This report details a significant security intrusion that began with the execution of a malicious file masquerading as a legitimate Windows utility, leading to the deployment of LockBit ransomware. The threat actor employed various techniques including data exfiltration through Rclone and significant lateral movement within the network using proxies and process injection methods. Affected: Cobalt Strike, LockBit Ransomware, File Servers, Domain Controllers
Keypoints :
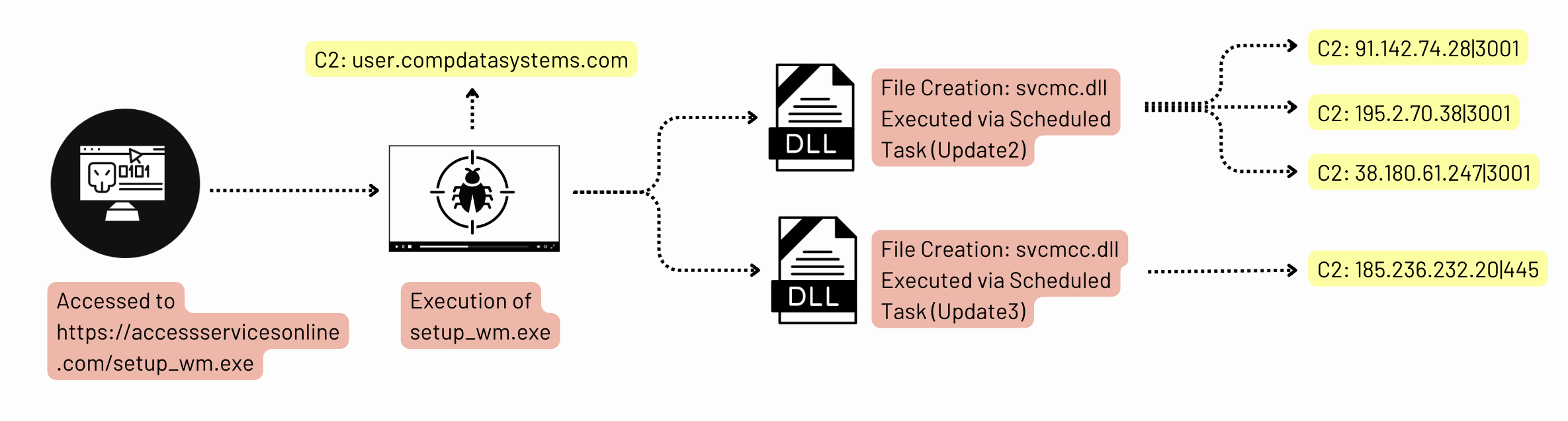
- The intrusion began in January 2024 with a malicious file named setup_wm.exe.
- The initial payload was a Cobalt Strike beacon which established outbound connections.
- Data exfiltration began after several failed attempts, eventually successful via Rclone and MEGA.io.
- LockBit ransomware was deployed on the 11th day of the intrusion after multiple reconnaissance and lateral movement activities.
- The threat actor utilized scheduled tasks, registry run keys, and various proxies to maintain persistence.
MITRE Techniques :
- T1071.001 – Web Protocols: The threat actor communicated using HTTP to various command and control servers.
- T1075 – Remote File Copy: Files were transferred between systems within the compromised network using SMB and WebDAV.
- T1055 – Process Injection: Code was injected into legitimate processes such as WUAUCLT.exe to access restricted resources.
- T1021.001 – Remote Desktop Protocol: RDP sessions were initiated to access file servers and a backup server during the attack.
- T1048 – Exfiltration Over Alternative Protocol: Data was exfiltrated using Rclone over FTP and MEGA.io.
Indicator of Compromise :
- [URL] hxxps://accessservicesonline[.]com/setup_wm.exe
- [Domain] accessservicesonline[.]com
- [IP Address] 31.172.83.162
- [IP Address] 159.100.14.254
- [File] ds.exe
Full Story: https://thedfirreport.com/2025/01/27/cobalt-strike-and-a-pair-of-socks-lead-to-lockbit-ransomware/