### #WordPressSecurity #PluginVulnerabilities #WebApplicationRisks
Summary: A report has identified two critical vulnerabilities in the Anti-Spam by CleanTalk WordPress plugin, affecting over 200,000 installations and allowing unauthenticated attackers to compromise websites. Users are urged to update to the latest version to mitigate these risks.
Threat Actor: Unauthenticated Attackers | unauthenticated attackers
Victim: Anti-Spam by CleanTalk Users | Anti-Spam by CleanTalk
Key Point :
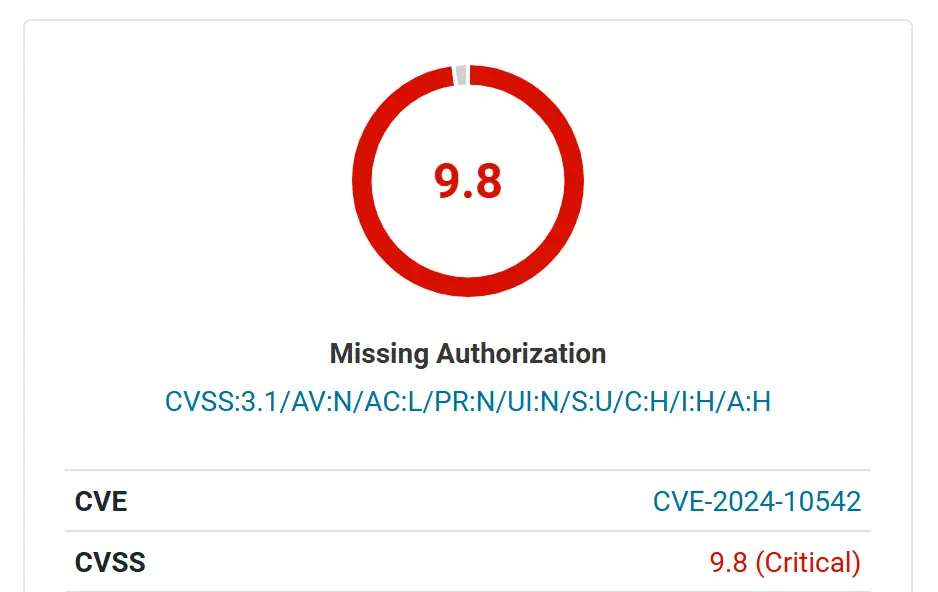
- Two vulnerabilities, CVE-2024-10542 and CVE-2024-10781, allow attackers to install malicious plugins and execute arbitrary code.
- CVE-2024-10542 involves an authorization bypass due to reverse DNS spoofing, enabling remote plugin activation.
- CVE-2024-10781 results from a lack of checks on empty API keys, allowing unauthorized access to unconfigured sites.
- Both vulnerabilities have a CVSS score of 9.8, indicating critical severity.
- Users are strongly advised to update to version 6.45 of the plugin to secure their websites.
A recent report from the Wordfence Threat Intelligence Team has revealed two critical vulnerabilities in the Anti-Spam by CleanTalk WordPress plugin, impacting over 200,000 active installations. These vulnerabilities, tracked as CVE-2024-10542 and CVE-2024-10781, could allow unauthenticated attackers to compromise websites by installing malicious plugins and executing arbitrary code.
Reverse DNS Spoofing and Empty API Key Checks Lead to Authorization Bypass
The first vulnerability, CVE-2024-10542, stems from an authorization bypass issue related to reverse DNS spoofing. As the report explains, “The IP address is determined based on the X-Client-Ip and X-Forwarded-By header parameters, which are user-defined parameters making this function vulnerable to IP address spoofing.” This flaw allows attackers to manipulate DNS records and bypass authentication checks, gaining the ability to install and activate plugins remotely. This flaw was responsibly disclosed by researcher mikemyers through the Wordfence Bug Bounty Program, earning a bounty of $4,095.00.
The second vulnerability, CVE-2024-10781, arises from a missing empty value check on the API key. “Unfortunately, the function does not include any checks to prevent authorization when the API key is empty,” states the report. This means that sites with an unconfigured API key are vulnerable to unauthorized access, enabling attackers to perform actions like plugin installation and activation.
Urgent Action Needed to Secure WordPress Sites
Both vulnerabilities carry a CVSS score of 9.8, highlighting their critical severity and the potential for widespread exploitation. The Wordfence Threat Intelligence Team urges all users of the Anti-Spam by CleanTalk plugin to update to the latest patched version, 6.45, immediately.
“We urge users to update their sites with the latest patched version of Anti-Spam by CleanTalk, version 6.45 at the time of this writing, as soon as possible,” the report emphasizes.
Protecting Your WordPress Website
This incident serves as a stark reminder of the importance of keeping WordPress plugins up to date. Website owners and administrators should:
- Update Anti-Spam by CleanTalk: Immediately update to version 6.45 or later to patch these vulnerabilities.
- Regularly Update Plugins: Establish a routine for regularly updating all WordPress plugins and themes.
- Use a Web Application Firewall (WAF): A WAF can help protect against various attacks, including plugin vulnerabilities.
- Monitor Website Activity: Regularly monitor website activity for any suspicious behavior.