
Keypoints :
- Kairos is a cyber extortion group that emerged in late 2024.
- They specialize in data theft and extortion rather than traditional ransomware attacks.
- The group has claimed 14 victims as of 2025, focusing mainly on the U.S.
- Targets include sectors like Healthcare, Business Services, Manufacturing, Education, and Technology.
- Kairos uses Initial Access Brokers (IABs) to gain access to networks for data exfiltration.
- The group applies pressure on victims by threatening to release stolen data unless ransom is paid.
- They utilize Data-Leak Sites to publicly release stolen data, enhancing extortion pressure.
- Organizations can protect themselves by implementing proactive cybersecurity measures.
MITRE Techniques :
- Initial Access (T1078) – Kairos purchases access from Initial Access Brokers to gain footholds in corporate networks.
- Data Exfiltration (T1041) – After gaining access, they conduct reconnaissance and exfiltrate sensitive data.
- Extortion (T1499) – They threaten to release stolen data unless ransom is paid, leveraging Data-Leak Sites.
Indicator of Compromise :
- [domain] kairos-extortion-group.com
- [url] data-leak-site.com
- [file name] stolen_data.txt
- [tool name] Initial Access Broker Tool
- Check the article for all found IoCs.
Kairos is a low-profile but rising cyber extortion group that has been active since late 2024. Unlike many of its counterparts, Kairos does not rely on ransomware in its attacks but instead focuses on data theft and subsequent extortion. The group primarily targets sensitive data within organizations, threatening to release it unless a ransom is paid. So far, Kairos has claimed 14 victims, with operations mainly based in the United States. While the group’s tactics are not as aggressive as some larger extortion gangs, the threat of public data exposure remains a significant pressure point for their victims. By employing this tactic, Kairos positions itself within a growing trend of cybercriminal groups that combine traditional hacking methods with extortion to force payouts.

Threat actor card of Kairos Extortion Group
Who is Kairos?
The Kairos Extortion Group, emerging in late 2024, has quickly gained attention for its unique method of cybercrime. Unlike traditional ransomware gangs, they specialize in data theft and extortion rather than encrypting victims’ files.
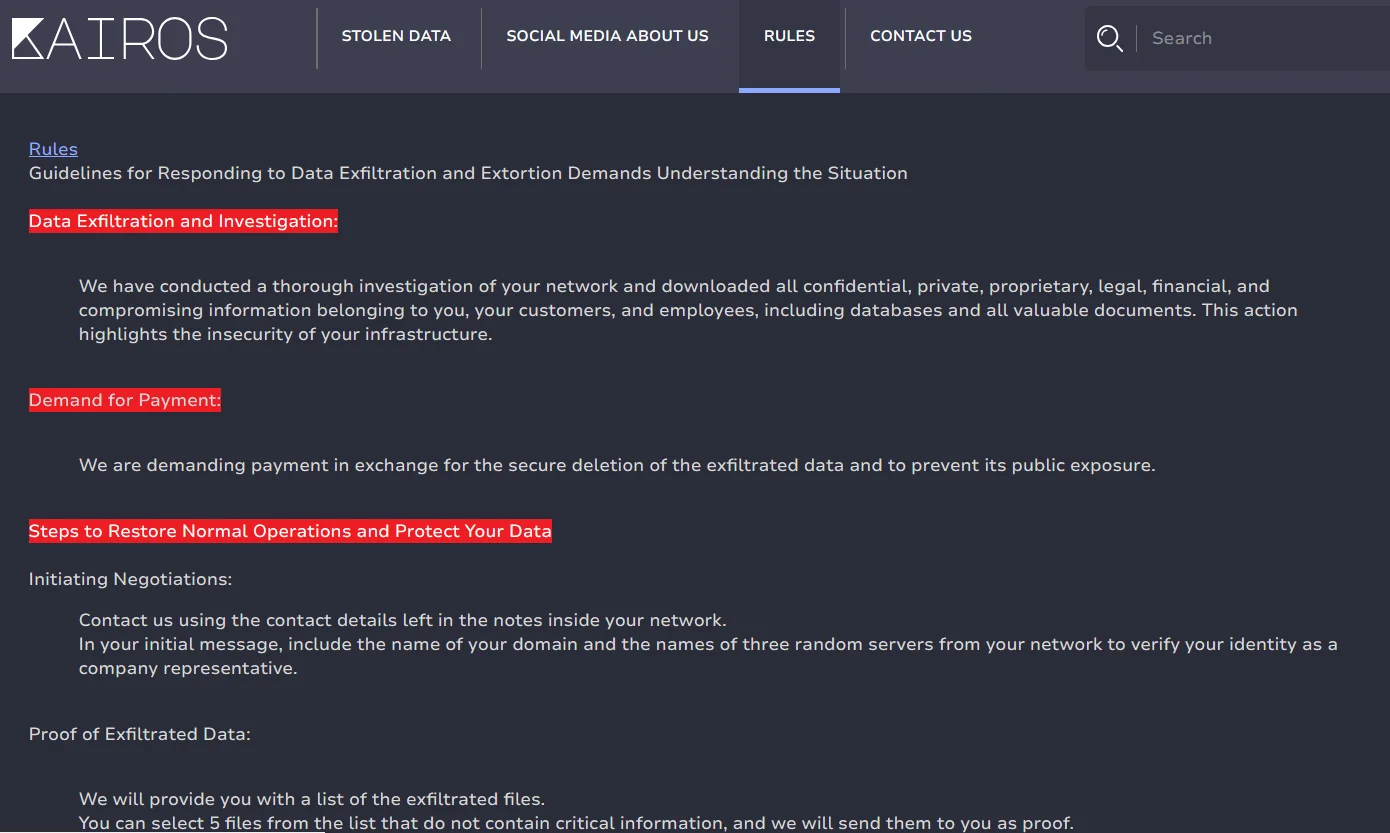
A part of their “RULES” section also shows that they are only an extortion group
Their tactic revolves around stealing sensitive information from organizations and demanding payment to prevent its public release. Despite their growing presence, the group’s activity has remained relatively low-profile, with only 14 confirmed victims by 2025. This limited number of attacks highlights their selective approach and calculated strikes, as they aim to apply pressure through data exposure threats rather than widespread, aggressive assaults.
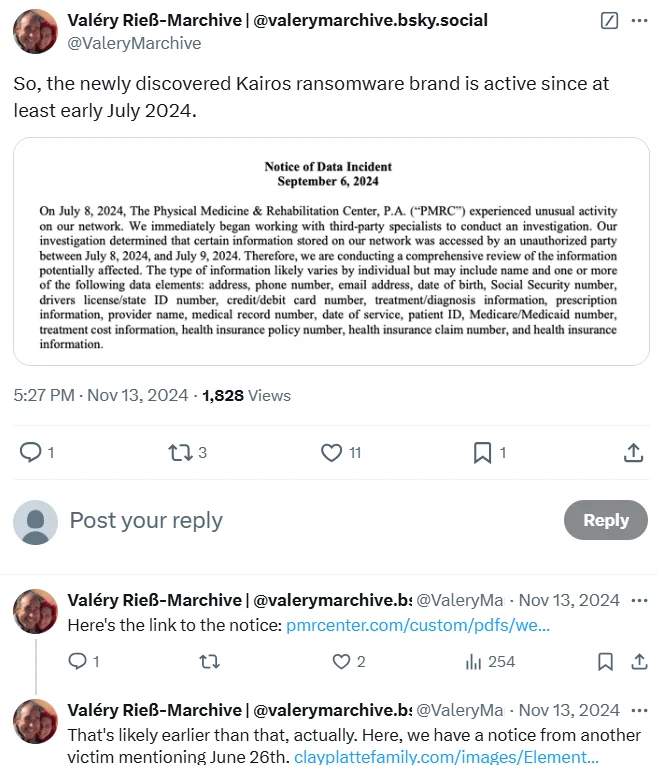
A post by an X user claiming their activities started in summer of 2024 (X)
What are Their Targets?
Kairos has targeted organizations in multiple countries, with a significant focus on the United States, which remains the most frequently attacked region. The group has primarily concentrated its efforts on sectors like Healthcare, Business Services, and Manufacturing, with attacks on medical centers, clinics, and businesses within these sectors. There has also been activity in the Education and Technology sectors.
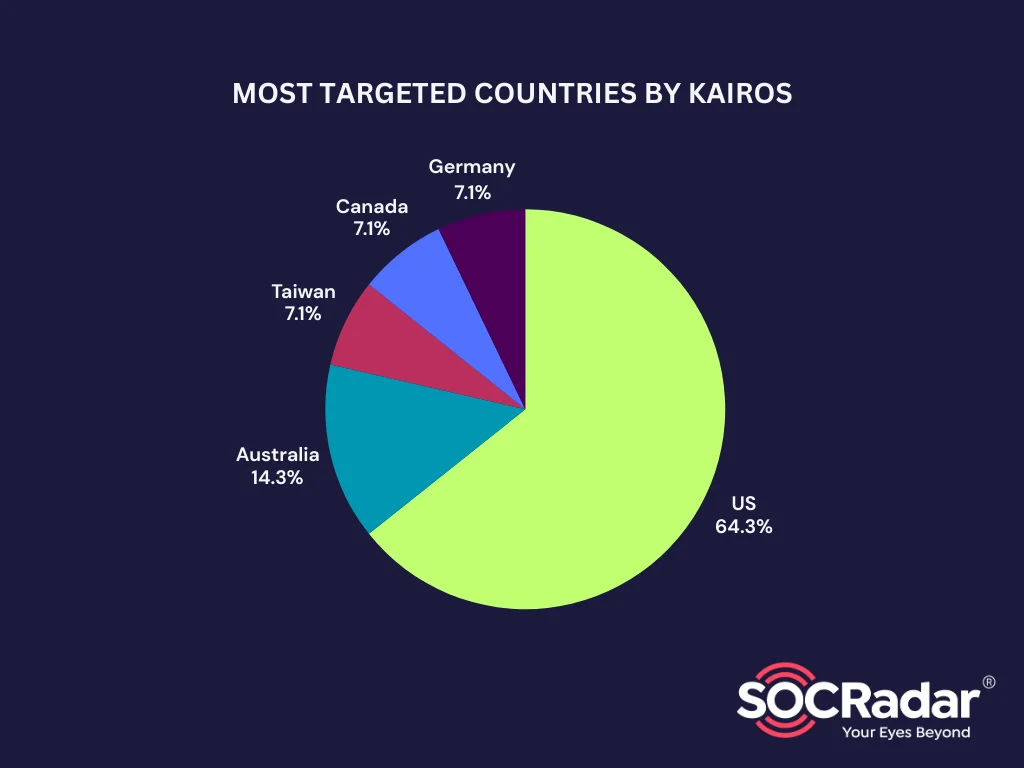
Targeted countries by Kairos Extortion Group
Beyond the U.S., Kairos has expanded its reach internationally. In Australia, the group attacked a financial services firm, Austin’s Financial Solutions. In the United Kingdom, Anetic Aid, a healthcare company, was impacted. The Construction sector was targeted in Canada, where Tacoma Engineers fell victim to an attack. Additionally, Taiwan saw an attack on Formosa Certified Public Accountants, a financial services company.
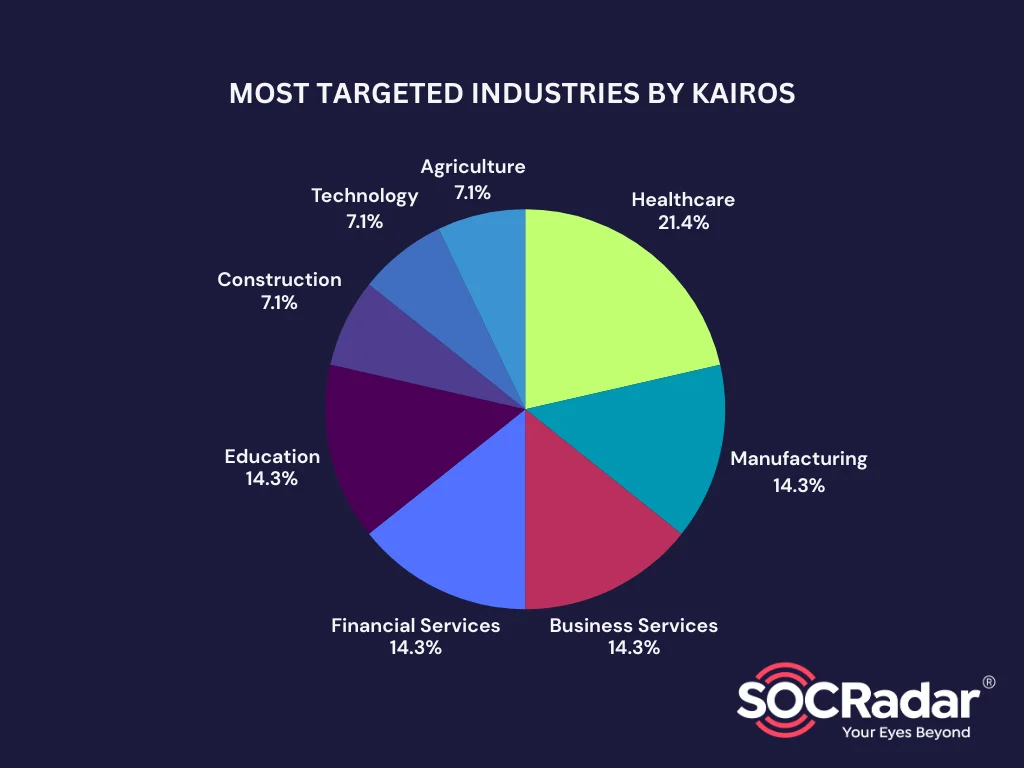
Targeted industries by Kairos Extortion Group
This range of targets highlights Kairos’ broad operational scope. While the group has a tendency to strike critical infrastructure, particularly in Healthcare and Business Services, its activities span across diverse sectors and regions, reflecting a well-rounded attack strategy.
What are Their Tactics?
Kairos employs a range of tactics to carry out their extortion campaigns, seemingly relying largely on Initial Access Brokers (IABs) to gain footholds in corporate networks. By purchasing access to networks from IABs, Kairos bypasses the complex initial stages of compromising targets and directly enters the data exfiltration and extortion phases. This method enables them to focus their efforts on reconnaissance, gathering sensitive information, and threatening to release it unless a ransom is paid. Here’s an overview of their key tactics:
- Use of Initial Access Brokers (IABs): Kairos actively participates in IAB markets, purchasing access to networks via cybercriminal forums. This allows them to target organizations with specific criteria—such as location, industry, and revenue—without having to exploit vulnerabilities themselves. By buying access from IABs, they bypass the often time-consuming and technical stages of network intrusion, enabling them to focus on their extortion activities more efficiently. They have been identified bidding on access to various organizations, including those in the U.S., Canada, and Taiwan, to gain a foothold in high-value targets.
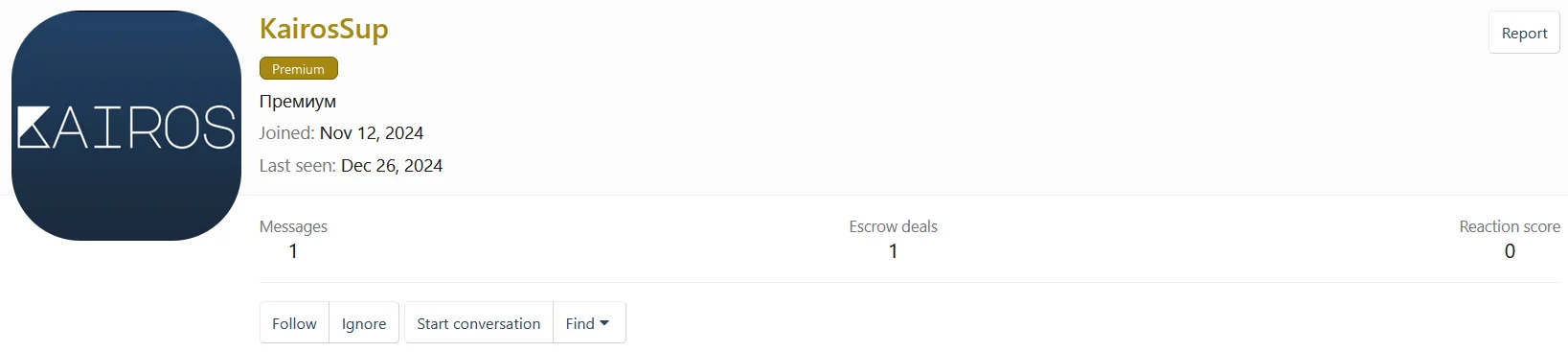
A user possibly moderated by Kairos group used for buying initial access from a specific hacker forum, the name is clearly inspired by the infamous LockBit’s LockBitSupp account
- Data Exfiltration and Extortion: After obtaining initial access to the network, Kairos conducts reconnaissance to identify sensitive data, including personal information, financial records, and medical details. Their primary tactic is data exfiltration followed by extortion, where they threaten to release the stolen data on data-leak sites unless their demands are met. They have used this approach in targeting sectors like healthcare, business services, and construction, where personal or sensitive data is often stored.
- Targeting Specific Sectors and Organizations: Kairos demonstrates an ability to select targets based on sector, revenue, and location. By purchasing access through IABs, they can narrow down potential victims and tailor their extortion demands. This possible precision allows them to avoid random targeting and focus on organizations that could be more susceptible to their threats, enhancing the likelihood of success in their extortion campaigns.
- Leveraging Data-Leak Sites: Kairos uses Data-Leak Sites (DLS) to publicly release stolen data, applying pressure on victims to meet their ransom demands. These sites serve as platforms for extortion groups to shame victims into compliance, amplifying the threat of reputational damage and financial loss if the stolen data is made public.

Kairos’s Data Leak Site (DLS)
By utilizing IABs, targeting specific sectors, and focusing on data exfiltration and extortion rather than deploying ransomware, Kairos differentiates itself from other extortion-focused groups. Their tactics streamline the attack process, reducing technical barriers and accelerating the timeline for extortion campaigns. As they continue to refine their methods, it is likely they will expand their reach and develop more sophisticated approaches to exfiltration and threats.
How To Protect Your Organization From Extortion?
Organizations can implement a variety of proactive measures to protect themselves from extortion groups like Kairos. Since these groups focus on data exfiltration and leveraging access purchased from Initial Access Brokers (IABs), traditional cybersecurity approaches alone may not be enough. Here are some key strategies to enhance protection:
- Strengthen Initial Access Defenses: Since extortion groups like Kairos often bypass traditional attack vectors by purchasing initial access from IABs, it is crucial to harden entry points into your network. This includes ensuring that remote access solutions, such as VPNs, are secure and regularly patched. Multi-factor authentication (MFA) should be enforced wherever possible, especially for remote and administrative accounts.
- Implement Zero Trust Architecture: A Zero Trust security model assumes that any device, user, or application trying to access resources on the network could be compromised. This approach minimizes the lateral movement of attackers within the network, effectively reducing the risk of exfiltration. With Zero Trust, continuous verification of user identity and behavior helps prevent unauthorized access.
- Conduct Regular Vulnerability Scanning and Penetration Testing: Proactively identify vulnerabilities in your infrastructure through regular vulnerability assessments and penetration testing. This helps ensure that attackers cannot easily exploit known weaknesses to gain access. Regular testing will also reveal potential areas where unauthorized access may occur, allowing teams to secure those gaps before they are exploited.
- Monitor and Detect Suspicious Activity: Implement robust security monitoring to detect abnormal behavior indicative of an ongoing breach. Network Intrusion Detection Systems (IDS) and Endpoint Detection and Response (EDR) solutions can help identify early signs of compromise, such as unexpected login attempts, suspicious file transfers, or unusual access patterns. Combining behavioral analytics with real-time alerts can help detect and stop attackers before they can exfiltrate sensitive data.
- Secure Sensitive Data: Ensure sensitive data is encrypted both in transit and at rest. Even if an attacker gains access to your network, encrypted data will be difficult to use or leak. Additionally, adopting Data Loss Prevention (DLP) solutions can help prevent unauthorized transfers of sensitive data, minimizing the risk of exfiltration.
- Limit Data Access and Implement Least Privilege: Restrict access to sensitive data based on roles and responsibilities. By applying the principle of least privilege, you ensure that only authorized personnel have access to critical systems or sensitive information. Regularly review user permissions to ensure they align with their current roles, reducing the risk of insider threats or unauthorized data exposure.
- Employee Training on Social Engineering: While Kairos is known for using IABs to gain access, it’s still essential to train employees to recognize and respond to social engineering attempts, such as phishing emails or phone calls that attempt to trick them into revealing credentials or other sensitive information. Regular awareness training and simulated phishing campaigns can help employees stay vigilant.
- Have an Incident Response Plan: Prepare for potential extortion attempts by creating and regularly updating an Incident Response (IR) plan. The plan should include predefined steps for isolating compromised systems, investigating the breach, and coordinating with legal, forensic, and public relations teams. It should also address communication protocols with law enforcement and cybersecurity agencies.
- Build a Strong Legal and Financial Response Strategy: In case of an extortion attack, having a pre-established legal and financial response strategy is essential. Engage with legal counsel to understand the implications of paying or not paying the extortion demands, and ensure that you are compliant with regional regulations around data breaches and ransom payments.
- Collaborate with External Partners: Work with cybersecurity firms, threat intelligence providers, and law enforcement agencies to stay informed about the latest threat actor tactics and trends. Sharing threat intelligence with other organizations in your industry can also help identify and mitigate risks early.
How Can SOCRadar Help?
SOCRadar offers a comprehensive suite of tools designed to help organizations mitigate the risks posed by extortion groups like Kairos. With its advanced threat intelligence platform, SOCRadar provides critical insights and real-time monitoring capabilities to identify, assess, and respond to cyber threats, including those related to extortion and data breaches. Here’s how SOCRadar can help protect your organization:
- Dark Web Monitoring: SOCRadar’s service continuously scans underground forums and marketplaces where extortion groups like Kairos often operate. By identifying any leaks of sensitive data or mentions of your organization, SOCRadar helps you stay ahead of potential threats. This early warning system allows you to take swift action to secure your data and prevent it from being sold or used against your organization.
SOCRadar’s Advanced Dark Web Monitoring
- Real-Time Threat Intelligence: With SOCRadar’s real-time threat intelligence, you gain immediate visibility into emerging threats and tactics used by extortion groups. This includes identifying Initial Access Broker (IAB) activity and other threat actor movements within the cybercrime ecosystem. By understanding these dynamics, your security team can implement targeted defense strategies to counteract extortion attempts.
- Comprehensive Attack Surface Management: SOCRadar’s Attack Surface Management module helps you identify and monitor all digital assets exposed to potential exploitation. By continuously tracking vulnerabilities, open ports, and weak points in your network, SOCRadar ensures that your attack surface is minimized and protected from unauthorized access.
- Extortion and Data Leak Monitoring: SOCRadar tracks data-leak sites and other extortion-related platforms where groups like Kairos may post stolen data. If your organization’s data is involved in an extortion attack, SOCRadar’s monitoring tools will alert you immediately, allowing you to respond quickly to prevent further exposure and mitigate the risk of extortion.
- Threat Actor Profiling: SOCRadar’s profiling tools allow you to monitor and analyze the tactics, techniques, and procedures (TTPs) of extortion groups like Kairos. By understanding their attack patterns and targets, you can proactively strengthen your defenses and develop countermeasures that are specifically tailored to the threat landscape posed by these groups.
- Customizable Alerts and Notifications: SOCRadar allows you to set up customized alerts for any suspicious activity, including potential extortion threats. Whether it’s detecting signs of data exfiltration or identifying attempts to purchase access via IABs, SOCRadar ensures that your team is always in the loop with actionable intelligence.
- Vulnerability Management: SOCRadar’s Vulnerability Management capabilities help you identify weaknesses in your systems and take corrective actions before they can be exploited by extortion groups. By continuously monitoring for vulnerabilities and applying timely patches, you reduce the risk of unauthorized access and data exfiltration.
By leveraging SOCRadar’s advanced capabilities, your organization can gain a significant advantage in defending against extortion groups like Kairos. Through continuous monitoring, threat intelligence, and proactive defense strategies, SOCRadar ensures that your organization stays one step ahead of cybercriminals.
In Summary
Extortion groups like Kairos continue to evolve, leveraging tactics such as collaboration with Initial Access Brokers (IABs) to streamline their attacks. These groups exploit vulnerabilities in organizational security to exfiltrate sensitive data and demand ransoms, posing significant risks to businesses globally. To counter such threats, organizations must adopt a multi-layered security approach that includes advanced threat intelligence, attack surface management, and real-time monitoring.
SOCRadar provides a comprehensive solution to these challenges, offering tools to monitor data-leak sites, track emerging threats, and proactively defend against extortion attempts. By utilizing SOCRadar’s capabilities, organizations can safeguard their data, minimize their attack surface, and build resilience against evolving cyber threats.
Adopting SOCRadar not only strengthens your security posture but also equips your team with the insights and tools needed to stay ahead of extortion groups, ensuring your organization remains protected in an increasingly hostile cyber landscape.
Full Research: https://socradar.io/dark-web-profile-kairos-extortion-group/