Ransomware Operators Thrive in the Shadows
ARCrypter ransomware, also known as ChileLocker, emerged in August 2022 and gained attention following an attack on an entity located in Chile. Subsequently, researchers revealed that this ransomware started targeting organizations worldwide. The Threat Actors (TA)s responsible for this group do not maintain a leak site for extorting their victims. It has been observed that ARCrypter ransomware targets both Windows and Linux operating systems.
In early 2023, researchers reported the emergence of a new Linux variant of ARCrypter, developed using the GO programming language. Cyble Research and Intelligence Labs (CRIL) also discovered an updated version of the ARCrypt Windows executable, which previously existed in the wild.
This version of ARCrypt ransomware has been observed in the wild for approximately 2-3 months. During our investigation, we discovered some unusual techniques employed by the TA to interact with their victims.
In contrast to the older variant of ARCrypt ransomware, which utilized a common chat site hosted on Tor for all victims, we analyzed multiple binaries of the updated version and identified the following:
- The ransom note of each binary was pointing to a mirror site
- The TA created dedicated chat sites hosted on Tor for each victim
- In one instance, the ransom note instructed the victim to contact the TA via TOX, a messaging platform, by creating a profile with a specific username
Apart from this, we also found an instance shown in the figure below, where TA offered the victim a discount if the ransom was paid in Monero. Tracing transactions is difficult in Monero compared to Bitcoin, so some TAs prefer to use this. We have also observed AvosLocker ransomware in the past seeking ransom payments in Monero with added discounts.

This ransomware variant now utilizes the “.crYpt” instead of the “.crypt” extension to rename the encrypted filename and consists of a new ransom note. In this blog, we will further explore the changes observed in the ransomware binary and the communication method used by the threat actor (TA).
Analysis
Communication Method
During our analysis of multiple binaries of the ARCrypt ransomware, we discovered that each ransom note in the binaries directed victims to different Tor sites for communication, as highlighted in Figure below. Further investigation revealed that these sites were mirror sites, sharing the same user interface but having different URLs. Typically, ransomware TAs include all the mirror sites in the ransom note to ensure accessibility for victims. This approach allows victims to access an alternative site if one becomes inaccessible.

We conducted tests using login credentials obtained from various ransom notes, regardless of the associated Tor site mentioned in each note. However, these login credentials failed to authenticate on the Tor sites. This indicates that the provided login credentials are specific to the corresponding Tor site mentioned in the ransom note, further confirming that the threat actor (TA) creates dedicated Tor sites for each victim. Additionally, we observed that the Tor sites mentioned in older ransom notes were no longer accessible, suggesting that TA might be intentionally removing traces to clear their footprints.
The figure below shows the ARCrypt ransomware tor site.

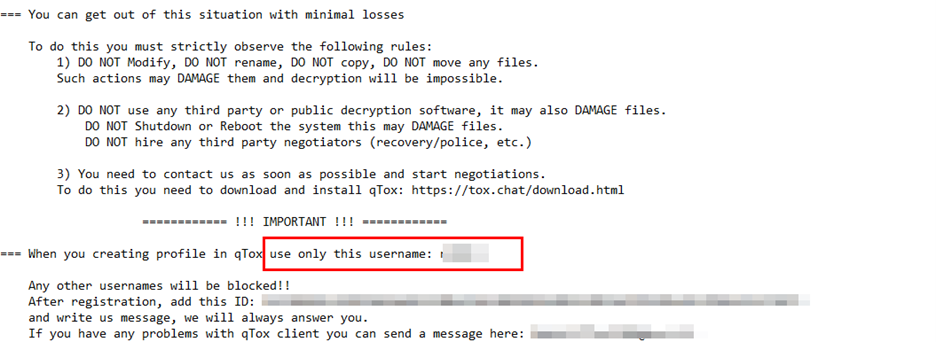
We also encountered an instance where the TA was urging its victim to create a profile on TOX with a specific username, as shown in the figure below. This highlights that the TA might be carrying out targeted attacks.
ARCrypt ransomware binary (SHA256: 4f2e40e6353a2430a80824d113268b5cdb28a0ddb079418be05ba79dea608410) is a 64-bit executable.
The figure below shows the file details.

Execution
Upon execution, the ransomware copies itself to the %TEMP% directory and assigns a random six-character alphanumeric string comprised of uppercase letters [A-Z] and digits [0-9] as its filename. It then proceeds to run from this location and deletes the original ransomware binary using the command “cmd /c DEL “%SAMPLEPATH%” &EXIT”. A batch script was employed in earlier versions to remove the initial executable file.
The figure below illustrates the portion of the ransomware responsible for self-deletion.

The updated variant of ARCrypt ransomware has the ability to terminate processes and disable specific services, including those related to anti-malware, backup, and recovery. This behavior suggests that the ransomware might be targeting servers.
| zhudongfangyu | QBFCService | BackupExecAgentBrowser |
| YooIT | QBCFMonitorService | BackupExecAgentAccelerator |
| YooBackup | PDVFSService | AcronisAgent |
| VSNAPVSS | Intuit.QuickBooks.FCS | mepocs |
| VeeamTransportSvc | DefWatch | memtas |
| VeeamNFSSvc | ccSetMgr | backup |
| VeeamDeploymentService | ccEvtMgr | AcrSchSvc |
| veeam | CAARCUpdateSvc | GxVss |
| stc_raw_agent | BackupExecVSSProvider | GxFWD |
| sophos | BackupExecRPCService | GxCVD |
| SavRoam | BackupExecManagementService | GxCIMgr |
| RTVscan | BackupExecJobEngine | GxBlr |
| QBIDPService | BackupExecDiveciMediaService | CASADDWebSvc |
The ransomware terminates the following processes. Due to the resource-intensive nature of the encryption process, the ransomware executables often terminate processes to free up system resources and accelerate the encryption process. It also terminates a few Endpoint Detection and Response (EDR) solutions as a means to evade detection.
| sql.exe | epam_svc.exe | mspub.exe |
| oracle.exe | EPWD.exe | onenote.exe |
| ocssd.exe | Compliance.exe | outlook.exe |
| dbsnmp.exe | cpda.exe | powerpnt.exe |
| synctime.exe | cptrayLogic.exe | steam.exe |
| agntsvc.exe | cptrayUI.exe | thebat.exe |
| ocautoupds.exe | TESvc.exe | thunderbird.exe |
| encsvc.exe | RemediationService.exe | visio.exe |
| firefox.exe | IDAFServerHostService.exe | winword.exe |
| tbirdconfig.exe | dbeng50.exe | wordpad.exe |
| mydesktopqos.exe | sqbcoreservice.exe | notepad.exe |
| ocomm.exe | excel.exe | isqlplussvc.exe |
| EFRService.exe | infopath.exe | xfssvccon.exe |
| epab_svc.exe | msaccess.exe | mydesktopservice.exe |
The figure below shows the process tree.

Artifacts
This ransomware uses RegCreateKeyA API to open registry keys under HKEY_LOCAL_MACHINE and uses RegSetValueExA API to set values for a specific key. The values being set to include “legalnoticecaption”, and “legalnoticetext” in the Key “HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystem”.
The following data is added to the values:
- legalnoticecaption: ALL YOUR FILES HAS BEEN ENCRYPTED!
- Legalnoticetext: For unlock your files follow the instructions from the readme_for_unlock.txt
It modifies this registry key to show a message during system startup.
The figure below shows the code for altering the registry keys.

The figure below shows the message displayed by the ransomware binary.

This ransomware variant renames the encrypted files with the extension “.crYpt”, whereas the older variant used the “.crypt” extension.
The figure below shows the encrypted files.

Ransom Note
This variant of ARCrypt ransomware introduces a distinct ransom note that bears only a few similarities to the older ransom note.
The figure below illustrates the comparison between the older and new ransom note.

Conclusion
The ARCrypt ransomware has evolved with an updated variant that incorporates certain changes. We believe the TA behind the ARCrypt ransomware is trying to avoid attracting unwanted attention. By updating the ransomware binary and adopting certain practices such as preferring ransom payments in Monero, not extorting victims through leak sites, and utilizing a new communication medium for each victim, the attacker aims to enhance their level of anonymity.
Our Recommendations
We have listed some of the essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
Safety Measures Needed to Prevent Ransomware Attacks
- Conduct regular backup practices and keep those backups offline or in a separate network
- Turn on the automatic software update feature on your computer, mobile, and other connected devices wherever possible and pragmatic
- Use a reputed anti-virus and Internet security software package on your connected devices, including PC, laptop, and mobile
- Refrain from opening untrusted links and email attachments without verifying their authenticity
Users Should Take the Following Steps After the Ransomware Attack
- Detach infected devices on the same network
- Disconnect external storage devices if connected
- Inspect system logs for suspicious events
Impact And Cruciality of Ransomware
- Loss of valuable data
- Loss of the organization’s reputation and integrity
- Loss of the organization’s sensitive business information
- Disruption in organization operation
- Financial loss
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
| Execution | T1204 | User Execution |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder |
| Defense Evasion | T1622 T1070 | Debugger Evasion Indicator Removal |
| Discovery | T1057 T1082 T1083 | Process Discovery System Information Discovery File and Directory Discovery |
| Impact | T1486 T1489 T1490 | Data Encrypted for Impact Service Stop Inhibit System Recovery |
Indicators of Compromise
| Indicators | Indicator type | Description |
| 9b80a70be01700866a667085aad93b5a 0408d6208440ef3caf7078361897f47c911de543 a933ebeb8bec26881b2d191f5034b7d6cacbb8d2cc06eeb7327f752fd0fab24d | MD5 SHA-1 SHA256 | ARCrypt Executable |
| 7df9c7e23c2a1f8d3d87cd2460bb275c b589fccc88bd05df102b7584c356fce21be1de58 94e227ad918034ae9b569a380a5e6c8928428862236395e3357a085b03f25fef | MD5 SHA-1 SHA256 | ARCrypt Executable |
| 90aeedae5648c65ca3c3fb2ac0380337 44069c654987abb00ce9068dd856bd2065a20aa9 e56eba93a0f3fab5e26c992a18cb6754c4b1a688e26a73c424d272babeab503c | MD5 SHA-1 SHA256 | ARCrypt Executable |
| a84957660902eb17fd021f3d187fb787 cb3700cb561a449e6ff88978fb4ce1495982fe95 b38807e5d6c4c4ae6811058fd868256abd6ed95f440e7f27ea81408bb9ee27fb | MD5 SHA-1 SHA256 | ARCrypt Executable |
| a0aad92f585dfc6ac762b5fc829e6fba 9ad2ae2c7fda526131ad6d535b21fe55d027d3aa 4f2e40e6353a2430a80824d113268b5cdb28a0ddb079418be05ba79dea608410 | MD5 SHA-1 SHA256 | ARCrypt Executable |
Related
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português