Advanced Persistent Threat Group 31 (APT31), also known by aliases like ZIRCONIUM or Judgment Panda, represents a sophisticated cybersecurity threat with ties to state-sponsored activities.

Threat Actor Card of APT31
This group is believed to operate primarily on behalf of the Chinese government, engaging in cyber espionage and targeted attacks to gather intelligence and support strategic objectives aligned with China’s national interests.

APT31 Depiction, Image created by BING AI
APT31’s activities are characterized by advanced tactics, including the use of malware, spear-phishing campaigns, and exploitation of zero-day vulnerabilities, making them a significant concern for global cybersecurity efforts. Understanding APT31’s modus operandi and the implications of its actions is crucial in combating cyber threats posed by state-sponsored actors.
Indictment and Charges
In recent developments, the United States Department of Justice unsealed an indictment charging seven individuals associated with APT31, a Chinese state-sponsored hacking group, with conspiracy to commit computer intrusions and wire fraud. The indictment, announced on March 25, 2024, sheds light on APT31’s extensive cyber operations targeting perceived critics of China, U.S. businesses, and political officials over a span of approximately 14 years.
The defendants, identified as Ni Gaobin, Weng Ming, Cheng Feng, Peng Yaowen, Sun Xiaohui, Xiong Wang, and Zhao Guangzong, are believed to reside in China and have allegedly operated as part of the APT31 hacking group in support of China’s Ministry of State Security’s objectives related to transnational repression, economic espionage, and foreign intelligence.

The U.S. Department of State’s Rewards for Justice (RFJ) program, individuals associated with APT31 (rewardsforjustice)
The indictment outlines APT31’s tactics, including the use of more than 10,000 malicious emails to target individuals worldwide. These emails, often disguised as legitimate news articles from prominent sources, contained hidden tracking links that transmitted sensitive information about the recipients back to the hackers. APT31 then used this information to conduct more sophisticated targeted attacks, compromising victims’ networks, email accounts, cloud storage, and telephone call records.
The indictment also highlights APT31’s targeting of U.S. government officials, political figures, election campaign staff, and U.S. companies across various industries. The group’s activities included attempts to gather economic plans, intellectual property, and trade secrets, contributing to significant financial losses for American businesses.
Moreover, APT31 targeted dissidents and individuals supporting dissident causes globally, including surveillance and intrusions into the networks of activists and organizations critical of the Chinese government.
For further details about the indictment and charges you may refer to court’s statement.
APT31 Techniques and Modus Operandi
According to the indictment APT31 has ties to the Hubei State Security Department in Wuhan. Around 2010, APT31 established a front company named “Wuhan XRZ” to conceal its cyber operations, leveraging another local entity called “Wuhan Liuhe” for support, although the latter was not directly implicated as an MSS front.
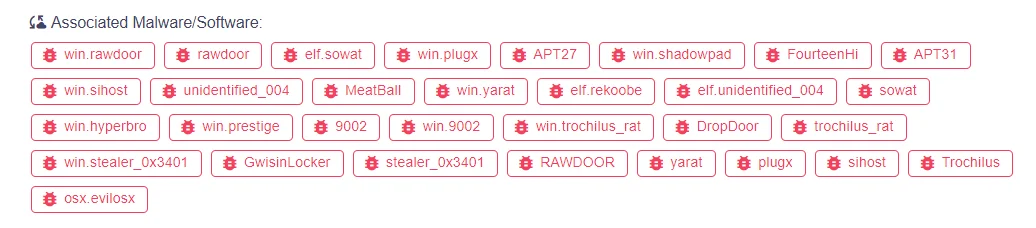
Associated Malware with APT31
APT31 was observed employing a dual-phase approach, initiating emails purportedly from prominent US journalists sent to potential victims. These emails included snippets from genuine news articles along with tracking links, presumably leading to the full article. Clicking these links provided attackers with initial data, such as the device type used to open the email and the recipient’s public IP address. Notably, between June and September 2018 alone, over 10,000 tracking emails were dispatched.
Subsequently, armed with this gleaned information (T1598.003), APT31 proceeded to launch direct hacking endeavors against the victims’ devices. The indictment specifically highlights APT31’s targeting of victims’ family members, allowing them to exploit less secure home routers rather than more fortified corporate networks. This strategic shift towards targeting Small Office/Home Office (SOHO) devices aligns with findings from ANSSI’s report in December 2021.
Initially, APT31 employed various malware families like RAWDOOR, Trochilus, EvilOSX, DropDoor/DropCat, employing DLL side-loading for staging. However, they later transitioned to utilizing cracked versions of Cobalt Strike, a legitimate software testing tool. A notable strategy of APT31 involves a two-pronged approach to hacking, targeting subsidiaries, managed service providers or even spouses of their primary targets to gain initial access.
An instance cited by the U.S. DoJ involves APT31 compromising a victim’s subsidiary, a defense contractor manufacturing military flight simulators, as a stepping stone to infiltrate the core network. This operation involved leveraging a local privilege escalation 0-day exploit followed by an SQL injection.
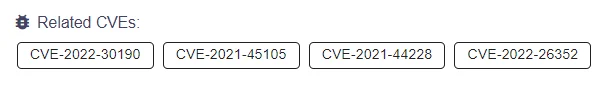
Related CVEs for APT31
While APT31 leans towards server-side exploitation to minimize interactions with victims in these campaigns, the indictment reveals a broader spectrum of activities. For instance, their involvement in targeting Hong Kong’s Umbrella Movement activists in 2019 showcases reliance on spear phishing emails containing malicious attachments or links. Moreover, the defendants are accused of crafting counterfeit Adobe Flash update pages to deploy the EvilOSX malware (T1036).
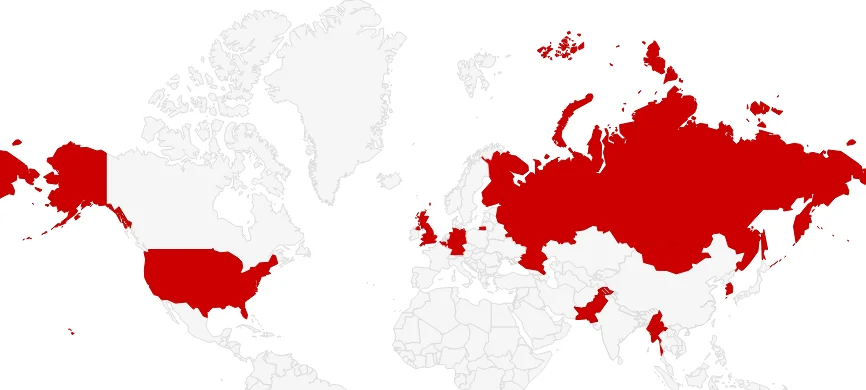
Targeted countries by APT31
A noteworthy detail in the indictment is APT31’s use of double infections for some victims, enabling them to re-access the network if the initial malware implant was detected, underscoring their sophisticated and persistent tactics.
Conclusion
APT31, a Chinese cyber-espionage group, has posed a persistent and evolving threat since its emergence. The tactics employed by APT31 are multifaceted and sophisticated. They encompass a wide range of techniques, from spear phishing emails and exploiting software vulnerabilities to custom-built malware. This adaptability and evolution in tactics render APT31 a highly dangerous threat actor.
The global scope and dynamic nature of APT31’s operations underscore the critical need for vigilance and robust cybersecurity measures. As APT31 continues to refine its tactics and strategies, organizations must also enhance their defenses to effectively counter these threats.
Security Recommendations Against APT31
Educate and Train Staff: Conduct regular training sessions to help staff recognize and mitigate phishing attempts and malicious attachments, especially spear-phishing emails.
Keep Software Updated: Ensure all software is regularly updated to patch known vulnerabilities, reducing potential avenues for unauthorized access by APT31.
Implement Multi-Factor Authentication (MFA): Utilize MFA, particularly for critical systems and data, to add an extra layer of security even if passwords are compromised.
Monitor for Suspicious Activity: Regularly monitor networks and systems for any unusual or suspicious activity that may indicate a breach or intrusion.
Use Security Software: Employ robust security software capable of detecting and blocking malware and other malicious activities associated with APT31.
Collaborate and Share Information: Foster collaboration with other organizations and government agencies to share threat intelligence and best practices for defense against APT31.
Develop an Incident Response Plan: Establish a comprehensive incident response plan to swiftly and effectively respond to security incidents, including breaches attributed to APT31.
By implementing these proactive measures, organizations can significantly reduce their risk of falling victim to APT31 and other cyber-espionage groups. Cyber Threat Intelligence plays a crucial role in staying ahead of specific threats like APT31 by identifying vulnerabilities and enabling preemptive actions to mitigate potential risks.
MITRE ATT&CK Techniques
Below are the techniques used by ZIRCONIUM or APT31 in MITRE.
| ID | Name | Use |
| T1583.001 | Acquire Infrastructure: Domains | ZIRCONIUM purchased domains for targeted campaigns. |
| T1583.006 | Acquire Infrastructure: Web Services | ZIRCONIUM used GitHub to host malware linked in spearphishing emails. |
| T1547.001 | Boot or Logon Autostart Execution | ZIRCONIUM created a Registry Run key for persistence with a malicious binary. |
| T1059.003 | Command and Scripting Interpreter: Cmd | ZIRCONIUM opened a Windows Command Shell on a remote host. |
| T1059.006 | Command and Scripting Interpreter: Python | ZIRCONIUM used Python-based implants for interaction with compromised hosts. |
| T1555.003 | Credentials from Password Stores | ZIRCONIUM stole credentials from web browsers. |
| T1140 | Deobfuscate/Decode Files or Information | ZIRCONIUM used AES256 decryption for exploit code. |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | ZIRCONIUM utilized AES encrypted communications in C2. |
| T1041 | Exfiltration Over C2 Channel | ZIRCONIUM exfiltrated files via the Dropbox API C2. |
| T1567.002 | Exfiltration Over Web Service | ZIRCONIUM exfiltrated data to Dropbox. |
| T1068 | Exploitation for Privilege Escalation | ZIRCONIUM exploited CVE-2017-0005 for local escalation. |
| T1105 | Ingress Tool Transfer | ZIRCONIUM downloaded malicious files to compromised hosts. |
| T1036.004 | Masquerading: Masquerade Task or Service | ZIRCONIUM used a run key for masking a persistence mechanism. |
| T1027.002 | Obfuscated Files or Information: Packing | ZIRCONIUM used multi-stage packers for exploit code. |
| T1566.002 | Phishing: Spearphishing Link | ZIRCONIUM used malicious links in emails for malware delivery. |
| T1598.003 | Phishing for Information | ZIRCONIUM targeted presidential campaign staffers with credential phishing emails. |
| T1012 | Query Registry | ZIRCONIUM queried the Registry for proxy settings. |
| T1218.007 | System Binary Proxy Execution: Msiexec | ZIRCONIUM used msiexec.exe for downloading and executing malicious MSI files. |
| T1082 | System Information Discovery | ZIRCONIUM captured processor architecture for C2 registration. |
| T1016 | System Network Configuration Discovery | ZIRCONIUM enumerated proxy settings. |
| T1033 | System Owner/User Discovery | ZIRCONIUM captured usernames for C2 registration. |
| T1124 | System Time Discovery | ZIRCONIUM captured system time for C2 registration. |
| T1204.001 | User Execution: Malicious Link | ZIRCONIUM used malicious links for malware downloads. |
| T1102.002 | Web Service: Bidirectional Communication | ZIRCONIUM used Dropbox for bidirectional C2 communication and execution of commands. |
Latest IoCs for APT31
Below are the latest IoCs for APT31 in SOCRadar Platform
SHA-256 Hashes:
74f7a3b2a5df81eb7b5e0c5c4af8548e61dc37c608dda458b75b58852f2f2cfd
f332a941d786148a35cec683edb965ea4bbd6ff6bd871880f30dc7d42b922443
6f9512a5f2f86938075b14e34928d07cdc78f46ed9401dea799f131f7a3d9644
c3056e39f894ff73bba528faac04a1fc86deeec57641ad882000d7d40e5874be
e98d8ae395ec7d2bbc29c21fa2bf79e26ada9d8bd5098487027b32aeae8b03b7
6a9979638d4e4719cfef65bdd6e1d7c0b28b84df9ca73a3bc1e919e9a1df50df
7fda8879c55398434ab0f423b0f1c75658bddd925d90437ad2e6fd8723cb1d78
bd3be94afa57936741a5debde1eff537dcd7c7bc79ccfa9739c4614efc424eeb
e89079508dca536019535bb021ae388a990d9cb64e1e6bd769e6a29ec237d8be
52238d884006a06e363e546dcfa88c1b2cbdadd80c717e415ac26956900f40bf
697db25145c2d37f0a521b3ca6b49f1f4d7c3e0c2e57804f5317b3d0b6d242fb
For more detailed information about Chinese and Russian threat actors and their threat landscape, please see our relevant report.
Source: https://socradar.io/dark-web-profile-apt31/
Views: 0
