Threat Actor: CyberNiggers | CyberNiggers
Victim: MedicaMall | MedicaMall
Price: $500
Exfiltrated Data Type: Personal and transactional data
Key Points :
- A threat actor claimed responsibility for a data breach involving over 70,000 customers.
- Compromised data includes full names, phone numbers, addresses, email addresses, payment methods, and shipping/billing details.
- The breach reportedly occurred on August 29, 2024.
- MedicaMall is known for offering a wide range of medical products.
Threat Actor: grep | grep
Victim: Supreme Court of Philippines | Supreme Court of Philippines
Price: Not specified
Exfiltrated Data Type: 13,564 rows of court-related data
Key Points :
- The breach allegedly impacted data belonging to applications, court cases, and other services.
- Leaked data includes assessment numbers, full names, collection types, payments, and details of various court cases.
- The threat actor included a sample of the leaked data in their post.
Threat Actor: SILKFIN AGENCY | SILKFIN AGENCY
Victim: DimeCuba | DimeCuba
Price: Not specified
Exfiltrated Data Type: SMS records, email records, transaction details
Key Points :
- The breach reportedly compromised over 1 million SMS records and more than 100,000 email records.
- Data includes private information from cardsims, admin and reseller records, and various user transaction details.
- The breach occurred on August 26, 2024, and samples of the stolen data were released by the attackers.
Threat Actor: (unknown) | unknown
Victim: Federación Española de Balonmano | Federación Española de Balonmano
Price: Not specified
Exfiltrated Data Type: 70,000 records
Key Points :
- The breach reportedly involves approximately 70,000 records containing valid DNI and mobile numbers.
- Compromised data includes sensitive information such as DNI, full names, phone numbers, dates of birth, and addresses.
- The accuracy of the claim remains unverified, and the situation is being monitored closely.
Threat Actor: (unknown) | unknown
Victim: Isuzu Motors International Operations (Thailand) | Isuzu Motors International Operations (Thailand)
Price: $500
Exfiltrated Data Type: Unauthorized VPN access
Key Points :
- The threat actor claims to offer unauthorized access to the Palo Alto Networks VPN of Isuzu Motors.
- Access includes full VPN entry into Isuzu’s network, potentially exposing sensitive corporate information.
- The company operates in the architecture, engineering, and design industry in Thailand.
Threat Actor: (unknown) | unknown
Victim: Major French Advertising and Technology Company | Major French Advertising and Technology Company
Price: $1,500
Exfiltrated Data Type: Sensitive data and system access
Key Points :
- The threat actor claims to have gained unauthorized access to the systems of a leading advertising and technology company in France.
- Access includes customer servers, critical company details, internal communications, and sensitive customer data.
- The hacker states they have control over the company’s chat system, allowing them to monitor confidential discussions.
Threat Actor: (unknown) | unknown
Victim: Major Israeli Health Fund | Major Israeli Health Fund
Price: 2 BTC
Exfiltrated Data Type: Personal data of 1.3 million customers
Key Points :
- The breach allegedly obtained personal data of 1.3 million customers from a major health fund in Israel.
- Compromised data includes full names, identity card numbers, dates of birth, addresses, phone numbers, and email addresses.
- The threat actor is reportedly selling the entire dataset for 2 BTC, with payment to be made exclusively in Bitcoin.
Threat Actor: (unknown) | unknown
Victim: Spanish Athletics Federation | Spanish Athletics Federation
Price: Not specified
Exfiltrated Data Type: Sensitive personal information of approximately 140,000 individuals
Key Points :
- The breach reportedly leaked a portion of the database containing sensitive personal information.
- The compromised data includes DNI numbers, full names, phone numbers, dates of birth, and addresses.
- The threat actor claimed that the data is fully formatted with no duplicates or invalid DNI numbers.
Threat Actor: (unknown) | unknown
Victim: Israeli Mobile Website | Israeli Mobile Website
Price: $2,000
Exfiltrated Data Type: Admin access
Key Points :
- The threat actor is offering admin access to a mobile website in Israel, including full control over the site’s gift card system.
- This access allows browsing the website’s backend, modifying user accounts, and changing site settings.
- The seller is allegedly offering this high-level access for $2,000, with payment to be made in Bitcoin.
hourly
1
The post Threat Actor Offers Alleged Access to Large Israeli IT Company appeared first on Daily Dark Web.
]]>The threat actor has set the selling price at $150,000, with payment only accepted in Bitcoin. The post highlights that the transaction details and further communication will be conducted through encrypted messaging platforms, providing a Tox ID and a Telegram link for potential buyers.
The post Threat Actor Offers Alleged Access to Large Israeli IT Company appeared first on Daily Dark Web.
]]>
The post A Threat Actor Alleged Data Breach of Federación Española de Balonmano appeared first on Daily Dark Web.
]]>The compromised data includes sensitive information such as DNI, full names, phone numbers, dates of birth, and addresses. The database is said to be fully formatted, with no duplicates or invalid DNIs. The breach allegedly affects individuals within Spain.
The accuracy of this claim remains unverified, and the situation is being monitored closely. The potential impact on the affected individuals could be significant if the data is confirmed to have been compromised.
The post A Threat Actor Alleged Data Breach of Federación Española de Balonmano appeared first on Daily Dark Web.
]]>
The post MedicaMall Allegedly Breached by CyberNiggers, Customer Data Exposed appeared first on Daily Dark Web.
]]>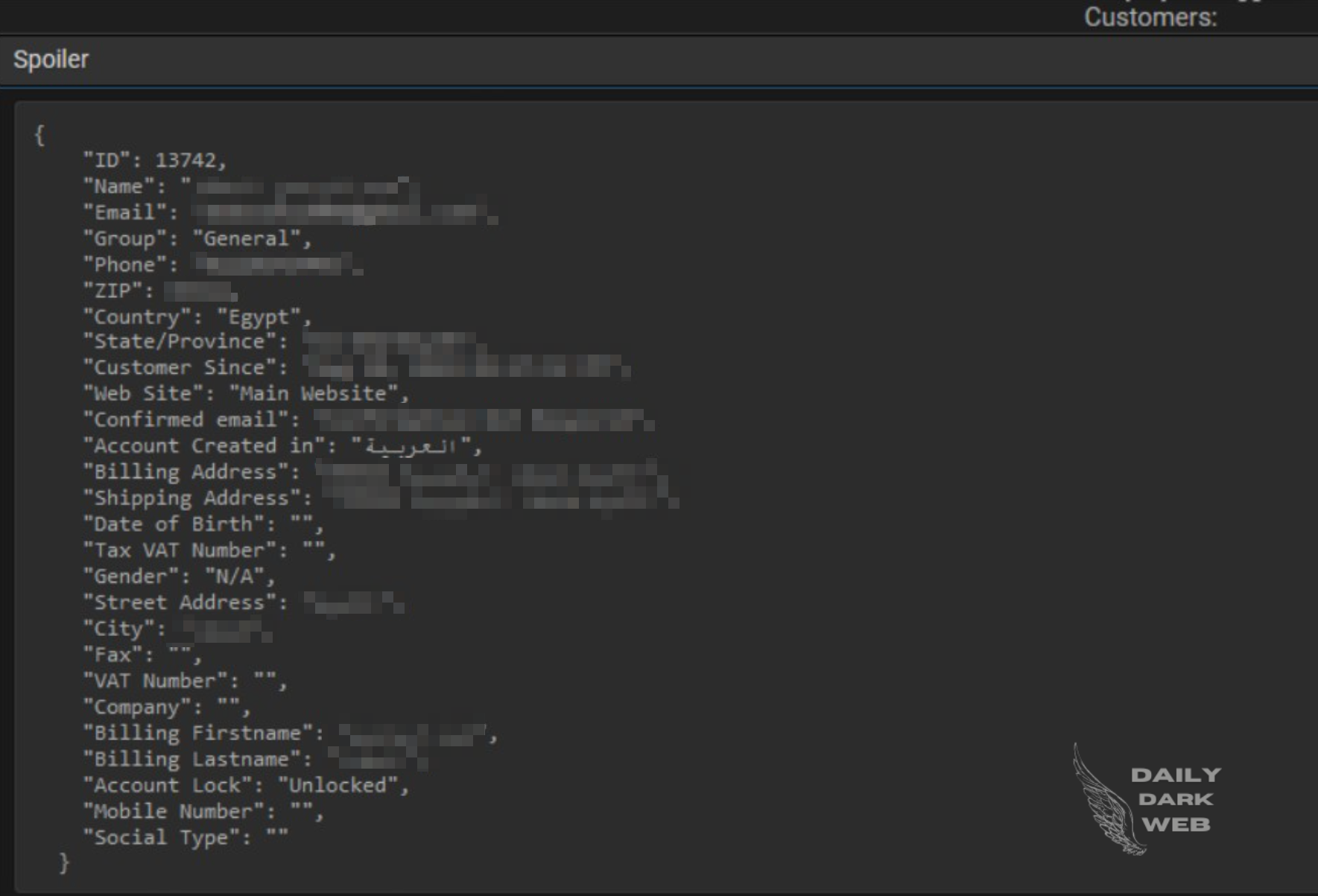
MedicaMall, known for offering a wide range of medical products such as surgical instruments and comprehensive medical equipment, now faces the potential fallout from this breach.
The post MedicaMall Allegedly Breached by CyberNiggers, Customer Data Exposed appeared first on Daily Dark Web.
]]>
The post Threat Actor Claims to Sell Unauthorized VPN Access to Isuzu Motors International Operations (Thailand) appeared first on Daily Dark Web.
]]>According to the threat actor’s announcement, the access being sold includes full VPN entry into Isuzu Motors International Operations’ network, potentially exposing sensitive corporate information and internal systems. The company, headquartered in Thailand with 76 employees, is a critical part of Isuzu’s international operations. The alleged sale of such access poses a significant risk, not only to Isuzu but also to its partners and customers, highlighting the increasing threats faced by companies in today’s digital landscape.
The post Threat Actor Claims to Sell Unauthorized VPN Access to Isuzu Motors International Operations (Thailand) appeared first on Daily Dark Web.
]]>
The post Threat Actor Claims to Sell Access to Major French Advertising and Technology Company appeared first on Daily Dark Web.
]]>In the hacker’s announcement, they claim to have successfully infiltrated the company’s systems, allowing them to view and download all files stored on customer servers. These files are said to contain highly sensitive customer data, including financial records. Additionally, the hacker states they have access to the company’s internal and sensitive information, such as employee records, financial data, and more. They also claim to have control over the company’s chat system, giving them the ability to monitor and access all conversations, including those involving confidential discussions. The breach is described as extensive, also covering other parts of the company’s infrastructure, including their website and FTP server.
The post Threat Actor Claims to Sell Access to Major French Advertising and Technology Company appeared first on Daily Dark Web.
]]>
The post Major Israeli Health Fund Allegedly Breached 1.3 Million Records Exposed appeared first on Daily Dark Web.
]]>According to the post, the compromised data includes a wide array of sensitive personal information:
- Full name
- Identity card number
- Date of birth
- Address
- Phone number
- Number of children
- Email address
- City
The threat actor is reportedly selling the entire dataset for 2 BTC, with payment to be made exclusively in Bitcoin. Interested buyers are directed to contact the seller via a provided Telegram link.
The post Major Israeli Health Fund Allegedly Breached 1.3 Million Records Exposed appeared first on Daily Dark Web.
]]>
The post Spanish Athletics Federation Allegedly Breached appeared first on Daily Dark Web.
]]>According to the post the full database originally contained around 500,000 lines of information. However, the leaked subset of the database was carefully filtered to include only entries with complete and valid data, specifically ensuring that each line contained a DNI (Spanish national identity number) and a phone number. The allegedly compromised data reportedly encompasses DNI numbers, full names, phone numbers, dates of birth, and addresses.
The threat actor claimed that the data is “FULL formatted” with no duplicates or invalid DNI numbers.
The post further included a Telegram handle, for interested parties to reach out, presumably to negotiate the sale or distribution of the data.
The post Spanish Athletics Federation Allegedly Breached appeared first on Daily Dark Web.
]]>
The post The Supreme Court of Philippines Allegedly Breached 13K Rows Published appeared first on Daily Dark Web.
]]>According to the post published by the threat actor, the compromised database includes 13,564 rows of information. The leaked data encompasses the following:
- Assessment numbers
- Full names
- Collection types
- Payments
- Details of various court cases (including types and categories)
The threat actor also included a sample data from the alleged leak.
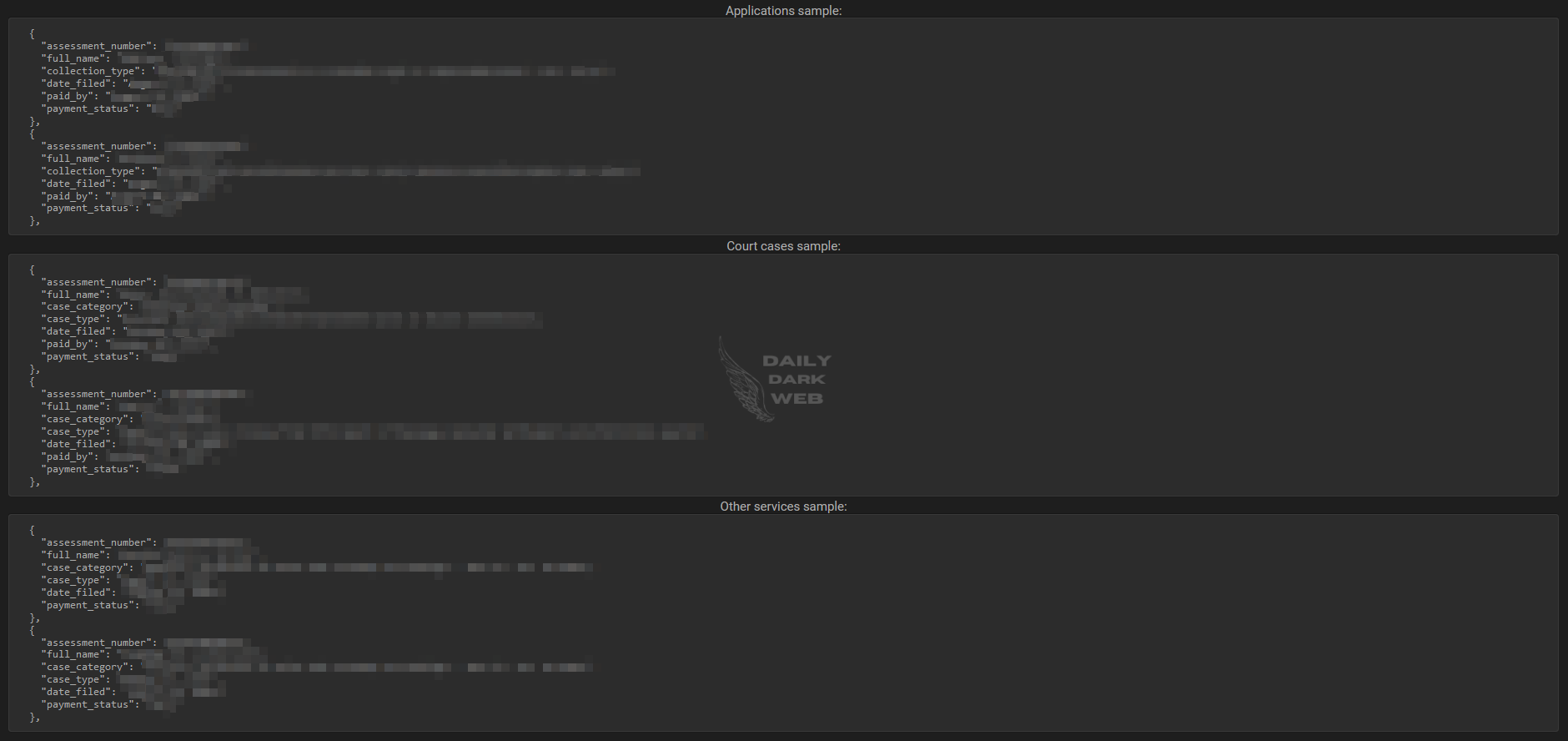
The post The Supreme Court of Philippines Allegedly Breached 13K Rows Published appeared first on Daily Dark Web.
]]>
The post Alleged Sale of Admin Access to Israeli Mobile Website appeared first on Daily Dark Web.
]]>The seller is allegedly offering this high-level access for $2,000, with the payment to be made in Bitcoin (equivalent to 0.032 BTC).
The post Alleged Sale of Admin Access to Israeli Mobile Website appeared first on Daily Dark Web.
]]>
The post Threat Actor Claimed to Breach Database of DimeCuba appeared first on Daily Dark Web.
]]>DimeCuba, widely used by Cubans living abroad, offers services such as mobile recharges, international calls, and remittances. The compromised data allegedly includes private information from cardsims, admin and reseller records, and various user transaction details. The attackers have also released samples of the stolen data to substantiate their claims.
fb_sms_history_sample: ***
card_chatsim_sample: ****
app_validation_codes_sample: ****
admin_and_resellers_sample: ****
mails_sample: ****
chase_payments_sample: ***
This breach, if verified, could have severe implications for the privacy and security of DimeCuba’s users and highlights ongoing vulnerabilities in digital platforms handling sensitive personal data.
The post Threat Actor Claimed to Breach Database of DimeCuba appeared first on Daily Dark Web.
]]>