Summary: A new variant of the Mallox ransomware is targeting Linux systems, encrypting victim’s data and demanding a ransom for its release.
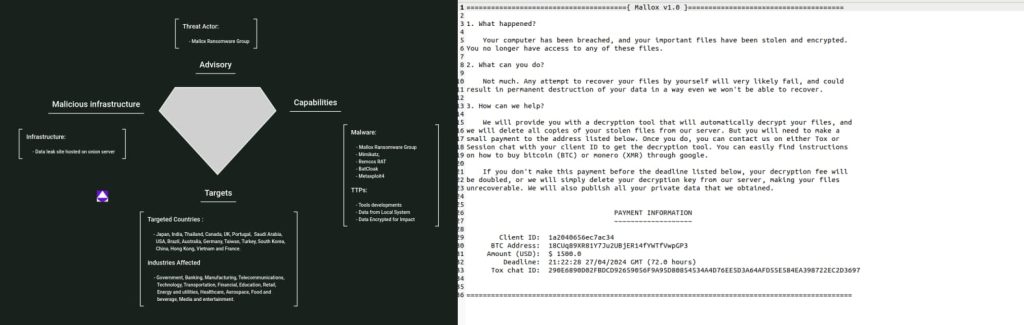
Threat Actor: Mallox ransomware | Mallox ransomware
Victim: Linux systems | Linux systems
Key Point :
- The new variant of Mallox ransomware targets Linux systems and uses custom encryption and a builder web panel.
- The attackers employ a custom Python script to deliver the ransomware payload and use a web panel to build custom variants of the malware.
- Cybersecurity researchers at Uptycs have discovered a decryptor for this variant, offering hope to victims.
- Maintaining backups and strong security practices are essential for defense against ransomware attacks.
New variant of Mallox ransomware targets Linux systems using custom encryption and a builder web panel. Cybersecurity researchers at Uptycs found decryptor which offers hope to victims, but maintaining backups and strong security practices are essential for defence.
Uptycs threat research team have discovered a new Mallox Ransomware variant targeting Linux systems. This malicious software encrypts the victim’s data, rendering it inaccessible until a ransom is paid.
The attackers employ a custom Python script (web_server.py) to deliver the ransomware payload to the targeted system. The script is a Flask framework-based Mallox ransomware web panel that connects to a backend database using environment variables of the system for credentials, providing researchers with insight into the hacker’s infrastructure.
What makes Mallox ransomware (aka Fargo, TargetCompany, and Mawahelper) particularly concerning is the web panel that empowers cybercriminals to build custom variants of Mallox, manage their deployment, and even download the ransomware.
The new Mallox variant encrypts user data and appends a .locked extension to encrypted files, whereas previous versions used.NET-based,.EXE, or.DLL files and were distributed via MS-SQL servers and phishing or spam emails. The malware includes routes for various functions, including user authentication, build management, new user registration, login and password reset, and ransomware build creation.
Additionally, it also allows admins to manage users, view logs, and perform account actions and features user profile management, a chat interface, and a custom 404 error page.
According to Uptycs’ report, the encryption process used by Mallox leverages the AES-256 CBC algorithm, a robust encryption standard. This encryption method makes it incredibly difficult, if not impossible, for victims to decrypt their files without the decryption key held by the attackers.
For your information, Mallox ransomware operations have been active since mid-2021. From mid-2022 it transitioned into the Ransomware-as-a-Service (Raas) distribution model. Mallox group uses multi-extortion tactics, encrypting victims’ data and threatening to post it on public TOR-based sites.
Fortunately, Uptycs researchers have discovered a decryptor for Mallox ransomware. This provides a glimmer of hope for victims who have been infected with this malware. However, the creators of Mallox could potentially update their ransomware to evade decryption so this remedy may be short-lived.
To protect yourself from Mallox ransomware, maintain regular backups of your data, be cautious of suspicious attachments and links, keep your software up-to-date with security patches, and use reliable security solutions. These steps help restore your files in case of a ransomware attack without paying the ransom.
RELATED TOPICS
- New Cylance Ransomware Targets Linux and Windows
- Volcano Demon Ransomware Makes Phone Calls for Ransom
- New AcidRain Linux Malware Variant “AcidPour” Targeting Ukraine
- No More Ransom Offers Free LockerGoga Ransomware Decryptor
- Universal decryptor key for Sodinokibi, REvil ransomware released
Source: https://hackread.com/mallox-ransomware-variant-targets-linux-systems
“An interesting youtube video that may be related to the article above”