Summary: This content discusses a new command execution technique called ‘GrimResource’ that utilizes specially crafted MSC files and an unpatched Windows XSS flaw to execute code through the Microsoft Management Console.
Threat Actor: Unknown threat actor | Unknown threat actor
Victim: Windows users | Windows users
Key Point :
- A new command execution technique called ‘GrimResource’ is utilizing specially crafted MSC files and an unpatched Windows XSS flaw to perform code execution via the Microsoft Management Console.
- Threat actors have been experimenting with different file types in phishing attacks after Microsoft disabled macros by default in Office, including ISO images, password-protected ZIP files, Windows Shortcuts, OneNote files, and now Windows MSC files.

A novel command execution technique dubbed ‘GrimResource’ uses specially crafted MSC (Microsoft Saved Console) and an unpatched Windows XSS flaw to perform code execution via the Microsoft Management Console.
In July 2022, Microsoft disabled macros by default in Office, causing threat actors to experiment with new file types in phishing attacks. The attackers first switched to ISO images and password-protected ZIP files, as the file types did not properly propagate Mark of the Web (MoTW) flags to extracted files.
After Microsoft fixed this issue in ISO files and 7-Zip added the option to propagate MoTW flags, attackers were forced to switch to new attachments, such as Windows Shortcuts and OneNote files.
Attackers have now switched to a new file type, Windows MSC (.msc) files, which are used in the Microsoft Management Console (MMC) to manage various aspects of the operating system or create custom views of commonly accessed tools.
The abuse of MSC files to deploy malware was previously reported by South Korean cybersecurity firm Genian. Motivated by this research, the Elastic team discovered a new technique of distributing MSC files and abusing an old but unpatched Windows XSS flaw in apds.dll to deploy Cobalt Strike.
Elastic found a sample (‘sccm-updater.msc’) recently uploaded onto VirusTotal on June 6, 2024, which leverages GrimResource, so the technique is actively exploited in the wild. To make matters worse, no antivirus engines on VirusTotal flagged it as malicious.
While this campaign is using the technique to deploy Cobalt Strike for initial access to networks, it could also be used to execute other commands.
The researchers confirmed to Bleepingcomputer that the XSS flaw is still unpatched in the latest version of Windows 11.
How GrimResource works
The GrimResource attack begins with a malicious MSC file that attempts to exploit an old DOM-based cross-site scripting (XSS) flaw in the ‘apds.dll’ library, which allows the execution of arbitrary JavaScript through a crafted URL.
The vulnerability was reported to Adobe and Microsoft in October 2018, and while both investigated, Microsoft determined that the case did not meet the criteria for immediate fixing.
As of March 2019, the XSS flaw remained unpatched, and it is unclear if it was ever addressed. BleepingComputer contacted Microsoft to confirm if they patched the flaw, but a comment wasn’t immediately available.
The malicious MSC file distributed by attackers contains a reference to the vulnerable APDS resource in the StringTable section, so when the target opens it, MMC processes it and triggers the JS execution in the context of ‘mmc.exe.’
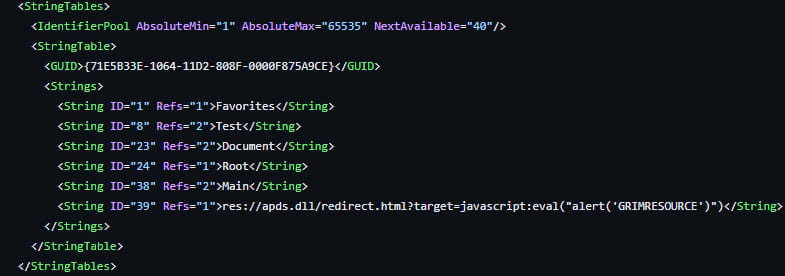
Source: Elastic Security
Elastic explains that the XSS flaw can be combined with the ‘DotNetToJScript‘ technique to execute arbitrary .NET code through the JavaScript engine, bypassing any security measures in place.
The examined sample uses ‘transformNode’ obfuscation to evade ActiveX warnings, while the JS code reconstructs a VBScript that uses DotNetToJScript to load a .NET component named ‘PASTALOADER.’
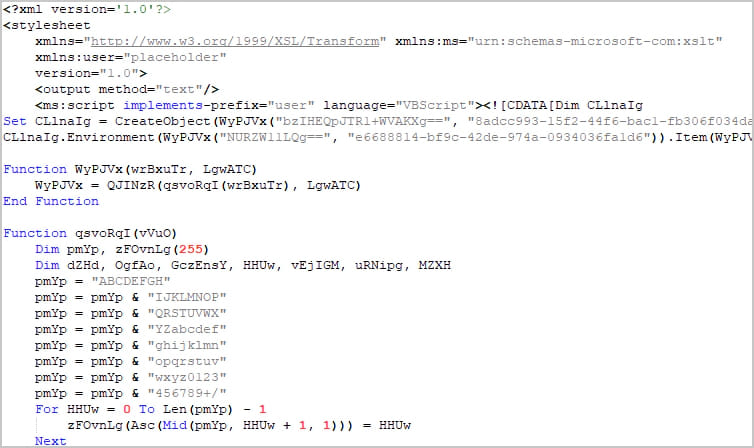
Source: Elastic Security
PASTALOADER retrieves a Cobalt Strike payload from the environment variables set by the VBScript, spawns a new instance of ‘dllhost.exe,’ and injects it using the ‘DirtyCLR‘ technique combined with function unhooking and indirect system calls.
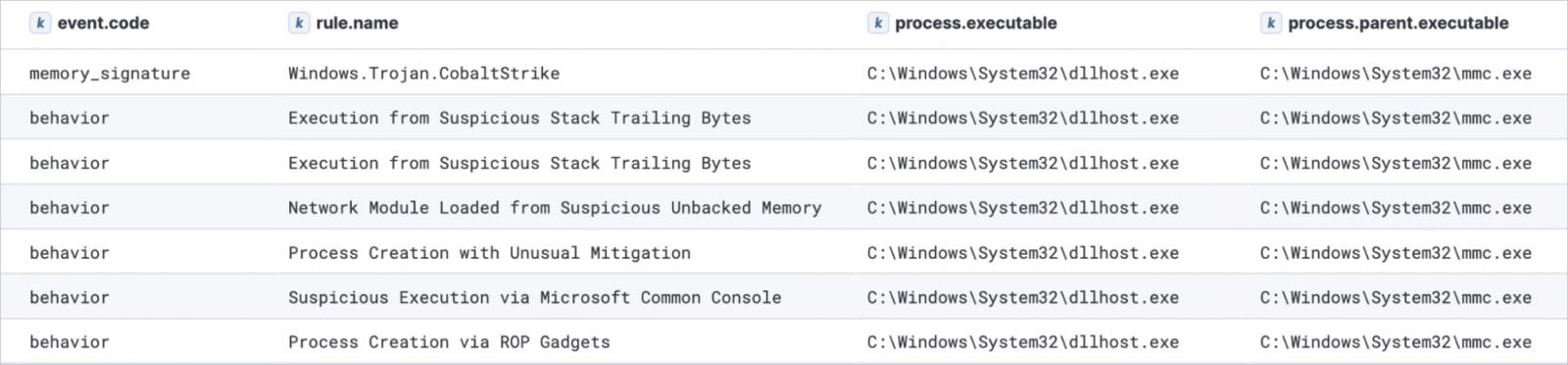
Source: Elastic Security
Elastic researcher Samir Bousseaden shared a demonstration of the the GrimResource attack on X.
Stopping GrimResource
In general, system administrators are advised to be on the lookout for the following:
- File operations involving apds.dll invoked by mmc.exe.
- Suspicious executions via MCC, especially processes spawned by mmc.exe with .msc file arguments.
- RWX memory allocations by mmc.exe that originate from script engines or .NET components.
- Unusual .NET COM object creation within non-standard script interpreters like JScript or VBScript.
- Temporary HTML files created in the INetCache folder as a result of APDS XSS redirection.
Elastic Security has also published a complete list of GrimResource indicators on GitHub and provided YARA rules in the report to help defenders detect suspicious MSC files.
“An interesting youtube video that may be related to the article above”