Threat Actor: Unknown | Unknown
Victim: Palo Alto Networks | Palo Alto Networks
Price: Not applicable
Exfiltrated Data Type: Not applicable
Additional Information:
- The vulnerability, designated as CVE-2024-3400, affects Palo Alto Networks’ PAN-OS software, specifically targeting the GlobalProtect feature.
- The vulnerability allows malicious actors to execute arbitrary code with root privileges on vulnerable firewalls.
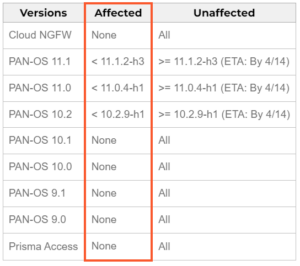
- The vulnerability impacts PAN-OS versions 10.2, 11.0, and 11.1 when both GlobalProtect gateway and device telemetry are enabled.
- Cloud NGFW, Panorama appliances, and Prisma Access are confirmed to be unaffected by this vulnerability.
- The severity of the vulnerability is classified as CRITICAL with a CVSSv4.0 Base Score of 10.
- Palo Alto Networks is working on fixes for affected PAN-OS versions, with scheduled availability by April 14, 2024.
- A recommended mitigation strategy involves enabling Threat ID 95187 for customers with a Threat Prevention subscription.
- Customers are advised to apply vulnerability protection to their GlobalProtect interface for additional protection.
- Temporary workarounds include disabling device telemetry until the affected device can be upgraded to a patched version of PAN-OS.
A significant security flaw has been unearthed within Palo Alto Networks’ PAN-OS software, specifically targeting the GlobalProtect feature. Designated as CVE-2024-3400, this vulnerability poses a grave risk to the integrity and security of affected systems, potentially allowing malicious actors to execute arbitrary code with root privileges on vulnerable firewalls.
Vulnerability Overview
The vulnerability manifests in PAN-OS versions 10.2, 11.0, and 11.1, particularly impacting configurations where both GlobalProtect gateway and device telemetry are enabled. This specific combination creates a gateway for exploitation, opening the door to unauthorized access and potential compromise of critical systems.
It’s important to note that certain PAN-OS deployments remain unaffected by this vulnerability. Cloud NGFW, Panorama appliances, and Prisma Access have been confirmed as not impacted, providing reassurance to users of these systems.
Severity Assessment: CRITICAL
Given its severity, the vulnerability has been classified with a CVSSv4.0 Base Score of 10, highlighting the critical nature of the threat it poses.
Evaluating System Exposure
To determine whether your firewall is susceptible to this vulnerability, it is imperative to conduct a thorough examination of your configurations:
GlobalProtect Gateway: Inspect configurations via the firewall web interface under Network > GlobalProtect > Gateways.
Device Telemetry: Verify the status of device telemetry by accessing the firewall web interface under Device > Setup > Telemetry.
Fixes for Affected Versions
In response to this critical issue, Palo Alto Networks is working on fixes for affected PAN-OS versions. These fixes are anticipated to be released promptly, with scheduled availability by April 14, 2024. However, proactive measures are essential to mitigate risk until patches are applied.
Recommended Workarounds and Mitigation Strategies
To safeguard against potential exploits, the following mitigation strategies are advised:
Recommended Mitigation: Customers equipped with a Threat Prevention subscription possess the capability to thwart attacks associated with this vulnerability. By enabling Threat ID 95187 (introduced in Applications and Threats content version 8833-8682), users can effectively mitigate the risk posed by potential exploits.
Additional Protection Measures: In conjunction with enabling Threat ID 95187, it is imperative for customers to ensure the application of vulnerability protection to their GlobalProtect interface. This additional layer of defense serves to fortify systems against exploitation attempts, bolstering overall security posture.
Temporary Workarounds: In scenarios where immediate implementation of Threat Prevention-based mitigation is unfeasible, alternative measures can still be employed to mitigate vulnerability impact. One such approach involves temporarily disabling device telemetry until the affected device can be upgraded to a patched version of PAN-OS. Once the upgrade is completed, device telemetry functionality should be promptly re-enabled to ensure comprehensive system monitoring and security.
Original Source: https://dailydarkweb.net/critical-os-command-injection-vulnerability-cve-2024-3400-found-in-palo-altos-globalprotect-gateway/