
EXECUTIVE SUMMARY
A recent update from cybersecurity firm CrowdStrike caused the Blue Screen of Death (BSOD) on many Windows computers due to a faulty update to the Falcon Sensor agent. Millions of Windows-based systems across the globe experienced the dreaded Blue Screen of Death (BSOD), causing total system crashes. The issue disrupted businesses, airports, train stations, banks, broadcasters, and the healthcare sector globally. Cybercriminals quickly exploited the chaos and started phishing organizations and spinning up malicious domains purporting to be fixes. These domains were specifically designed to deceive users and propagate malicious activities.
The CYFIRMA research team conducted an analysis of these malicious domains to assist with mitigation efforts and protect affected users.
INTRODUCTION
CrowdStrike, a leading cybersecurity firm, recently released an update to its Falcon Sensor agent for Windows. Unfortunately, this update had a flaw that caused the Blue Screen of Death (BSOD) on many Windows computers globally. The BSOD is a type of error screen displayed on Windows computers following a fatal system error, indicating a system crash where the operating system can no longer operate safely. This incident caused significant disruption across various sectors, highlighting the critical importance of rigorous software testing and quality assurance. CrowdStrike has since identified and isolated the issue, halted the faulty update, and deployed a fix. They are actively working with impacted customers to resolve the issue. This problem is not a security incident or cyberattack, but manual intervention is required to fix each affected machine. The impact of the CrowdStrike BSOD issue was significant and global.
ANALYSIS OF MALICIOUS DOMAINS
Domain: crashstrike[.]com
Status: Not delivering any malware.
- In the past, resolving 172.67.206.221 has led to the delivery of the info stealer malware Lokibot.
- We observed a user on Twitter spreading the above malicious domain.
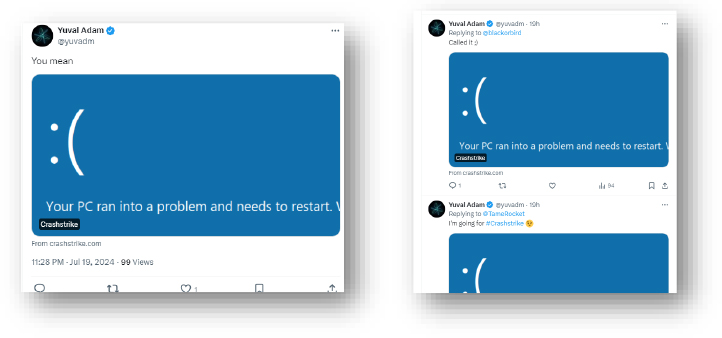
FIG: Twitter user: https://twitter.com/yuvadm
Domain: fix-crowdstrike-bsod[.]com
Status: Not delivering any malware.
- The IP address 185.199.108.153 is associated with GitHub, Inc. and is hosted by Fastly, Inc. It is used primarily for content delivery network (CDN) purposes, specifically under the hostname cdn-185-199-108-153.github.com. This IP address is part of the ASN 54113, which is managed by Fastly, a well-known CDN provider. The address is assigned for use by GitHub, making it part of their infrastructure for delivering content efficiently to users around the world.
- Additionally, the IP has been reported for suspicious activities in the past, indicating it has been used in some high-risk actions, although such reports are not uncommon for high-traffic IP addresses used by major services like GitHub (DB-IP). The threat actor is unknown behind this IOC.
Domain: bsodsm8rLIxamzgjedu[.]com
Status: Not delivering any malware.
- This domain seems unavailable at this moment leaving no detail to conduct further investigation.
Domain: crowdstrikebsodfix[.]blob[.]core[.]windows[.]net
Status: Not delivering any malware.
- Resolving to 20.38.122.68, it is associated with Microsoft Corporation and is typically used for Azure services. This IP address is part of Microsoft’s infrastructure, serving various purposes such as hosting, cloud services, and network management. Located in the United States, it is part of the larger Microsoft Azure IP range.
Domain: crowdstrikecommuication[.]app
Status: Not delivering any malware.
- This domain seems unavailable at this moment leaving no detail to conduct further investigation.
Domain: fix-crowdstrike-apocalypse[.]com
Status: Not delivering any malware.
- This domain is used for scamming. Specifically, asking users for donations in crypto after mentioning the solution to fix the blue screen error on their landing page.
- Resolving to IP address 80.78.22.84, the IP with no past malicious activity is communicating with the suspicious domain.
Domain: crowdstrikeoutage[.]info
Status: Not delivering any malware.
- This domain is used for guiding users to solutions for major outages.
- The domain is resolving to 89.117.139.195 with no malicious footprints from the past.
Domain: clownstrike[.]co[.]uk
Status: Not delivering any malware.
- The domain is used for trolling purposes.
- The domain is resolving to 185.199.222.21 with no malicious footprints from the past.
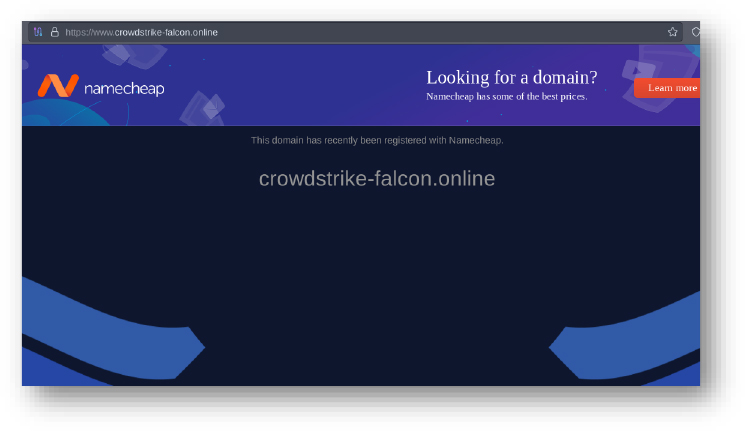
Domain: crowdstrike-falcon[.]online
- Status: The domain is parked currently, with the hosting provider being ‘Namecheap.’ In the past, the IP associated with the domain was found to be dropping Cobaltstrike by an Unknown Threat actor.
- Resolving IPs: 199.59.243.225, 192.64.119.170
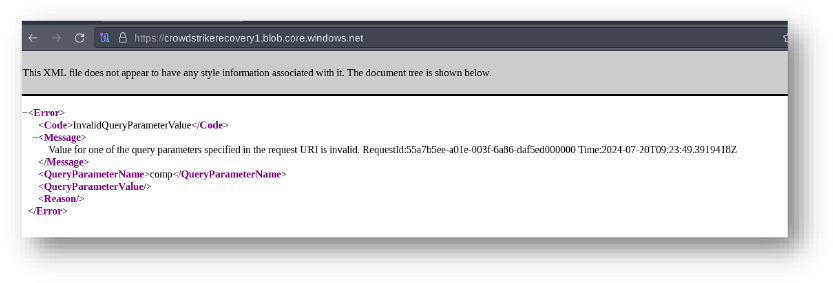
Domain: crowdstrikerecovery1[.]blob[.]core[.]windows[.]net
- Status: The subdomain is registered under MarkMonitor Inc., IP has previously been associated with the distribution of Commodity android trojans.
- Resolving IP: 20.60.132.100
Domain: crowdstrikeoutage[.]com
- Status: The domain is parked currently, with the hosting provider being Namecheap. In the past, the IP associated was found to be delivering commodity malware.
- Resolving IP: 192.64.119.34, 91.195.240.19
Domain: isitcrowdstrike[.]com
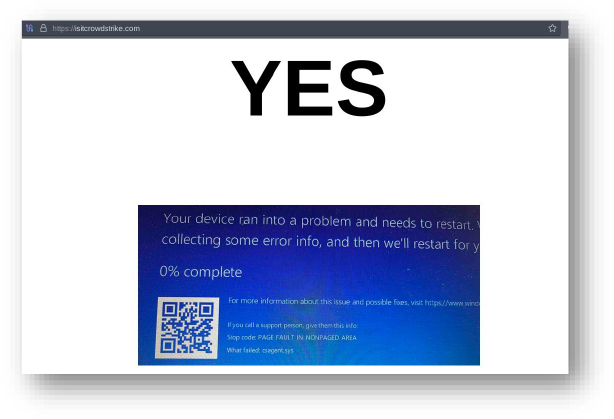
- Status: The domain appears to be registered to troll CrowdStrike. The associated IP address has a history of dropping FormBook malware or being involved in scams. The domain registrar is GoDaddy.
- Resolving IPs: 76.223.105.230, 13.248.243.5, 67.4.148.242
Domain: crowdstrike[.]black
- Status: The domain, registered with CSC Corporate Domains, Inc., currently shows “Server Not Found.” However, the associated IP address has previously been linked to the distribution of commodity malware.
- Resolving IP: 184.168.221.59
Domain: crowdstrikefix[.]zip
- Status: The domain, parked with Tucows, has been linked to phishing campaigns and SSH brute-force attacks. The threat actor is unknown, and the domain is currently inactive, or the server is down.
- Resolving IP: 198.185.159.144
Domain: failstrike[.].com
- Status: The domain appears to be registered to troll CrowdStrike.
- Resolving IP: 104.21.45.162, 172.67.216.164
Domain: winsstrike[.]com
- Status: Domain and server down.
Domain: supportfalconcrowdstrikel[.]com
- Status:– Domain and server down.
Domain: crowdfalcon-immed-update[.]com
- Status: Domain and server down.
Domain: microsoftcrowdstrike[.]com
- Status: Created using SquareSpace.com. The website is under construction, and no malware was observed.
- Resolving IP: 198.185.159.144
Domain: clownstrike. [.]co
- Status: The website looks like an attempt to demolish reputation/mock crowdstrike. No malware delivery was observed.
- Resolving IP: 3.33.251.168, 15.197.225.128
Domain: crowdstrikefix[.]com
- Status: crowdstrikefix[.]com is a suspicious domain registered with NameCheap, Inc. and associated with the IP address 91.195.240.19. The domain has been linked to Formbook malware, which steals sensitive information. Currently, the domain is inactive, indicating it may have been taken down.
- Malware observed: Commodity Malware.
- Resolving IP: 91.195.240.19
Domain: crowdstrikefix[.]com
- Status:– crowdstrikebluescreen[.]com is a suspicious domain registered with GoDaddy.com, LLC, and associated with IP addresses 13.248.243.5 and 76.223.105.230, located in the US. The domain has been linked to the Formbook malware, known for stealing sensitive information. Currently, the website is down.
- Resolving IP: 13.248.243.5, 76.223.105.230
Domain: crowdstrike-bsod[.]com
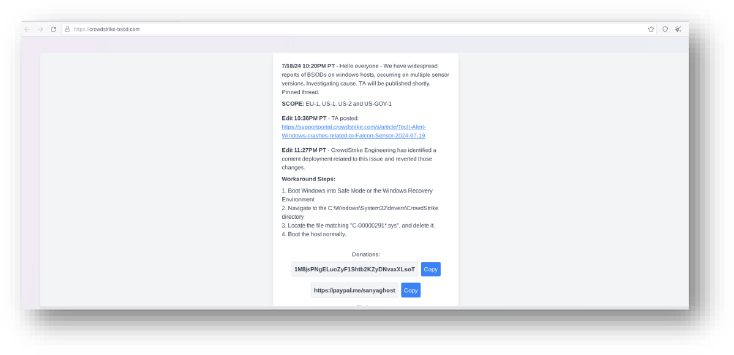
- Status:– crowdstrike-bsod[.]com is a suspicious domain registered with NameCheap, Inc. The website has been linked to the distribution of Commodity Malware. The site appears to provide false instructions and donation links, aiming to deceive users into executing potentially harmful actions on their systems.
- Resolving IP: 185.199.109.153
Domain: crowdstrikedoomsday[.]com
- Status:– This domain appears to be registered with Instra Corporation Pty Ltd. The identity of the threat actor associated with this domain is currently unknown.
- Resolving IP: 212.1.210.95
Domain: crowdstrike0day[.]com
- Status:– This domain is registered with NameCheap, Inc. The website is currently parked. The domain is potentially associated with threat actors from China, Russia, and North Korea, and may be related to the Formbook malware.
- Resolving IP: 198.185.159.145
Domain: crowdstriketoken[.]com
- Status:– The domain “crowdstrikedown[.]com” is associated with malicious activities, housing the Locky and Formbook malware. It is registered under Wix.com Ltd. Threat actors from China, Russia, North Korea, and Iran are attributed to activities related to this domain.
- Malware observed: Commodity Malware.
- Resolving IP: 185.230.63.171 and 34.149.87.45
Domain: crowdstrikedown[.]site
- Status:– The website “crowdstrikedown[.]site” appears to be currently unavailable. It is hosted on IP addresses 172.67.182.125 and 104.21.67.233 and is registered under Dotserve Inc.
- Resolving IP: 172.67.182.125, 104.21.67.233
Domain: crowdstrike-helpdesk[.]com
- Status:– The website “crowdstrike-helpdesk[.]com” is currently parked and inaccessible. It is registered under Squarespace Domains LLC. According to reports, the site has been linked to malware such as Renos and Formbook, with threat actor attributes potentially involving Chinese, Russian, and North Korean groups.
- Resolving IP: 198.185.159.144
Domain: crowdstrikereport[.]com
- Status:– 1-day old, created on 2024-07-19, and consequently, creates suspicion. This coincides with the Microsoft/Crowdstrike Blue Screen update incident. Probably aimed at phishing purposes but currently isn’t accessible. IP associated in the past with detection: Win.Ransomware.TeslaCrypt-9950169-0″
- Resolving IP: 104.21.75.98, 172.67.220.94
Domain: crowdstrikefix[.]zip

- Status:– 1-day old, created on 2024-07-19, and consequently, creates suspicion. This coincides with the Microsoft/Crowdstrike Blue Screen update incident and is probably aimed at phishing purposes.
- Resolving IP: 198.185.159.144
Domain: crowdstrike-cloudtrail-storage-bb-126d5e[.]s3[.]us-west-1[.]amazonaws[.]com
- Status:– Our assessment returned an XML error response, which is typically returned by cloud storage services like Amazon S3 or Google Cloud Storage when access to a resource is denied.
- Resolving IP: 3.5.160.162, 52.219.116.113, 52.219.220.138, 52.219.193.130, 52.219.121.66, 207.171.166.22
Domain: hoo[.]be/crowdstrike
- Status:– IP mentioned as IOCs in the past with detection: Win.Ransomware.TeslaCrypt-9950169-0″. Different links are provided which leads to other URLs.
- Resolving IP: 76.76.21.22
Domain: crowdstrike[.]orora[.]group
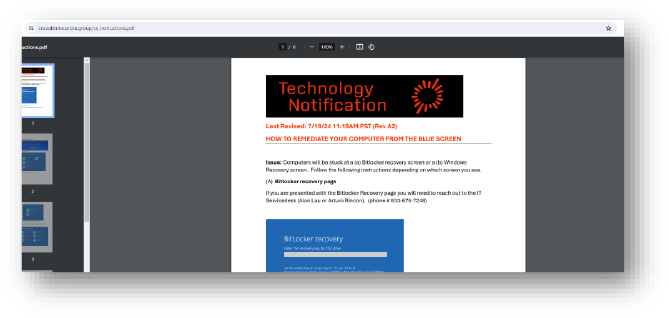
- Status: This link is provided to download a PDF file containing instructions to remediate and up the system after the Crowdstrike blue screen. PDF downloads (70DD468AE2CF038F23058BC96D0B842F), PDF mentions clean by multiple security solution vendors. Phone no. is also provided to provide support. Possibly an attempt at social engineering.
- Resolving IP: 35.81.42.29, 34.215.111.121, 54.68.181.161, 52.88.12.134, 13.248.243.5
Domain: supportportal.crowdstrike[.]com/s/login/?mkt_tok=MjgxLU9CUS0yNjYAAAGUa2XCfb6M3jra…
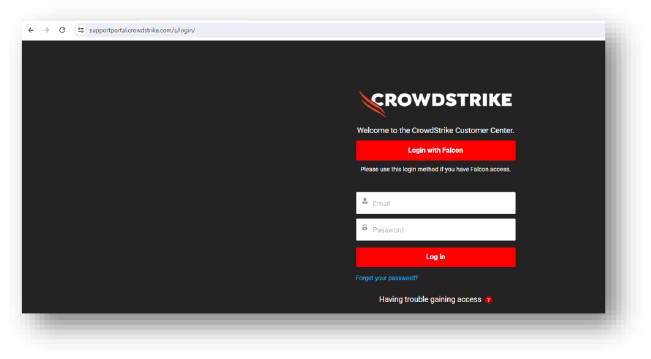
- Status:– Redirected to Crowdstrike login page. The higher-level domain belongs to Crowdstrike. This looks valid.
- Resolving IP: 104.16.180.118
Domain: crowdstrike[.]okta[.]com/app/coupa/exkqmsghe0qkvea070x7/sso/saml
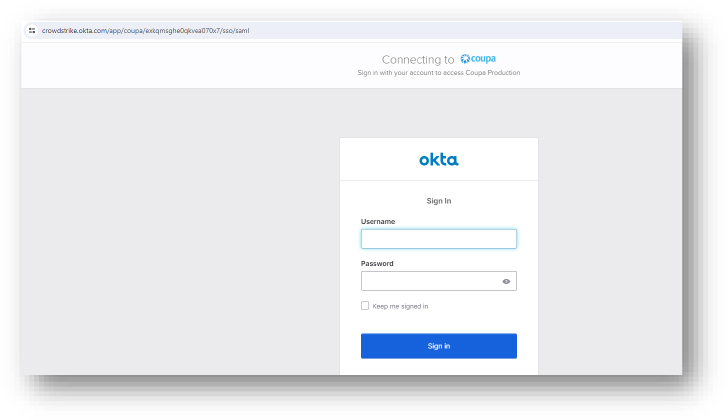
- Status:– Following this page opens a subdomain used by Crowdstrike, possibly to encash the recent update incident. Shows an Okta login page which we assess to be a possible phishing attempt to steal credentials. Okta is an identity management service that connects people to applications on any device.
- Resolving IP: 104.18.211.105, 75.2.87.65, 99.83.213.230
Domain: crowdstrikehealthcare[.]com
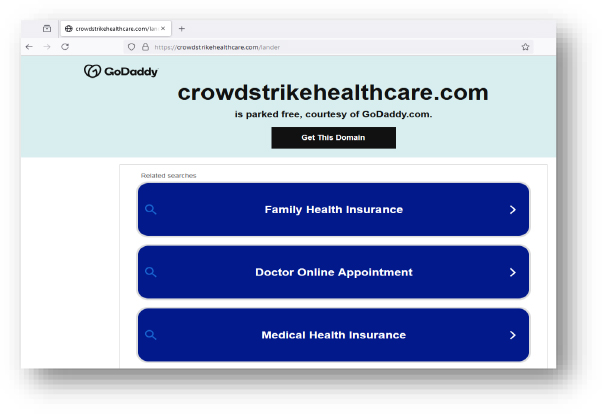
- Status:– The domain is being hosted on a shared server. HTTP requests to this domain land on “/lander” page, Both IP addresses are flagged as malicious with a historical IP address (34.102.136.180).
- Observation: No direct malicious indicator was observed.
- Resolving IP: 3.33.130.190, 15.197.148.33
Domain: crowdstrikeclaim[.]com
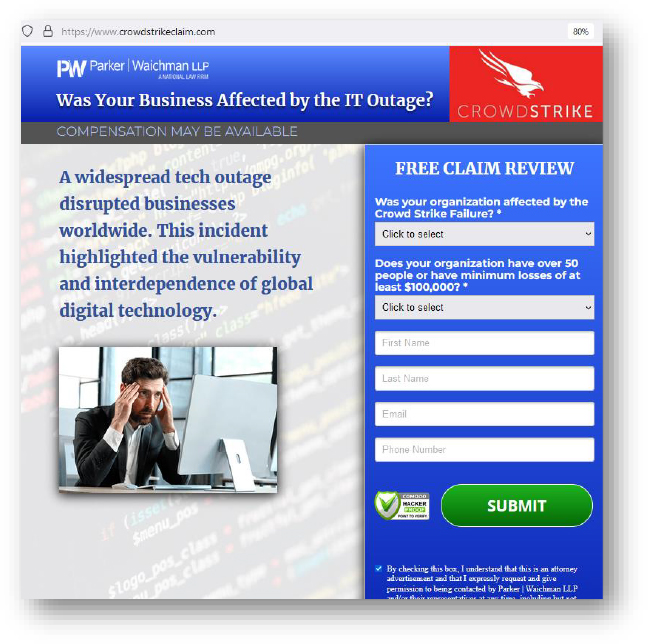
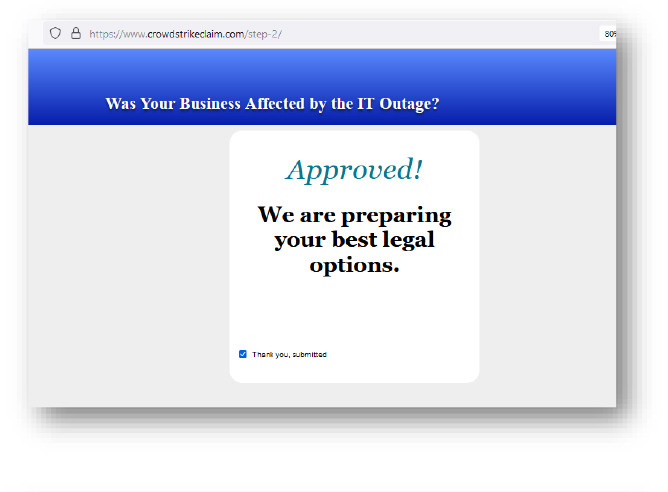
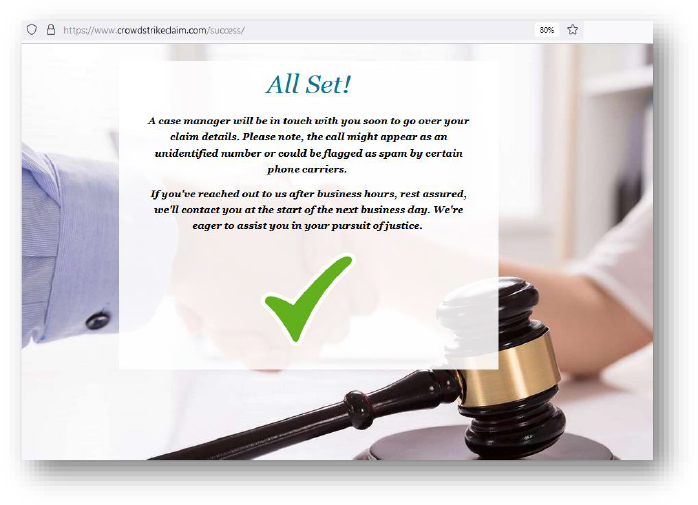
- Status: This domain is being hosted on a shared server and is flagged as malicious.
- Observation: Phishing website, trying to leverage the recent CrowdStrike outage incident. No malicious payload was observed.
- Resolving IP: 54.84.104.245 (crowdstrikeclaim.com), 104.18.19.37 (www. crowdstrikeclaim.com)
Domain: crowdstrikebug[.]com
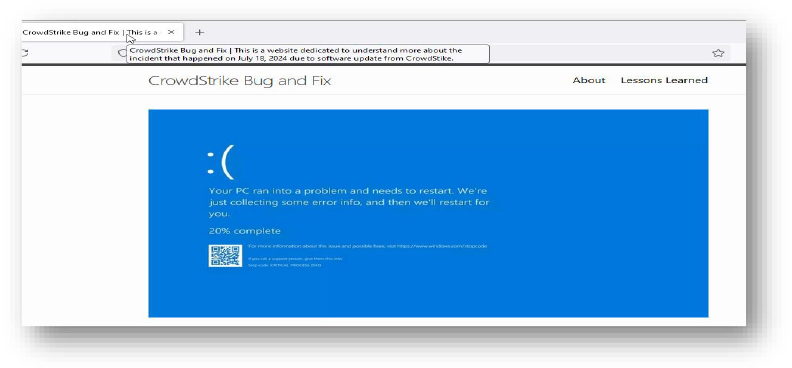
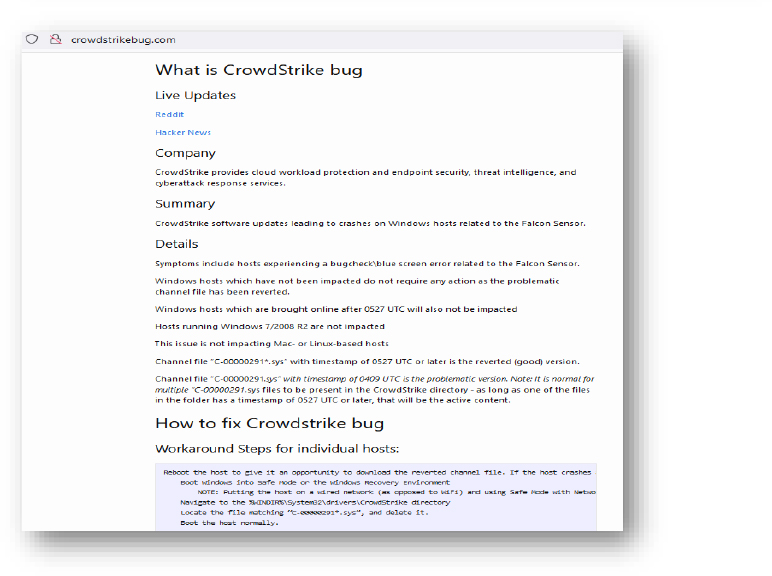
- Status: This website discusses the recent CrowdStrike outage incident and the workaround for this. No malicious link/URL or payload was observed.
- Resolving IP: 185.199.110.153, 185.199.108.153, 185.199.109.153, 185.199.111.153
Domain: crowdstrikeupdate[.]com
- Status:– No direct malicious indicator observed.
- Resolving IP: 185.53.177.53, 104.247.81.53
Domain: crowdstrikefail[.]com
- Status: The website owner is also associated with the domain crowdstrikeoopsie[.]com and crowdstrike[.]fail. No direct malicious indicator was observed.
- Resolving IP: 172.67.158.135, 104.21.14.88
Domain: crowdstrike[.]fail
- Status: The domain is being hosted on a shared server and has no detection for malicious activity. The website owner is also associated with the domain crowdstrikefail[.]com and crowdstrikeoopsie[.]com. No Direct malicious indicator was observed.
- Resolving IP: 104.21.19.9, 172.67.184.97, 2606:4700:3031::6815:1309
Domain: crowdstrikeoopsie[.]com
- Status: The domain is being hosted on a shared server and has no detection for malicious activity. The website owner is also associated with the domain crowdstrikefail[.]com and crowdstrikeoopsie[.]com. No Direct malicious indicator was observed.
- Resolving IP: 104.21.20.201, 104.21.20.201
Domain: crowdstrike[.]woccpa[.]com
- Status: No direct malicious indicator observed.
- Resolving IP: 208.91.197.24
CAMPAIGN DETAILS OBSERVED
CYFIRMA’s research team observed a campaign launched by hackers to monetize the fallout of this situation known as Campaign – Reap BlueScreen. As part of this campaign, hackers are potentially looking to inflict damage and intrude on systems by leveraging mass-scale phishing domains to target unsuspecting end users.
Our investigation has observed 45+ phishing domains already in the wild which could potentially be used by hackers to target users, and systems, globally.
The details of the campaign are given below:
- Suspected Hacking Group: Unknown Groups.
- Suspected Campaign: “Reap BlueScreen”, suspected to be active since 19 July 2024.
- Target Industries: Across Industries.
- Target Geographies: Worldwide.
- Target Technology: MS Windows, Applications & Services.
- Motivation: Credential Theft, Financial Gains, Gaining Elevated Access.
- Method Discussed by Hackers and their Interest: Spear-Phishing, Exploiting weakness of the systems, Lateral movement across the organization’s network.
Further investigation into the campaign is currently ongoing.
CONCLUSION
The recent CrowdStrike BSOD incident was a significant event that disrupted many systems worldwide. This incident highlights the importance of rigorous testing and quality assurance in software updates, especially for systems that are critical to business and infrastructure operations. Additionally, this incident underscores highlights the need for constant vigilance, prompt action, and robust cybersecurity measures in our increasingly interconnected digital world. It’s a stark reminder that in the realm of cybersecurity, the stakes are high, and the impact of a single point of failure can be far-reaching.
Here are the steps to fix this issue:
- Boot your Windows system into safe mode or the Windows Recovery Environment (winRE).
- Open the File Manager and navigate to C:WindowsSystem32driversCrowdStrike.
- Look for and delete any files that match the pattern C-00000291*.sys.
- Reboot as normal.