Intro
Resecurity has uncovered a cybercriminal group that is equipping fraudsters with sophisticated phishing kits to target banking customers in the EU. These kits are designed to intercept sensitive information, including credentials and OTP codes. The attackers use various social engineering tactics to trick victims into revealing their sensitive information. The kit is provided through Phishing-as-a-Service (PhaaS) model, and is also available for self-hosting.
One of the key actors, also known under alias “Vssrtje”, launched operations in March 2023, promoting the kit called “V3B” on Telegram and Dark Web communities. They have since built a client base focused on targeting European financial institutions. Currently, it is estimated that hundreds of cybercriminals are using this kit to commit fraud, leaving victims with empty bank accounts. Their Telegram channel has over 1,255 members, a significant indicator of the scale and scope of the malicious activity being promoted by the group.
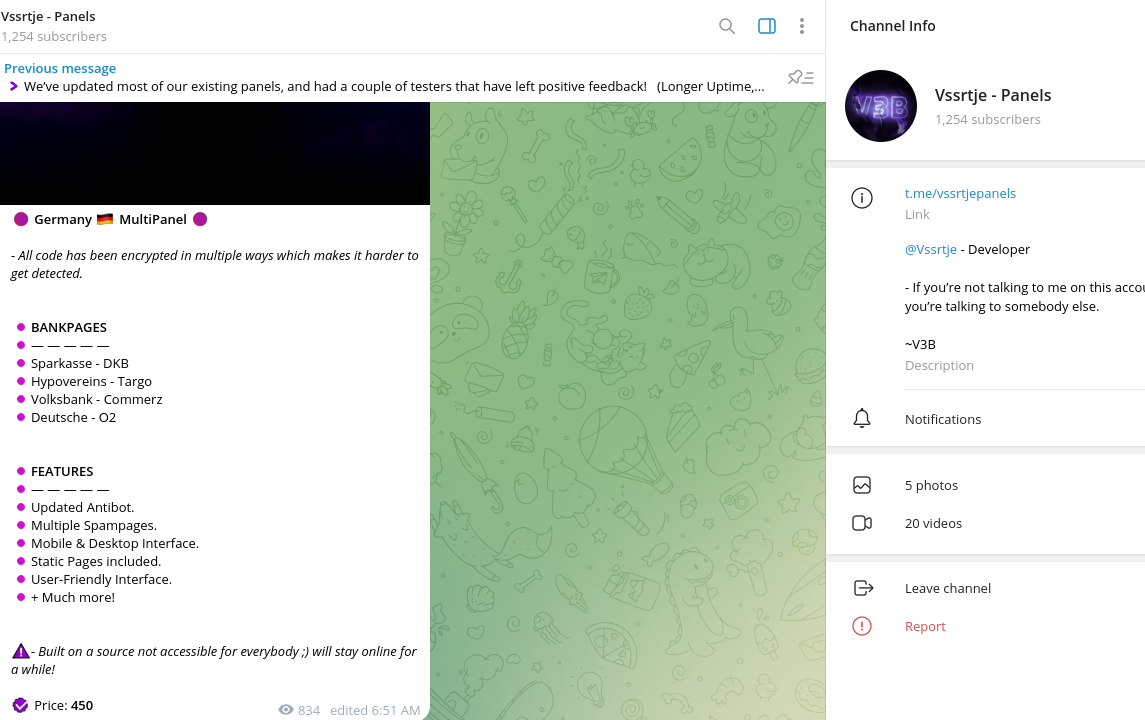
The majority of members on this Telegram channel are skilled cybercriminals who specialize in various forms of fraud. These include:
- Social engineering tactics
- SIM swapping schemes
- Banking and credit card fraud
The identified threat actors have been found to be primarily focusing on targeting EU-based banks, which are a key priority for them. Phishing activity has resulted in significant financial losses for European banking customers, estimated to be in the millions of euros. Bad actors have established a network of money mules in European countries, which enables them to process stolen financial data and facilitate illegal transactions.
Targeting Banks in European Union
Resecurity has acquired and analyzed multiple phishing kits, each customized to target specific banks, including top financial institutions in the EU:
– Ireland
Allied Irish Banks
– Netherlands
ICS Cards
– Finland
Nordea, Danske, OP Bank, Aktia, HandelsBank
– Austria
Bawag, VolksBank, George, Santander, EasyBank, Volksbank, Dadat, Bank99, Dolomiten, Raiffeissen, Bawag, Spardabank
– Germany
Sparkasse, DKB, Hypovereins, Targo, Volksbank, Commerzbank, Deutsche Bank, O2
– France
Epargne, Agricole, Populaire, Bourso, Socgenerale, HSBC, Hello, BNP Paribas, ING Bank, AXA Bank, Credit Agricole, Societe Generale
– Belgium
Fintro, Argenta, BNP, KBC, AXA, Belfius, BPOST, ING
– Greece
AlphaBank
– Luxembourg
ING
– Italy
Banco BPM, Poste Italiane
V3B phishing kit supports over 54 financial institutions featuring customized and localized templates to mimic authentication and verification processes of online banking and e-commerce systems in the EU.
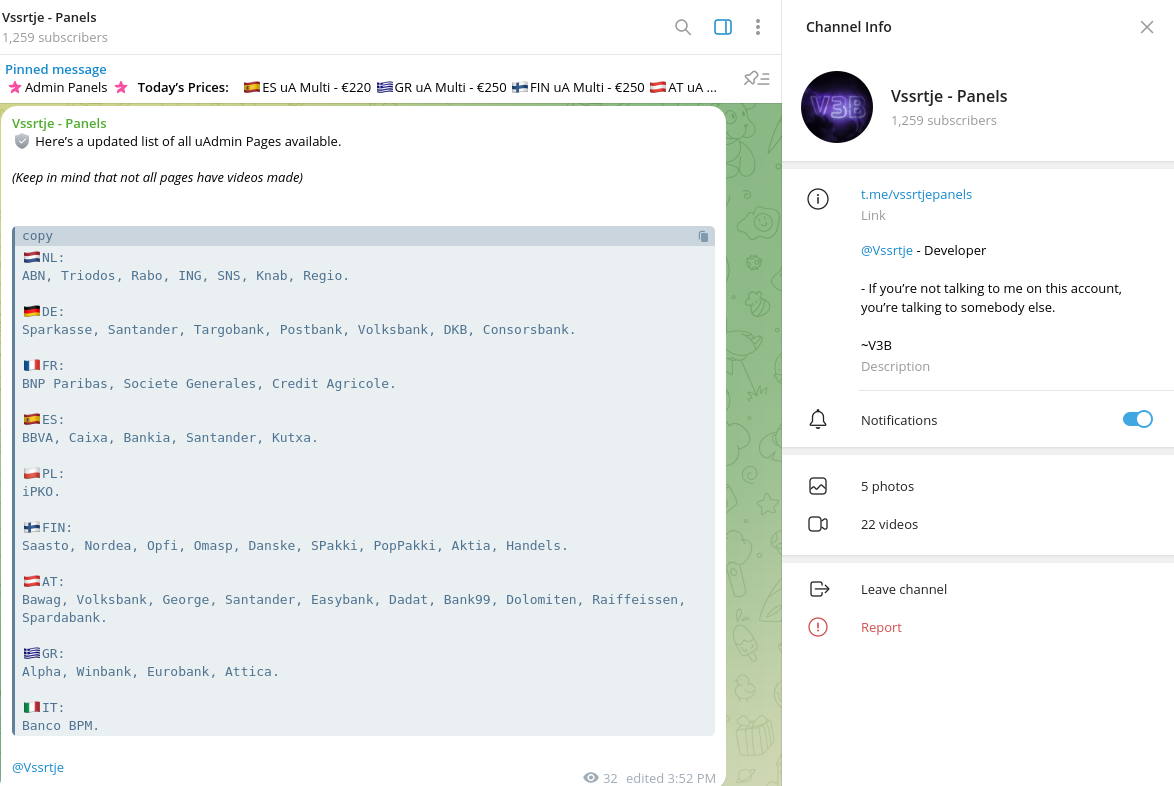
Evil Combination in Action (V3B + uPanel)
The phishing kit’s price varies between $130-$450 per month, paid in cryptocurrency. The cost depends on the specific modules and supported banks included in the kit. The author of the phishing kit regularly releases updates and adds new capabilities to evade detection, such as improved credentials-stealing algorithms and enhanced obfuscation techniques.
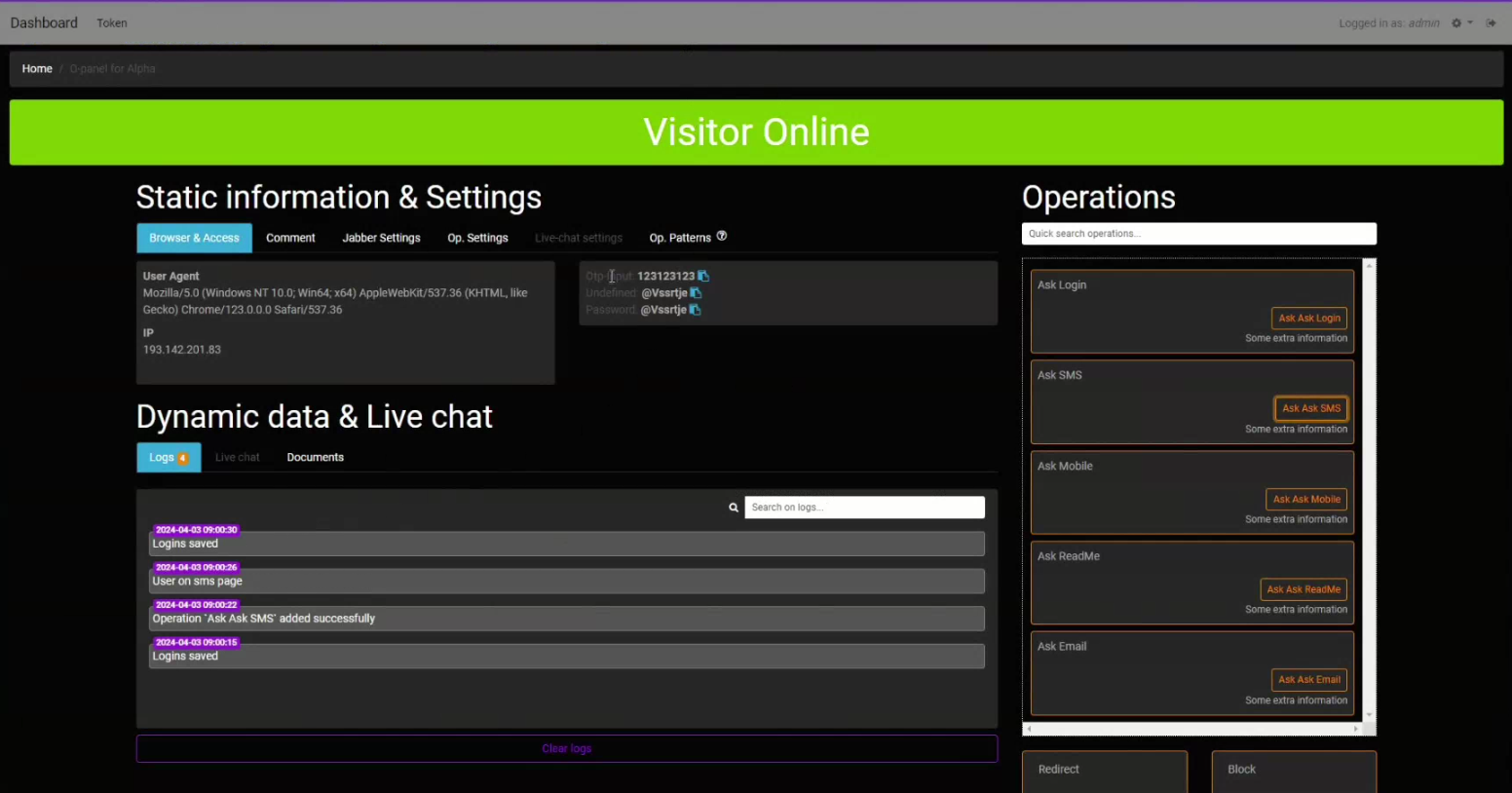
In fact, the phishing kit is comprised of two primary components: a scenario-based credential interception system (V3B), and mimic online-banking authorization pages. The administrative panel (uPanel) enables fraudsters to engage with victims and obtain one-time password (OTP) codes.
Key Features:
• Encrypted Code
The code for the live phishing kits is obfuscated (via JavaScript) in multiple ways to evade detection by anti-phishing systems, search engines and protect its source codes from signature analysis.
• Multi-Country Targeting
The kit targets multiple countries, including Ireland, the Netherlands, Finland, Austria, Germany, France, Belgium, Greece, Luxembourg, and Italy.
• Advanced Features
The kit includes advanced features such as:
+ Updated tokens
+ Anti-bot measures
+ Mobile and desktop interfaces
+ Live Chat (with victim) + OTP/TAN/2FA support including QR Codes and PhotoTAN method.
• Persistence
The kit is built on a customized CMS with obfuscated scenarios, ensuring it will evade detection and remain online for extended periods.
uPanel enables fraudsters to initiate an OTP / token request, tricking victims into entering their codes. The fraudster can then use these codes to verify the transaction.
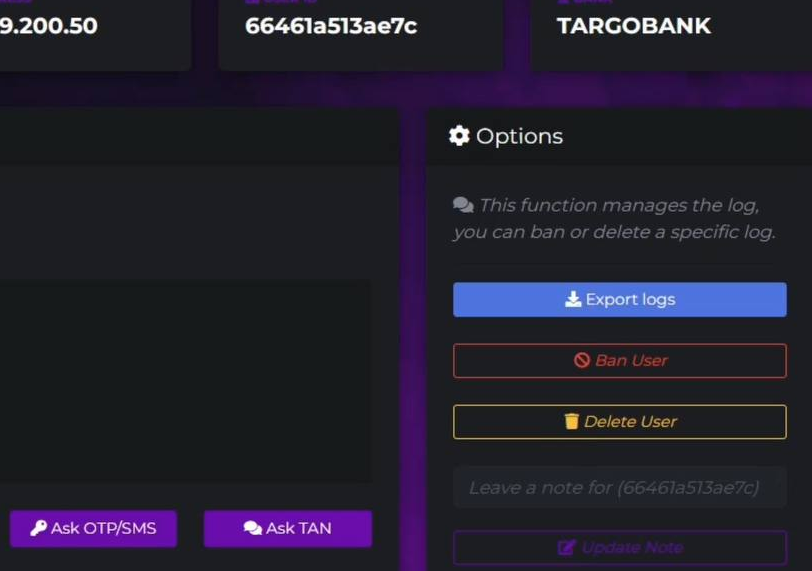
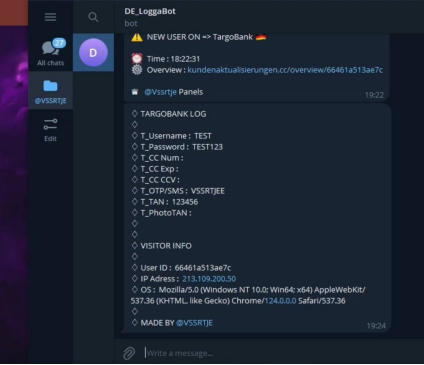
The phishing kit uses Telegram API as a communication channel to transmit intercepted payment data to the fraudster, alerting them to the successful completion of the attack.
The phishing kit has an advanced anti-bot system that detects and prevents detection by bots, robots, and security tools.
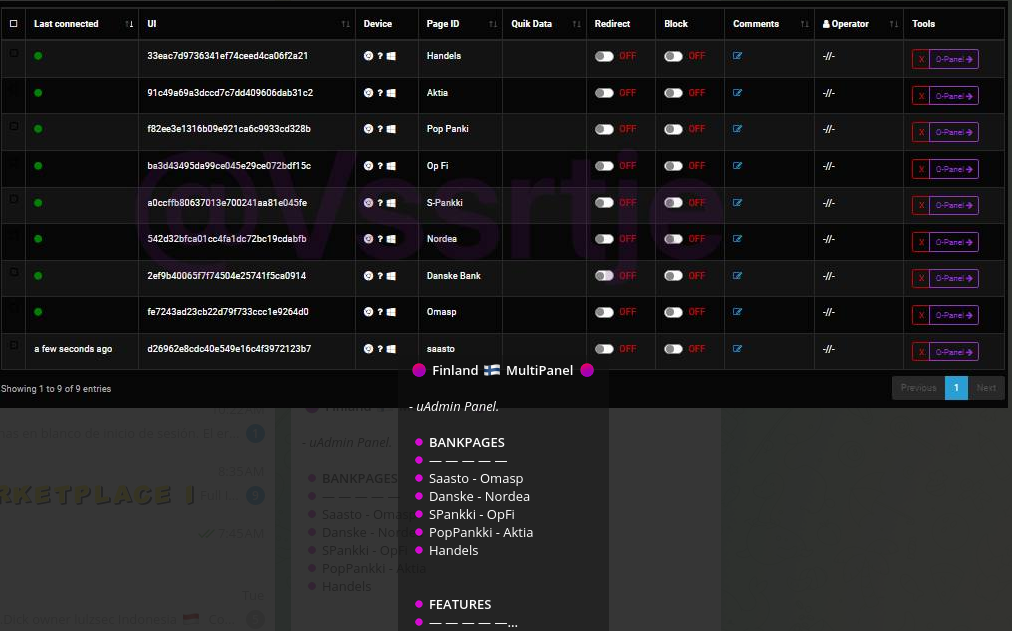
The phishing kit features advanced localization capabilities, including professionally translated pages in multiple languages, including Finnish, French, Italian, Polish and German.
Besides banks, the phishing kit also supports CC data interception. Around February 2024, the actors released a new module supporting International Cards Services (ICS) with localization of templates in Dutch:
Live Chat and Victim Tracking
The phishing kit contains an advanced system enabling fraudsters to interact with victims in real-time. In one such example, the actor tricks the victim into entering a PushTAN code as well as triggering an SMS OTP request in order to collect it from the victim and apply for further confirmation. Such method is widely used by online-banking thieves to bypass OTP validation. The actors released a customized module supporting such tactics for Sparkasse (Germany) in March:
Once the victim accesses the phishing page, the fraudster will immediately get notified. The kit will generated proactive “warning” (Visitor Online / Visitor Waiting), so he could trigger specific actions from the victim in order to leverage compromised access. The actors released a new module targeting Alpha Bank (Greece) and supporting such tactics to manipulate victim’s actions, confirming MyAlpha Code (OTP):
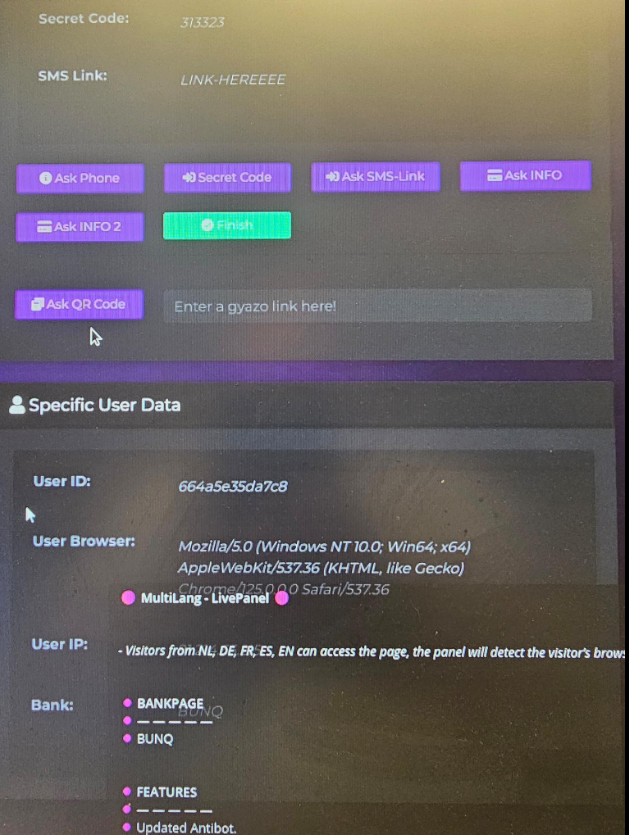
The events which could be triggered by the kit include:
– Ask Login
– Ask SMS/OTP
– Ask CC
– Ask Mobile
– Ask Email
– Ask DOB
– Ask PhotoTAN
– Ask SmartID
– Ask QR Code
– Show Notification (Custom Text)
– Show MFA Application Information (Custom Text)
Trigger combinations enable real-time interaction with the victim, allowing the phishing kit to orchestrate specific actions, gain unauthorized access, or facilitate fraudulent transactions.
QR code login jacking
One of the most notable features – trigger to generate request for QR Code. This feature, although relatively new, was initially introduced by cybersecurity researchers some time ago. According to research from Intel 471, a new twist on QR code phishing emerged in July 2023 from security researcher Kuba Gretzky, who developed a toolkit called EvilQR. Gretzky is also known for his work on Evilginx, a reverse proxy used in conjunction with phishing to snatch session cookies.
EvilQR executes a QR code login jacking (QRLJacking) attack on services that allow sign-in via QR codes. Many popular services, such as WhatsApp, Discord, and TikTok, offer this form of sign-in, making them vulnerable to this type of attack. The QR code is a dynamically generated session token that, when authorized by a user’s mobile phone, pairs with their account. The toolkit uses a browser extension to grab these QR codes from a service’s site and then immediately pipes them to a phishing site. If a victim scans the code, the attacker gains immediate access to the account. The image shows a frame collected from Gretzky’s demonstration proof-of-concept (PoC) video illustrating how the new tool works. A browser extension used by the attacker collects the sign-in QR code and uploads it to the phishing page at the right side. If the victim is already logged in to the target platform and scans the QR code, a dynamically generated session token is created, authorizing the attacker to take over the session.
V3B kit actors use the same approach, recognizing that QR codes are a crucial element of authorization for many financial services.
Novel Methods – PhotoTAN and Smart ID Support
Among all available action triggers, the one that stands out as particularly novel is the request for a PhotoTAN. The photoTAN app is a popular method of authentication for mobile banking that has a particularly high number of users in Germany and Switzerland. The photoTAN method involves the use of a separate device, the so-called photoTAN device, to generate TANs. TANs can be generated using photoTAN images.

Similar to QR codes, the idea of the kit is to receive the PhotoTAN code by triggering an event that asks the victim to provide it. According to Resecurity, this functional (Ask PhotoTAN) has been observed in modules of V3B kit targeting popular German banks specifically.
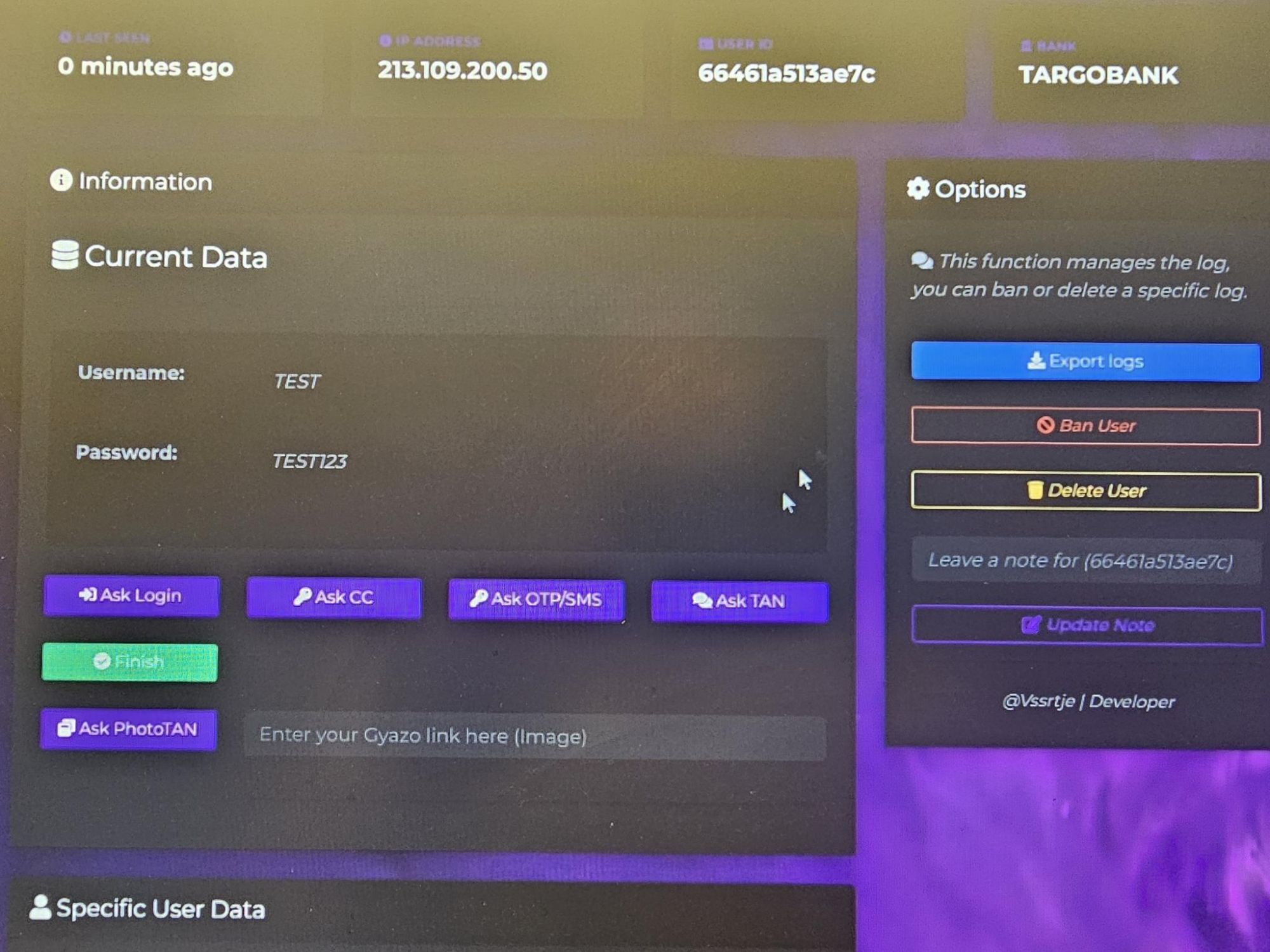
Resecurity has also observed the support of Smart ID (by the kit) in banking systems in Europe and the Baltics specifically, which may indicate that fraudsters are monitoring the latest 2FA technologies implemented by banks and seeking to exploit possible bypass methods to defraud their customers.
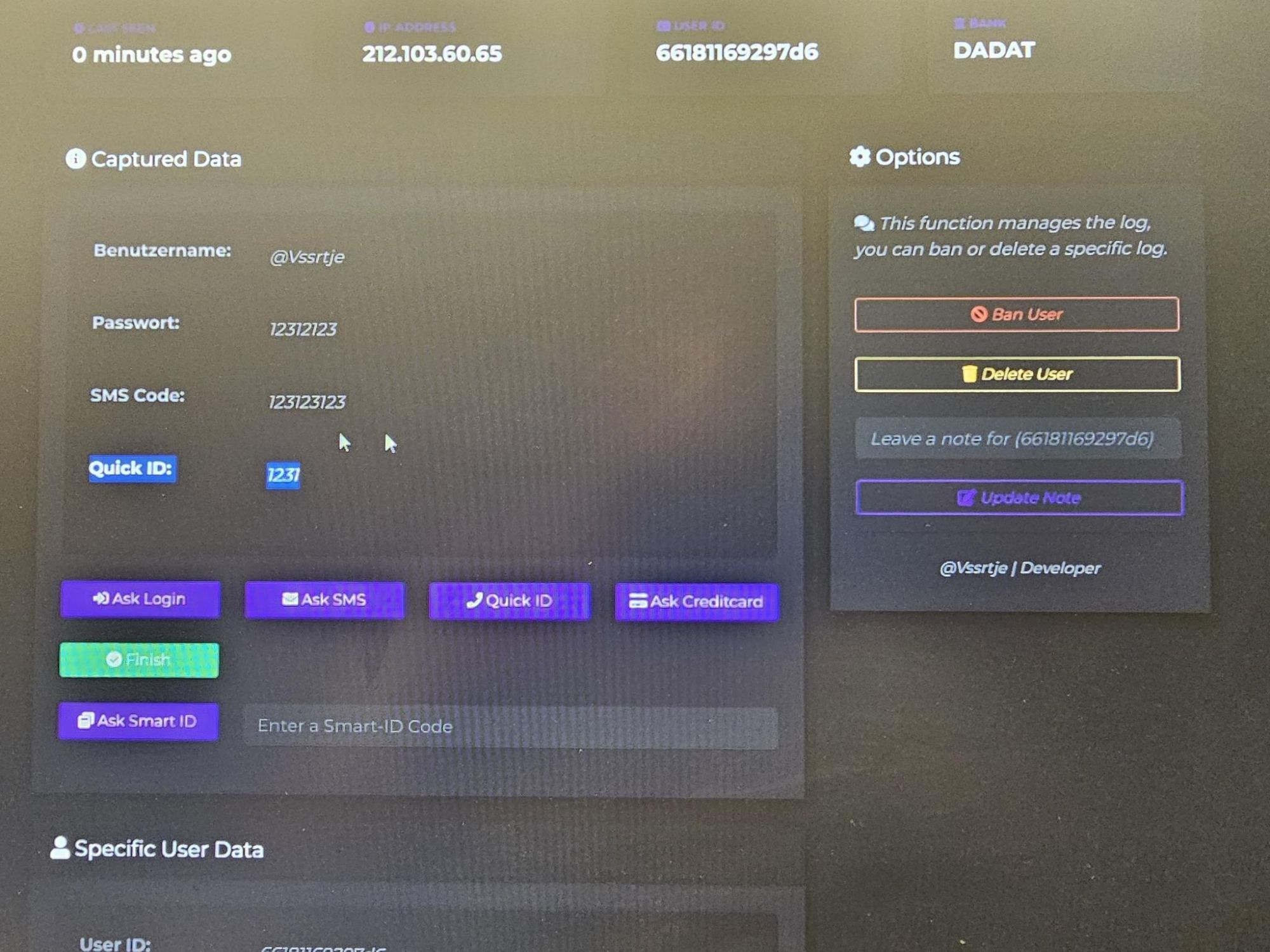
Of course, technologies used for customer authentication by banks may vary. However, the fact that fraudsters have started to implement support of alternative OTP/TAN validation mechanisms, rather than relying solely on traditional SMS-based methods, may confirm the challenges that fraud prevention teams will face in combating account takeover for both private and corporate customers.
Significance
Phishing attacks can result in substantial financial losses for organizations. In one instance, an aerospace company lost $47 million due to a successful whaling attack, where hackers impersonated the CEO to trick an employee into sending money. For example, in the United Kingdom, the annual value of online banking fraud losses reached approximately 159.7 million British pounds. In Canada, around $100 million was lost in the previous year due to online fraud, with the most common scams involving romance and investments. The European Union’s significant economy and mature financial system make it vulnerable to substantial losses from cybercrime activity and financial fraud, estimated in hundreds of millions of euros.
Cybercrime has emerged as a significant economic threat globally, with estimated losses of $11.50 trillion in 2023. The FBI, IMF, and other organizations forecast that cybercrime will continue to rise, potentially reaching $23 trillion by 2027, making it a major concern for organizations of all sizes. Phishing kits like V3B, available on the Dark Web, can cause significant financial losses for consumers. These advanced tools are accessible to fraudsters with a relatively low barrier to entry and can be purchased at a low cost, generating multi-million dollar losses.
To effectively prevent fraud, banks should maintain a proactive approach to dark web intelligence collection, staying informed about tools like V3B and continually updating their strategies and controls to protect customers. This includes monitoring the dark web for new tools and techniques, as well as implementing enhanced authentication and verification processes to prevent fraudulent activity.
Indicators of Compromise
Resecurity has acquired a list of Indicators of Compromise (IOCs) based on the analysis of recent campaigns involving V3B phishing kit. This valuable information can help security analysts track and detect new instances of V3B phishing kit-related activity and hosts associated with the threat actors.
MD5 Hashes:
9589194ff77c2edb9a2e89765f570c5e
3151764ce732dae8b863e15042ec2ac3
00a1b728410ef6fee05fff9bde46e541
20e77ddc3fe017e1bd711317adc86494
Domain Names:
kundenaktualisierungen[.]cc
icscards-nl[.]com
ics-cards[.]org
verifieer-gegevens[.]com
gemiste-aanmaning[.]com/belasting
redirect-bunq-client[.]ru/account/321/
kontoaktualisierer-nl[.]com/icscard.nl-v1
accounxt.bitvaqvio[.]nl-csdki.com
lnloggen-app[.]online/
app-lnloggen[.]online/authenticatie/inloggen/nl
abnamro.nl-appverifi[.]com/3/jjfosp/o34432fpo/index4.php
nl-appverifi[.]com
valideren-mijn-ics-web1[.]online/sq0.php?session=664483b236193
ics-beveiligde-verificatie[.]com/sqi.php
verifieer-nu[.]com/verificatie/66422f472f10c
nl-bunq-bijwerkerking[.]com
bvstigveriapp[.]online/pay/664130fb17583
reaktivieren-icsservice[.]nl/icscard.nl-v1/ics-log.php
belastingdienst-schuld[.]nl
bltvavo-bevestig.nt8zd3[.]ru
belastingoverzicht[.]info
bunq-app-nl[.]net
bunq-app-nl[.]net/K8IjL9/1M3k/lgn
black-loans7[.]shop
mijni-cs.bezoeknummer0734859938[.]info
https://mijni-cs.bezoeknummer0734859938[.]info/sca/7a970cab144c3e89685550829fe62941/login
bezoeknummer48912543221[.]info
icscardsvoorschriften[.]nl
abn-amro-gobal[.]com
reaktivieren-icsservice[.]nl/icscard.nl-v1/
lcs-valideren[.]online/ics/sca-app/663e0152c96c0
reaktivieren-icscard[.]nl
References
– PhotoTAN banking on mobile devices is not secure
https://www.fau.eu/2016/10/24/header/phototan-banking-on-mobile-devices-is-not-secure/
– Phishing Emails Abusing QR Codes Surge
https://intel471.com/blog/phishing-emails-abusing-qr-codes-surge
– FBI: Spoofing and Phishing
https://www.fbi.gov/how-we-can-help-you/scams-and-safety/common-scams-and-crimes/spoofing-and-phishi…
– CISA: Recognize and Report Phishing
https://www.cisa.gov/secure-our-world/recognize-and-report-phishing