.

WereWolves’ logo on their leak site
Modus Operandi
The WereWolves ransomware group employs an array of cyber attack techniques, notably seems to be using a variant of the LockBit3 ransomware. Their approach is characterized by double extortion tactics, where they not only encrypt the victim’s data but also threaten to release it publicly unless a ransom is paid. An old version of LockBit was leaked and many threat actors started using different versions, but the situation seems to be different with WereWolves, a possible LockBit affiliate.
Target Demographics
The WereWolves ransomware group’s targeting strategy is diverse, impacting a wide range of industries and businesses globally. Their victims, which have grown to 23 as last checked on January 9, 2024, mostly including mid to small scale enterprises and organizations, indicating a preference for easy targets. However, it does not appear that they are focusing on a specific country for now, which may indicate that they have a purely financial motivation.
Recruitment Strategies
The recruitment strategies of the WereWolves group are as intriguing as their cyber attacks. Unlike many cybercrime groups that operate in secrecy, the WereWolves have taken a more open and humorous approach to expanding their team.
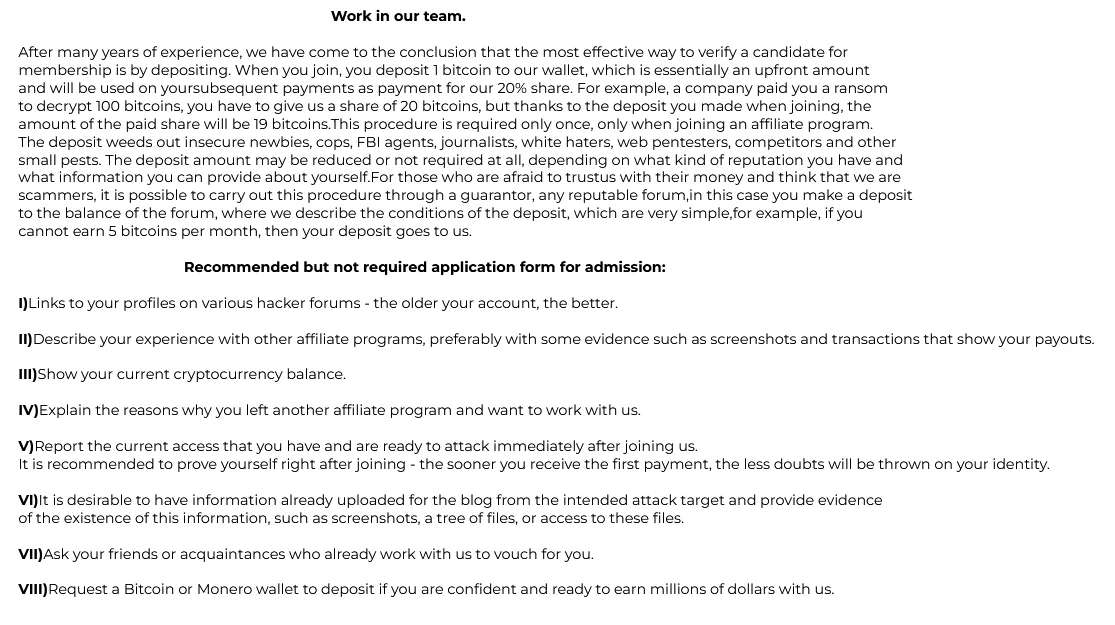
They have a “Work in our team.” section on their victim sharing website
Online Presence and Communication
The WereWolves ransomware group distinguishes itself with an engaging online presence. Their operational website is more than just a platform for communication; it serves as a hub for propaganda, information dissemination, and recruitment. They utilize their online presence to further their goals, interact with their victims, and maintain their cybercriminal network. This aspect of their operation highlights the modern ways in which cybercrime groups adapt to and leverage the digital landscape for their nefarious activities.
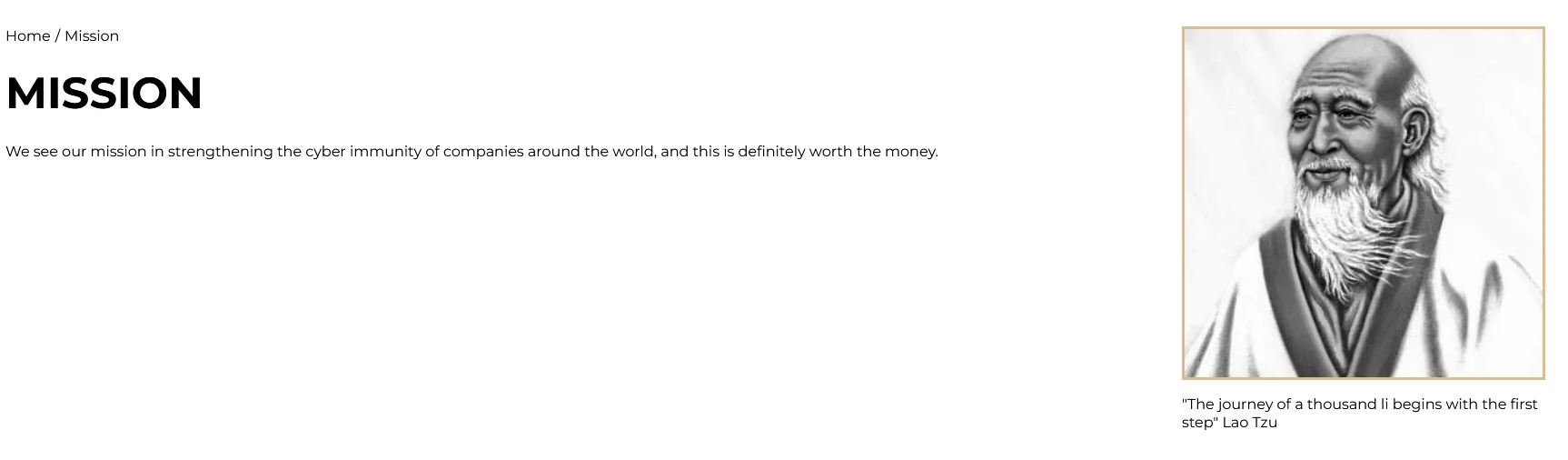
On their Mission page, they say that they provide a pentest service, which is a classic ransomware group joke that is not very original.
Affiliations and Comparisons
An interesting observation from HackManac’s blog post is that six of the victims listed by the WereWolves group seem to be identical to those previously targeted by the LockBit group. These include various organizations like the Agency for Electronic Communications and La Poste Mobile. The postings about these victims show striking similarities, including identical samples and the same amount of data claimed to be exfiltrated. This raises questions about the overlap or potential connections between these two cybercrime entities.
Targets of WereWolves Ransomware
The WereWolves ransomware group, characterized by their Russian-speaking origins, has targeted a range of sectors from Finance to Manufacturing. Their approach is looking random but they seem to focus on easy to attack but have high impact industries like small to mid scale services and organizations. This could also make their operations not just financially motivated but also potentially disruptive on a larger scale.
The group’s selection of targets underlines their intent to cause significant operational and financial distress to extract ransomware, impacting sectors that are crucial to the functioning of various economies and societies.
However, unlike traditional Russian ransomware groups, both Russian and former Soviet countries or countries close to the Soviets are included in their victim lists.

On their leak website, 4th of the 5 victim has .ru domain
Conclusion
The WereWolves group has an authentic approach, but there are doubts about their attacks. As HackManac stated well, verifying or disproving WereWolves’ cyber attacks is crucial for understanding the real threat this ransomware group presents, especially as they’ve largely operated unnoticed. The occurrence of six attacks simultaneously with LockBit’s activities raises the possibility of a connection between these two cybercriminal groups. Ongoing vigilance and monitoring are essential to fully grasp WereWolves’ operations and intentions.
Considering that even a minor incident may lead to further cyber attacks, this one year old group utilizing a dangerous LockBit Black variant underscores the need for vigilant, adaptive cyber defenses to mitigate such threats.

Source: Original Post