In late 2022, 4 ransomware strains were discovered that are derived from Conti‘s leaked ransomware strain. One of them was Meow ransomware. The operation of this crypto-ransomware was observed from late August to the first half of September 2022 and persisted until February 2023. In March 2023, a free decryptor for the Meow ransomware was released, leading to the cessation of their operation.
At the time the incident occurred, Kaspersky suggested that a modified Conti strain was likely employed to encrypt 257 victims, with 14 of them paying the attackers to regain access to their data. The private keys used for decryption were generated between November 13, 2022, and February 5, 2023, indicating the timeframe of the attacks.
A group named Meow is still active, and has made a relatively rapid entry into 2024 and has nine victims in 2024 so far. Although it does not seem to be a group that does not work with the RaaS model, they have three listed victims in March 2024 alone, and the institutions they target are not small targets.

Illustrated with Bing Image Creator
With no recent instances of sample encryptors being detected, the latest iteration of Meow ransomware could potentially operate solely as an extortion group, assuming it is the same entity. Therefore, we can’t state definitively whether Meow, the group still active, is a direct continuation of the previous operation -MeowCorps.
However, much like the Snatch group, they are probably adept hackers but lack the skills in malware development. Their ransomware was compromised after the release of the decryptor, but they haven’t managed to create a more sophisticated strain.
All recent victims listed on their leak site mention data extraction without any mention of encryption. There hasn’t been any indication of ransomware being employed in their operations, and their website is currently named Meow Leaks.
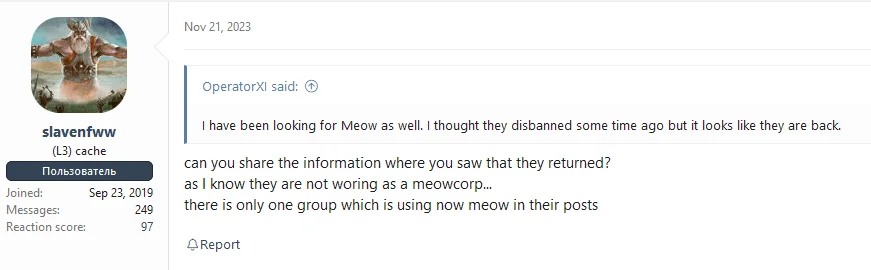
A thread in the XSS forum
The only aspect raising our doubts is that the Conti-based Meow encryptor targeted many Russian organizations initially. Consequently, some sources labeled them as an anti-Russian extortion group. However, their current choice of victims differs significantly from this characterization.
Who is Meow Ransomware?
Initially identified in August 2022, the Meow ransomware, associated with the Conti v2 variant, disappeared for a while after March of 2023, but a similar in name group surfaced in late 2023 and they remain highly active in 2024. They maintain a data leak site where they list 24 victims. Its dark web presence displays a limited roster of victims, but only those who haven’t paid the ransom are shown.

Threat Actor Card for Meow Ransomware
Once operating under different names like MeowCorp, MeowLeaks, or just Meow, it employed the ChaCha20 algorithm to encrypt data on compromised servers. Victims are then instructed to contact the extortionists through email or Telegram to receive instructions on paying the ransom and recovering their files. The title of the ransom note included the phrase “MEOW! MEOW! MEOW!” and “meowcorp2022” reiterated in the login credentials as of their initial ransomware strain in 2022.
Victimology
Compared to the old Meow, victim preferences are quite different. Their country target list is not extensive; the vast majority of their targets are in the US, with 17 attacks recorded. Meanwhile, Morocco has experienced 2 attacks, while Canada, UK, Italy, Nigeria, and Singapore each have 1 victim.

Meow Leaks Home Page
They are likely selecting targets with sensitive data since they cannot rely on encryption for extorting payment. Industries such as Healthcare and Medical Research are frequently targeted in their attacks.
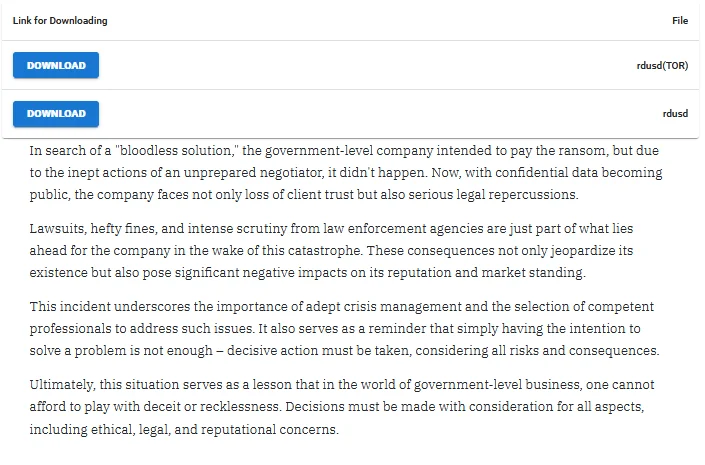
Victim “shaming” for River Delta Unified School District
They posted the above statement on their data leak site while disclosing the data of a victim who indicated intentions to pay. They explained that the purported reason for the failed agreement was an “unprepared ransomware negotiator.”

Alleged data sale of a victim company
Based on the content of the data, a price is assigned, and potential buyers are invited to reach out to them.
Contacting with Meow Project
On their data leak sites, only the contact section exists, excluding victim listings.

They sell certain data to multiple buyers but do not provide updates on whether the purchase(s) have been completed. The price range spans from approximately $2,999 to $60,000.
Modus Operandi
Let’s examine the period when Meow ransomware was capable of encrypting data with ransomware. As stated before, a variant stemming from leaked code of Conti-2 Ransomware encrypted data on compromised servers using the ChaCha20 algorithm. It demanded ransom payments from victims through various communication channels such as email or Telegram.
The ransomware was initially observed towards the end of August and the beginning of September 2022 and remained active until February 2023. The encrypted files bore the “.MEOW” extension, and the ransom note was named “readme.txt.”

Meow Ransomware note (Source)
The ransom note, marked with the repeated phrase “MEOW! MEOW! MEOW!”, instructed victims to contact the extortionists via specified email addresses and Telegram accounts to negotiate ransom payments and retrieve their encrypted files.
Meow ransomware spread through various means, including unprotected Remote Desktop Protocol (RDP) configurations, email spam with malicious attachments, deceptive downloads, botnets, exploits, malvertising, web injections, fake updates, and infected installers. The ransomware encrypted a wide range of file types, excluding “.exe” and note text files. The encrypted files were typically found in user folders and temporary directories.
There haven’t been captured pulse or malware samples regarding their purported ongoing operations, Vanderbilt University Medical Center, one of the recent affected entities, issued a statement. A spokesperson for VUMC acknowledged that they were addressing a cyber incident but refrained from disclosing when it took place, whether it involved ransomware, or the extent of the impact resulting from the attack.
Mitigation Strategy: Data Protection Focus
Given the evolving tactics of the Meow data extortion team, particularly their shift towards data sales instead of encryption-based ransomware attacks, it’s crucial to adapt mitigation strategies to prioritize data protection. Here’s a comprehensive approach:
Data Classification and Encryption:
- Implement robust data classification policies to identify sensitive information, especially in industries like Healthcare and Medical Research, which are prime targets.
- Encrypt sensitive data both at rest and in transit using strong encryption algorithms to mitigate the impact of unauthorized access.
Access Control and Least Privilege:
- Enforce strict access controls to limit data access to authorized personnel only.
- Follow the principle of least privilege, ensuring that individuals only have access to the data necessary for their roles.
Network Segmentation and Monitoring:
- Segment networks to contain potential breaches and limit lateral movement within the network.
- Implement continuous network monitoring using Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) tools to detect anomalous activities indicative of data exfiltration attempts.
Employee Training and Awareness:
- Conduct regular training sessions to educate employees about the latest phishing tactics, social engineering techniques, and other methods used by threat actors.
- Foster a culture of cybersecurity awareness where employees are encouraged to report suspicious activities promptly.
Incident Response Plan:
- Develop and regularly update an incident response plan tailored to address data breaches and extortion attempts.
- Establish clear protocols for responding to incidents, including communication procedures, legal considerations, and coordination with law enforcement agencies.
Backup and Recovery:
- Implement a robust backup and recovery strategy to ensure data availability in the event of a ransomware attack or data breach.
- Regularly test backup systems to verify their integrity and effectiveness in restoring critical data.
Vendor and Third-Party Risk Management:
- Assess the security posture of vendors and third-party partners with access to sensitive data.
- Require vendors to adhere to strict security standards and undergo regular security assessments.
By implementing these mitigation strategies, organizations can enhance their resilience against data extortion threats posed by groups like Meow, safeguarding sensitive data and minimizing the impact of potential breaches. Regular evaluation and adaptation of these measures are essential to stay ahead of evolving cyber threats.
SOCRadar Use Cases Against a Data Breach
SOCRadar offers a powerful solution for detecting and mitigating data leaks and credential compromises, safeguarding your business against cyber threats. By continuously monitoring the web, including both surface and dark web sources, SOCRadar swiftly identifies any exposure of sensitive information such as employee emails, customer login details, and credit card numbers.

Use cases of SOCRadar in case of and against a data breach
Moreover, in addition to its many other features, SOCRadar prioritizes critical security incidents, helping your team focus resources where they’re most needed. By ensuring compliance with GDPR regulations and protecting intellectual property, SOCRadar provides comprehensive threat intelligence to fortify your organization’s defenses against data extortion teams like Meow.
Possible MITRE ATT&CK TTPs of Meow Ransomware
Listed below are the TTPs obtained in the analysis of the Meow ransomware strain and their current possible TTPs.
| ATT&CK Tactic | ATT&CK Technique |
| Initial Access (TA0001) | |
| Exploit Public-Facing Application (T1190) | |
| External Remote Services (T1133) | |
| Phishing (T1566) | |
| Execution (TA0002) | |
| Shared Modules (T1129) | |
| Defense Evasion (TA0005) | |
| Obfuscated Files or Information (T1027) | |
| Indicator Removal from Tools (T1027.005) | |
| Masquerading (T1036) | |
| Virtualization/Sandbox Evasion (T1497) | |
| Credential Access (TA0006) | |
| Input Capture (T1056) | |
| Discovery (TA0007) | |
| Process Discovery (T1057) | |
| System Information Discovery (T1082) | |
| File and Directory Discovery (T1083) | |
| Virtualization/Sandbox Evasion (T1497) | |
| Security Software Discovery (T1518.001) | |
| Lateral Movement (TA0008) | |
| Taint Shared Content (T1080) | |
| Collection (TA0009) | |
| Input Capture (T1056) | |
| Command and Control (TA0011) | |
| Application Layer Protocol (T1071) | |
| Encrypted Channel (T1573) | |
| Exfiltration (TA0010) | |
| Exfiltration Over C2 Channel (T1041) | |
| Impact (TA0034) | |
| Data Encrypted for Impact (T1486) |
IoCs related to Meow Strain
The following are the IoCs for the now decrypted strain of the Meow group; An attack by the new extortion group has not been publicly reviewed.
SHA-256:
- fe311979cd099677b1fd7c5b2008aed000f0e38d58eb3bfd30d04444476416f9
- 7f6421cdf6355edfdcbddadd26bcdfbf984def301df3c6c03d71af8e30bb781f
- 7f624cfb74685effcb325206b428db2be8ac6cce7b72b3edebbe8e310a645099
- 5a936250411bf5709a888db54680c131e9c0f40ff4ff04db4aeda5443481922f
- 222e2b91f5becea8c7c05883e4a58796a1f68628fbb0852b533fed08d8e9b853
- b5b105751a2bf965a6b78eeff100fe4c75282ad6f37f98b9adcd15d8c64283ec
SHA-1:
- 59e756e0da6a82a0f9046a3538d507c75eb95252
- 987ad5aa6aee86f474fb9313334e6c9718d68daf
- 94a9da09da3151f306ab8a5b00f60a38b077d594
- 5949c404aee552fc8ce29e3bf77bd08e54d37c59
- 578b1b0f46491b9d39d21f2103cb437bc2d71cac
- 4f5d4e9d1e3b6a46f450ad1fb90340dfd718608b
MD5:
- 8f154ca4a8ee50dc448181afbc95cfd7
- 4dd2b61e0ccf633e008359ad989de2ed
- 3eff7826b6eea73b0206f11d08073a68
- 1d70020ddf6f29638b22887947dd5b9c
- 033acf3b0f699a39becdc71d3e2dddcc
- 0bbb9b0d573a9c6027ca7e0b1f5478bf

Source: https://socradar.io/dark-web-profile-meow-ransomware/
Views: 1