Summary: A critical vulnerability in the Chartify WordPress Chart Plugin, tracked as CVE-2024-10571, allows unauthenticated local file inclusion, enabling attackers to execute malicious code on affected websites. With over 2,000 installations, the vulnerability has led to widespread exploitation, prompting urgent updates for website administrators.
Threat Actor: Unknown | unknown
Victim: Chartify Plugin Users | Chartify Plugin Users
Key Point :
- Vulnerability CVE-2024-10571 has a CVSS score of 9.8 and affects all versions of the Chartify plugin up to 2.9.5.
- Attackers can exploit the flaw to bypass access controls, obtain sensitive data, or execute arbitrary PHP code.
- Over 2 million attacks targeting this vulnerability were blocked in just 24 hours, indicating a widespread exploitation campaign.
- Website administrators are urged to update to version 2.9.6 or newer to mitigate the threat.
- Proactive security measures, including regular updates and strong authentication, are essential for protecting WordPress websites.
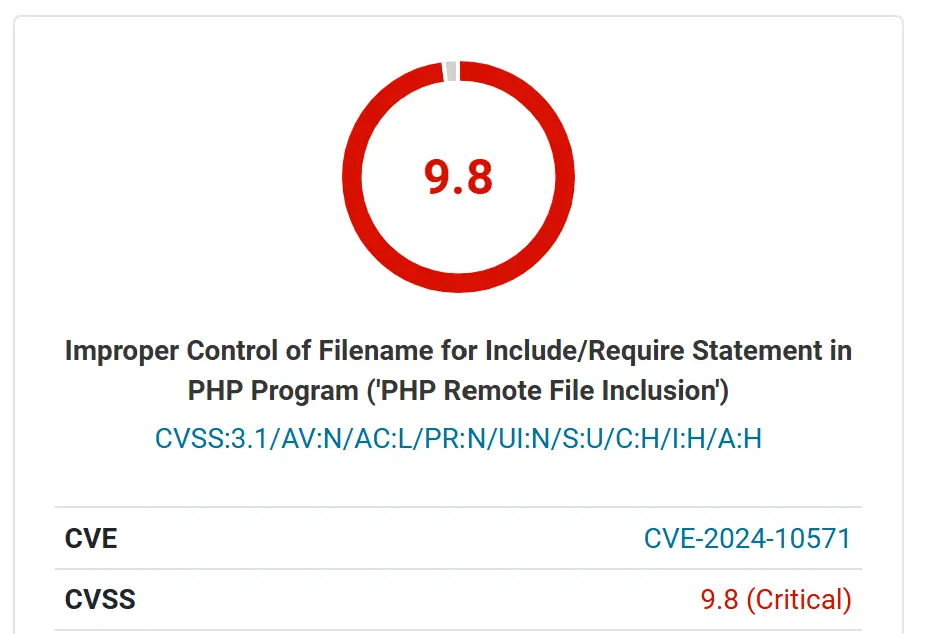
Administrator websites are facing a new threat as attackers actively exploit a critical vulnerability in the popular Chartify – WordPress Chart Plugin. This plugin, with over 2,000 active installations, is vulnerable to unauthenticated local file inclusion, enabling attackers to execute malicious code on affected websites.
CVE-2024-10571: Unauthenticated Local File Inclusion Flaw
Tracked as CVE-2024-10571 and assigned a CVSS score of 9.8, this vulnerability affects all versions of the Chartify plugin up to and including 2.9.5. The flaw stems from improper handling of the ‘source’ parameter, allowing attackers to inject arbitrary files and execute malicious PHP code.
“This can be used to bypass access controls, obtain sensitive data, or achieve code execution in cases where images and other “safe” file types can be uploaded and included,” warns the vulnerability report.
Widespread Exploitation Underway
The severity of this vulnerability is amplified by its active exploitation in the wild. Wordfence, a leading WordPress security firm, reports blocking a staggering “2,207,540 attacks targeting this vulnerability in the past 24 hours.” This indicates a widespread campaign by malicious actors to compromise vulnerable websites.
Urgent Action Required: Update Now!
Website administrators using the Chartify plugin are urged to take immediate action to mitigate this threat. The recommended solution is to update to version 2.9.6 or a newer patched version as soon as possible.
Protecting Your WordPress Website
This incident serves as a stark reminder of the importance of proactive security measures for WordPress websites. Here are some essential steps to protect your site:
- Keep Plugins and Themes Updated: Regularly update all plugins and themes to the latest versions to patch security vulnerabilities.
- Use a Web Application Firewall (WAF): A WAF can help block malicious traffic and prevent attacks from reaching your website.
- Implement Strong Passwords and Two-Factor Authentication: Secure your WordPress admin accounts with strong passwords and enable two-factor authentication for an extra layer of protection.
- Regularly Back Up Your Website: Create regular backups of your website files and database to ensure you can quickly recover from a compromise.
By taking these proactive steps, you can significantly reduce the risk of falling victim to attacks targeting WordPress vulnerabilities.