Summary: The decentralized finance (DeFi) crypto exchange dYdX announced that its older v3 trading platform’s website was compromised, leading to a warning for users against visiting the site or withdrawing assets. The incident is linked to a series of DNS hijacking attacks targeting DeFi platforms using the Squarespace registrar.
Threat Actor: Unknown | unknown
Victim: dYdX | dYdX
Key Point :
- dYdX v3 website was compromised, leading to a warning for users to avoid interaction.
- The attack involved hijacking the domain and deploying a phishing site to steal tokens from users.
- The incident is part of a broader trend of DNS hijacking attacks affecting DeFi platforms registered with Squarespace.
- dYdX has regained control of the compromised domain and advised users to clear their browser cache before accessing the site.

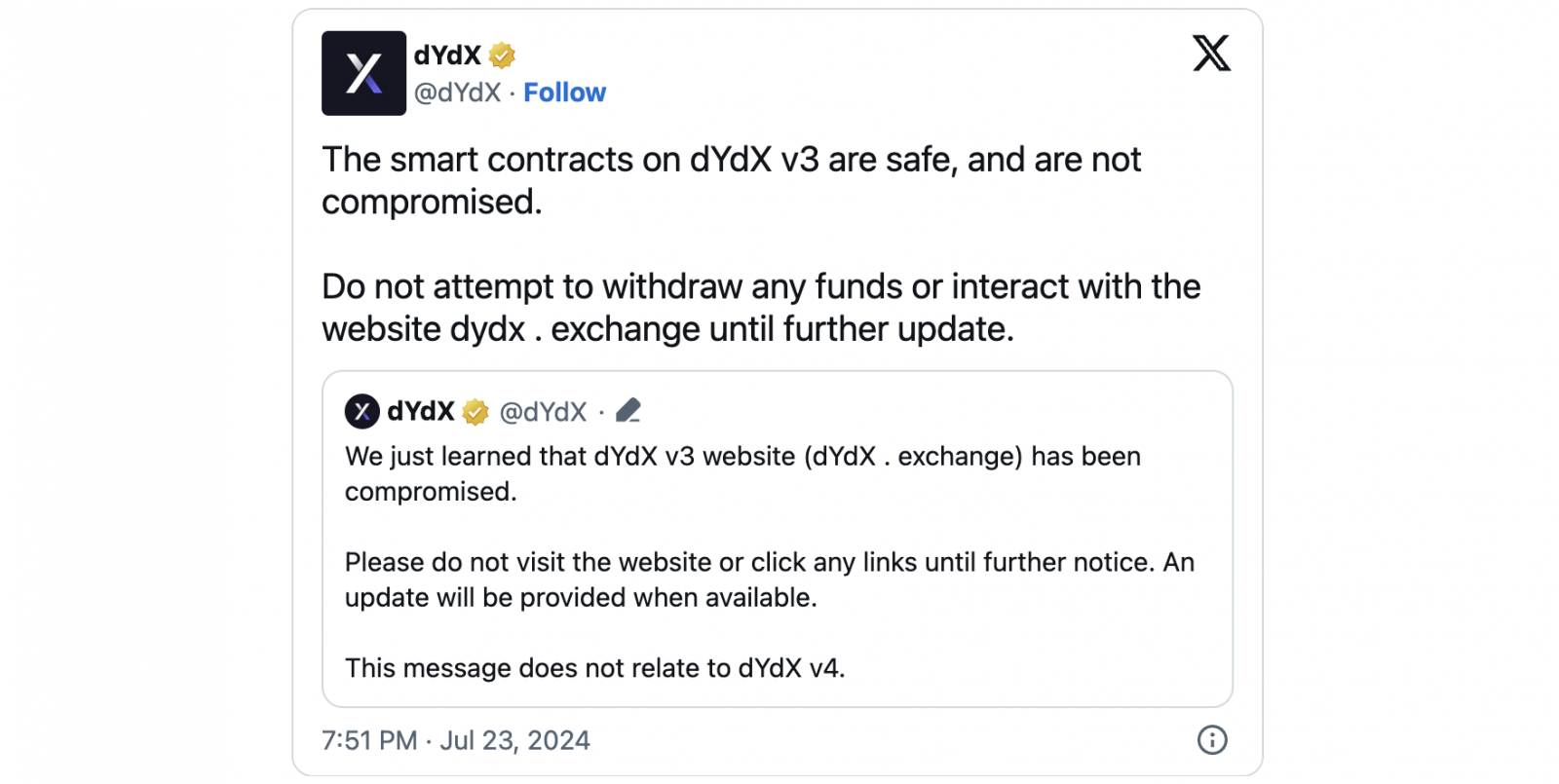
Decentralized finance (DeFi) crypto exchange dYdX announced on Tuesday that the website for its older v3 trading platform has been compromised.
dYdX also warned users not to visit or interact with the hacked dydx[.] exchange platform and cautioned against withdrawing assets until the platform was safe to use.
“We just learned that dYdX v3 website (dYdX . exchange) has been compromised. Please do not visit the website or click any links until further notice,” a new incident report on the official status page reads.
“An update will be provided when available. The smart contracts on v3 are not compromised and any funds currently in dydx v3 are safe.”
In a post on dYdX’s official Discord server earlier today, a community team member also shared that the attackers hijacked the crypto platform’s domain and deployed a copycat website that “when users connect their wallets to it, it asks them to approve via PERMIT2 transaction to steal their most valuable token.”
They also shared that the incident is believed to be linked to a wave of DNS hijacking attacks targeting DeFi crypto platforms using the Squarespace registrar, which is partially confirmed by the v3 website incident report, which links the incident to a DNS issue.
“A fix to the DNS resolution has been implemented. However, due to caching, the issue may not be fixed for every user yet,” the status page says.
As BleepingComputer reported, crypto platforms compromised in these Squarespace DNS hijacking attacks are being used to redirect visitors to phishing sites hosting wallet drainers.
The domains (originally registered at Google Domains) were left vulnerable after being force-transferred to Squarespace last year following an asset purchase agreement with Google.
However, during their transition to Squarespace, multi-factor authentication (MFA) was turned off for management accounts (domain owners are warned in a Squarespace support topic to enable MFA after the Google Domains migration).
While it’s unclear how the attackers are hijacking the domains, a report from security researchers Samczsun, Taylor Monahan, and Andrew Mohawk says the threat actors can gain full access using a valid address linked to the domains because Squarespace “does not require email validation to create an account using password authentication (i.e. you can create an account for bill@gates.com without owning the email address).”
dYdX said on July 11 that “no vulnerabilities or security issues have been detected at this time for http://dydx.exchange or http://dydx.trade,” as first spotted by Resonance Security analyst Grace Dees.
Today’s announcement that the dYdX v3 website was hacked came right after Bloomberg reported that DYdX Trading, the company behind the dYdX derivatives trading software, is in talks with multiple buyers (including Wintermute Trading and Selini Capital) to sell its older v3 software.
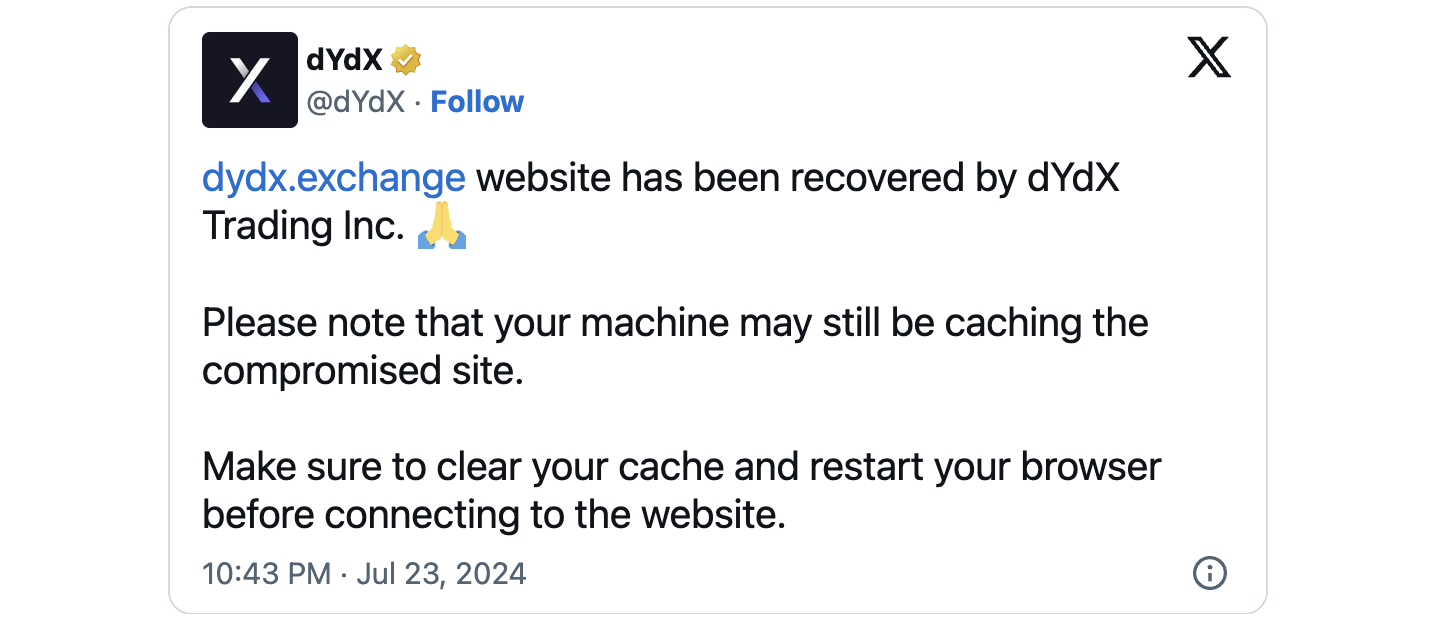
Update: dYdX has regained control of dydx.exchange and advises users to restart their browser and clear the cache before opening the website.

Views: 0