Threat Actor Modifies TeamViewer Installer to Deliver njRAT
Cyble Research & Intelligence Labs (CRIL) have been monitoring several instances where well-known applications and tools have been exploited as a delivery mechanism for malicious files. Threat Actors (TAs) leverage the trust associated with these applications to deceive users into downloading and executing them.
We encountered a notable incident involving the deceptive utilization of a TeamViewer application file. TeamViewer, a widely adopted software application, facilitates remote control, desktop sharing, online meetings, file transfers, and collaborative work across various devices.
Our preliminary investigation uncovered a significant correlation between the dissemination of the njRAT malware and a favored technique employed by Threat Actors (TAs). This technique entails exploiting the trust and prevalence of popular and legitimate applications such as TeamViewer, WireShark, Process Hacker, and others.
njRAT, commonly called Bladabindi, is a type of Remote Access Trojan (RAT) initially uncovered in 2012. This malware is primarily employed in attacks aimed at organizations located in Middle Eastern nations.
njRAT can perform various malicious activities such as logging keystrokes, taking screenshots, stealing passwords, exfiltrating data, accessing webcams and microphones, downloading additional files, etc.
Initial Infection
In addition to its typical distribution methods, such as phishing campaigns, cracked software on filesharing websites, and drive-by downloads, this njRAT sample is also being distributed through trojanized applications.
Technical Analysis
The malware sample we have identified is a 32-bit Smart Installer, with a SHA 256 hash of “224ae485b6e4c1f925fff5d9de1684415670f133f3f8faa5f23914c78148fc31” (shown in the figure below).

Upon execution, the aforementioned installer drops two files in the Windows folder, and the names of these files include the term “TeamViewer”. One of the files dropped in the Windows folder is njRAT, while the other is a genuine, TeamViewer application, as shown in the figure below.
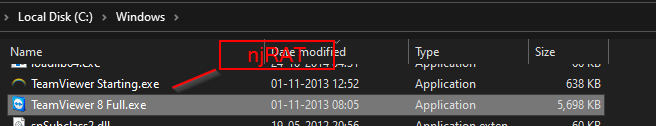
After dropping the files in the Windows folder, the installer triggers the execution of “TeamViewer Starting.exe” (njRAT) and subsequently launches the legitimate “teamviewer.exe” application.
The figure below displays the user prompt window, providing the option to proceed with the team viewer installation.

Simultaneously, the njRAT initiates its installation process by copying itself into the “AppDataLocalTemp” directory with the filename “system.exe“. This technique is designed to make the malicious process less noticeable to the end user by using a filename that resembles a legitimate Windows file. It will then execute the newly dropped file as a new process. The below figure illustrates the sequence of processes involved when executing the Trojanized TeamViewer installer.

Once the new process is launched, njRAT creates a mutex, or mutual exclusion object, as a locking mechanism to prevent two threads from writing to shared memory simultaneously and to avoid reinfection of the victim.
The name of the mutex is “301b5fcf8ce2fab8868e80b6c1f912fe“. The mutex name and other configurations are hardcoded into the njRAT binary.
The below image shows the complete configuration details of the njRAT.

Then, the njRAT modifies the value of the “SEE_MASK_NOZONECHECKS” environment variable in the Windows registry to 1, thereby adjusting the security settings. This alteration allows the malware to operate unhindered, bypassing any security warning prompts or dialog boxes that would typically be presented to the end user.
The image below shows the registry value added by njRAT to adjust the security settings in the victim’s machine.

Afterwards, the RAT creates a firewall regulation that allows for upcoming communication with its Command and Control (C&C) server.
The below figure shows the code used by njRAT to add the firewall rule.

Persistence
Then the malware implements two distinct methods to achieve persistence. The first one involves creating two autorun entries in the system registry:
- HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionRun
Value name: 301b5fcf8ce2fab8868e80b6c1f912fe
Value data: “C:Users[User Profile]AppDataLocalTempSystem.exe”
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun
Value name: 301b5fcf8ce2fab8868e80b6c1f912fe
Value data: “C:Users[User Profile]AppDataLocalTempSystem.exe”
Meanwhile, the second method entails copying itself to the startup directory:
“C:Users[User Profile]AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup301b5fcf8ce2fab8868e80b6c1f912fe.exe”
By doing so, the malware can ensure that it automatically runs every time the system boots up. The below image shows the file located in the startup folder.

Collection
After the initial configurations are successfully completed, the njRAT engages in keylogging activity. To achieve this, the RAT creates a dedicated thread that establishes an ongoing loop to continuously monitor keystrokes. This monitoring functionality is enabled by utilizing the GetAsyncKeyState function, which effectively detects any key presses.
Whenever a key press is detected, the thread captures and stores the corresponding key information in a newly generated file named “System.exe.tmp“. This file is specifically created in the “%appdata%/temp” location. The thread operates continuously with a delay interval of 1 ms between each iteration, allowing for ongoing monitoring of keystrokes and storage of the captured data.
The figure below shows the njRAT’s keylogger function code.

In addition to capturing keystrokes, the RAT also collects various system information such as the Windows operating system version, the service pack, the current date, the username, information about webcams, system architecture, and specific registry keys. The gathered data is encoded using the base64 encoding scheme to facilitate exfiltration.
The image below shows the partial function code for collecting system information for exfiltration.

Once the data is collected, the malicious sample establishes a connection with a Command and Control (C&C) server to transmit the gathered information. The C&C address and listening port are preconfigured within the file, as indicated in Figure 5.
Subsequently, njRAT enters a dormant state, awaiting instructions from the C&C server. The malware compares the received command against a predetermined set of hardcoded commands and proceeds to execute the specified action accordingly.
Before the user gains access to the TeamViewer application, the RAT discreetly conducts malicious operations within the compromised system.
The following image displays the TeamViewer window following the RAT operation.
Conclusion
Despite being in existence for almost a decade, njRAT remains a favored remote administration tool among TAs. Additionally, the method of distributing njRAT demonstrates the resourcefulness and adaptability of TAs in effectively spreading malware through widely-used applications. This kind of malware attack poses a significant threat to the affected systems’ privacy, security, and integrity. Cyble Research and Intelligence Labs (CRIL) actively monitors Trojanized applications to keep our readers informed about them.
Recommendations
- Downloading any tools or applications only from the official website. Avoid downloading it from third-party websites or sources.
- Turn on the automatic software update feature on your computer, mobile, and other connected devices wherever possible and pragmatic.
- Use a reputed anti-virus and Internet security software package on your connected devices, including PC, laptop, and mobile.
- Refrain from opening untrusted links and email attachments without verifying their authenticity.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
| Execution | T1204 T1059 | User Execution Command and Scripting Interpreter |
| Persistence | T1547 | Boot or Logon AutoStart Execution |
| Defense Evasion | T1036 | Masquerading |
| Discovery | T1082 T1057 T1012 | System Information Discovery Process Discovery Query Registry |
| Collection | T1056 | Input Capture |
| Command and Control | T1071 T1095 | Application Layer Protocol Non-Application Layer Protocol |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description | |
| 224ae485b6e4c1f925fff5d9de1684415670f133f3f8faa5f23914c78148fc31 9b9539fec7d0227672717e126a9b46cda3315895 11aacb03c7e370d2b78b99efe9a131eb | Sha256 Sha1 Md5 | Trojanized Teamviewer | |
| 9bcb093f911234d702a80a238cea14121c17f0b27d51bb023768e84c27f1262a b2f847dce91be5f5ea884d068f5d5a6d9140665c 8ccbb51dbee1d8866924610adb262990 | Sha256 Sha1 Md5 | system.exe/ TeamViewer Starting.exe | |
| hxxp://kkk[.]no-ip[.]biz | URL | C&C | |
Related
Source: https://blog.cyble.com/2023/07/13/trojanized-application-preying-on-teamviewer-users/
Views: 0