Summary: Cable is an open-source post-exploitation tool designed for the enumeration and exploitation of Active Directory (AD) environments, aiding security professionals in assessing vulnerabilities and performing privilege escalation. It offers various features, including Kerberoasting, DACL manipulation, and RBCD exploitation, to enhance understanding and security of AD systems.
Threat Actor: Cable | Cable
Victim: Active Directory environments | Active Directory environments
Key Point :
- Cable facilitates Kerberoasting by retrieving service tickets from AD accounts with SPNs, allowing for offline cracking of service account credentials.
- It enables RBCD exploitation by manipulating the msDs-AllowedToActOnBehalfOfOtherIdentity attribute, allowing lateral movement within AD.
- Cable provides capabilities for DACL manipulation, aiding in the management of access permissions on AD objects.
- Users can enumerate AD Certificate Services (ADCS) to identify potential vulnerabilities in certificate configurations.
- The tool supports comprehensive enumeration of domain and forest trusts, assisting in the identification of inter-domain vulnerabilities.
- Cable allows for flexible LDAP enumeration, enabling customized data gathering from AD.
- It includes password management features and control over SPN attributes for testing and privilege escalation.
- Cable can set or remove the DONT_REQ_PREAUTH flag for AS-REP Roasting, targeting accounts that do not require pre-authentication.
- It simplifies group and user membership enumeration, aiding in the identification of users with elevated privileges.
- Cable allows for the creation and deletion of computer objects within AD, providing additional avenues for privilege escalation.
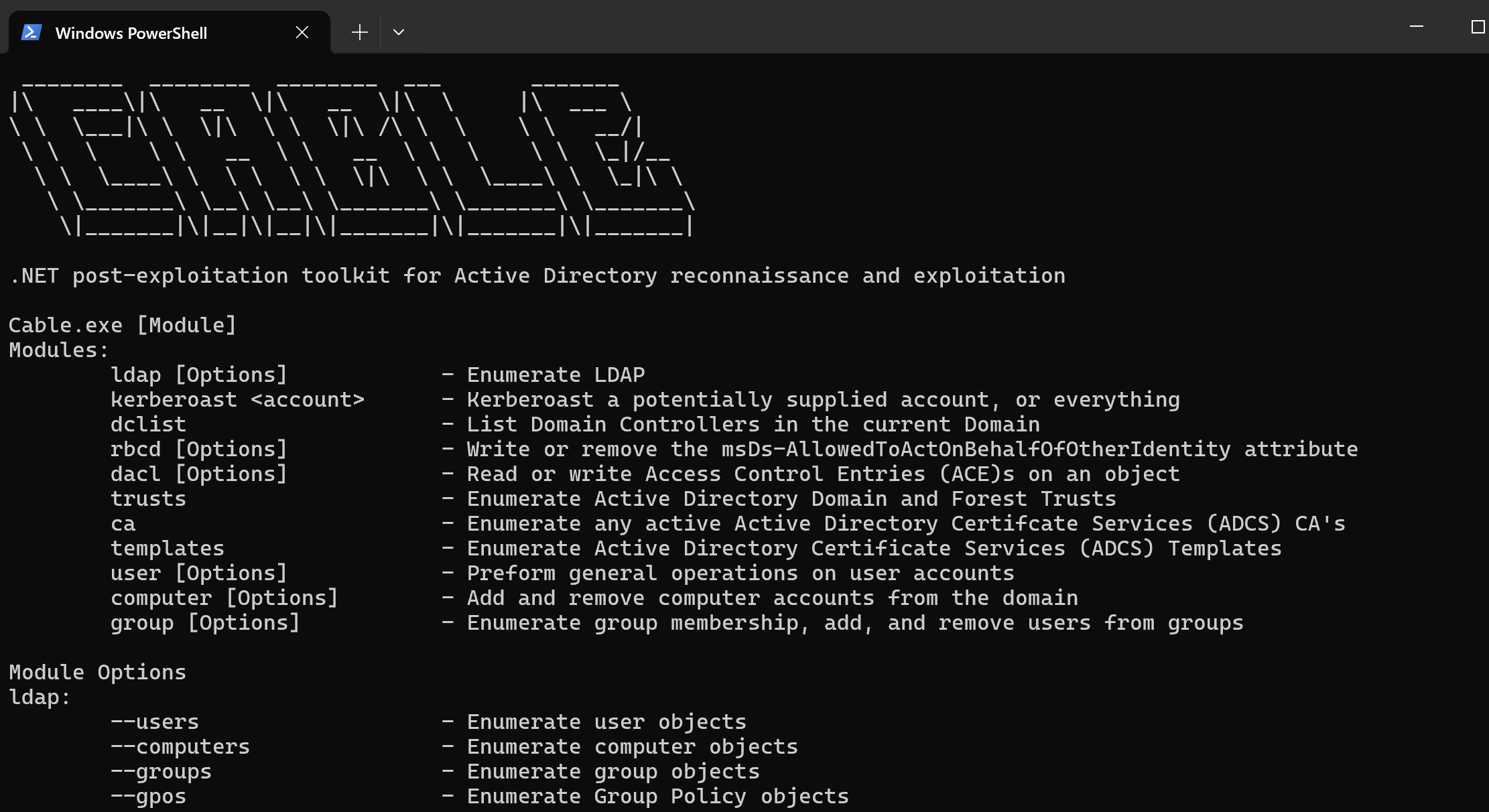
Active Directory (AD) remains a core component of enterprise environments, and as such, understanding its vulnerabilities is crucial for both attackers and defenders. Enter Cable, a streamlined, open-source post-exploitation tool designed specifically for enumeration and exploitation of Active Directory environments. Created with .NET, Cable provides security professionals with a variety of techniques for probing AD’s security posture and performing privilege escalation tactics in a controlled environment.
Cable was built with two key goals: advancing knowledge in .NET offensive development within an Active Directory context and expanding Active Directory exploitation techniques.
Key Features of Cable
- Kerberoasting Capabilities
Kerberoasting is an attack technique that targets service accounts with servicePrincipalName (SPN) attributes, allowing attackers to request and crack service tickets offline. Cable facilitates this process by retrieving tickets from AD accounts registered with SPNs and saving them in a crackable format, making it easier to obtain service account credentials. - Resource-Based Constrained Delegation (RBCD) Exploitation
Cable can manipulate the msDs-AllowedToActOnBehalfOfOtherIdentity attribute on specified objects, a key component in Resource-Based Constrained Delegation (RBCD) attacks. RBCD allows specific accounts to impersonate other users, providing a path to lateral movement within AD. - DACL (Discretionary Access Control List) Manipulation
With the ability to both read and modify Access Control Entries (ACE) in DACLs, Cable empowers users to manage access permissions on AD objects. This feature is essential for auditing permissions or adjusting access rights for specific security objectives. - Active Directory Certificate Services (ADCS) Enumeration
In recent years, ADCS has become a common target due to its potential vulnerabilities. Cable enables users to enumerate Certificate Authorities (CAs) and certificate templates, which can provide insight into possible misconfigurations or weak certificates. - Domain and Forest Trust Enumeration
Trust relationships between domains and forests can offer paths for cross-domain escalation. Cable allows for comprehensive enumeration of these trusts, assisting security analysts in identifying inter-domain vulnerabilities. - Domain Controller Enumeration
Knowing the domain controllers (DCs) is critical for any attack or defense strategy within AD. Cable provides enumeration of DCs within the current domain, aiding in reconnaissance. - Flexible LDAP Enumeration
Cable supports both general LDAP enumeration and custom queries, making it highly versatile for gathering user, group, and computer data within AD. Users can select specific attributes to be returned, streamlining the process and improving accuracy in data collection. - Password Management and ServicePrincipalName Control
Cable allows for changing user passwords within AD, which can assist in testing or privilege escalation efforts. It also provides control over servicePrincipalName (SPN) attributes, allowing security professionals to toggle an object’s kerberoastable status. - AS-REP Roasting Setup
Cable can set or remove the DONT_REQ_PREAUTH flag on an object’s userAccountControl attribute, which is key for AS-REP Roasting. This attack method targets accounts that don’t require pre-authentication, which attackers can then request and crack offline. - Group and User Membership Enumeration
Cable allows for listing group memberships for users and vice versa, simplifying the task of finding users with elevated privileges or assessing potential escalation paths. - Computer Object Management
The ability to create and delete computer objects within AD can offer attackers additional avenues for privilege escalation or lateral movement.
Practical Uses for Cable in Security
For red teams and penetration testers, Cable’s straightforward, modular design makes it ideal for reconnaissance and privilege escalation exercises in AD. Each function aligns with common techniques used in AD exploitation, and Cable’s flexibility in configuring LDAP queries allows for highly customized enumeration of directory services. Blue teams and system administrators can also use Cable in a controlled environment to understand potential vulnerabilities within their AD deployments.
Getting Started with Cable
Cable, available on GitHub, represents a powerful addition to the toolkit of any security professional working with or defending Active Directory environments. With its broad functionality spanning Kerberoasting, DACL manipulation, RBCD exploitation, and ADCS enumeration, Cable simplifies many aspects of AD post-exploitation. For IT professionals, understanding and testing AD vulnerabilities with tools like Cable is essential for strengthening overall network defenses.