Summary: This content discusses the activities of the threat actor ChromeConnection, who uses a decoy document to distract from their malicious actions and deploys a fileless backdoor onto the victim’s system.
Threat Actor: ChromeConnection | ChromeConnection
Victim: N/A
Key Point :
- The threat actor ChromeConnection utilizes a decoy document to divert attention from their malicious activities.
- They employ a malicious MSBuild project file that is triggered by a PowerShell script and executed via msbuild.exe.
- The project file creates a scheduled task for persistence and loads an obfuscated payload into the system.
- This payload serves as a fileless backdoor.
The content provides further technical details and a visual representation of the PowerShell script embedded in the LNK file used by ChromeConnection.
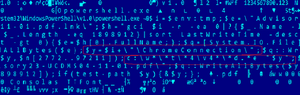
This document is a decoy which is to detract from of the malicious activities performed in the background by ChromeConnection. Said file is a malicious MSBuild project file that will be loaded by msbuild.exe after being triggered by a PowerShell script.
The project file will only work on 64-bit operating systems as the assembly file indicated in it is located in the Framework64 directory of Microsoft.Net. Upon execution of the project file “ChromeConnection” via msbuild.exe, it creates a scheduled task as part of the malware’s persistence mechanism:
/create /sc MINUTE /mo 30 /st 07:00:00 /tn "ChromeConnection" /tr "cmd /c start /min
%windir%Microsoft.NETFramework64v4.0.30319MSBuild %temp%ChromeConnection" /fAs we can see, “ChromeConnection” is started every 30 minutes, starting at 7 a.m.
Then it loads the obfuscated payload of the project file into the system. This payload is a fileless backdoor.
Source: https://www.gdatasoftware.com/blog/2024/07/37977-turla-evasion-lnk-files
“An interesting youtube video that may be related to the article above”