Summary: This content discusses the CarnavalHeist banking Trojan, which targets users in Brazil and is capable of stealing banking credentials and performing other malicious actions.
Threat Actor: CarnavalHeist | CarnavalHeist
Victim: Users in Brazil | Users in Brazil
Key Point :
- CarnavalHeist is a banking Trojan that targets users in Brazil and can result in financial loss, identity theft, and other issues.
- The malware uses overlay attacks to trick users into disclosing personal information and has various data capture capabilities.
- CarnavalHeist utilizes a modified protocol from a Delphi Remote Access Client.
What kind of malware is CarnavalHeist?
CarnavalHeist is a banking Trojan targeting users in Brasil. It is capable of stealing banking credentials and performing other actions. Having a device infected with CarnavalHeist can result in financial loss, identity theft, and other issues. Thus, CarnavalHeist should be eliminated from compromised devices as soon as possible.
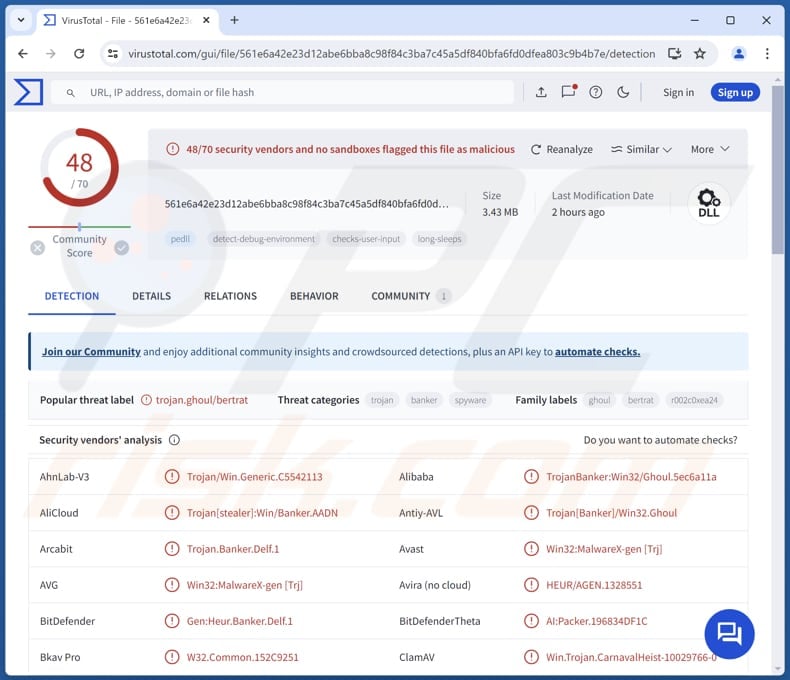
More about CarnavalHeist
CarnavalHeist can steal banking credentials through overlay attacks. It can display a fake window over legitimate banking applications to trick users into disclosing personal information (e.g., IDs, usernames, and passwords). It monitors specific window titles and, upon discovering a match, hides the original window and displays a corresponding overlay.
CarnavalHeist includes various data capture capabilities, which can be triggered automatically or via commands received through its command and control server. It uses a modified protocol from a Delphi Remote Access Client, similar to those used by Mekotio and Casbaneiro malware. This protocol allows the attackers to execute about 80 commands.
These commands include logging keystrokes, taking screenshots, capturing videos, and controlling the device remotely. CarnavalHeist also has the ability to perform remote control via AnyDesk, allowing the attackers to perform certain actions using the victim’s device during banking sessions.
Moreover, the malware can generate and capture QR codes to redirect transactions to accounts controlled by threat actors. Additionally, CarnavalHeist logs mouse and keyboard inputs, revealing PINs and other sensitive details when victims make transactions using legitimate services.
Overall, users with devices infected by CarnavalHeist may experience theft of their banking credentials, leading to unauthorized access to their financial accounts. Attackers can intercept and redirect transactions, potentially resulting in financial losses. Additionally, the malware’s ability to capture keyboard and mouse inputs can expose sensitive information like PINs and other security tokens.
| Name | CarnavalHeist Banking Trojan |
| Threat Type | Banking Trojan |
| Detection Names | Avast (Win32:MalwareX-gen [Trj]), Combo Cleaner (Gen:Heur.Banker.Delf.1), ESET-NOD32 (A Variant Of Win32/Spy.Banker.AEPR), Kaspersky (HEUR:Trojan-Banker.Win32.BertRAT.gen), Microsoft (Trojan:Win32/Banker!MSR), Full List (VirusTotal) |
| Symptoms | Banking trojans tend to be designed to stealthily infiltrate the victim’s computer and remain silent, and thus no particular symptoms are clearly visible on an infected device. |
| Distribution methods | Infected email attachments, malicious websites, social engineering. |
| Damage | Stolen passwords and banking information, identity theft, financial loss. |
| Malware Removal (Windows) | To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. |
Conclusion
In conclusion, CarnavalHeist poses serious threats to victims. Its ability to generate fake login screens, coupled with comprehensive data capture and remote control functionalities, allows threat actors to steal login credentials (and other sensitive information) and manipulate transactions (steal money).
To avoid this threat, users must exercise be careful when using online banking platforms and prioritize cybersecurity measures to protect their financial well-being.
How did CarnavalHeist infiltrate my computer?
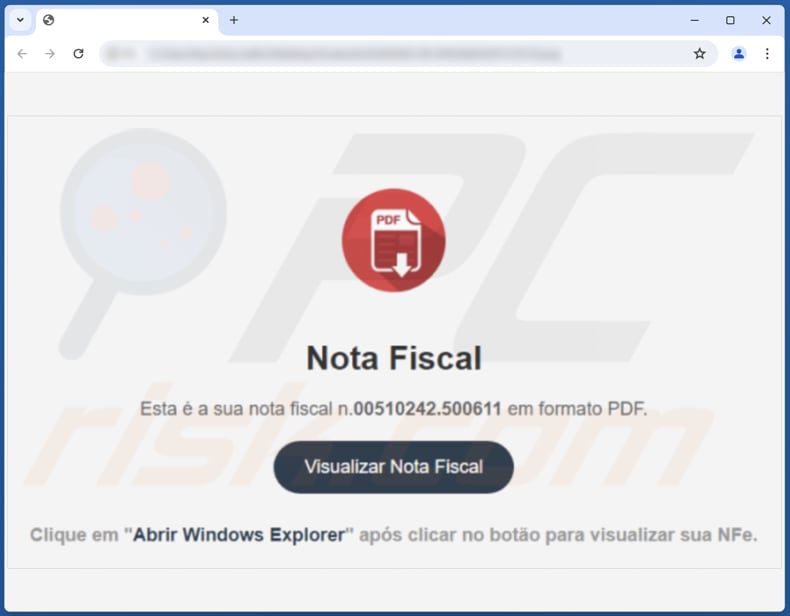
CarnavalHeist employs a sophisticated social engineering attack disguised as a financial document to compromise user credentials and potentially steal sensitive financial information. The attack starts with a fake invoice email. Clicking the link leads to a webpage mimicking an invoice download platform.
On this fake website, a malicious file disguised as a PDF is downloaded, which secretly launches the next stage of the attack (this fake runs a command designed to execute a malicious component), leading to the infiltration of CarnavalHeist.
How to avoid installation of malware?
Use official websites and app stores to download software or files. Do not use third-party sources or download pirated software, cracking tools, or unofficial key generators. Be careful with emails containing links or files and pop-ups, ads, and buttons on questionable web pages. Also, do not allow suspicious sites to show notifications.
During installations, deselect unwanted apps (if there are any unwanted offers in installers). Regularly update the operating system and installed software. Additionally, utilize a reputable security tool (or tools). If you believe that your computer is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Malicious attachment containing a link to a fake web page hosting CarnavalHeist (source: Talos Intelligence):
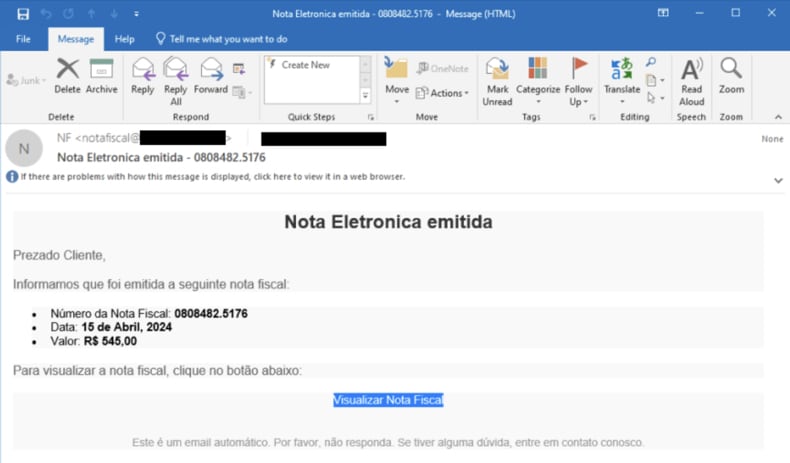
Text in the scam email:
Subject: Nota Eletronica emitidat – 0808482.5176
Nota Eletronica emitida
Prezado Cliente,
Informamos que foi emitida a seguinte nota fiscal:
Número da Nota Fiscal: 08084282.5176
Data: 15 de Abril, 2024
Valor: R$ 545,00Para visualizar a nota fiscal, clique no botão abaixo:
Visualizar Nota Fiscal
Deceptive website promoted via a fraudulent email (source: Talos Intelligence):
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Quick menu:
How to remove malware manually?
Manual malware removal is a complicated task – usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user’s computer:
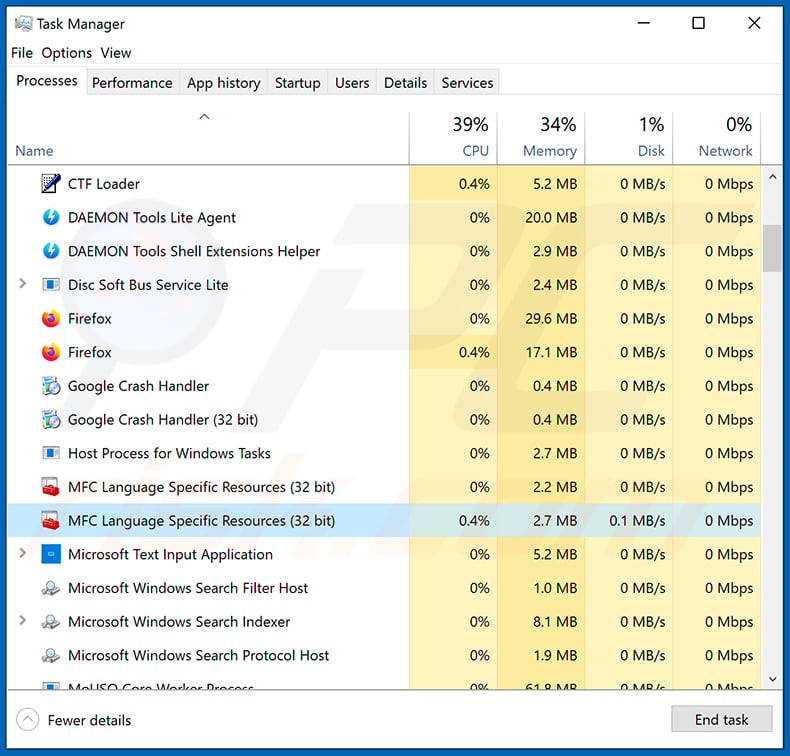
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
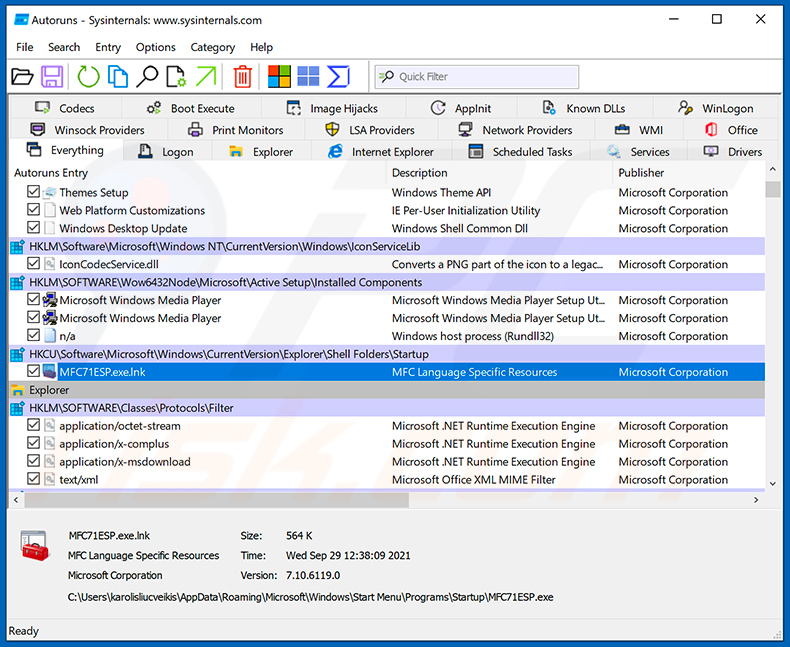
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in “Safe Mode with Networking”:
[embedded content]
Windows 8 users: Start Windows 8 is Safe Mode with Networking – Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened “General PC Settings” window, select Advanced startup.
Click the “Restart now” button. Your computer will now restart into the “Advanced Startup options menu”. Click the “Troubleshoot” button, and then click the “Advanced options” button. In the advanced option screen, click “Startup settings”.
Click the “Restart” button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in “Safe Mode with Networking”:
[embedded content]
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click “Restart” while holding “Shift” button on your keyboard. In the “choose an option” window click on the “Troubleshoot”, next select “Advanced options”.
In the advanced options menu select “Startup Settings” and click on the “Restart” button. In the following window you should click the “F5” button on your keyboard. This will restart your operating system in safe mode with networking.
Video showing how to start Windows 10 in “Safe Mode with Networking”:
[embedded content]
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
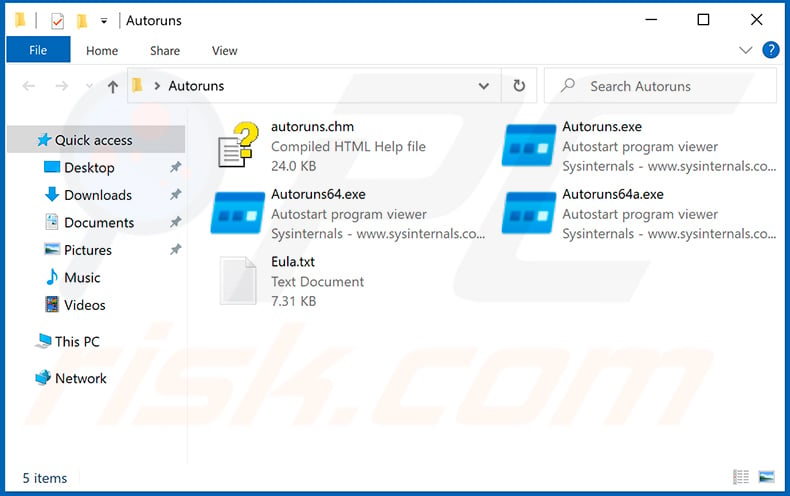
 In the Autoruns application, click “Options” at the top and uncheck “Hide Empty Locations” and “Hide Windows Entries” options. After this procedure, click the “Refresh” icon.
In the Autoruns application, click “Options” at the top and uncheck “Hide Empty Locations” and “Hide Windows Entries” options. After this procedure, click the “Refresh” icon.
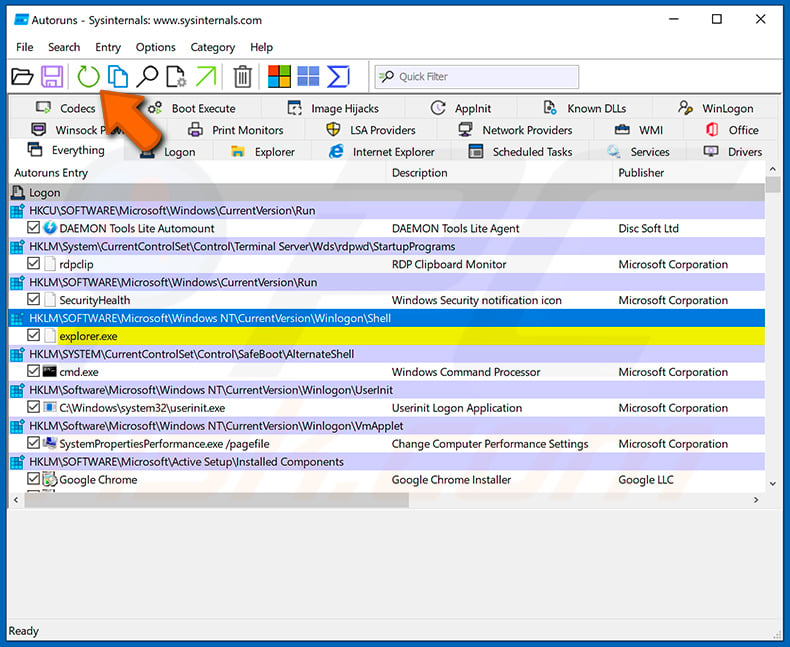
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose “Delete”.
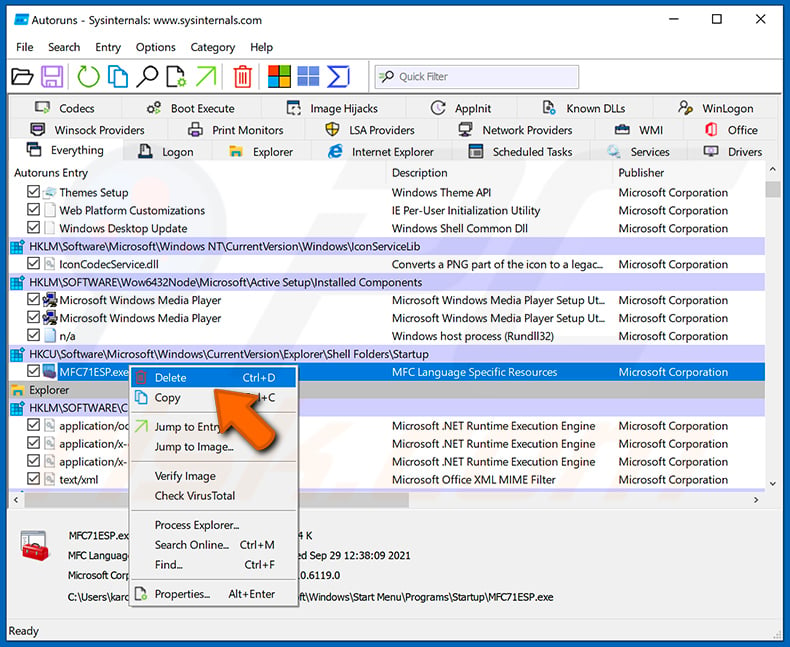
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
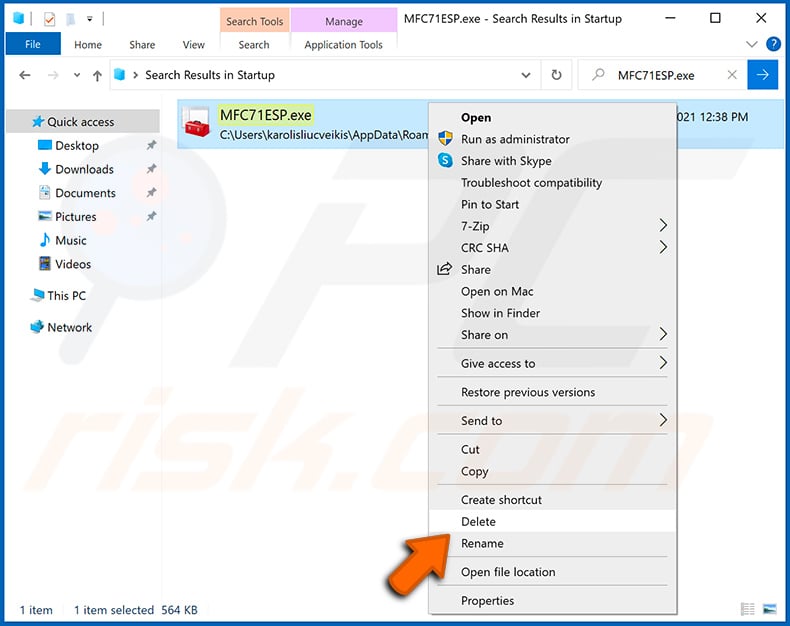
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with CarnavalHeist malware, should I format my storage device to get rid of it?
It is recommended to use a reputable antivirus and anti-malware program to scan your device for CarnavalHeist and attempt removal. Formatting a storage device will remove all data, so it should be done when other methods fail.
What are the biggest issues that malware can cause?
Malware can cause data loss through encryption and other ways, financial loss, identity theft, loss of access to online accounts, additional infections, and similar issues.
What is the purpose of CarnavalHeist malware?
CarnavalHeist targets bank users with the goal of stealing their financial information. It tricks them into revealing login details and captures other sensitive data.
How did CarnavalHeist malware infiltrate my computer?
You likely clicked a malicious link in a fraudulent email. This action downloaded a fake PDF file that launched CarnavalHeist. Phishing emails are CarnavalHeist’s usual entry point.
Will Combo Cleaner protect me from malware?
Combo Cleaner is effective in detecting and removing a wide range of malware. Even with advanced malware, a thorough system scan with Combo Cleaner can result in a successful removal.
Source: https://www.pcrisk.com/removal-guides/30138-carnavalheist-malware
“An interesting youtube video that may be related to the article above”
Views: 0