Executive summary
- Earlier this year Sygnia’s IR team was engaged in a Business Email Compromise (BEC) attack against one of its clients.
- Following a successful phishing attempt, the threat actor gained initial access to one of the victim employees’ accounts and executed an ‘Adversary In The Middle’ attack to bypass Office365 authentication and gain persistent access to that account.
- Once gaining persistence, the threat actor exfiltrated data from the compromised account and used his access to spread phishing attacks to other victim’s employees along with several external targeted organizations.
- Using a variety of CTI enrichment techniques Sygnia was able to determine that this BEC attack was only a part of a much wider campaign, potentially impacting dozens of world-wide organizations.
- Following the conclusions yielded from the utilization of these techniques, Sygnia has composed a CTI enrichment toolkit to help security professionals analyze suspicious and malicious IOCs they encounter during their daily monitoring and detection procedures.

High level description of attack-chain
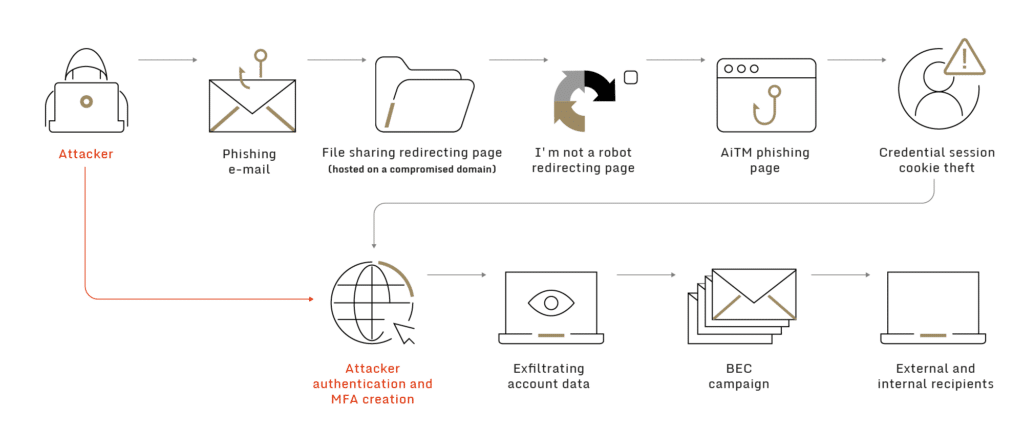
- A phishing email was sent to one of the client’s employees, originating from a legitimate mailbox of an external company, assumed to be previously compromised.
- The phishing email included a link leading to a file sharing request page, hosted on an assumed to be compromised domain, with a URL path associated with the email sender’s company.
- Upon clicking the link, the victim was referred to an ‘I’m not a robot’ check hosted by Cloudflare, which acts as an anti-tracing method.
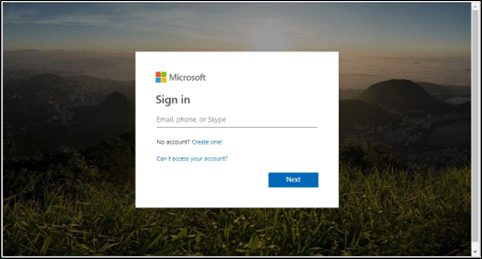
- After passing the check, the victim was referred to a fraudulent Office365 authentication page, generated by a phishing kit.
- After the victim entered his credentials, the phishing kit initiated an ‘Adversary in The Middle’ (AiTM) attack, forwarding the client authentication and MFA challenge to a legitimate Microsoft authentication service while stealing the acquired session token as well as the credentials to enable access to the account.
- The threat actor then logged into the victim’s account using the stolen token and added a new MFA device to gain persistent access.
- Once persistent access was achieved, the threat actor created a new file sharing request site related to the new victim’s company and compromised account.
- In addition to exfiltration of sensitive data from the compromised account, the threat actor used this access to send new phishing emails containing the new malicious link to dozens of the client’s employees as well as to additional targeted organizations.
Analyzing findings using enrichment techniques
1. Phishing mail delivery
Based on Sygnia’s findings from the investigation, the phishing mails spread in a worm-like fashion from one targeted company to others and within each targeted company’s employees. All analyzed emails contain the same structure, only differing in their title, senders’ account and company, and attached link.
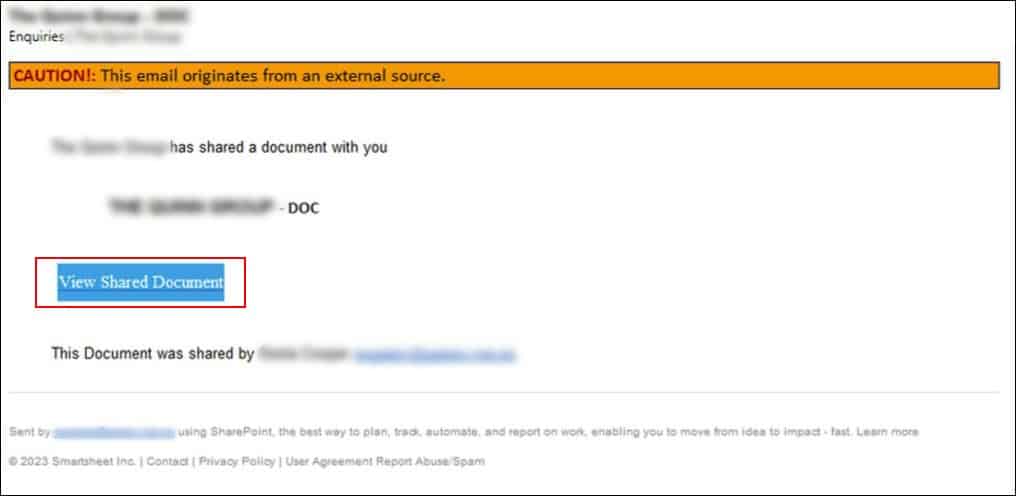
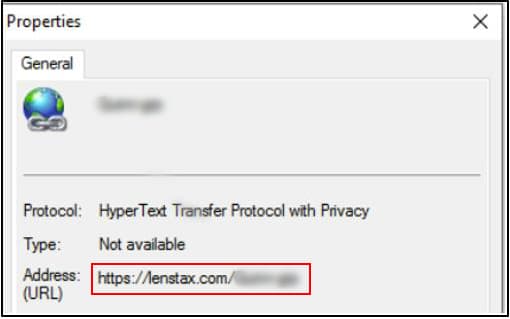
2. Phishing landing page
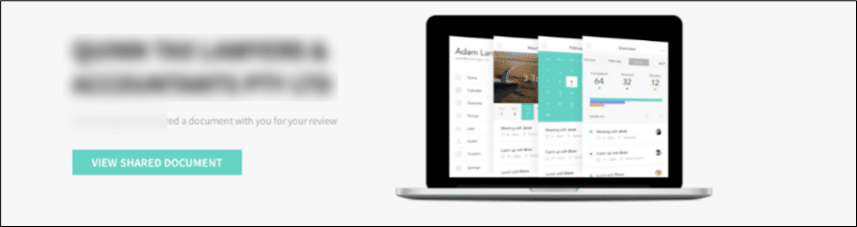
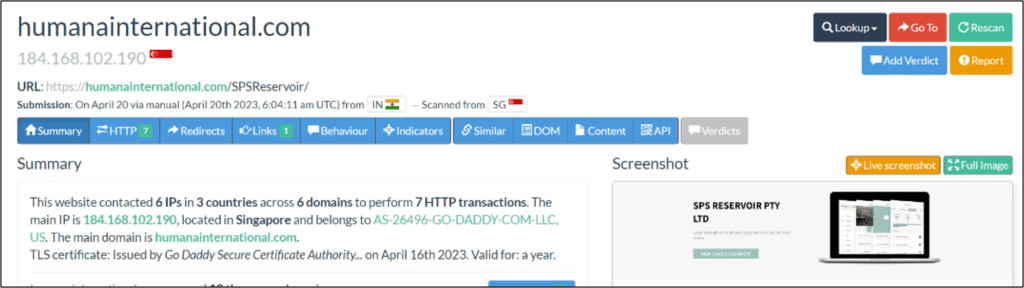
Using the urlscan.io service we were able to see that the URL linked in the mail looks like a file-sharing site, showcasing a document share request which originated from the impersonated sender.

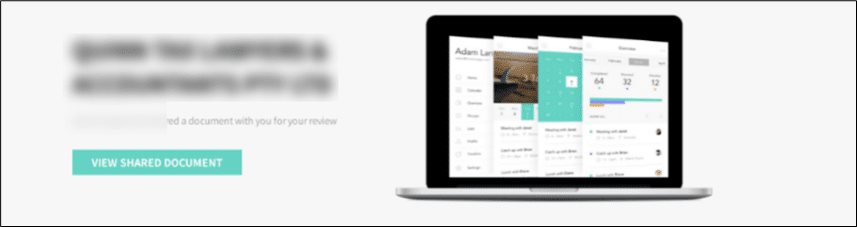
The URL consists of a domain name (lenstax[.]com), followed by a compromised company name.
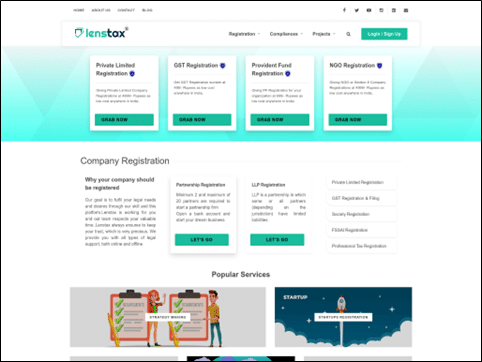
By querying urlscan.io again, this time only for the abovementioned domain, it appears to be a legitimate site – assumed to be compromised by the threat actor:
3. Anti-forensics URL redirection
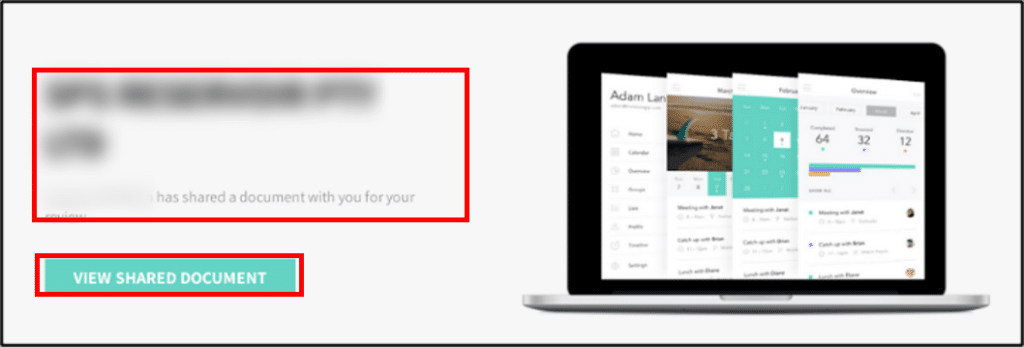
Clicking the ‘VIEW SHARED DOCUMENT’ link refers the victim to a Cloudflare link, which holds an “I’m not a robot” checkbox (id840902[.]com). This method was consistent on every observed branch of the campaign and assumed to serve as an anti-forensic method which prevents tools such as urlscan.io, VirusTotal and other similar engines from scraping the site and revealing where it refers to.
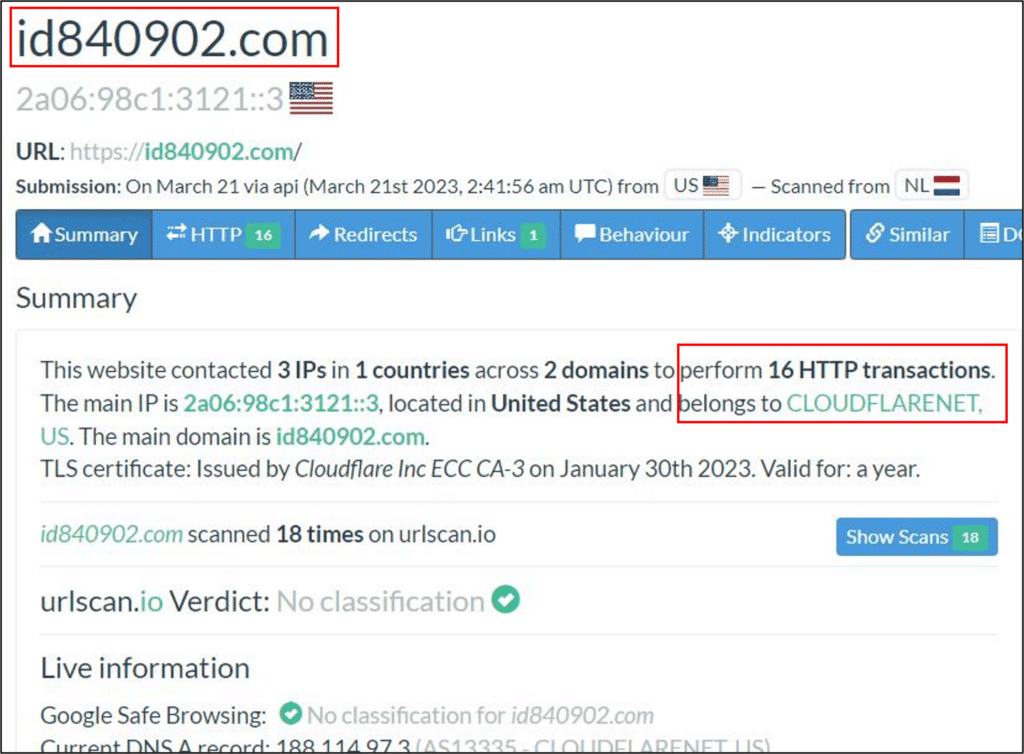
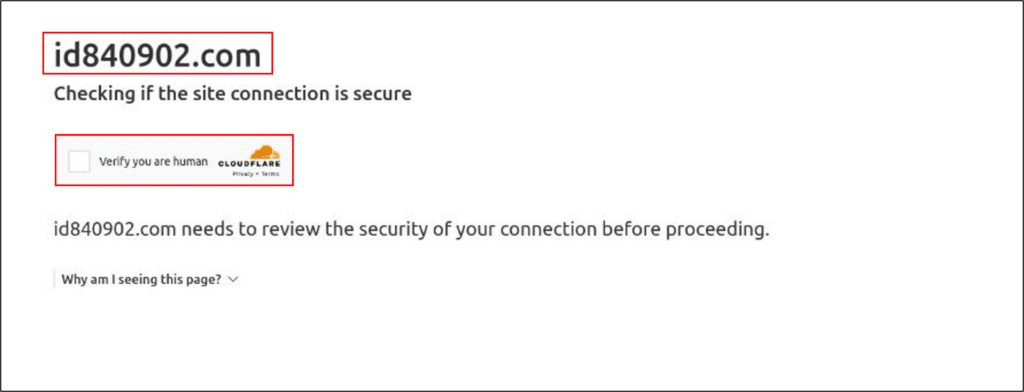
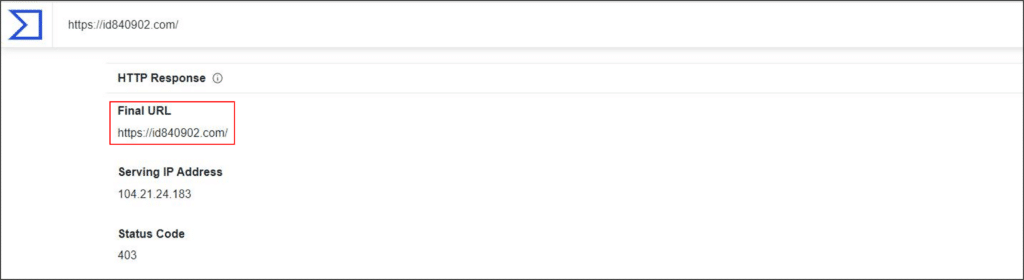
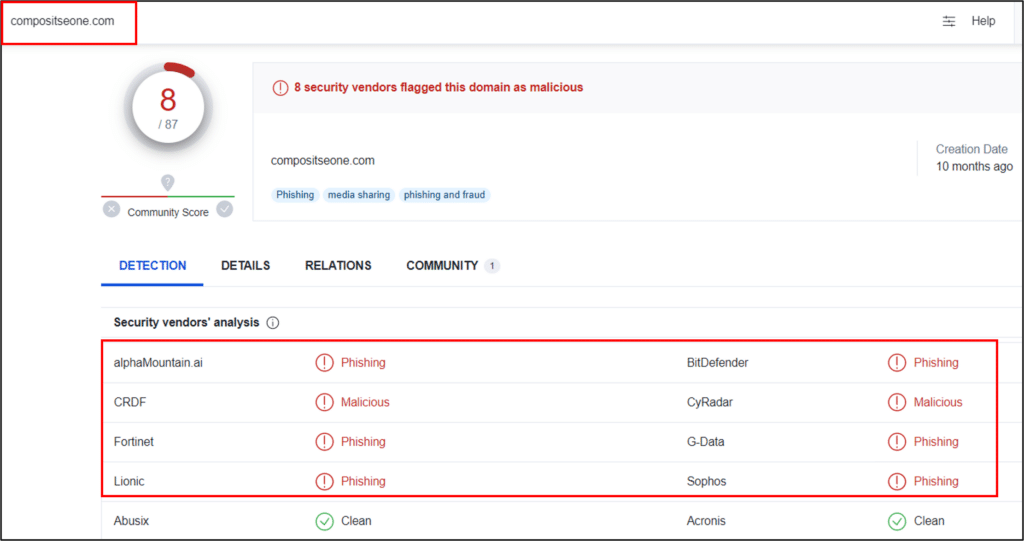
4. Fraudulent authentication site
By analyzing browser history and firewall logs from victim’s network, the full chain was discovered, revealing the final URL of the Cloudflare link refers to is a fraudulent Microsoft authentication site generated by a phishing kit hosted on domain compositseone[.]com.
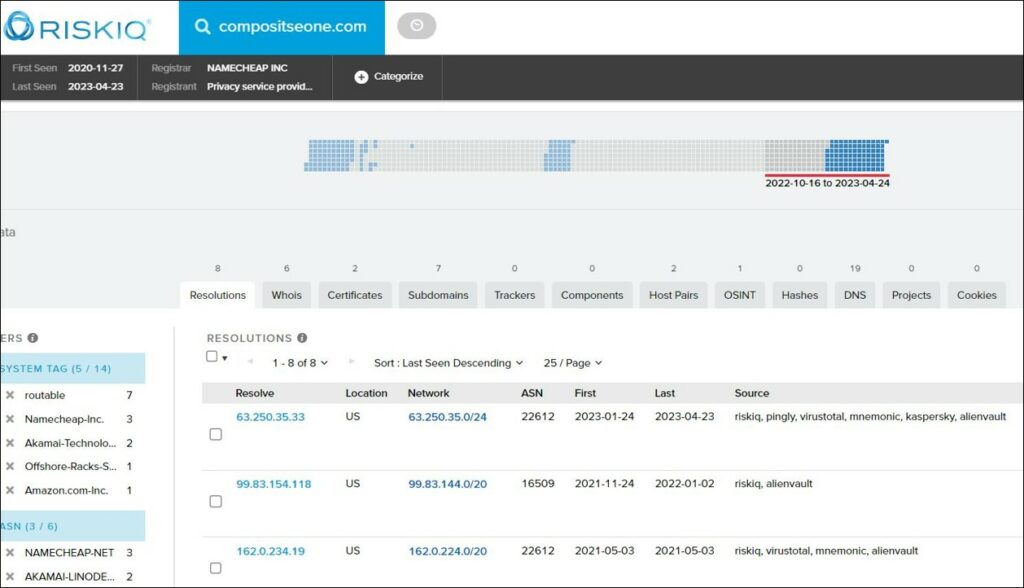
Using RiskIQ yielded some interesting information about this domain:
- Recent and previous IPs it resolved to – including specific time periods per IP:
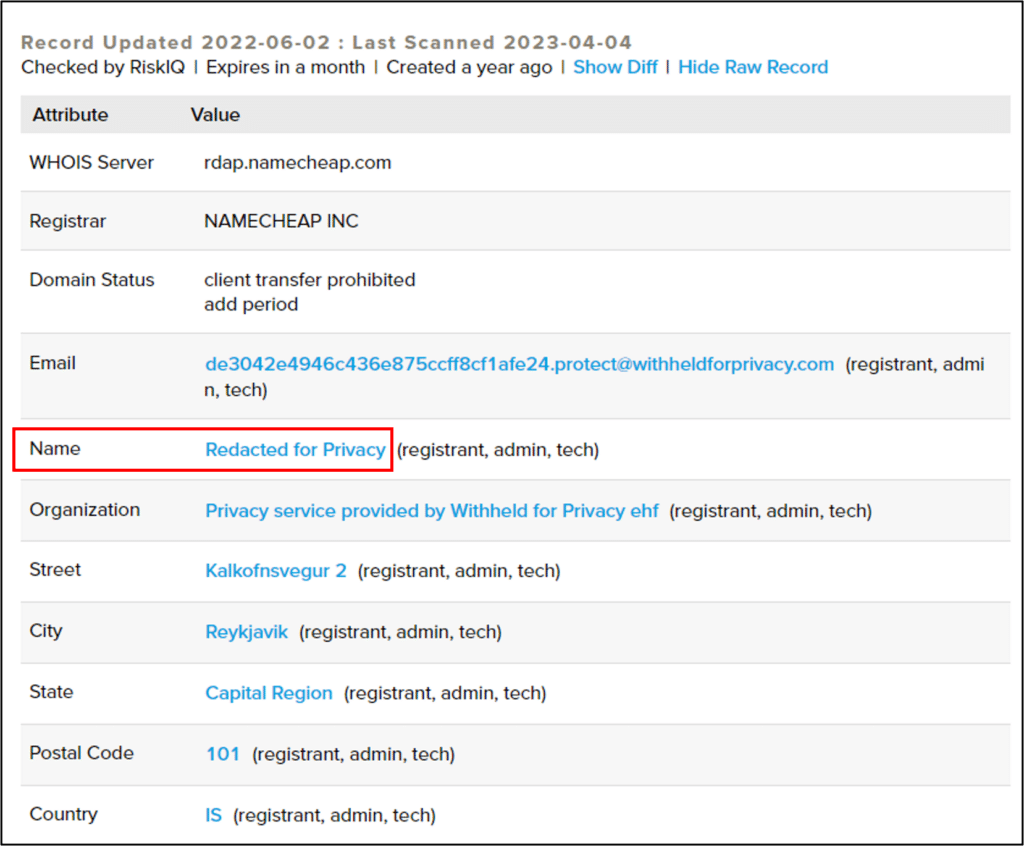
- Current WHOIS record shows it was updated on June 2nd, 2022 and registered under NAMECHEAP INC with privacy restrictions (might be additional indication of suspicious use in some cases):
Querying the domain using VirusTotal shows it is related to phishing activities:
5. ‘Adversary in The Middle’ attack
Once the victim entered his credentials, an ‘AiTM’ attack was initiated automatically by the phishing kit. After forwarding authentication data the session token was stolen and used for successful login to victim’s Azure environment.
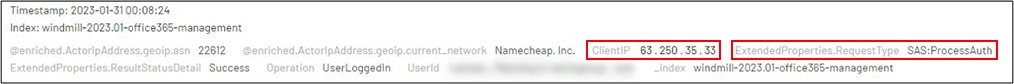
6.MFA modification
In order to gain persistent access to the compromised account, the threat actor used his temporary access to register a new MFA device, this time connecting from different IP addresses – 179.61.228[.].187
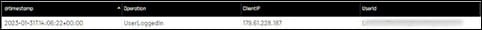
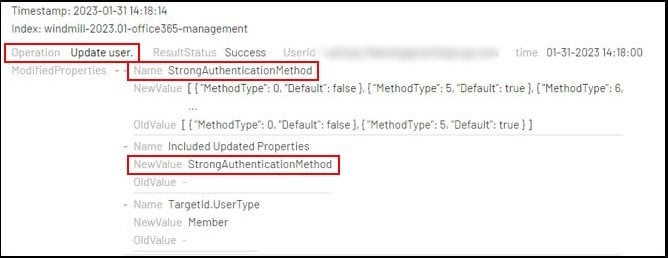
Using the Spur.us service revealed that the IP 179.61.228[.].187, which was used for login, is located in Australia and belongs to PIA VPN:
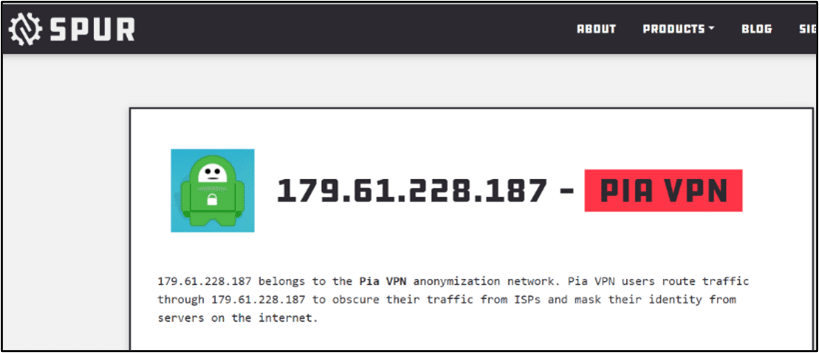

It is assumed that the threat actor used a VPN service to hide the real IP he operates from as well as to avoid network restrictions allowing only specific IP ranges to connect to cloud services.
Mapping additional IPs of this specific ASN enabled the researchers to detect other connections made by the threat actor to the client’s environment from other PIA VPN’s IPs.
7. New phishing site creation
After gaining persistent access to a compromised account, the threat actor set up a new phishing landing page aligned to current victim’s company and hosted on a different domain – patrickaweller[.]com.
As can be seen based on urlscan.io query – the landing page looks identical to the original file-sharing page, only with a different path and company name displayed.
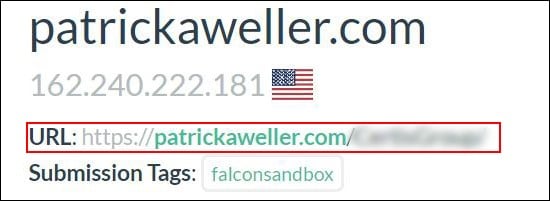
Querying urlscan.io again, this time for the new domain, suggests it might also be a legitimate site compromised by the threat actor (however it is uncertain):

8. New phishing wave from newly acquired victim
A new phishing attack wave was initiated by the threat actor, sending emails from the compromised account to hundreds of external mailboxes as well as dozens of internal employees’ accounts.
This time, the mail sender impersonated with the new company name and compromised account and attached a newly created link.
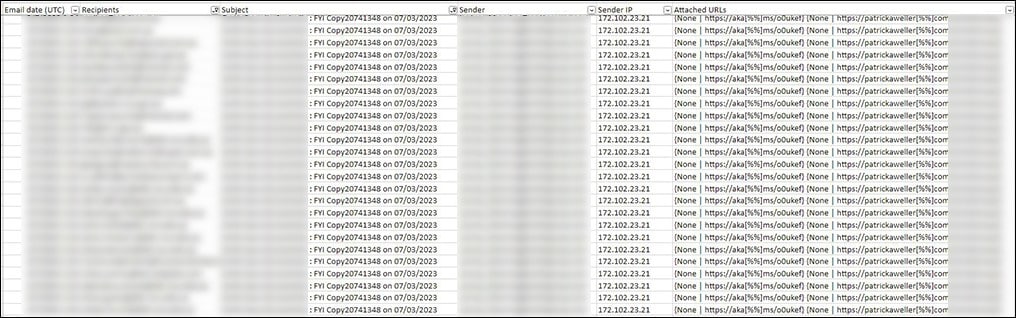
Pivoting using TI toolkit
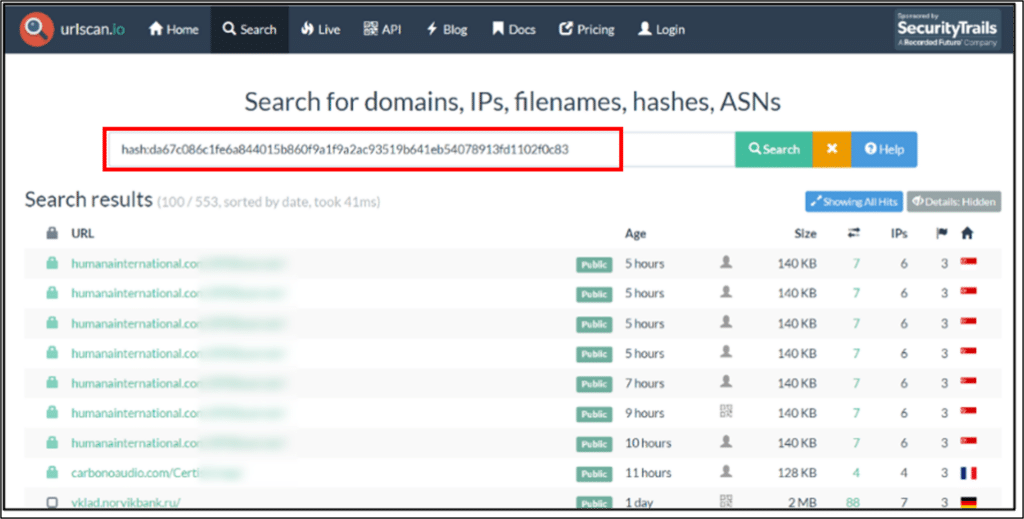
Pivoting on image hash using urlscan.io
After observing both phishing pages links – the one sent to the victim and the one sent from the victim – a clear similarity was discovered as both contain similar structure, font, color scheme, and image:
Pivoting on the mutual image hash with urlscan.io yielded more than 500 unique URLs fitting the exact same structure:
It is assumed that at least some of the domains hosting these URLs were compromised based on sampled analysis. In addition, it is assumed that ‘//’ indicates organizations targeted by this campaign starting a year ago, and some seem to be still active.
By observing each URL and its screenshot, the targeted organization and specific account from which phishing mails were sent can be extracted – for example:
After extraction of all unique domains from the abovementioned URLs list, additional queries on their relations using VirusTotal discovered a massive list of URLs from which additional targeted organizations can be extracted, e.g:
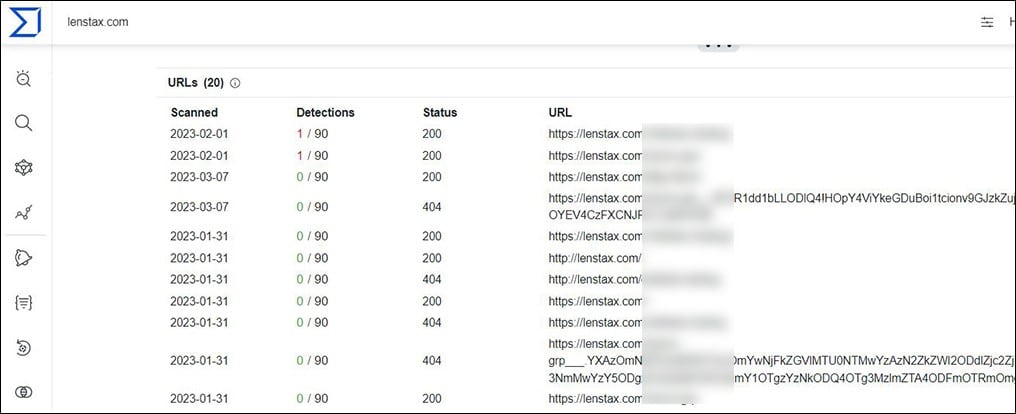
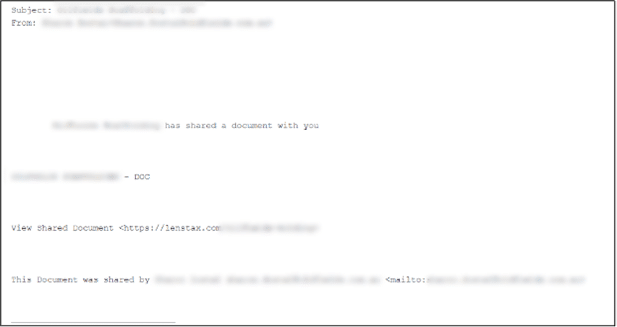
In some cases, this VirusTotal query also discovered additional similar phishing mails related to these domains that are also part of this campaign – for example:
Pivoting on malicious IP 63.250.35[.]33
Querying the malicious IP using RiskIQ brought up several findings:
- It belongs to Namecheap Inc.
- It resolved over time to more than 170 domains and sub-domains, most of them starting in the past six months:
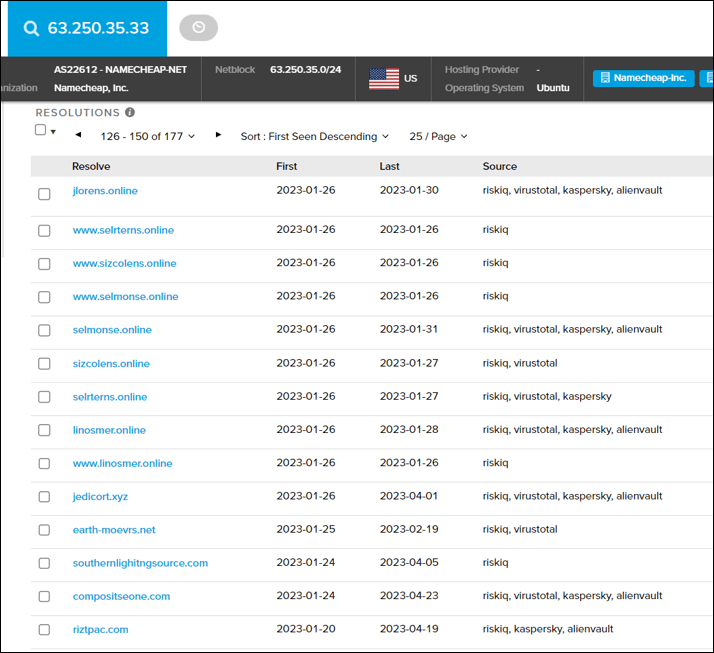
It is assumed all recently resolved domains are part of the threat actor’s infrastructure and used in other branches of this campaign or in other campaigns.
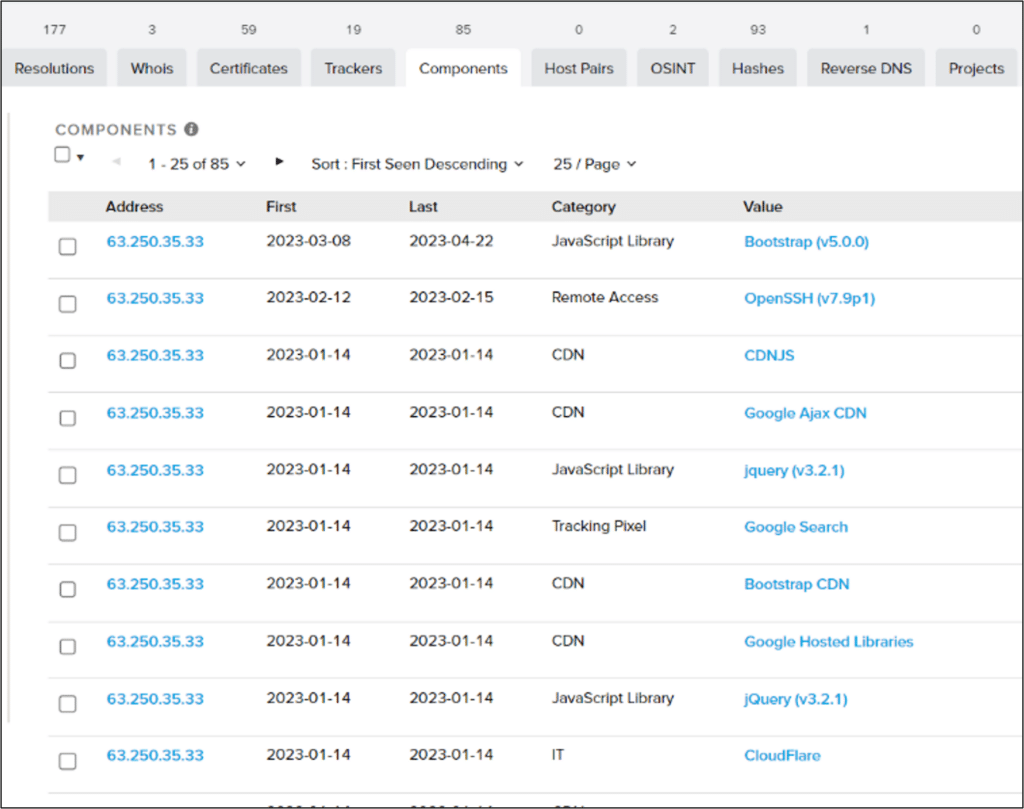
- Several components were installed on the server – most around mid-January:
Querying on IP’s relations using VirusTotal discovered nearly 100 malicious files with recent uploads communicating with it:
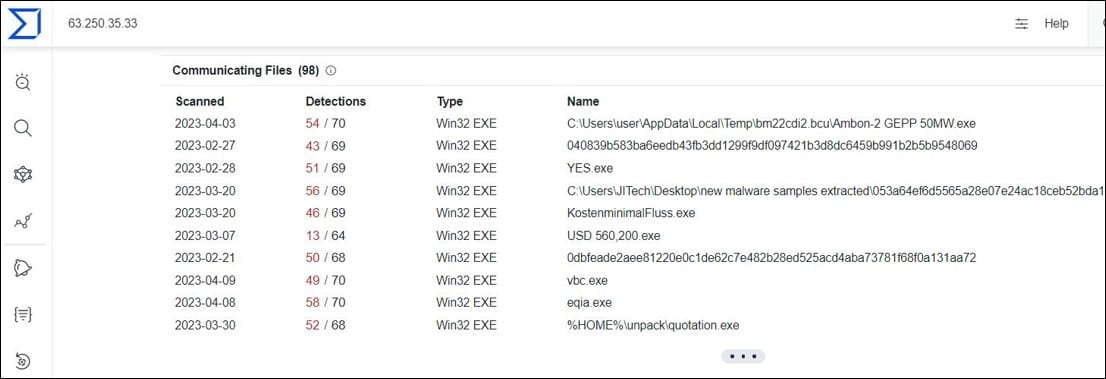
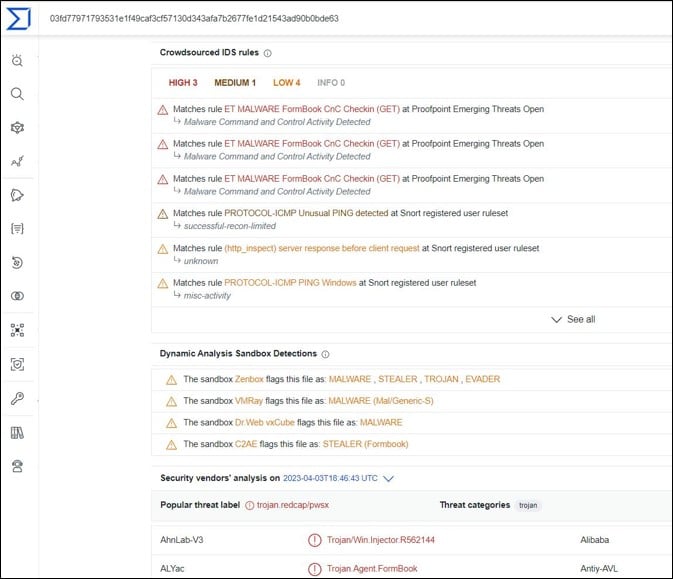
This might be another indication of its malicious use as well as indication it might be used for additional malicious purposes by the threat actor. Some of these files were found to be related to FormBook malware family:
Pivoting on malicious domain id-82882[.]com
Using RiskIQ to query this domain reveals it was created on mid-January 23 and that its registrant is Stew Jeanne:

In addition, it was resolved to several Cloudflare IPs since its creation:
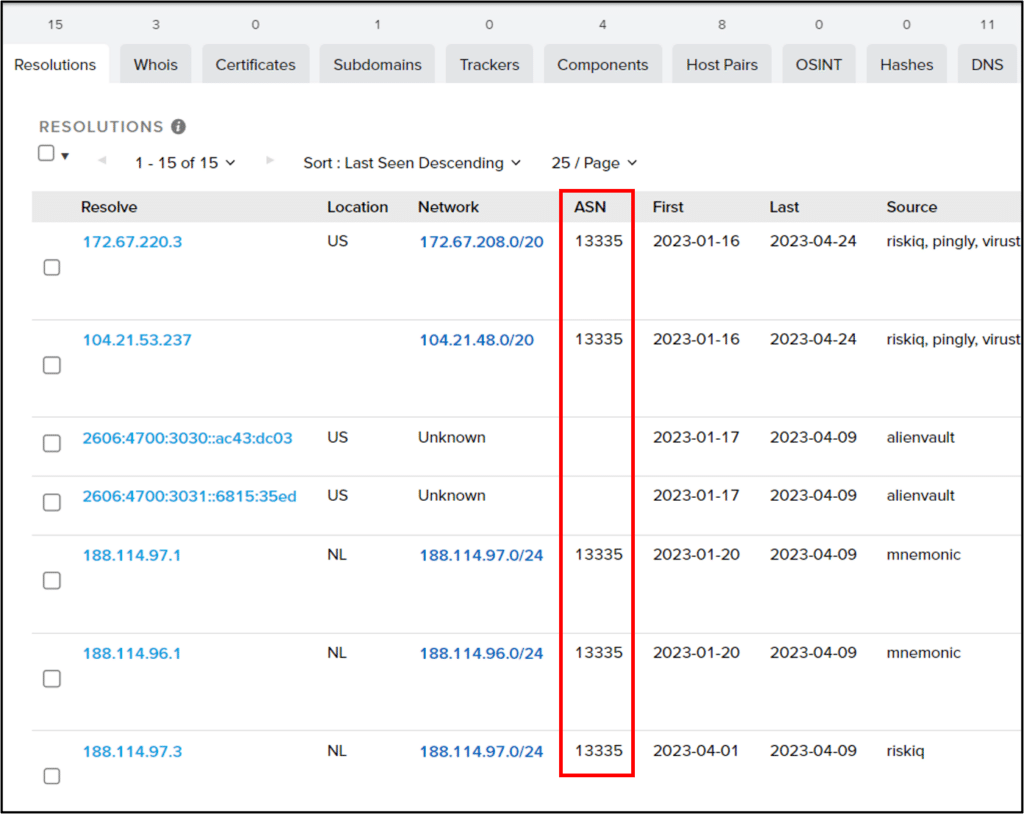
By pivoting on unique fields from domain’s current WHOIS record some additional domains were discovered – assumed to be related to this campaign or other campaigns operated by the same threat actor:
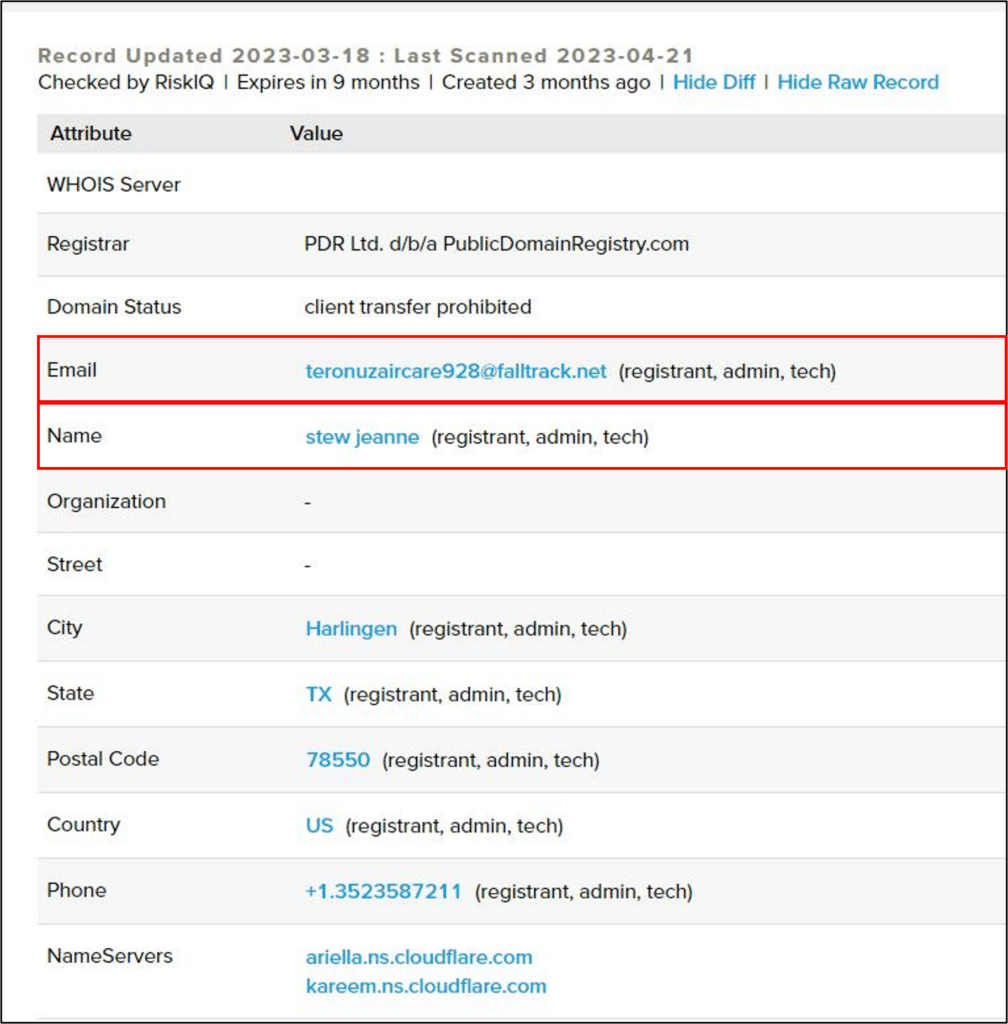
More than 30 domains were registered with registrant name Stew Jeanne (all since February 23):
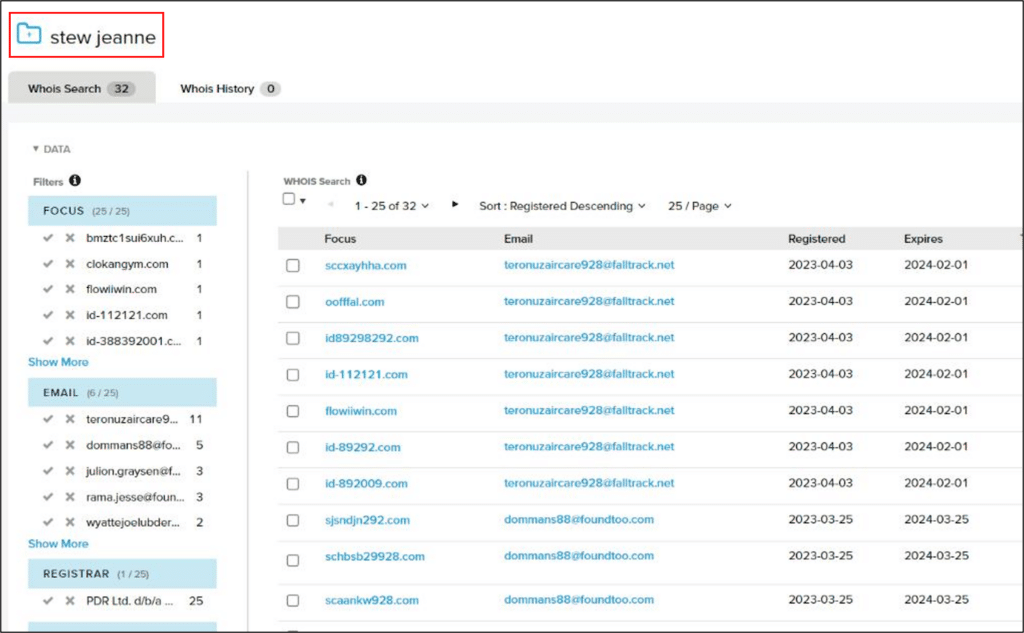
More than 10 domains were registered with the e-mail teronuzaircare928@falltrack.net:
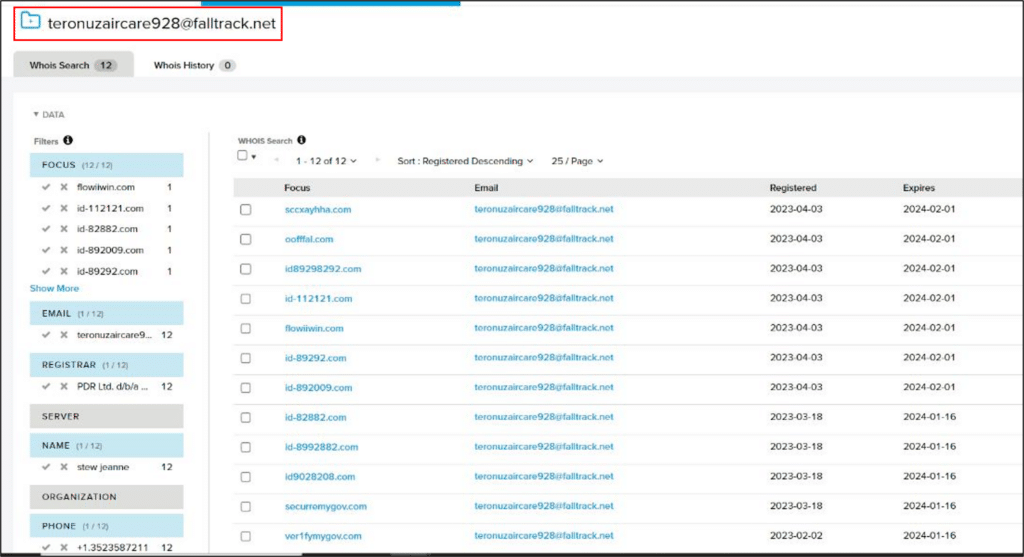
Conclusion
According to the FBI’s 2022 Congressional Report on BEC and Real Estate Wire Fraud, BEC is “one of the fastest growing, most financially damaging internet-enabled crimes”. In the past few years, Sygnia’s IR teams have engaged in numerous incidents in which world-wide organizations were targeted by BEC attacks. While some of these attacks were focal and concentrated, some were widely spread and affected massive number of cross-sectors victims. In the case described in this blog post, Sygnia demonstrates how it was able to crack and reveal a massive and high impact BEC campaign by using a set of enrichment techniques. The entire enrichment toolset, which is relevant to all types of attacks, is hereby shared by Sygnia to help security professionals analyze suspicious and malicious IOCs they encounter during their daily monitoring and detection procedures.
If you were impacted by this attack or are seeking guidance on how to prevent similar attacks, please contact us at contact@sygnia.co or our 24-hour hotline +1-877-686-8680.
This advisory and any information or recommendation contained herein has been prepared for general informational purposes and is not intended to be used as a substitute for professional consultation on facts and circumstances specific to any entity. While we have made attempts to ensure the information contained herein has been obtained from reliable sources and to perform rigorous analysis, this advisory is based on initial rapid study, and needs to be treated accordingly. Sygnia is not responsible for any errors or omissions, or for the results obtained from the use of this Advisory. This Advisory is provided on an as-is basis, and without warranties of any kind.
Source: https://blog.sygnia.co/cracking-global-phishing-campaign-using-threat-intelligence-toolkit
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português