Summary: Hackers are using Facebook advertisements and hijacked pages to promote fake Artificial Intelligence services, such as MidJourney, OpenAI’s SORA and ChatGPT-5, and DALL-E, to infect unsuspecting users with password-stealing malware.
Threat Actor: Unknown | Unknown
Victim: Facebook users | Facebook
Key Point :
- Hackers are using hijacked Facebook profiles to impersonate popular AI services and promote fake AI services through advertisements.
- Users who fall for the ads become members of fraudulent Facebook communities, where they are tricked into downloading malware that steals their personal information.
- The malware focuses on stealing data from the victim’s browser, including stored credentials, cookies, cryptocurrency wallet information, autocomplete data, and credit card information.
- The stolen data is either sold on dark web markets or used by the attackers to breach the victim’s online accounts and conduct further scams or fraud.
- The campaigns have been successful due to the high interest in AI and the difficulty for users to discern legitimate announcements from fakes.
- One malicious Facebook page impersonating Midjourney amassed 1.2 million followers and remained active for nearly a year before being taken down.
- The ads targeted a demographic of men aged 25 to 55 in Europe, primarily Germany, Poland, Italy, France, Belgium, Spain, the Netherlands, Romania, and Sweden.
- The attackers set up multiple sites that cloned the official Midjourney landing page to trick users into downloading malware.
- The malware masquerades as legitimate tools or extensions, such as a Google Translate extension or a desktop version of the AI service.
- The success of these campaigns highlights the sophistication of social media-based malvertising strategies and the need for vigilance when engaging with online advertisements.

Hackers are using Facebook advertisements and hijacked pages to promote fake Artificial Intelligence services, such as MidJourney, OpenAI’s SORA and ChatGPT-5, and DALL-E, to infect unsuspecting users with password-stealing malware.
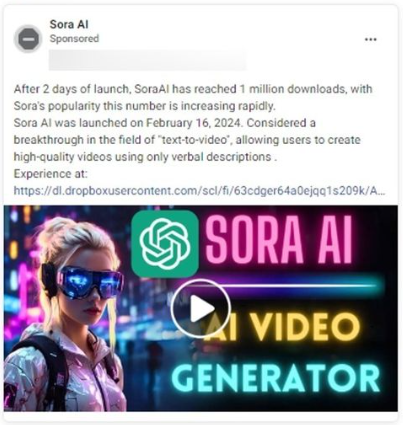
The malvertising campaigns are created by hijacked Facebook profiles that impersonate popular AI services, pretending to offer a sneak preview of new features.
Users tricked by the ads become members of fraudulent Facebook communities, where the threat actors post news, AI-generated images, and other related info to make the pages look legitimate.
Source: Bitdefender
However, the community posts often promote limited-time access to upcoming and eagerly anticipated AI services, tricking the users into downloading malicious executables that infect Windows computers with information-stealing malware, like Rilide, Vidar, IceRAT, and Nova.
Information-stealing malware focuses on stealing data from a victim’s browser, including stored credentials, cookies, cryptocurrency wallet information, autocomplete data, and credit card information.
This data is then sold on dark web markets or used by the attackers to breach the target’s online accounts to promote further scams or conduct fraud.
Midjourney campaign
The reach of those campaigns is staggering in some cases, as people’s interest in AI is currently very high. The developments in the field are so rapid that it’s not easy for people to keep up and discern legitimate announcements from obvious fakes.
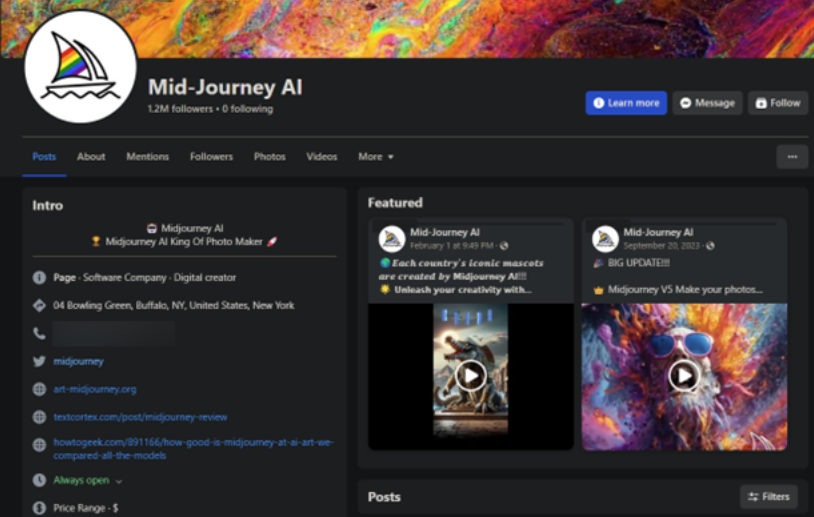
In one of the cases seen by researchers at Bitdefender, a malicious Facebook page impersonating Midjourney amassed 1.2 million followers and remained active for nearly a year before it was eventually taken down.
The page wasn’t created from scratch; instead, the attackers hijacked an existing profile in June 2023 and converted it to a fake Midjourney page. Facebook shut down the page on March 8, 2024.
Source: Bitdefender
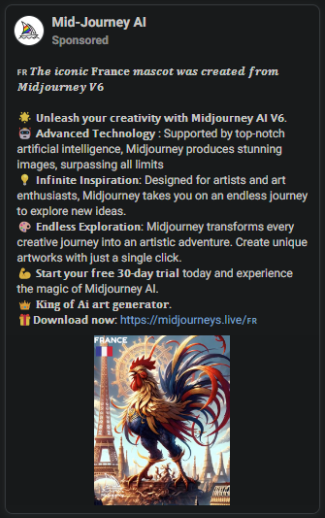
Many posts tricked people into downloading the infostealers by promoting a non-existent desktop version of the tool. Some posts highlighted the release of V6, which isn’t officially out yet (the latest version is V5).
Source: Bitdefender
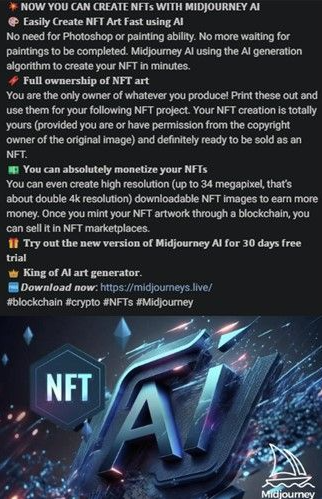
In other cases, the malicious ads promoted opportunities to create NFT art and monetize their creations.
Source: Bitdefender
As you can view the targeting parameters of Facebook ads in the Meta Ad Library, the researchers found that the ads targeted a demographic of men aged 25 to 55 in Europe, primarily Germany, Poland, Italy, France, Belgium, Spain, the Netherlands, Romania, and Sweden.
Instead of using Dropbox and Google Drive links to host the payloads, the operators of this campaign set up multiple sites that cloned the official Midjourney landing page, tricking users into downloading what they thought was the latest version of the art-generating tool via a GoFile link.
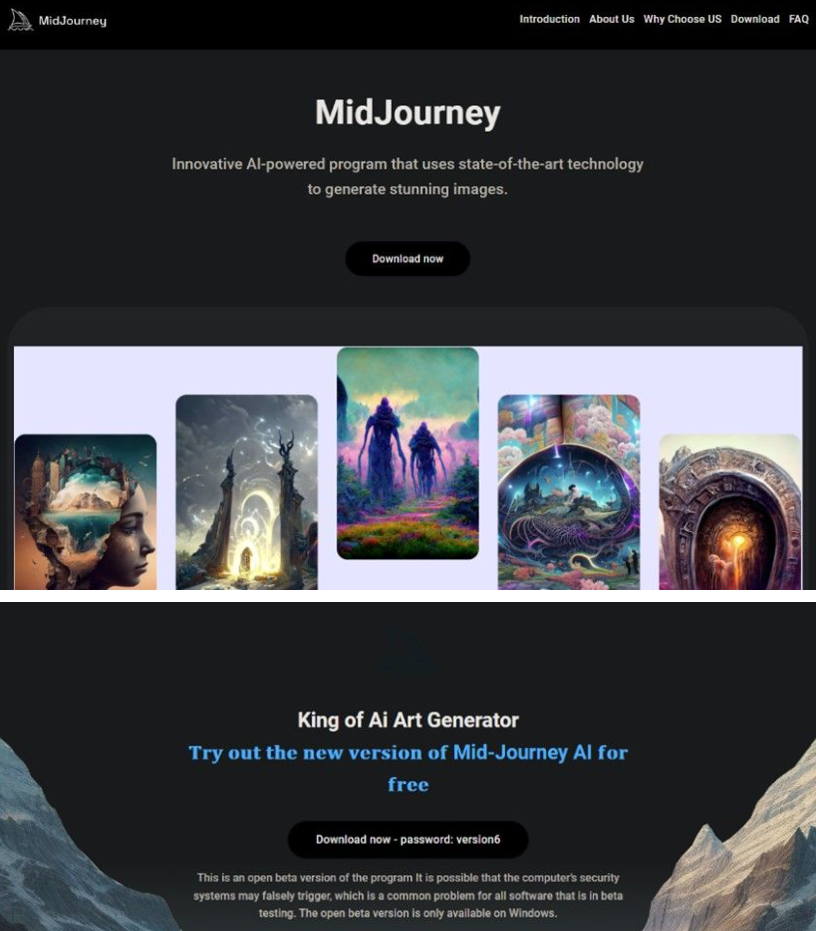
Source: Bitdefender
Instead, they got Rilide v4, which masquerades as a Google Translate extension for their web browser, effectively hiding the malware as it siphoned Facebook cookies and other data in the background.
While this page has since been taken down, the threat actors launched a new page that is still active with over 600,000 members that is pushing a fake Midjourney site distributing malware.
Although the imposter page boasting over 1.2 million followers was recently shut down, our research has shown that cybercriminals acted quickly to set up a new page impersonating Midjourney between March 8-9, 2024. The page was also set up after taking over another user’s Facebook account, who also commented in the review section of the page warning other users that the account was hacked. Since we began our investigation, we noticed an additional four Facebook pages attempting to impersonate Midjourney, some of which were also removed from the platform.
The latest malicious page impersonating Midjourney appears to have been taken over by the attackers on March 18 when the cybercriminals changed the original name of the original Facebook page. As of March 26, the scam profile has 637,000 followers (as seen below).
❖ Bitdefender.
This campaign’s success highlights the sophistication of social media-based malvertising strategies and the importance of vigilance when engaging with online advertisements.
The vast scale of social media networks such as Facebook, coupled with insufficient moderation, allow these campaigns to persist for prolonged periods, facilitating the unchecked spread of malware that leads to extensive damages from malware infections.
“An interesting youtube video that may be related to the article above”
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português