In late 2023, a new and distinct ransomware group named 3AM Ransomware emerged. It came to the forefront as a fallback for other ransomware, notably during failed deployments of the infamous LockBit ransomware and later their interesting choice in their website.
First reported by Symantec, the discovery and emergence of 3AM Ransomware marked a notable and interesting event in the cybercrime world. As stated initially, 3AM came to light as a secondary option for cybercriminals, particularly when their attempts to deploy the well-known LockBit ransomware were unsuccessful.
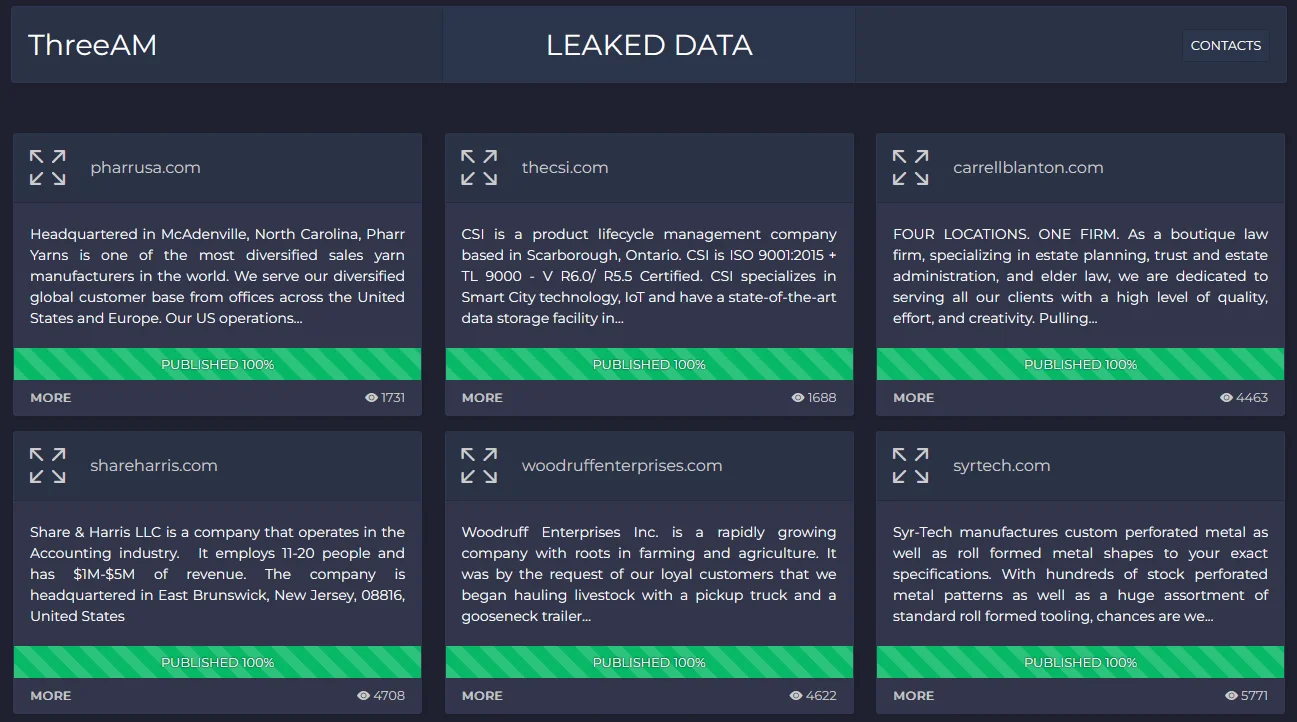
ThreeAM’s Onion Leak Site
Who is 3AM Ransomware
3AM or ThreeAM seems to be a Russian-speaking group, as it is used by other threat actors who also have the LockBit variant and mostly targets Western-affiliated countries. However, they are not just a secondary option, 3AM Ransomware distinguishes itself through its unique technical characteristics. Notably, it is developed using Rust, setting it apart as a novel entity in the ransomware family. Functioning as a 64-bit executable, is designed to disrupt applications, backup systems, and security software. It targets specific files, renames them with a “.threeamtime” extension, and aims to eliminate Volume Shadow copies, showcasing its destructive capabilities.

Threat Actor Card
Modus Operandi
3AM Ransomware’s operational sequence involves meticulous pre-encryption activities, targeting and disabling specific services, particularly those related to security and backup, from well-known vendors.
As stated in a blog post of Speartip, tactics of 3AM Ransomware exhibit a calculated approach to cyberattacks. Initially, 3AM begins its operation by using the “gpresult” command to extract policy settings from the target system. This is followed by a reconnaissance phase involving various commands for network and server enumeration, establishing persistence, and data exfiltration using tools like the Wput FTP client. The malware is also known to employ command-line parameters for targeted operations, which include specifying the encryption method and controlling the encryption speed.
Once these services are neutralized, 3AM initiates its file encryption process, appending a unique ‘.threeamtime’ extension to encrypted files. Furthermore, it attempts to delete Volume Shadow copies, a tactic aimed at hindering data recovery efforts. These technical nuances of 3AM Ransomware reveal a somewhat sophisticated approach to cyberattacks, emphasizing the importance of understanding its mechanics in cybersecurity defense strategies. However, 3AM employs conventional ransomware extortion methods. Initially, it transfers the target data to the attacker, followed by the encryption of these exfiltrated files, a typical approach in ransomware operations.
Following encryption, the ransomware generates a TXT file named “RECOVER-FILES” in each scanned folder, containing the ransom note:
Hello. "3 am" The time of mysticism, isn't it?
All your files are mysteriously encrypted, and the systems "show no signs of life", the backups disappeared. But we can correct this very quickly and return all your files and operation of the systems to original state.
All your attempts to restore data by himself will definitely lead to their damage and the impossibility of recovery. We are not recommended to you to do it on our own!!! (or do at your own peril and risk).
There is another important point: we stole a fairly large amount of sensitive data from your local network: financial documents; personal information of your employees, customers, partners; work documentation, postal correspondence and much more.
We prefer to keep it secret, we have no goal to destroy your business. Therefore can be no leakage on our part.
We propose to reach an agreement and conclude a deal.
Otherwise, your data will be sold to DarkNet/DarkWeb. One can only guess how they will be used.
Please contact us as soon as possible, using Tor-browser:
http://threeam7[REDACTED].onion/recovery
Access key:
[32 CHARS SPECIFIED BY -k COMMAND LINE PARAMETER]Attack Scheme in Failed LockBit Deployment
According to findings by Symantec researchers, during an unsuccessful LockBit attack, malicious actors introduced the 3AM ransomware onto three computers within the target organization’s network. Nevertheless, their efforts faced resistance, as two of these machines were able to fend off the attack.
The assailants were observed utilizing the post-exploitation utility known as Cobalt Strike. Subsequently, they initiated reconnaissance commands such as “whoami,” “netstat,” “quser,” and “net share” to facilitate lateral movement within the network. To ensure their persistence, the attackers introduced a new user. Furthermore, they employed the Wput tool to transfer files to their FTP server.
Following a successful attack, the perpetrators patiently await communication from the victims. To facilitate ransom negotiations, a TOR support portal for the 3AM ransomware has been established, allowing interactions with victims regarding ransom payments.
Also check out our article on the subject.
Targets and Impact
Since the group’s leak site emerged, various victims have been shared and removed, and this leaves some question marks, but there are currently 23 victims on the leak site and only those whose data is 100% published are listed. At the same time, they do not use an uploading service or torrent to download this data, they host download links on their own leak sites.
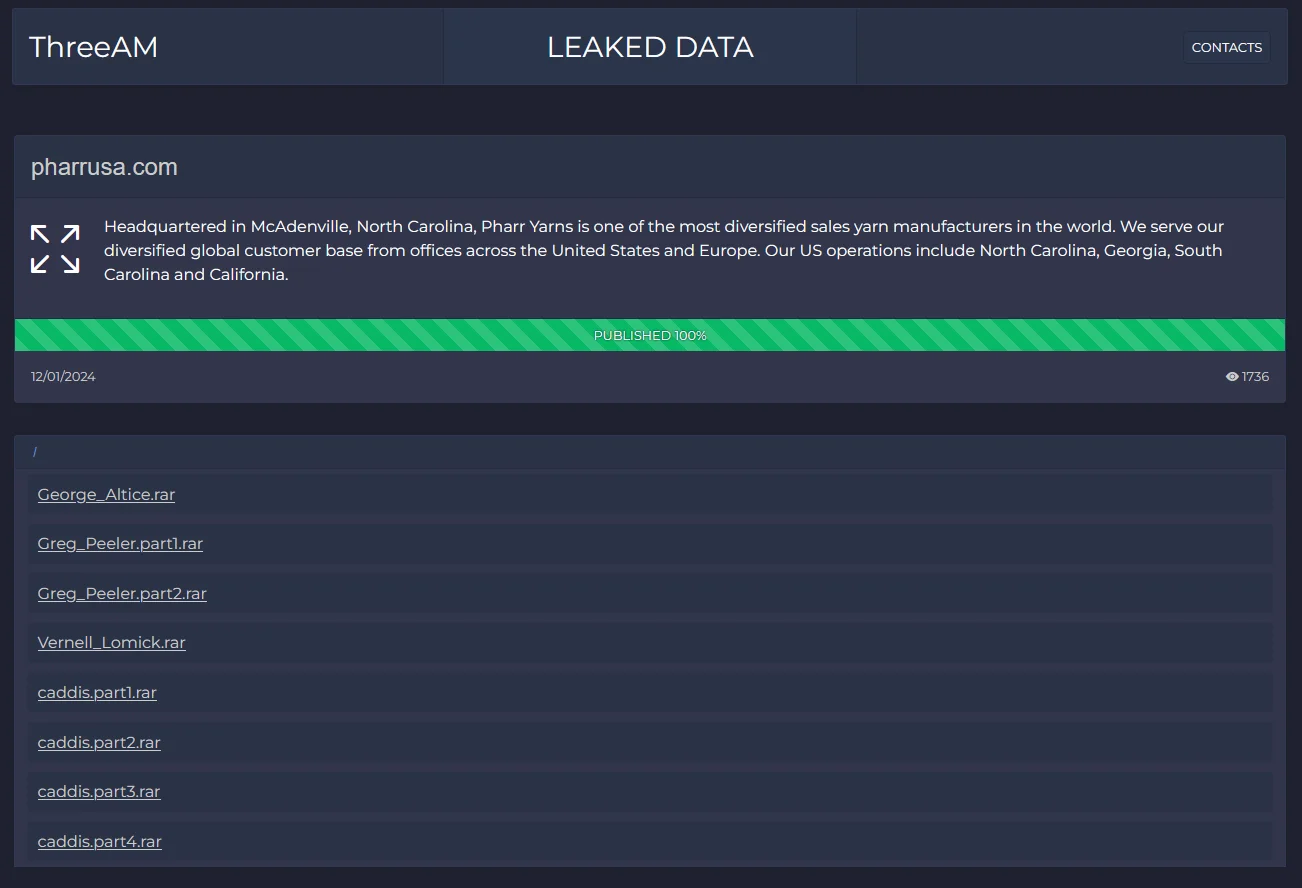
Leaked data is published under the victim’s related page
One of the victims on the leak site is located in Malaysia, but all the others are from NATO member countries. Almost 3/4 of the targets are US-based companies. After the US, UK and France comes.
The impact and reach of 3AM Ransomware, while currently limited, reveal its potential as a significant threat. Its usage, primarily as a fallback option in a few incidents, has so far resulted in successful encryption on a small number of systems. This limited impact, however, demonstrates the effectiveness of current cybersecurity defenses, which have been able to mitigate and contain 3AM’s activities in several instances. Nonetheless, the emergence of 3AM highlights the need for continued vigilance and adaptation in cybersecurity practices, as new threats like this may evolve to become more widespread and damaging.
Alleged Ties and What to Come?
Most lately, security researchers at Intrinsec have discovered strong connections between the 3AM ransomware operation and well-known cybercrime groups, including the Conti syndicate and the Royal ransomware gang according to BleepingComputer’s news. Moreover, 3AM has also adopted a new extortion tactic by publicizing data leaks on the victim’s social media followers and using automated bots to respond to high-ranking accounts on the X (formerly Twitter) platform, directing them to the data leaks.
Intrinsec’s analysis found significant overlaps in communication channels, infrastructure, and tactics between 3AM and the Conti syndicate. They also discovered evidence such as shared IP addresses and the use of specific tools and malware that linked these groups.
Additionally, 3AM ransomware was found to have used automated Twitter bots to respond to tweets from victims and high-profile accounts, directing them to the data leak site. This tactic aimed to spread news of successful attacks and damage the reputation of victims. It was deployed with one victim but did not yield the expected results.
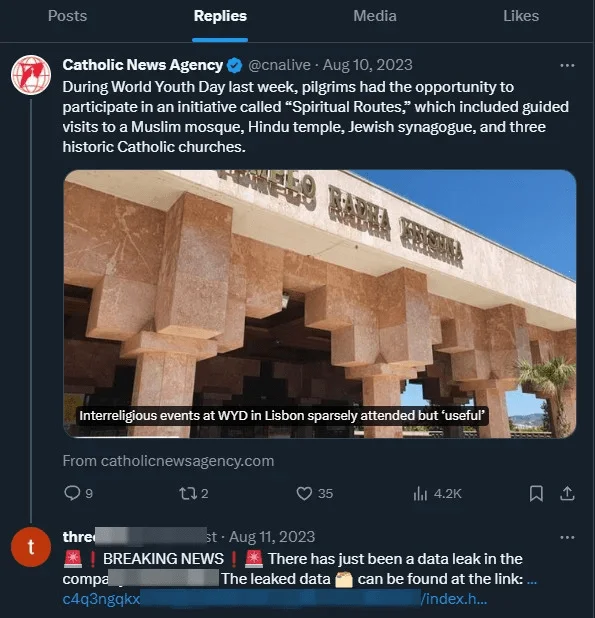
ThreeAM’s X bots. (BleepingComputer)
So, ThreeAM ransomware appears to have strong connections with the Conti Ransomware and the Royal ransomware gang. They have adopted new tactics, including using social media to publicize data leaks, and are considered a potential threat with the ability to carry out a significant number of attacks despite being a less sophisticated subgroup of Royal.
The existence of 3AM Ransomware in the digital landscape could be concerning. While its emergence as a secondary option to more established ransomware indicates a potential shift in the tactics of cybercriminals. As 3AM gains attention, it might attract interest from other malicious actors, leading to its evolution and possible increase in sophistication and reach in 2024. This underscores the need for the cybersecurity community to remain alert and adapt to these evolving threats. The continued development and deployment of 3AM could pose new challenges, making it imperative for cybersecurity strategies to evolve in tandem to effectively counter this and similar emerging threats.
You can also check out our blog post for the not-so-new tactics of this potential and new threat.
Conclusion
The rise of 3AM Ransomware highlights the dynamic and ever-changing nature of cyber threats. While its current impact is limited, its potential for future growth and sophistication serves as a reminder of the ongoing challenges in cybersecurity. This new ransomware underscores the importance of continuous vigilance and adaptive defense strategies in the digital realm. As cybercriminals evolve, so must our approaches to cybersecurity, ensuring preparedness for both current and emerging threats in this perpetual cat-and-mouse game.
SOCRadar provides proactive threat monitoring and intelligence to enhance your organization’s security. The platform offers the ability to search for specific threat actors and access detailed information about them, including their targeted vulnerabilities, affiliations with other actors, and indicators of compromise. Additionally, you can continuously monitor their activities to ensure ongoing readiness against potential threats.
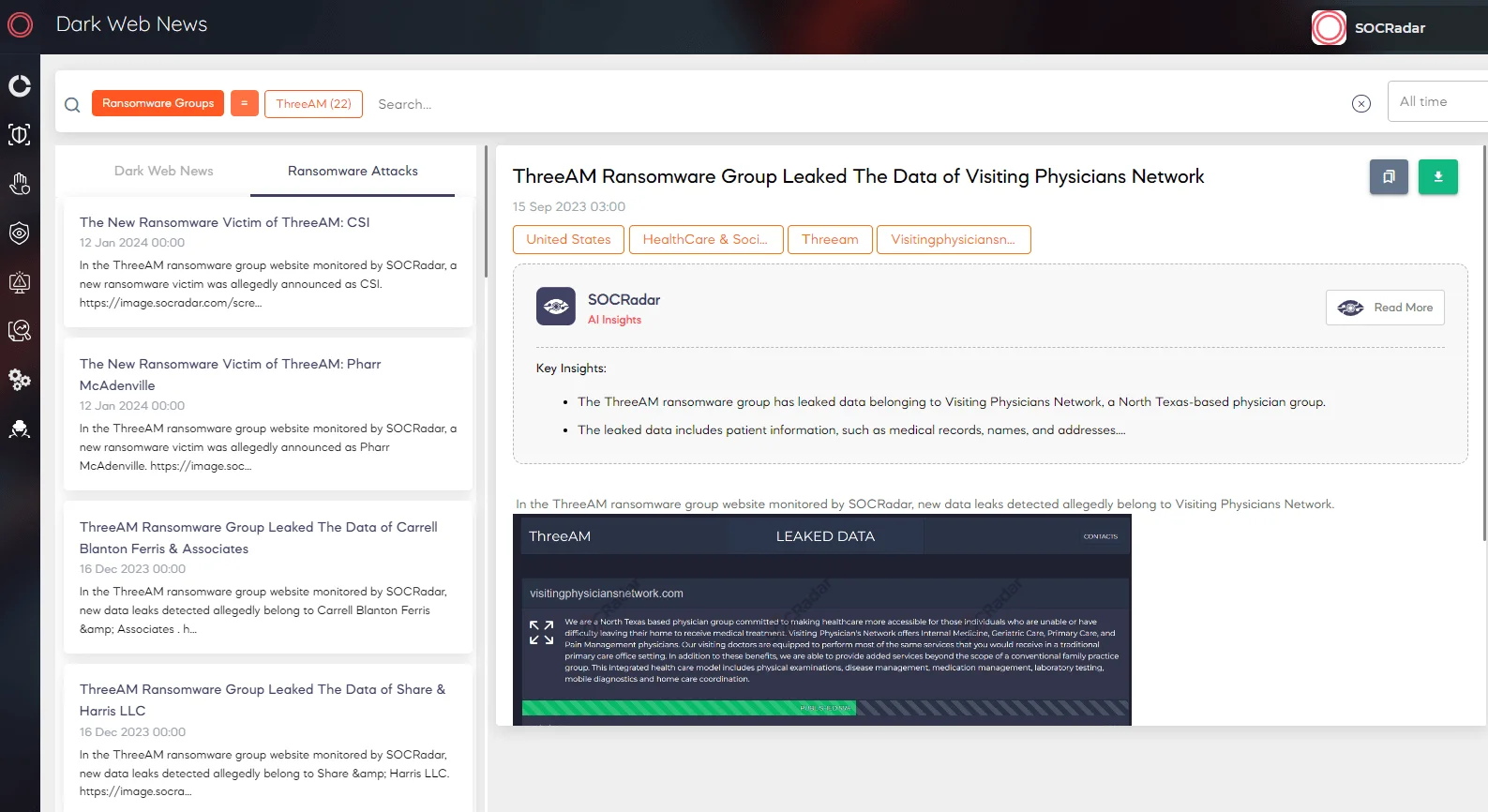
SOCRadar Dark Web News, Ransomware Attacks
In addition to many features of the SOCRadar Platform, you can also search for threat actors to follow new ransomware groups and related news.
Possible MITRE ATT&CK Framework TTPs
| Tactic | Technique ID | Technique Name | Use |
| Execution | T1053 | Scheduled Task/Job | Potentially used by 3AM for execution of ransomware or maintaining persistence in the system. |
| Defense Evasion | T1082 | System Information Discovery | 3AM uses “gpresult” and other commands to gather information and potentially evade defenses based on system configs. |
| T1140 | Deobfuscate/Decode Files or Information | Could be implied in the encryption process or in how 3AM handles the deletion of Volume Shadow Copies. | |
| T1490 | Inhibit System Recovery | Specifically targets backup systems and Volume Shadow Copies to hinder recovery efforts. | |
| Discovery | T1082 | System Information Discovery | Employing reconnaissance commands like “whoami,” “netstat,” “quser,” to discover network and server information. |
| T1083 | File and Directory Discovery | Implied through the encryption process targeting specific files. | |
| T1518 | Software Discovery | Targeting and disabling security services from well-known vendors. | |
| Lateral Movement | T1021 | Remote Services: SMB/Windows Admin Shares | Utilizes Cobalt Strike for lateral movement and the Wput tool for data exfiltration. |
| Collection | T1005 | Data from Local System | Data is collected before encryption, including sensitive info. |
| T1056 | Input Capture | Implied through the collection of sensitive data from the local network. | |
| Command and Control | T1071 | Application Layer Protocol: Web Protocols | Use of TOR for command and control communications. |
| Exfiltration | T1041 | Exfiltration Over C2 Channel | Exfiltrates data to attacker-controlled servers using FTP transfer before encryption. |
| Impact | T1486 | Data Encrypted for Impact | Encrypts files with a “.threeamtime” extension, disrupts backup systems, and deletes Volume Shadow copies. |
| T1491 | Defacement | Generating a ransom note in encrypted directories, which could be considered a form of defacement. | |
| T1499 | Endpoint Denial of Service | By encrypting files and possibly disabling critical services, 3AM can cause a denial of service to affected systems. |
Source: Original Post