Summary: The Sandworm hacking group, associated with Russian military intelligence, has been hiding their attacks and operations behind multiple online personas posing as hacktivist groups. They have been active since at least 2009 and are known for their multi-faceted attacks on critical infrastructure in Ukraine.
Threat Actor: Sandworm | Sandworm
Victim: Various entities, including water utilities in the U.S. and Poland, a hydroelectric facility in France, and Ukrainian military and security personnel.
Key Points:
- The Sandworm hacking group has been using multiple online personas to hide their attacks and operations.
- They are highly adaptive and use various methods for initial access, including phishing, credential harvesting, exploiting vulnerabilities, and supply-chain compromise.
- Sandworm has been active since at least 2009 and is associated with Russian military intelligence.
- They have targeted critical infrastructure in Ukraine, including state networks, telecommunications providers, news media, and the power grid.
- The group has recently shifted focus to espionage and influence-focused operations to change perceptions about their power and capabilities.
- Mandiant warns that APT44 (Sandworm) is likely to interfere with upcoming national elections and other significant political events in various countries.

The Sandworm hacking group associated with Russian military intelligence has been hiding attacks and operations behind multiple online personas posing as hacktivist groups.
According to Mandiant, the threat actor is linked to at least three Telegram channels that were used to amplify the group’s activity by creating narratives in favor of Russia.
Sandworm – a.k.a. BlackEnergy, Seashell Blizzard, Voodoo Bear, has been active since at least 2009, with multiple governments attributing its operations to Unit 74455, the Main Centre for Special Technologies (GTsST) within the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GU), better known as the Main Intelligence Directorate (GRU).
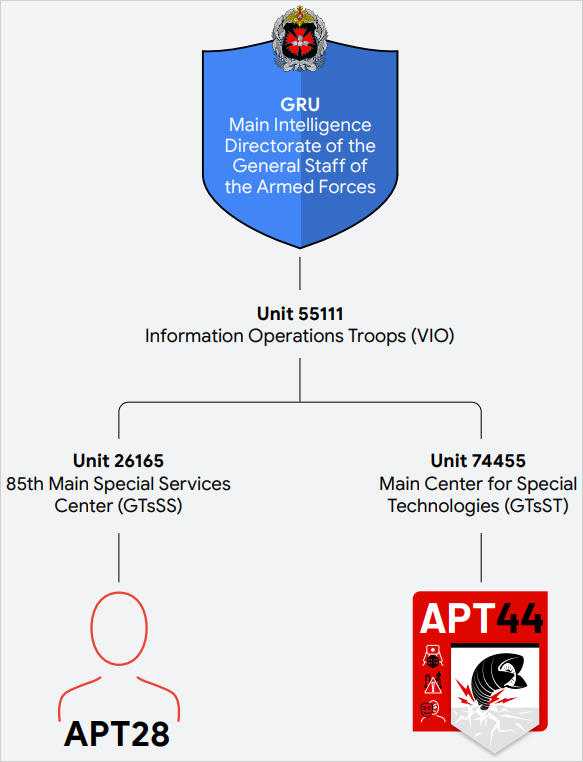
The adversary is highly adaptive and relies on both common initial access methods like phishing and credential harvesting as well as exploiting known vulnerabilities and supply-chain compromise.
Mandiant has started tracking the group as APT44 and notes that it “has established itself as Russia’s preeminent cyber sabotage unit.”
Since Russia invaded Ukraine a little over two years ago, Sandworm began using online personas for data leaks and disruptive operations.
In a report today, Mandiant says that Sandworm relied on three main hacktivist-branded Telegram channels named XakNet Team, CyberArmyofRussia_Reborn, and Solntsepek, all operating in parallel and independently of one another.
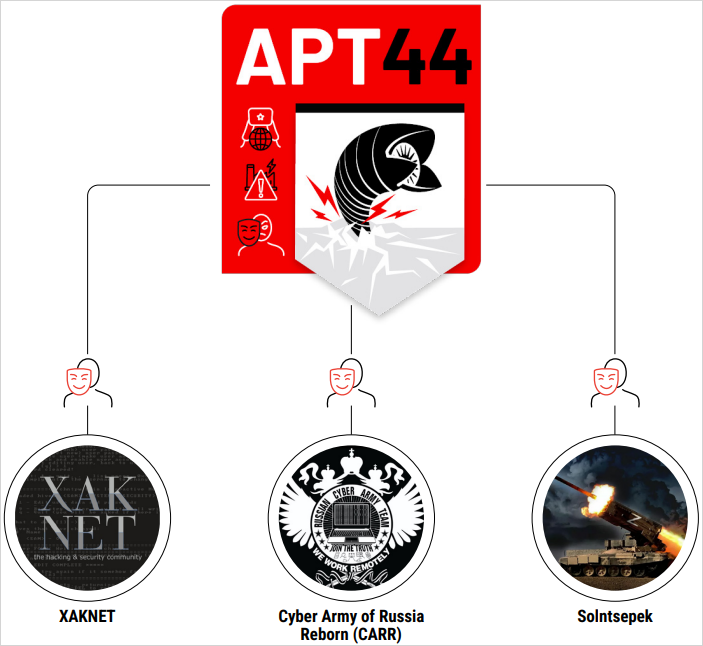
It is unclear how much control the threat actor had over these identities but Google’s Threat Analysis Group found in the case of CyberArmyofRussia_Reborn the closest operational relationship.
Google TAG found that the seemingly hacktivist group’s YouTube channel had been created from infrastructure attributed to Sandworm/APT44.
Additionally, “Mandiant has observed known APT44 infrastructure used to exfiltrate data from victims later leaked in the CyberArmyofRussia_Reborn Telegram channel, as well as egress to Telegram in close temporal proximity to the persona’s posted claims.”
At one point, an error on APT44’s part resulted in CyberArmyofRussia_Reborn claiming on their channel an attack that APT44 had not yet carried out.
Although most of the attack-and-leak activity that Mandiant attributed to the GRU and involved Telegram personas centered on Ukrainian entities, CyberArmyofRussia_Reborn claimed attacks on water utilities in the U.S. and Poland and a hydroelectric facility in France.
In both cases, the “hacktivists” published videos and screenshots showing control of operational technology assets.
Mandiant notes that while it can’t verify these intrusions, officials at the impacted utilities in the U.S. confirmed incidents and malfunctions at organizations that CyberArmyofRussia_Reborn claimed to have breached.
The Solntsepek channel had leaked personally identifiable information from Ukrainian military and security personnel before a rebrand to “hacker group” in 2023 when it started to take credit for APT44’s disruptive cyberattacks.
“Beyond a crude attempt to maximize its operational impact, we assess that these follow-on information operations are likely intended by APT44 to serve multiple wartime objectives,” explains Mandiant in the report.
“These aims include priming the information space with narratives favorable to Russia, generating perceptions of popular support for the war for domestic and foreign audiences, and making the GRU’s cyber capabilities appear more potent through exaggerated claims of impact” – Mandiant
The war in Ukraine made Sandworm notorious for launching multi-faceted attacks aimed at causing damage to the country’s critical infrastructure and services, including state networks, telecommunications providers, news media, and the power grid.
During that period, the Russian hackers employed a range of wiper malware to erase data beyond recovery.
It appears that Sandworm has moved focus, if only temporarily, from sabotage attacks in Ukraine to espionage and influence-focused operations to change domestic and foreign perceptions about Russian hacktivist’s power and GRU’s cyber capabilities.
APT44’s activity this year
Mandiant’s report elaborates on APT44’s use of a rich malware set, phishing campaigns, and vulnerability exploitation for initial access and sustained operations within targeted networks, offering several specific case studies:
- APT44 continues to target electoral systems in NATO countries, using cyber-operations that involve leaking sensitive information and deploying malware to influence election outcomes.
- The group has increased its focus on intelligence collection to support Russian military advantages, including extracting data from mobile devices captured on battlefields.
- APT44 conducts widespread credential theft targeting global mail servers, aiming to maintain access to high-value networks for further malicious activities.
- The group targets journalists and organizations like Bellingcat that investigate Russian government activities using phishing messages.
- Since the start of the year, APT44 has carried out cyber operations to express political displeasure or retaliate against grievances, deploying disruptive malware against critical infrastructure in NATO countries.
- APT44’s activities remain concentrated on Ukraine, with ongoing operations to disrupt and collect intelligence, supporting Russian military and political goals in the region.
Mandiant warns that based on APT44’s patterns of activity, there’s a very high chance that the group will attempt to interfere with upcoming national elections and other significant political events in various countries, including the U.S.
However, researchers believe that Ukraine will continue to be the threat actor’s primary focus for as long as the war continues. At the same time, Sandworm is versatile enough for running operations for global-level strategic objectives.
“An interesting youtube video that may be related to the article above”