The increasing sophistication of e-commerce malware has led to serious security threats for platforms such as WordPress WooCommerce. A recent case uncovered a coordinated attack involving a credit card skimmer, a hidden backdoor file manager, and a reconnaissance script, aimed at stealing customer data and maintaining long-term access. Immediate action is required to mitigate the impacts of such threats. Affected: WordPress, WooCommerce, e-commerce platforms
Keypoints :
- Attackers are using sophisticated tactics to target e-commerce platforms.
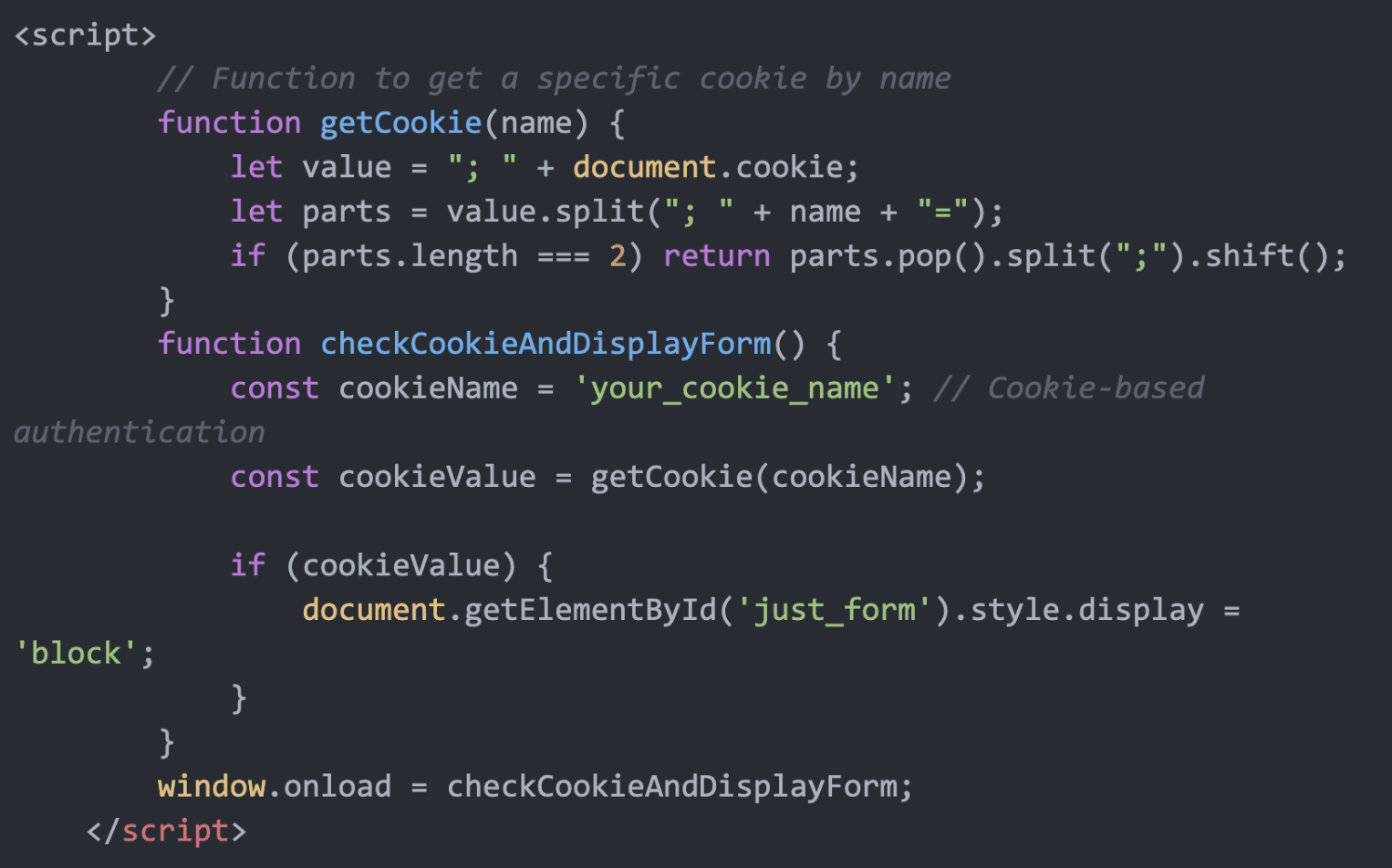
- A customer reported suspicious files and unusual checkout behavior on their WordPress site.
- The malware included a credit card skimmer, a backdoor file manager, and a reconnaissance script.
- The attack was financially motivated, focusing on stealing credit card information.
- Malicious IPs and domains used in the attack have been blocklisted.
- The impact of such malware includes financial loss, reputational damage, and potential PCI violations.
- Preventative measures include regular security audits, malware removal, and implementation of web application firewalls.
MITRE Techniques :
- Web Service (T1102): Used to transmit stolen data to the attacker’s server through a fake image request.
- Remote File Copy (T1105): Leveraged a PHP backdoor to copy files or execute commands remotely on the server.
- Data Obfuscation (T1001): The credit card skimmer code was heavily obfuscated to avoid detection and analysis.
- Credential Dumping (T1003): The hidden file manager could be used to access and manipulate credentials or sensitive files.
Indicator of Compromise :
- [Malicious IP] 104.194.151.47
- [Malicious IP] 185.247.224.241
- [Malicious Domain] imageresizefix[.]com
- [Malicious Domain] imageinthebox[.]com
- [URL] https://imageresizefix[.]com/pixel_info/img-sort.php?validator=ENCODED_DATA
Full Story: https://blog.sucuri.net/2025/03/credit-card-skimmer-and-backdoor-on-wordpress-e-commerce-site.html