Threat Actor: Silk Typhoon | Silk Typhoon Victim: U.S.…


Threat Actor: Silk Typhoon | Silk Typhoon Victim: U.S.…
Date Reported: 2025-01-07 Country: CAN | Canada Victim: Organisation des magasins d’alcool du Nouveau-Brunswick | New Brunswick Liquor Corporation Website: anbl.com Additional Information :
New Brunswick liquor stores have been closed for over two days. A potential cybersecurity threat prompted the organization to shut down its systems on Tuesday.…
Threat Actor: Everest Ransomware Gang | Everest Victim: STIIIZY | STIIIZY
Key Point :
Data breach occurred after hackers compromised STIIIZY’s point-of-sale vendor.…
Threat Actor: Unknown | unknown Victim: Tails Users | Tails Users
Key Point :
Critical vulnerabilities in Tails 6.10 and earlier versions could allow persistent malware installation via Tails Upgrader.…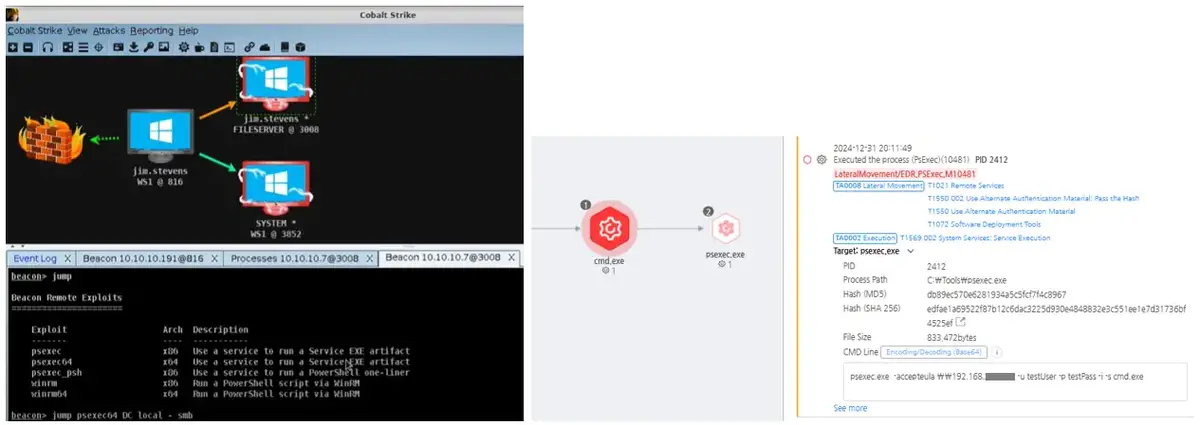
Threat Actor: Andariel Group | Andariel Group Victim: Various Organizations | Various Organizations
Key Point :
Play ransomware encrypts files and follows a double extortion model, stealing data before encryption.…
Threat Actor: Natohub, Silk Typhoon | Natohub, Silk Typhoon Victim: International Civil Aviation Organization, Bank of America, Green Bay Packers | International Civil Aviation Organization, Bank of America, Green Bay Packers
Key Point :
The US Defense Department has linked Tencent and CATL to the Chinese military.…
Threat Actor: FunkSec | FunkSec Victim: Various organizations | various organizations
Key Point :
FunkSec uses double extortion tactics, combining data theft with encryption to pressure victims.…
Threat Actor: Ransomhub | Ransomhub Victim: BayMark Health Services | BayMark Health Services
Key Point :
BayMark operates around 200 addiction treatment facilities across the US, treating over 70,000 patients daily.…
Threat Actor: Malicious OpenVPN peers | malicious OpenVPN peers Victim: OpenVPN users | OpenVPN users
Key Point :
CVE-2024-5594 allows attackers to inject arbitrary data into third-party executables or plugins, with a CVSS score of 9.1.…

Threat Actor: Unknown | unknown Victim: Individuals using PayPal | PayPal
Key Point :
The phishing email appears legitimate, with a valid sender address and genuine-looking URL.…
Key Points :
Medusind is a U.S. medical billing company that provides services to healthcare organizations. The data breach was discovered on December 29, 2023, affecting 360,934 individuals.…
Threat Actor: UNC5221 | UNC5221 Victim: Ivanti | Ivanti
Key Point :
Mandiant identified exploitation of CVE-2025-0282 by Chinese hackers, linked to previous attacks on Ivanti products.…

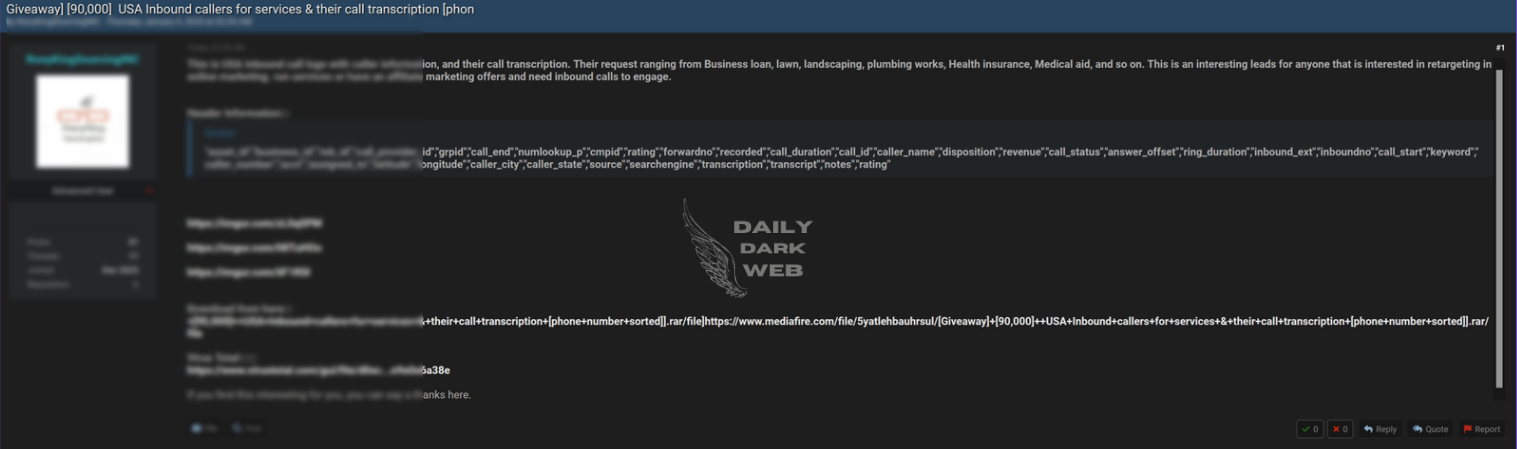
Key Points :
A reported data breach has exposed sensitive information from 90,000 inbound calls. The leaked data includes detailed call transcriptions and associated phone numbers.…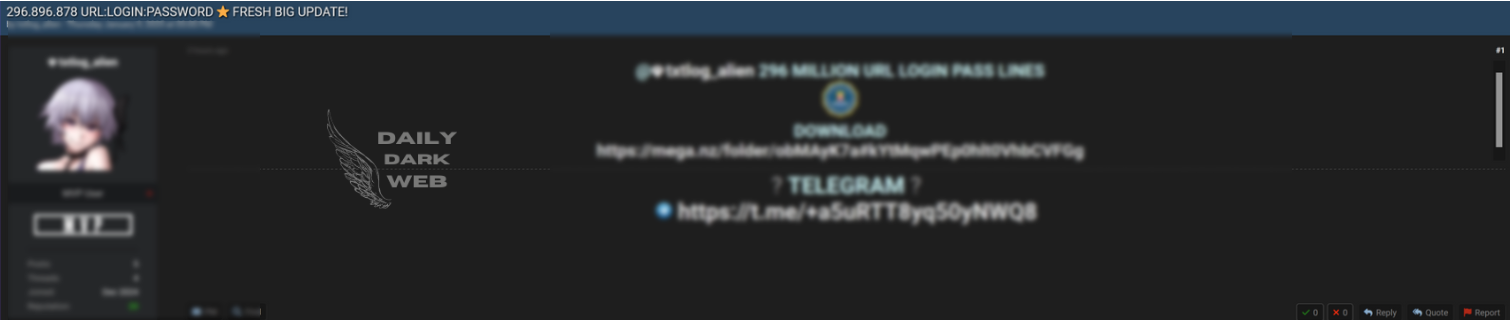
Key Points :
A massive data breach has exposed approximately 296,896,878 URL login credentials and passwords. The leaked database contains sensitive user information, raising significant online security and privacy concerns.…
Key Points :
11GB Mega Logs Pack for December leaked, raising concerns about user data security. Potentially includes login credentials, browsing histories, and other sensitive information.…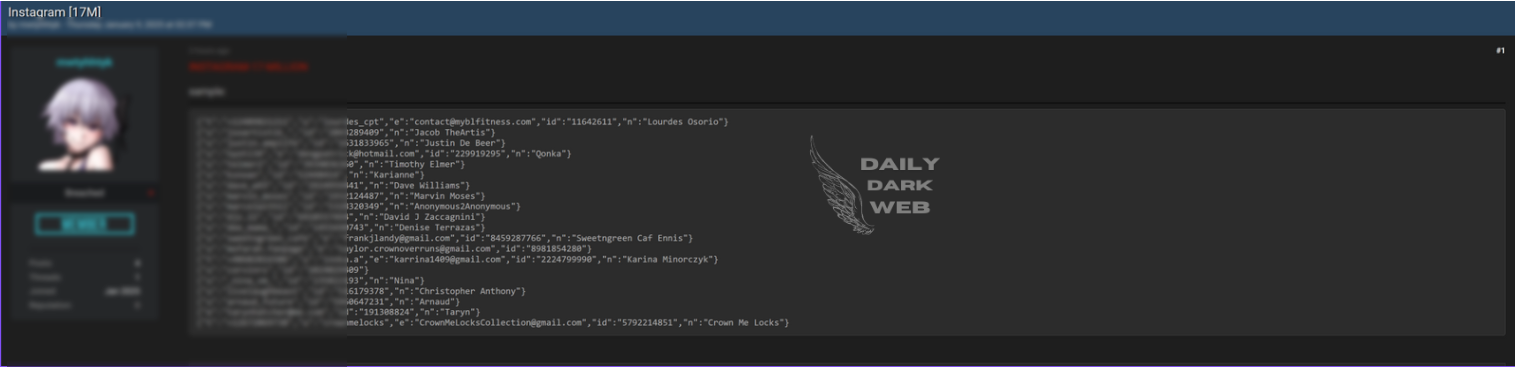
Key Points :
17 million Instagram users’ data exposed in a reported breach. Compromised data includes user IDs, email addresses, and phone numbers.…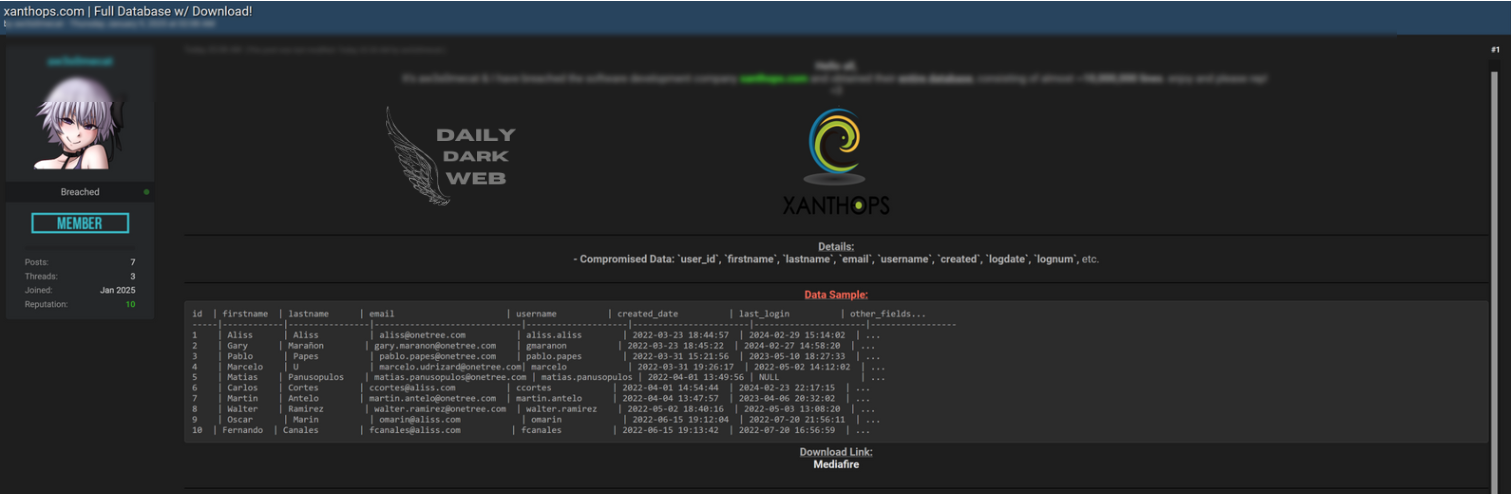
Key Points :
A significant data breach has exposed the full database of Xanthops.com. Compromised information includes sensitive user data such as names, email addresses, and encrypted passwords.…