Emerging Ransomware Strain Quickly Expanding its List of Victims
Ransomware is a grave cybersecurity threat and is currently one of the most effective cybercrimes causing organizational problems. It has proven to be highly profitable for cybercriminals, resulting in severe consequences such as financial loss, data loss, and damage to the reputation of the targeted entities.
Over time, Cyble Research and Intelligence Labs (CRIL) has continuously examined and shared information regarding the most dominant and active ransomware groups while offering recommendations to prevent such incidents from occurring again.
Recently, CRIL came across a Reddit post about a new ransomware variant named “Akira”, actively targeting numerous organizations and exposing their sensitive data. To increase the chances of payment from victims, Akira ransomware exfiltrates and encrypts their data using a double-extortion technique. The attackers then threaten to sell or leak the stolen data on the dark web if the ransom is not paid for decrypting the data.
Akira ransomware emerged in April 2023 and has already impacted over 15 publicly disclosed victims, with the majority located in the United States. These victims represent a variety of industries, such as BFSI, Construction, Education, Healthcare, Manufacturing, and others.
Multiple options on the Akira ransomware leak site’s homepage allow users to access the most recent news, leaked data, and other functions, as shown in the image below.

Technical Analysis
We have taken the below sample hash for this analysis:
(SHA256), 3c92bfc71004340ebc00146ced294bc94f49f6a5e212016ac05e7d10fcb3312c,
which is a console-based 64-bit executable written in Microsoft Visual C/C++ compiler, as shown below.

When the ransomware is executed, it uses the API function GetLogicalDriveStrings() to obtain a list of the logical drives currently available in the system, as shown in the figure below.

Then, the malware drops a ransom note in multiple folders with the file name “akira_readme.txt”. The contents of the ransom note are illustrated in the below figure.

After dropping the ransom note, the ransomware searches for files and directories to encrypt by iterating through them using the API functions FindFirstFileW() and FindNextFileW().
The ransomware excludes the below file extensions and file/folder names from encryption.
| File extension | File names | Folder names |
| .exe .dll .sys .msi .lnk .akira | akira_readme.txt Bootmgr BOOTNXT DumpStack.log.tmp pagefile.sys swapfile.sys ntuser.dat | tmp winnt temp thumb $Recycle.Bin $RECYCLE.BIN System Volume Information Boot Windows Trend Micro ProgramData |
Encryption
The ransomware utilizes the “Microsoft Enhanced RSA and AES Cryptographic Provider” libraries to encrypt the victim’s machine. The malware employs several functions from CryptoAPI, including CryptAcquireContextW(), CryptImportPublicKeyInfo(), CryptGenRandom(), and CryptEncrypt().

As mentioned earlier, Akira ransomware uses the RSA and AES encryption algorithms, and it comes with a fixed hardcoded base64 encoded public key, as shown below.

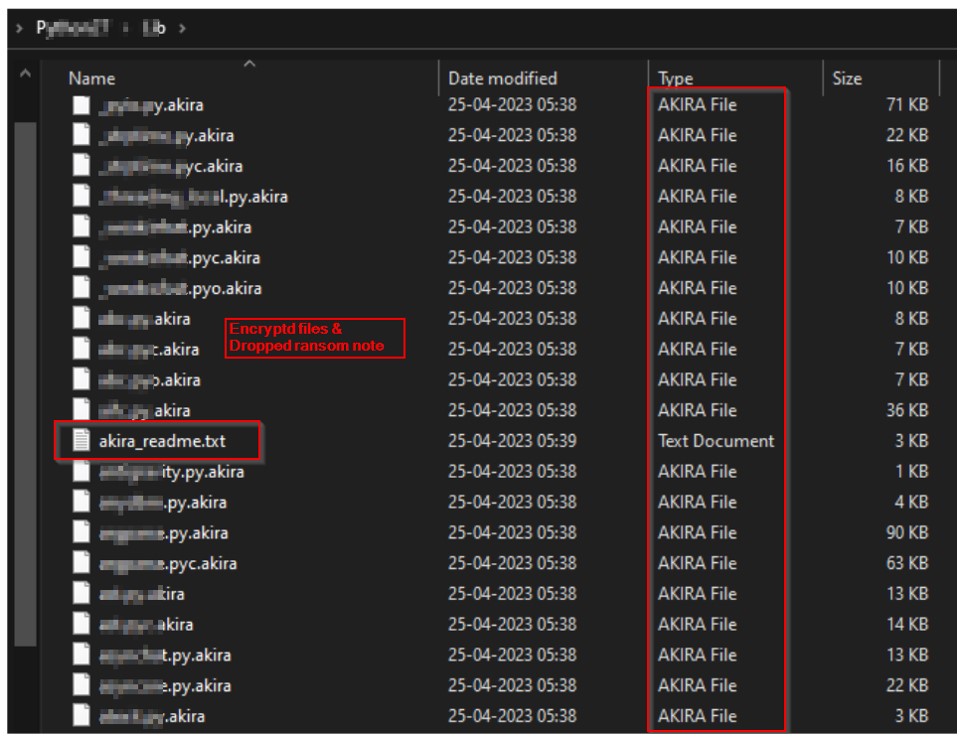
The malware renames the encrypted files with the “.akira” extension in the next step.
The figure below shows the files encrypted by Akira ransomware after the successful infection of a victim’s machine.
Additionally, the ransomware utilizes a PowerShell command, shown in Figure 9, to execute a WMI query that deletes the shadow copy, preventing system restoration.

The dropped ransom note provides instructions to the victims on how they can get in touch with the Akira Ransomware Gang to initiate negotiations for the ransom.
The operators responsible for the Akira ransomware often threaten their victims, claiming to have exfiltrated a large amount of corporate data before encrypting it. They also warn of their intention to sell personal information, trade secrets, databases, and source codes on the dark web market.
Additionally, they threaten to expose the stolen information publicly through their blog (accessible via an Onion site) if the ransom demand is not met.

Figure 11 depicts an Onion site belonging to Akira ransomware, which requires a code (mentioned in the ransom note) to initiate communication or request assistance from the Threat Actor.

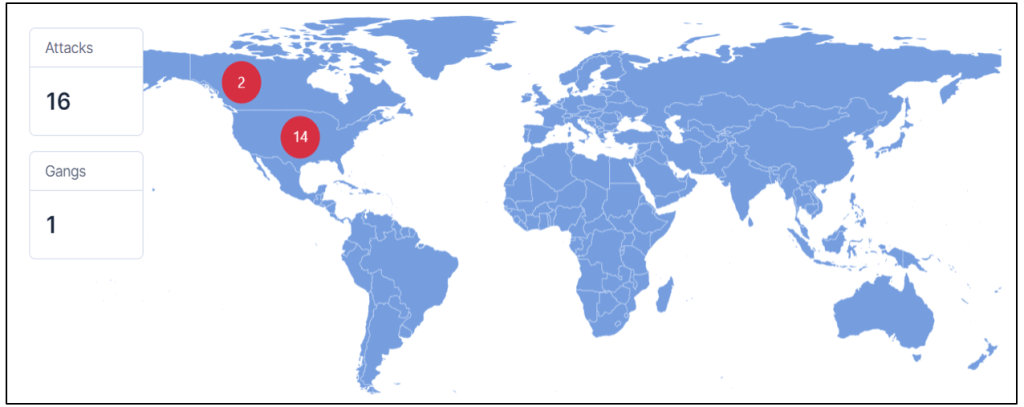
The Akira ransomware homepage features a ‘news’ command that reveals a comprehensive list of 16 victim organizations targeted by the group as of May 5th. The stolen information is summarized for each organization and can be viewed on the same page.
The corresponding figure is provided below.

On the Akira ransomware homepage, a command called ‘leaks’ provides a list of organizations targeted by the group that did not pay the demanded ransom (5 victims as of now).
The leaked data associated with each organization is available for download and includes the organization’s name and a brief description.

Conclusion
Akira ransomware is a newly discovered strain that has mainly affected victims in the United States and Canada. This ransomware group actively targets businesses and demands a significant amount of money in exchange for decryption keys.
As organizations implement security measures to defend against ransomware attacks, there is a corresponding rise in the number of new ransomware groups emerging. These groups continuously adapt their strategies and expand their operations to maximize profits.
Cyble Research & Intelligence Labs (CRIL) continuously monitors new ransomware campaigns to keep our readers updated with our latest findings.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
Safety Measures Needed to Prevent Ransomware Attacks
- Conduct regular backup practices and keep those backups offline or in a separate network.
- Turn on the automatic software update feature on your computer, mobile, and other connected devices wherever possible and pragmatic.
- Use a reputed anti-virus and Internet security software package on your connected devices, including PC, laptop, and mobile.
- Refrain from opening untrusted links and email attachments without verifying their authenticity.
Users Should Take the Following Steps After the Ransomware Attack
- Detach infected devices on the same network.
- Disconnect external storage devices if connected.
- Inspect system logs for suspicious events.
Impact of Akira Ransomware
- Loss of valuable data.
- Loss of the organization’s reputation and integrity.
- Loss of the organization’s sensitive business information.
- Disruption in organization operation.
- Financial loss.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
| Execution | T1204 T1047 T1059 | User Execution Windows Management Instrumentation PowerShell |
| Defense Evasion | T1497 T1027 | Virtualization/Sandbox Evasion Obfuscated Files or Information |
| Discovery | T1057 T1012 T1082 T1083 | Process Discovery Query Registry System Information Discovery File and Directory Discovery |
| Impact | T1486 T1490 | Data Encrypted for Impact Inhibit System Recovery |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| c7ae7f5becb7cf94aa107ddc1caf4b03 923161f345ed3566707f9f878cc311bc6a0c5268 3c92bfc71004340ebc00146ced294bc94f49f6a5e212016ac05e7d10fcb3312c | MD5 SHA1 SHA256 | Akira Ransomware Exe |
Related
Source: https://blog.cyble.com/2023/05/10/unraveling-akira-ransomware/