
EXECUTIVE SUMMARY
The CYFIRMA research team has identified an infostealer builder known as ‘Blank Grabber’ while monitoring threat actor discussions. It was released in 2022, however since then, it has been frequently updated – with 85 contributions to the project in the last one month alone. The infostealer targets Windows operating systems and possesses a wide range of capabilities aimed at stealing sensitive information from unsuspecting users (including Discord tokens, Steam and Epic sessions, browser data such as passwords, cookies, and history, as well as various other credentials and system information). The tool is also equipped with features to evade detection, disable security measures, and maintain persistence on compromised systems. Once deployed, the Blank Grabber can result in unauthorized access and theft of valuable information, including user credentials, intellectual property, and sensitive data, with potential damage, including financial losses, reputational harm, and compromised business operations.
INTRODUCTION
Blank Grabber was being vouched for by an experienced black hat malware developer/reverse engineer, who is a part of the “Stealer Developers” community. The developer of this infostealer has kept the project ‘open source’, which means that the priority of the operator is developing a reputation in the industry, rather than financial gains. The CYFIRMA research team has noted that threat actors have added this infostealer to their malware arsenal and are launching campaigns in the wild to compromise suitable targets. In this research report, we will talk about the capabilities of this malware and what organizations must do to proactively prevent these threats.
KEY FINDINGS
- The malware builder is written in python3, and the compiled malware is written in C++.
- The malware stub is often found using open-source python obfuscators to evade detection.
- As more people have utilized the technology, Blank Grabber has evolved and become far more sophisticated, with feature additions improving its scope.
- The developer is also considering enabling the infostealer to harvest Whatsapp data.
- The infostealer is being maintained by multiple developers, including but not limited to the creator of the project that goes by the alias “Blank” and the admin of BlackForums that goes by the alias “Astounding”.
- We noticed the abuse of services such as webhook[.]site, Discord and Telegram as C2s to log HTTP requests and subsequently exfiltrate data. The fact that no VPS is required by the malware makes it a highly lucrative alternative for many emerging threat actors.
- The malware uses the WMI command-line (WMIC) utility to identify and display various system information, including OS, CPU, GPU, and disk drive names; memory capacity; display resolution; and baseboard, BIOS, and GPU driver products/versions. Some of these commands were used by Aurora Stealer in late 2022/early 2023.
- We have observed that Blank Grabber is being distributed to end users using github repositories targeting users who are specifically into gaming : https://github.com/axstlinn/CELESTIAL-INJECTOR, https://github.com/theDEVVV/fps-booster-for-all-games.
BUILDER PANEL
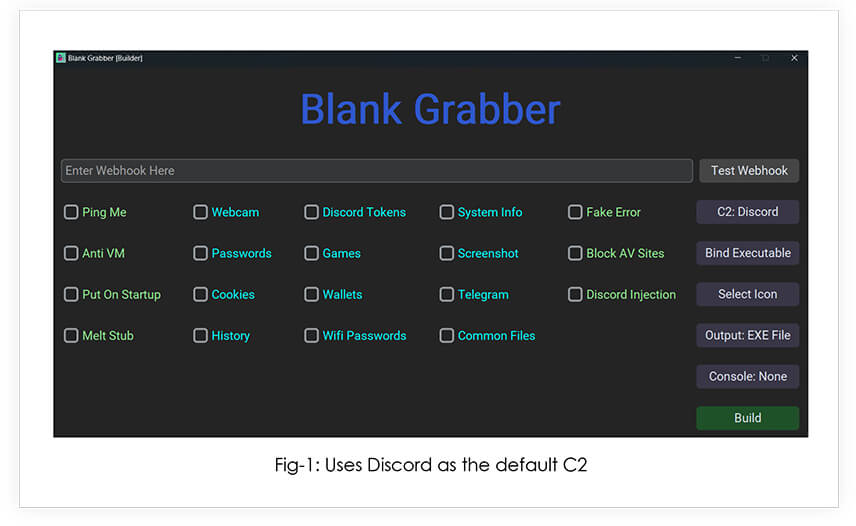
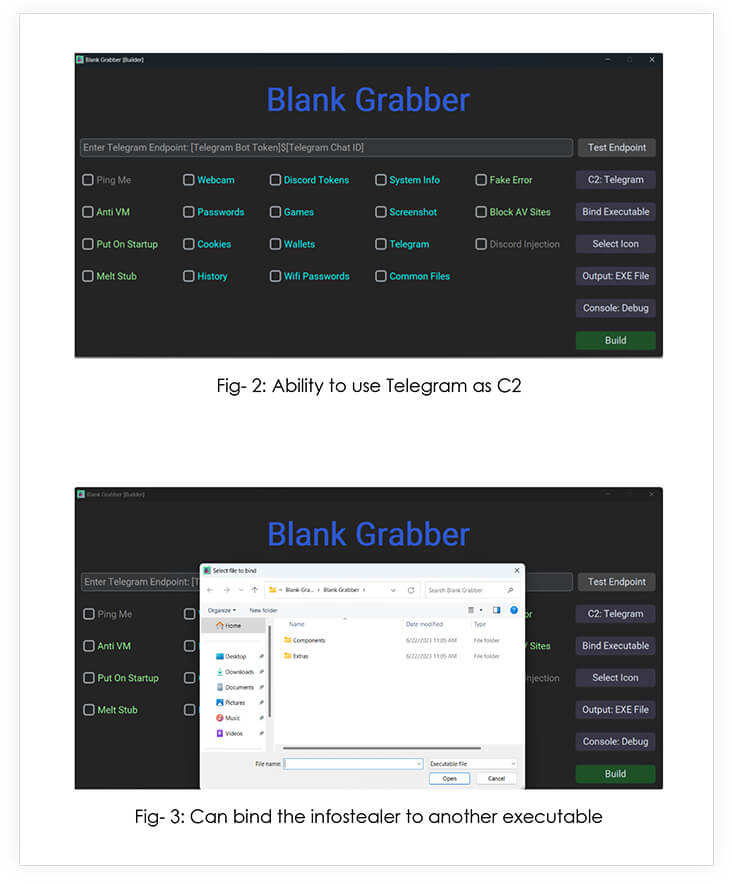
The builder code is a batch script that checks for the presence of Python and several Python libraries and installs them if they are not found. The script then starts the Python script gui.py (the builder GUI).
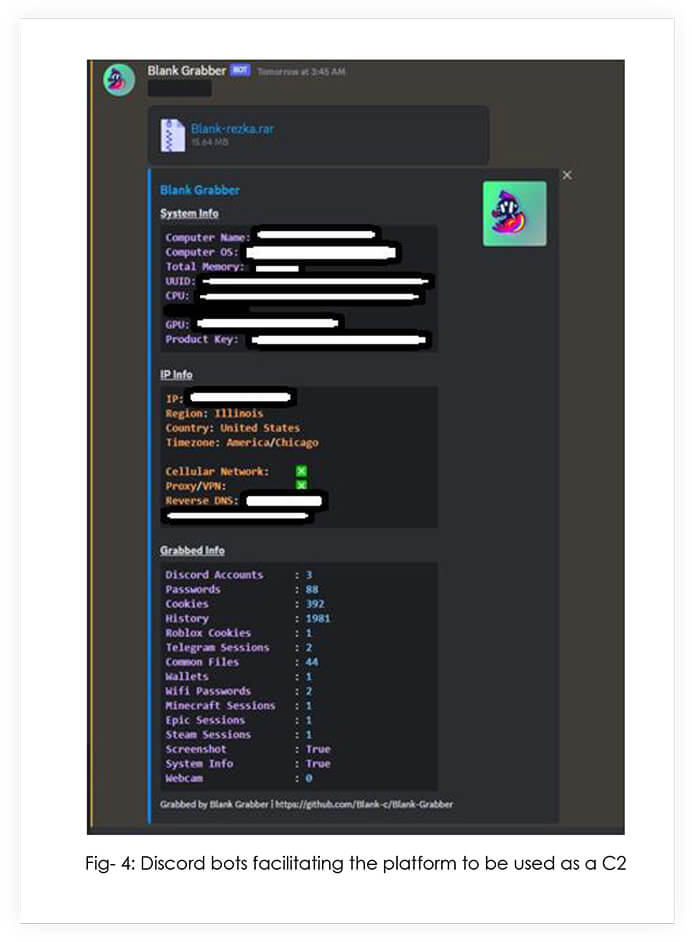
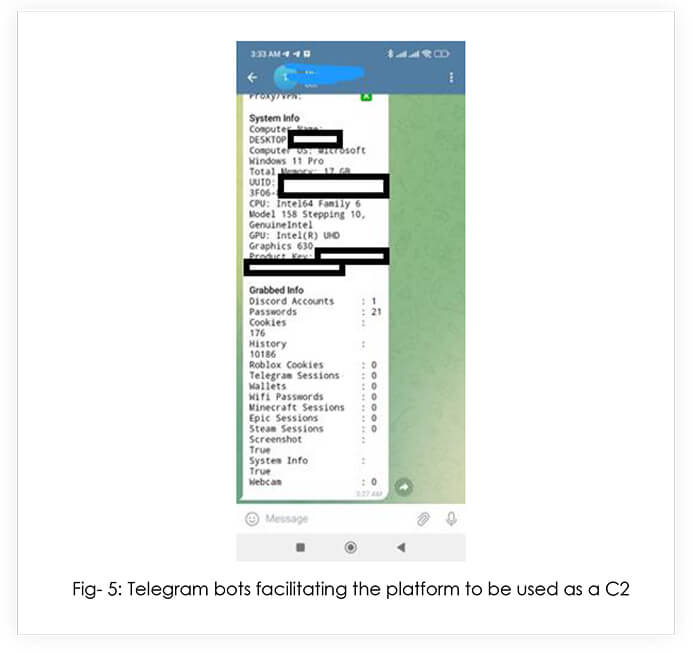
Upon execution, the infostealer harvests all the data, compresses it and sends it over to the C2 as a password protected .rar file that has a hardcoded password.
Below are some of the key features of the infostealer:
- GUI Builder.
- UAC Bypass.
- Custom Icon.
- Runs On Startup.
- Disables Windows Defender.
- Anti-VM.
- Blocks AV-Related Sites.
- Melt Stub.
- Fake Error.
- EXE Binder.
- Obfuscated Stub.
- Discord Injection.
- Grabs Discord Tokens.
- Grabs Steam Session.
- Grabs Epic Sessions.
- Grabs Passwords from Multiple Browsers.
- Grabs Cookies from Multiple Browsers.
- Grabs History from Multiple Browsers.
- Grabs Minecraft Session Files.
- Grabs Telegram Session Files.
- Grabs Wallets.
- Grabs Roblox Cookies.
- Grabs IP Information.
- Grabs System Info.
- Grabs Saved Wi-Fi Passwords.
- Steals Common Files.
- Captures Screenshot of all the Displays.
- Captures Webcam Image.
- Sends All Data Through Discord Webhooks/Telegram Bot.
ETLM
Threat Actor Profile: The operators behind the Blank Grabber infostealer are advanced and skilled malware developers, possessing a deep understanding of evasion techniques and data exfiltration methods. Their motivation is likely to build a rapport within the cybercriminal community as an entry strategy to a larger threat actor group.
Threat Landscape: The threat landscape for information stealers like the Blank Grabber is evolving and increasingly sophisticated. Cybercriminals continuously develop and distribute such tools to exploit vulnerabilities in systems and applications. The widespread use of social engineering, phishing, and malware distribution techniques amplify the risk of users inadvertently downloading and executing such stealers. Threat actors may leverage underground markets and forums to sell stolen information or use it for further malicious activities. The infostealer is being maintained by multiple developers, including the creator using the alias “Blank” and a developer/admin of BlackForums, known as “Astounding”. It is worth noting that a black hat group known as “Threatsec” is affiliated with Blackforums, so it is likely that they have employed this stealer in their malware arsenal.
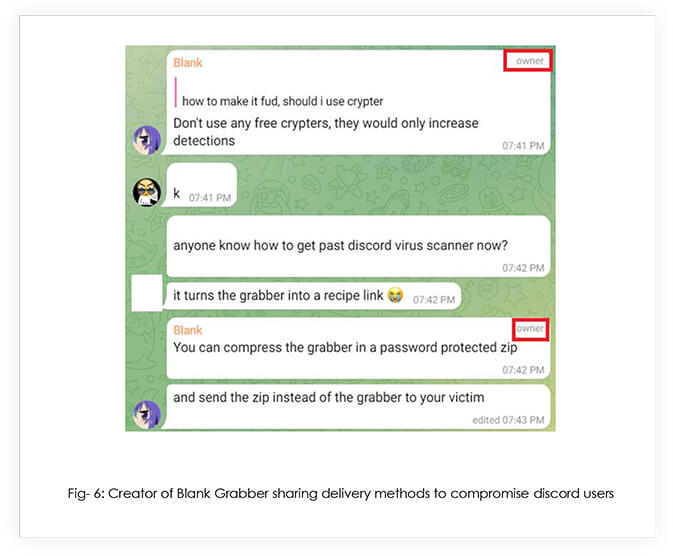
Victimology: As the malware has been gifted to the cybercriminal community by the developers, absolutely anyone is able to deploy it. Threat actors are already using the infostealer for exfiltrating data from unsuspecting users, as well as binding it with their own malware.
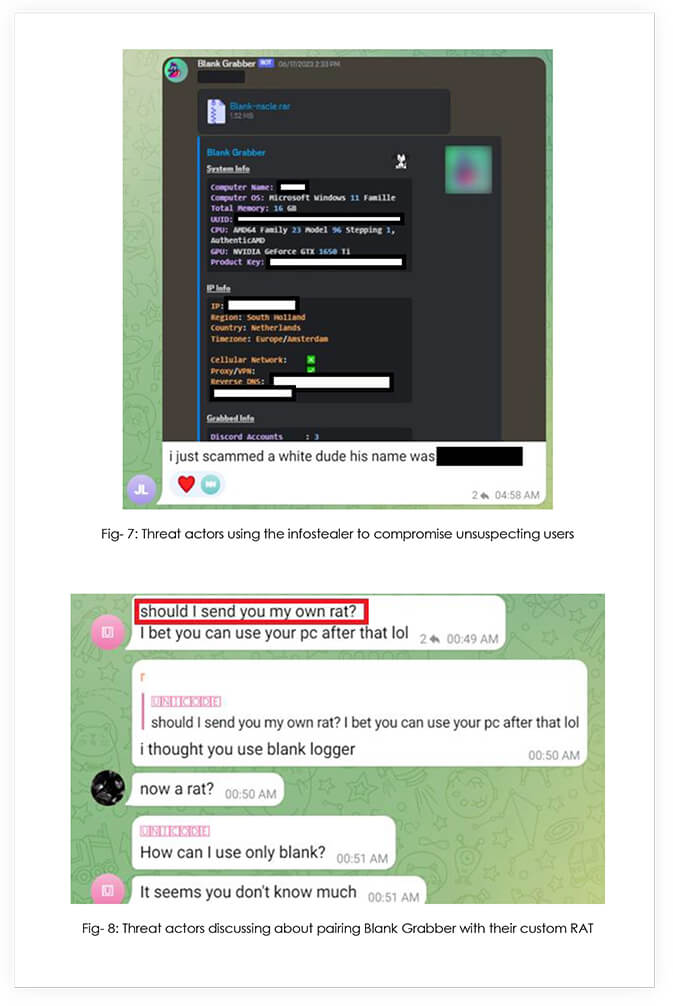
Note: CYFIRMA team was able to get the RAT being discussed above. The malware is being detected by only 1 out of 69 AV vendors. Kindly refer to the IOCs section for hash values of the RAT.
DIAMOND MODEL
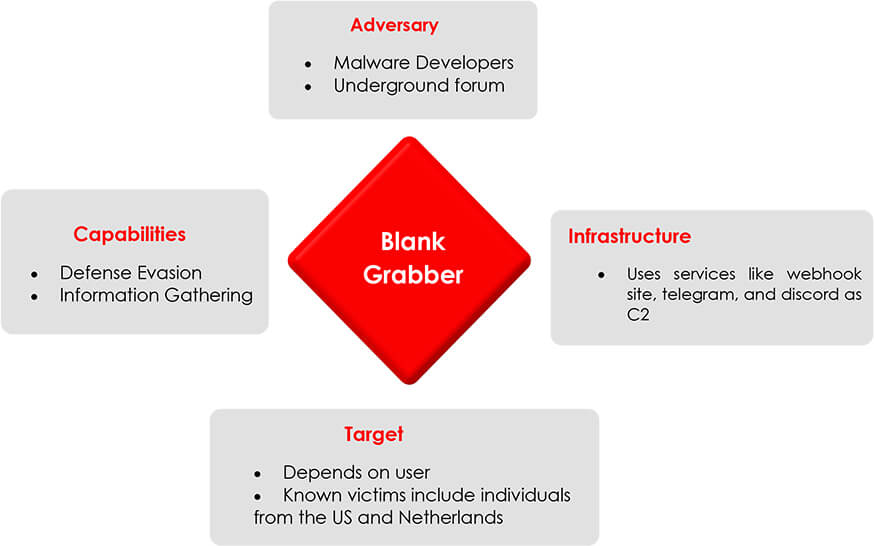
Impact Assessment: The impact of the Blank Grabber infostealer can be severe for organizations. It has the potential to compromise sensitive information, including user credentials, intellectual property, and financial data. The theft of such information can lead to financial losses, reputational damage, regulatory non-compliance, and legal consequences. Additionally, the deployment of the stealer can disrupt business operations, compromise network security, and undermine customer trust. Timely detection, effective incident response, and preventive measures are crucial to minimizing the impact of such threats.
CONCLUSION
The Blank Grabber infostealer represents a significant and evolving threat in today’s external threat landscape. Its advanced capabilities (including data exfiltration, system compromise, and evasion techniques) pose a grave risk to organizations and individuals alike, and the implications of falling victim are severe, from financial losses and reputational damage, to legal consequences and compromised business operations. Mitigating this threat requires a multi-faceted approach, including robust endpoint protection, employee awareness training, secure configurations, and incident response planning. Continual vigilance, proactive security measures, and staying informed about emerging threats are essential in safeguarding against infostealers like the Blank Grabber.
IOCs
| No. | Indicator | Type | Comments |
| 1 | 7b026e20696754040ff390afa8356b6b | md5 | Compiled Malware |
| 2 | 4949588f7ee9ce7bc4a8408982865e1a5192284c | sha1 | Compiled Malware |
| 3 | 094e9745af4bf22f6ce77e3f23b722edd03e447f3810ee66de64cf5ce32f1a9e | sha256 | Compiled Malware |
| 4 | 5ade6e0edac7caf4c1913d717009f954 | md5 | Compiled Malware |
| 5 | 6b871b4522ab28435635aeb316b47254c4e20ea7 | sha1 | Compiled Malware |
| 6 | 1196c0ab10592a87191900cafe69b19e6c44f16252236d9290d5b63747876b4d | sha256 | Compiled Malware |
| 7 | 8efb75694b0150fd63d1e097b0340048 | md5 | Builder |
| 8 | 40c06827cb7aab0287ac60b2d884521ebdc87cf2 | sha1 | Builder |
| 9 | ca63867458c6dbd78c68612106068ee6dd786852fc6c7bb488840045d983c134 | sha256 | Builder |
| 10 | e1c8233b71f5b4befa0605a036c2439f | md5 | RAT used with Blank Grabber |
| 11 | 3c1ed3b56c662706f8817e62cd2f9c4466596d9a | sha1 | RAT used with Blank Grabber |
| 12 | 7a0fa7427224a98c57c65175eff4d069d4776e8aa3e2ba84f1ac53c169548ae8 | sha256 | RAT used with Blank Grabber |
SIGMA RULE(S)
1. Detects any attempts by malware to perform reconnaissance about security products using Wmic.EXE
title: Product Reconnaissance via Wmic.EXE status: experimental
description: Detects the execution of WMIC in order to get a list of firewall and antivirus software
author: CYFIRMA_RESEARCH date: 2023/07/06
tags:
– attack.execution
– attack.t1047 logsource:
category: process_creation
product: windows detection:
selection_img:
– Image|endswith: ‘wmic.exe’ – OriginalFileName: ‘wmic.exe’
selection_cli: CommandLine|contains: ‘Product’
condition: all of selection_* falsepositives:
– Unknown level: medium
2. Detects any attempts by malware to disable Windows Defender Functionalities via Registry Keys
title: Disable Windows Defender Functionalities Via Registry Keys status: experimental
description: Detects when attackers or tools disable Windows Defender functionalities via the windows registry
date: 2022/08/01 modified: 2023/05/10 tags:
– attack.defense_evasion
– attack.t1562.001 logsource:
product: windows
category: registry_set detection:
selection_main: EventType: SetValue TargetObject|contains:
– ‘SOFTWAREMicrosoftWindows Defender’
– ‘SOFTWAREPoliciesMicrosoftWindows Defender Security Center’ – ‘SOFTWAREPoliciesMicrosoftWindows Defender’
selection_dword_1: TargetObject|endswith:
– ‘DisableAntiSpyware’
– ‘DisableAntiVirus’
– ‘Real-Time ProtectionDisableBehaviorMonitoring’
– ‘Real-Time ProtectionDisableIntrusionPreventionSystem’ – ‘Real-Time ProtectionDisableIOAVProtection’
– ‘Real-Time ProtectionDisableOnAccessProtection’
– ‘Real-Time ProtectionDisableRealtimeMonitoring’
– ‘Real-Time ProtectionDisableScanOnRealtimeEnable’ – ‘Real-Time ProtectionDisableScriptScanning’
– ‘ReportingDisableEnhancedNotifications’
– ‘SpyNetDisableBlockAtFirstSeen’
Details: ‘DWORD (0x00000001)’ selection_dword_0:
TargetObject|endswith:
– ‘App and Browser protectionDisallowExploitProtectionOverride’
– ‘FeaturesTamperProtection’
– ‘MpEngineMpEnablePus’
– ‘PUAProtection’
– ‘Signature UpdateForceUpdateFromMU’
– ‘SpyNetSpynetReporting’
– ‘SpyNetSubmitSamplesConsent’
– ‘Windows Defender Exploit GuardControlled Folder AccessEnableControlledFolderAccess’
Details: ‘DWORD (0x00000000)’
condition: selection_main and 1 of selection_dword_*
falsepositives:
– Administrator actions via the Windows Defender interface
level: high
MITRE MAPPING
| Sr. No | Tactics | Techniques | Procedures |
| 1 | TA0002- Execution | T1047: Windows Management Instrumentation |
|
| T1059: Command and Scripting Interpreter |
|
||
| T1129: Shared Modules |
|
||
| 2 | TA0003- Persistence | T1574.002: DLL Side-Loading | Tries to load missing DLLs |
| 3 | TA0004- Privilege Escalation | T1574.002: DLL Side-Loading | Tries to load missing DLLs |
| 4 | TA0005- Defense Evasion | T1027: Obfuscated Files or Information |
|
| T1027.002: Software Packing |
|
||
| T1070.006: Timestomp | Binary contains a suspicious time stamp | ||
| T1112: Modify Registry | Uses reg.exe to modify the Windows registry | ||
| T1497: Virtualization/Sandbox Evasion |
|
||
| T1562.001: Disable or Modify Tools |
|
||
| T1574.002: DLL Side-Loading | Tries to load missing DLLs | ||
| 5 | TA0006- Credential Access | T1003: OS Credential Dumping | Tries to harvest and steal browser information (history, passwords, etc) |
| T1056: Input Capture | Creates a DirectInput object (often for capturing keystrokes) | ||
| 6 | TA0007- Discovery | T1010: Application Window Discovery | Sample monitors Window changes (e.g. starting applications) |
| T1016: System Network Configuration Discovery | Checks the online ip address of the machine | ||
| T1018: Remote System Discovery | Reads the hosts file | ||
| T1057: Process Discovery |
|
||
| T1082: System Information Discovery |
|
||
| T1083: File and Directory Discovery |
|
||
| T1497: Virtualization/Sandbox Evasion |
|
||
| T1518.001: Security Software Discovery |
|
||
| 7 | TA0009- Collection | T1005: Data from Local System |
|
| T1056: Input Capture |
|
||
| T1115: Clipboard Data |
|
||
| 8 | TA0011- Command and Control | T1071: Application Layer Protocol |
|
| T1095: Non-Application Layer Protocol |
|
||
| T1105: Ingress Tool Transfer |
|
||
| T1573: Encrypted Channel |
|
HOW TO RECOVER?
- Change All of your passwords that you had stored on your PC.
- Go to the common startup directory by pressing Win + R to open the run dialog box and then typing shell:common startup in it. Now delete All files you see there with the .scr extension (you may want to enable show file extension for this).
- Open the Local folder by typing %localappdata% in the run dialog box. Delete any folder whose name contains the word “discord” and then reinstall discord.
- Check if your AV sites have been blocked or not, by going here. If you cannot access this site, then this means your access is blocked. If so, then follow this (you would need to install Python for this).
RECOMMENDATIONS
Tactical:
- Endpoint Protection: Deploy and regularly update robust endpoint protection solutions with real-time threat detection capabilities. This includes antivirus, anti- malware, and host intrusion prevention systems (HIPS). Ensure that these tools are configured to scan for known indicators of compromise (IOCs) associated with the Blank Grabber.
- Network Monitoring: Implement network monitoring solutions that can detect unusual or suspicious network traffic patterns. This helps in identifying potential data exfiltration attempts by the Blank Grabber. Intrusion detection and prevention systems (IDPS) can also be employed to detect and block malicious activities.
- Web Filtering: Employ web filtering solutions that block access to known malicious websites and domains associated with the Blank Grabber and similar threats. Regularly update the web filtering rules to stay protected against emerging threats.
Strategic:
- Threat Intelligence: Establish relationships with trusted threat intelligence providers to receive timely updates on emerging threats, including information related to the Blank Grabber. Leverage this intelligence to enhance security controls and proactively identify potential risks.
- Vulnerability Management: Implement a comprehensive vulnerability management program to regularly scan and patch systems, applications, and software. Keep abreast of vendor security advisories to address known vulnerabilities that could be exploited by Blank Grabber.
- Security Training and Awareness: Conduct regular security awareness programs to educate employees about the risks associated with social engineering, phishing attacks, and the use of malicious software. Foster a culture of security consciousness and ensure employees understand their role in safeguarding sensitive information.
Management:
- Incident Response Planning: Develop and regularly update an incident response plan specific to dealing with data breaches and malware incidents. Define roles and responsibilities, establish communication channels, and conduct regular tabletop exercises to test the effectiveness of the plan.
- Security Governance: Establish a robust security governance framework that includes policies, standards, and procedures to govern the organization’s security posture. This framework should cover areas such as access control, data classification, encryption, and third-party risk management.
- Regular Auditing and Testing: Conduct regular security audits, vulnerability assessments, and penetration testing to identify potential vulnerabilities and weaknesses in the organization’s defenses. This enables proactive remediation of security gaps and ensures ongoing security resilience.
Source: https://www.cyfirma.com/outofband/blank-grabber-returns-with-high-evasiveness/