BlackSuit ransomware is a rebranded version of the notorious Royal ransomware, which emerged due to heightened law enforcement actions against the original group. This rebranding signifies a strategic shift aimed at evading detection and continuing their cybercriminal activities under a new guise. The Royal ransomware, now BlackSuit, has a notorious history of targeting high-profile sectors and demanding substantial ransoms.
BlackSuit’s logo
Who is BlackSuit Ransomware
BlackSuit first emerged in May 2023 and appears to be closely linked to the Royal ransomware gang, which itself originated from the remnants of the infamous Conti group.

Threat Actor Card for BlackSuit Ransomware
In November of 2023, CISA and the FBI updated their joint Cybersecurity Advisory (CSA) on Royal Ransomware under the #StopRansomware initiative, highlighting its impact on critical sectors like manufacturing, communications, healthcare, and education. Since September 2022, Royal Ransomware has targeted over 350 victims globally, demanding ransoms exceeding $275 million.
For more information about the Royal Ransomware, check our relevant blog post.
Later, the advisory warned of a potential rebranding to BlackSuit Ransomware, noting similar coding characteristics. The update included detailed Tactics, Techniques, and Procedures (TTPs) and Indicators of Compromise (IoCs) identified by the FBI.
Modus Operandi
BlackSuit ransomware employs various techniques to infiltrate victims’ systems. One common method is through phishing emails, where attackers send deceptive messages designed to trick recipients into clicking on malicious links or downloading infected attachments. These emails often appear legitimate, making it easier for attackers to lure their targets.
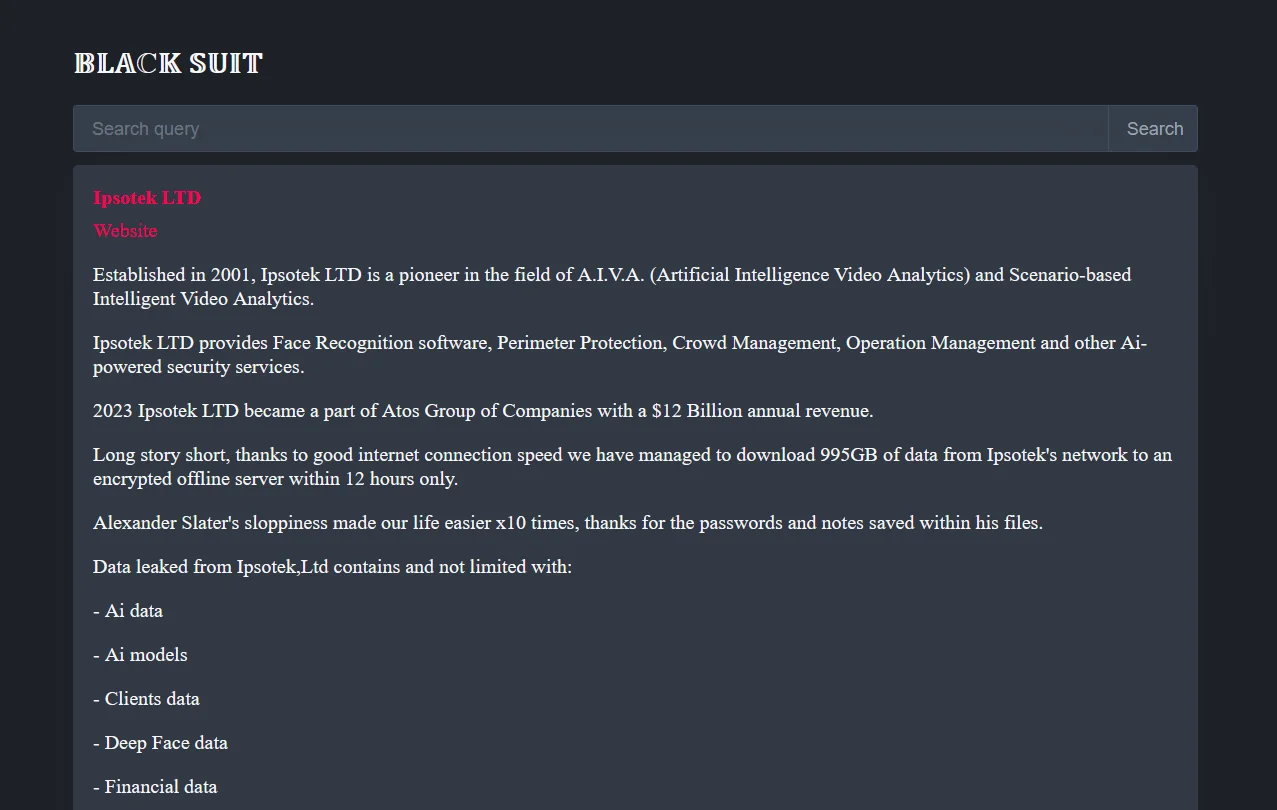
BlackSuit’s data leak site
Additionally, BlackSuit exploits known vulnerabilities in software and systems to gain unauthorized access. This method leverages flaws in outdated or unpatched software, allowing the ransomware to bypass security defenses. Exploiting these vulnerabilities is a critical component of BlackSuit’s infiltration strategy, as it targets weaknesses in widely-used applications and systems.
BlackSuit also uses legitimate tools for malicious purposes. Tools such as Chisel and Cloudflared are employed for network tunneling, enabling the attackers to bypass firewalls and other network security measures. These tools create secure communication channels that are difficult for traditional security systems to detect. Furthermore, BlackSuit utilizes AnyDesk and MobaXterm for establishing and maintaining remote access to compromised systems. These legitimate remote access tools are repurposed to provide the attackers with persistent access, allowing them to control and monitor infected systems over extended periods.
Most Targeted Industries by BlackSuit Ransomware
BlackSuit ransomware targets a diverse range of industries, often focusing on sectors where disruptions can have severe consequences.
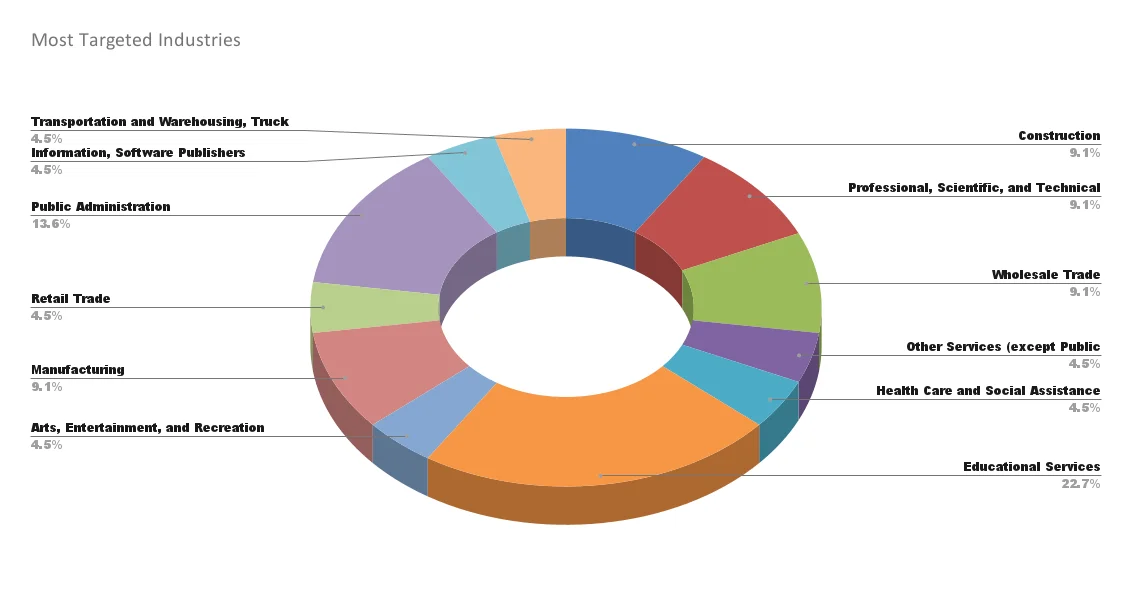
Most Targeted Industries
Notable targets include:
Healthcare: Hospitals and medical facilities are prime targets due to the critical nature of their operations and the sensitivity of their data. Disruptions in healthcare can have life-threatening consequences, making these institutions more likely to pay ransoms to restore operations quickly. Education, which ranks first, may have similar characteristics, although it is not as sensitive as healthcare.
Critical Infrastructure: This includes sectors like energy, water, and transportation, which are essential for public safety and economic stability. Attacks on these sectors can cause widespread disruptions, impacting large populations and creating significant pressure to resolve the incident swiftly.
Large Enterprises: Businesses with substantial financial resources are often targeted because they have the means to pay significant ransoms. These enterprises also store vast amounts of sensitive data, making them attractive targets for data exfiltration and subsequent extortion.
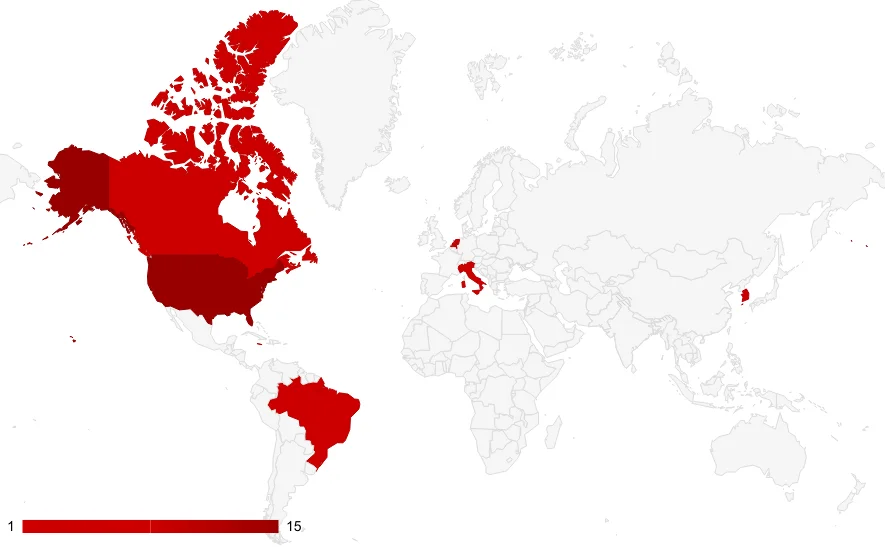
BlackSuit targets the US most
Ransom demands from BlackSuit are typically substantial, reflecting the high stakes of their chosen targets. The group employs a dual extortion tactic: they exfiltrate sensitive data before encrypting files, threatening to leak the data if the ransom is not paid. This approach adds pressure on the victims to comply with the ransom demands to prevent both operational disruptions and data breaches. The ransomware encrypts files using strong encryption algorithms, rendering the data inaccessible without the decryption key provided by the attackers upon payment.
Further Technical Details
In the analyses carried out in 2023, it was revealed that BlackSuit ransomware retained much of the original codebase from Royal ransomware, demonstrating over 90% code similarity. This indicated that BlackSuit inherits many of Royal’s technical attributes.
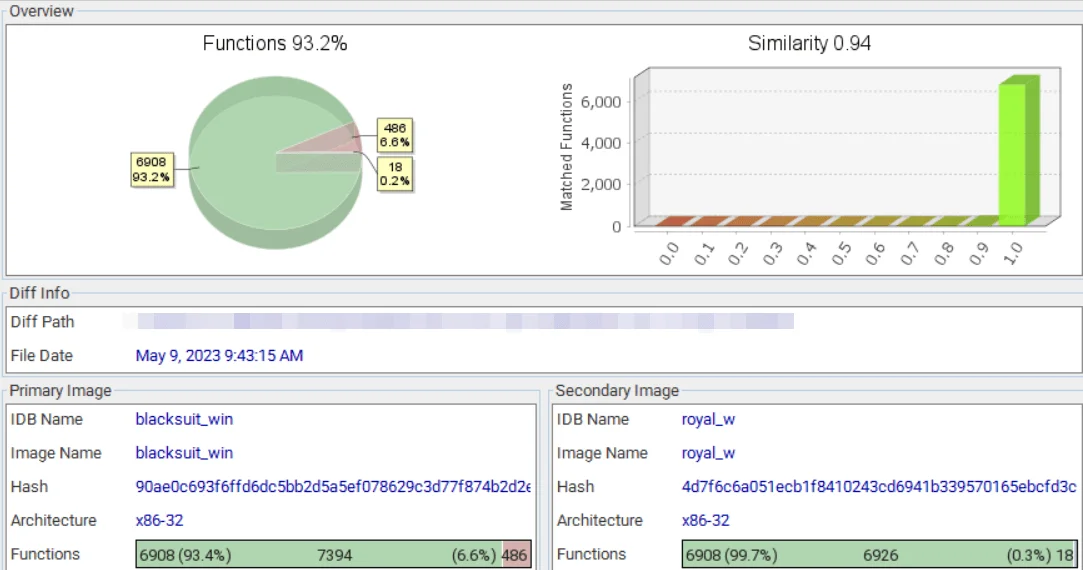
Similarity of the BlackSuit with Royal (Trend Micro)
Encryption Methods: BlackSuit utilizes robust encryption algorithms to lock files, making decryption extremely difficult without the attacker-provided key. BlackSuit ransomware payloads, designed for both Windows and Linux systems, employ OpenSSL’s AES implementation for data encryption. The encryption is designed to be efficient and fast, ensuring that a significant portion of the victim’s data is rendered inaccessible quickly, thereby increasing the pressure to pay the ransom.
Credential Theft: To escalate privileges and move laterally within the victim’s network, BlackSuit uses tools such as Mimikatz. This tool allows the attackers to harvest credentials from memory, enabling them to gain access to additional systems and accounts within the network. By obtaining high-level credentials, BlackSuit can bypass security measures and spread its reach more broadly within an organization.
Persistence Mechanisms: BlackSuit maintains its presence on compromised systems through the use of legitimate remote access tools like AnyDesk and MobaXterm. These tools allow the attackers to establish and maintain remote control over the infected systems. This persistence ensures that the attackers can monitor the systems, execute further commands, and potentially reinfect the network if initial remediation efforts are not thorough.
Network Tunneling: To bypass traditional security measures like firewalls, BlackSuit employs network tunneling tools such as Chisel and Cloudflared. These tools enable the creation of secure communication channels that are difficult to detect, allowing the attackers to move data in and out of the network undetected. This capability is particularly useful for exfiltrating sensitive data before encryption, which is a critical component of their dual extortion strategy.
Contact us section of the data leak site
BlackSuit’s ability to exploit known vulnerabilities in software and systems, combined with its use of sophisticated tools and techniques, makes it a formidable threat. Its lineage from the Royal ransomware ensures that it inherits a proven and effective ransomware platform, enhanced with new tactics to evade detection and increase its impact. This comprehensive approach to ransomware deployment highlights the importance of robust cybersecurity measures and proactive threat hunting to detect and mitigate such advanced threats.
For more detailed information, please consult the advisory on CISA’s website here.
How to Mitigate BlackSuit Ransomware Attacks
Implement secure-by-design and -default principles in software development to limit the impact of ransomware techniques, such as backdoor vulnerabilities into remote software systems. Incorporate practices suggested by CISA’s Secure by Design webpage and joint guide.
Password Security
- Password Policies: Ensure all accounts with password logins comply with NIST’s standards for developing and managing password policies. Use longer passwords (at least 8 characters, up to 64 characters) and store them in hashed format using industry-recognized password managers.
- Multi Factor Authentication (MFA): Require MFA for all services, particularly for webmail, virtual private networks, and accounts accessing critical systems.
- Password Management: Avoid password reuse, enable multiple failed login attempt lockouts, disable password hints, and refrain from frequent password changes (NIST recommends longer passwords over frequent resets to avoid predictable patterns).
Remote Access Security
- Administrator Credentials: Require administrator credentials for software installations.
- Securing Remote Access: Apply mitigations from the Joint Guide to Securing Remote Access Software to reduce the threat of malicious actors using remote access tools.
System and Network Security
- Patch Management: Keep all operating systems, software, and firmware updated to minimize exposure to cybersecurity threats.
- Network Segmentation: Segment networks to control traffic flows and restrict adversary lateral movement, reducing the spread of ransomware.
- Network Monitoring: Implement a networking monitoring tool to detect abnormal activity and potential ransomware traversal. Use EDR tools for endpoint detection and response.
- Antivirus Software: Install, regularly update, and enable real-time detection for antivirus software on all hosts.
Access Controls and Privilege Management
- User Account Management: Audit user accounts, configure access controls based on the Principle of Least Privilege (PoLP), and disable unused ports.
- Just-in-Time (JIT) Access: Implement time-based access controls for admin-level accounts using JIT access methods to enforce PoLP and the Zero Trust model.
- Disable Command-line and Scripting Activities: Prevent privilege escalation and lateral movement by disabling command-line and scripting activities and permissions.
Data Backup and Recovery
- Backup Practices: Maintain offline backups of data, ensure backups are encrypted and immutable, covering the entire organization’s data infrastructure.
- Recovery Plan: Implement a recovery plan to maintain multiple copies of sensitive data in physically separate, segmented, and secure locations.
By implementing these mitigations, organizations can significantly reduce the risk of BlackSuit ransomware attacks and enhance their overall cybersecurity posture.
How Can SOCRadar Help?
Understanding their methods and implementing robust mitigation strategies are crucial steps for organizations to strengthen their defenses and reduce the risk of falling victim to ransomware attacks. Remaining vigilant and proactive in cybersecurity efforts is essential in combating ransomware groups like BlackSuit.
SOCRadar Attack Surface Management has Ransomware Check function
We can assist you in developing a proactive security posture. SOCRadar enhances your organization’s security stance against ransomware threats through proactive threat monitoring and intelligence solutions. By utilizing our platform, you can actively search for threat actors, comprehend their tactics and vulnerabilities, and implement preemptive measures to safeguard your assets.
SOCRadar’s Attack Surface Management module includes a Ransomware Check function. This feature offers ongoing monitoring of potential attack vectors, providing timely alerts for suspicious activities. This proactive approach facilitates swift responses to threats, strengthening your overall cybersecurity defenses. Integrating SOCRadar into your cybersecurity framework adds an additional layer of protection against ransomware and various cybersecurity threats.

Source: Original Post
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português